Q3 Product Updates: Introducing EASM<sup>X</sup>

Table of contents
Your digital footprint is growing. So is our coverage: Meet Xtended External Attack Surface Management (EASMX).
Q3, who? We get it, you’re on to the Q4! But trust us when we say our Q3 product updates are about to make your Q4 (and beyond) a whole lot better. This wasn’t an ordinary quarter here at CybelAngel (although they rarely ever are) but a time for delivering you our most impactful launch yet. One that will make your external attack surface management efforts more accurate, efficient, and effective. We also packed in updates to our machine learning capabilities and are offering an M&A Due Diligence Assessment you won’t want to miss. Ready to see beyond? Keep reading!
Secure Your External Attack Surface
Imagine an old event page is still active and can be leveraged by threat actors to access a production database. Disrupted operations anyone? Or maybe you just completed an M&A deal that has resulted in some major domain blindspots. Here comes the ransomware! As your organization’s appetite for cloud services, third-party vendors and IoT devices continues to grow, so will its external attack surface. To proactively surface these types of exposures and secure threats, you need a powerful solution with an evolving outside-in view beyond your organization’s IT perimeter. Our Digital Risk Protection Solutions proactively protect your digital infrastructure from threats. But why stop there?
See Beyond with EASMX
Your external attack surface is cloud high, dark-web deep, supply-chain wide and internet infinite. Today we are expanding your vision so you can see it all. It started with our Digital Risk Protection Solutions, which include:
- Data Breach Prevention
- Domain Protection
- Account Takeover Prevention
- Dark Web Monitoring
We’ve continued to iterate on this holistic approach to EASM with enhancements to our most innovative module yet: Asset Discovery & Monitoring. This coupling is the foundation of EASMX:
| Digital Risk Protection Solution (DRPS) + Asset Discovery & Monitoring (ADM) = EASMX | |
|---|---|
Digital Risk Protection Solution With DRPS, you can proactively protect your digital infrastructure from threats during digital transformation.DRPS stops…
|
Asset Discovery & Monitoring Our ADM solution maps your organization’s exposed assets outside of its security perimeter and then continues to monitor them for vulnerabilities and/or remediation.ADM detects & monitors…
|
Under the umbrella of this CybelAngel power pairing, your expanding external attack surface is covered by the exponential reach of our solutions. While DRPS attains document level depths, ADM will account for the breadth of your external attack surface; keeping you fully secure beyond your perimeter.
Asset Discovery & Monitoring Updates
ADM allows you to eliminate shadow risk by detecting services exposed outside of your perimeter, attributing them to your organization in a complete inventory and prioritizing remediation based on criticality to your specific business needs. 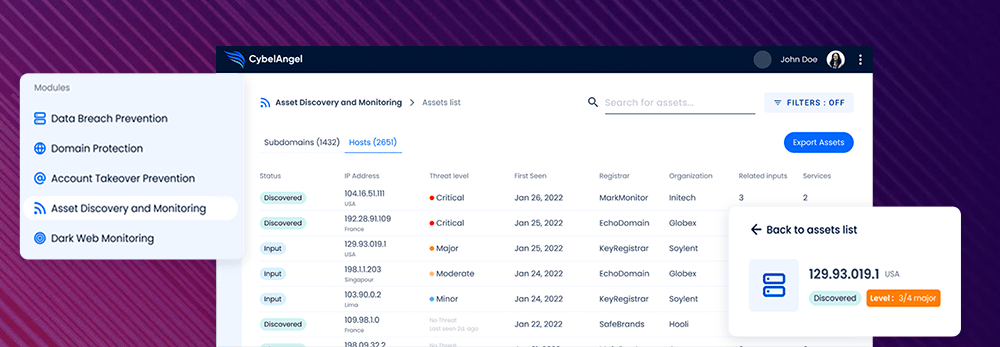 We keep your asset inventory accurate and actionable on a daily basis through a unique and thorough discovery method. Think of it as a one-two punch: 1. Anchor your assets by pivoting:
We keep your asset inventory accurate and actionable on a daily basis through a unique and thorough discovery method. Think of it as a one-two punch: 1. Anchor your assets by pivoting:
- We use known asset inputs to find other unknown assets that may be just out of your current purview.
2. In-depth web scanning:
- Our extensive web scanners utilize keywords to locate vulnerable shadow services across your business environment.
Let’s dig into what makes this recent launch so revolutionary: ![]() The Most Complete External Asset Inventory List The first step in securing your external attack surface is having a comprehensive asset inventory. Our solution? An automated, always up-to-date inventory of all your organization’s external-facing assets (we’re talking thousands of IPs and domains).
The Most Complete External Asset Inventory List The first step in securing your external attack surface is having a comprehensive asset inventory. Our solution? An automated, always up-to-date inventory of all your organization’s external-facing assets (we’re talking thousands of IPs and domains). ![]() Shadow IT, Ranked by Criticality How will you prioritize this comprehensive list of assets? Our continuous exposure monitoring (updated every 24 hours) allows you to filter assets based on their vulnerability level to drive focus on the assets that pose the most risk to you.
Shadow IT, Ranked by Criticality How will you prioritize this comprehensive list of assets? Our continuous exposure monitoring (updated every 24 hours) allows you to filter assets based on their vulnerability level to drive focus on the assets that pose the most risk to you. ![]() Take Action with Full Contextualization We’ve identified a critical asset that’s yours…now what?! The devil is in the details. We provide you specifics like related inputs and further threat information, giving you all the context you need to quickly remediate and eliminate potential threats. To top it off, your dedicated analyst will continue to deliver on accurate asset attribution. During the keyword matching phase, your analyst will confirm that discovered assets actually belong to your organization. They’ll push this critical information directly to you through actionable incident reports. Want to learn more? Reach out to your dedicated Customer Success Manager or send us a message here for more details.
Take Action with Full Contextualization We’ve identified a critical asset that’s yours…now what?! The devil is in the details. We provide you specifics like related inputs and further threat information, giving you all the context you need to quickly remediate and eliminate potential threats. To top it off, your dedicated analyst will continue to deliver on accurate asset attribution. During the keyword matching phase, your analyst will confirm that discovered assets actually belong to your organization. They’ll push this critical information directly to you through actionable incident reports. Want to learn more? Reach out to your dedicated Customer Success Manager or send us a message here for more details.
Machine Learning for Faster Time to Remediation
You’ve got a ton of tools to manage with hundreds of alerts to sift through; it’s too much! That’s why we don’t send you false positives. 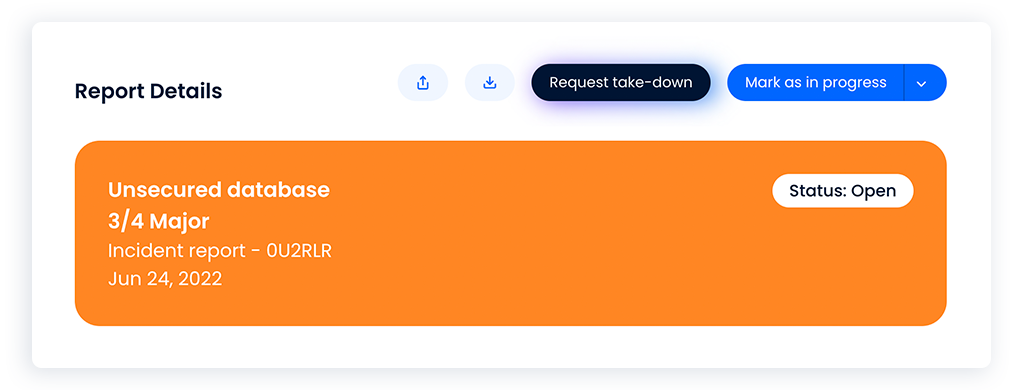 This can be attributed to our advanced technology and, for further refinement, a human touch. The discernment of your dedicated analyst is a critical part of the alert process. We’ve continued to iterate on our machine learning capabilities to reduce alert noise in your analyst’s feed related to cloud drive and potential duplicative asset discoveries The result? Your analyst is better able to assist you by focusing solely on true positives and critical alerts, meaning you can take immediate action.
This can be attributed to our advanced technology and, for further refinement, a human touch. The discernment of your dedicated analyst is a critical part of the alert process. We’ve continued to iterate on our machine learning capabilities to reduce alert noise in your analyst’s feed related to cloud drive and potential duplicative asset discoveries The result? Your analyst is better able to assist you by focusing solely on true positives and critical alerts, meaning you can take immediate action.
M&A: Don’t Let Cyber Risk Be a Deal Breaker
Is your organization in the midst of any M&A activity to close out the year? Any big plans for 2023? If so, you may be a target for cyberattacks. Acquirers with mature M&A practices recognize this and will integrate this risk into their due diligence strategy and valuation, using multiple factors as estimating guides such as industry, policies and history. Sometimes they get it right, sometimes they don’t… What if you could see the exposure first hand? And…start remediation immediately? 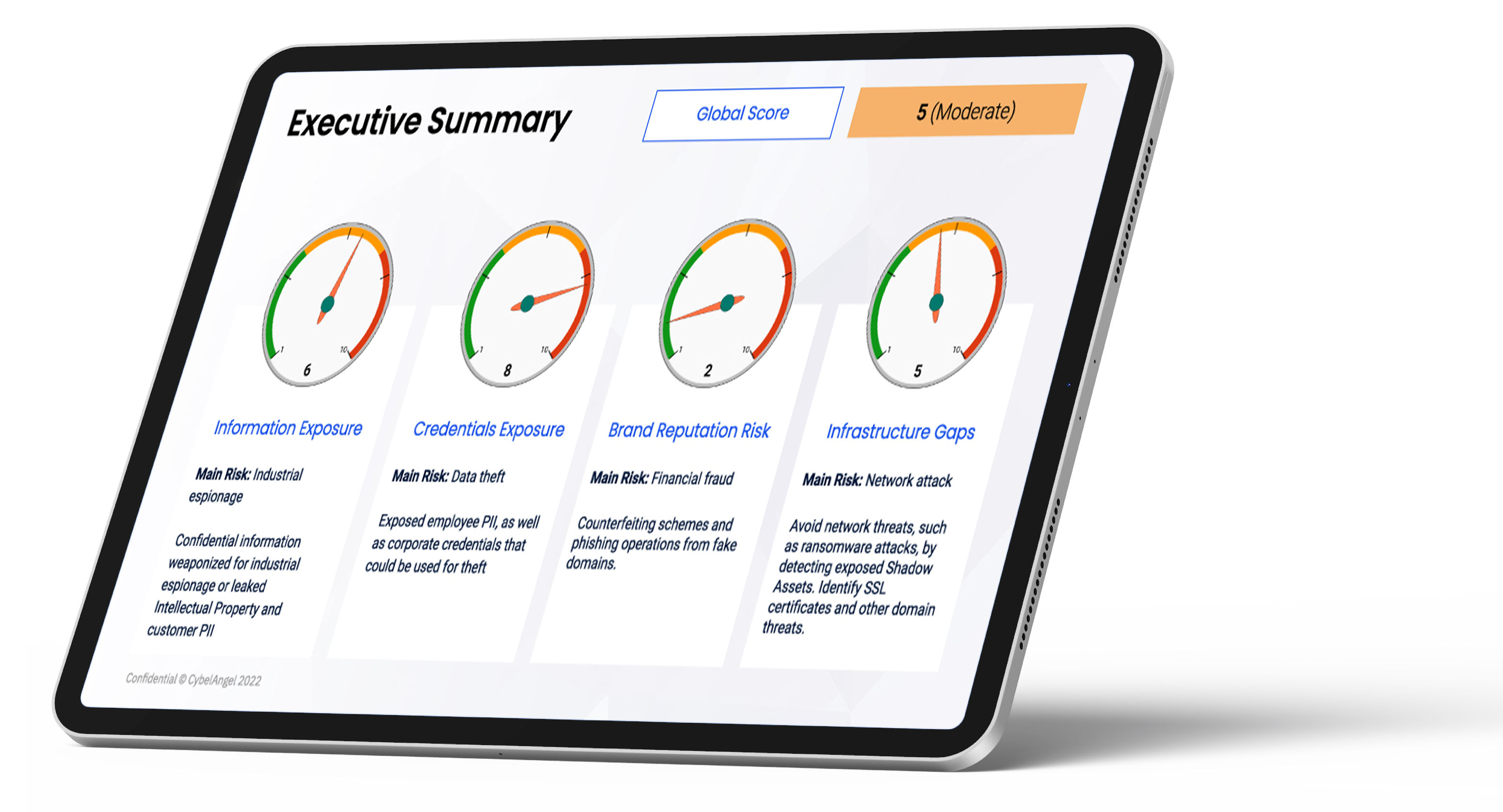 We’re giving you real-time visibility into real risk potential — and providing you the ability to price risk appropriately to protect both target and buyer from cyberthreats. Capture It All Identify, contextualize and mitigate cyber exposure before you make the deal! Our M&A cyber assessments leverage unprecedented search technology built upon close to a decade of machine learning activity and offers the most comprehensive threat detection available. At Lightning Speed Scanning the depths of the internet every 24 hours to find exposures and threat patterns, you get concrete insights—in just four business days Tailored to Your Needs No more automatic, inconsequential scores. An expert team of analysts build in-depth Cybersecurity Due Diligence Reports that include insights into:
We’re giving you real-time visibility into real risk potential — and providing you the ability to price risk appropriately to protect both target and buyer from cyberthreats. Capture It All Identify, contextualize and mitigate cyber exposure before you make the deal! Our M&A cyber assessments leverage unprecedented search technology built upon close to a decade of machine learning activity and offers the most comprehensive threat detection available. At Lightning Speed Scanning the depths of the internet every 24 hours to find exposures and threat patterns, you get concrete insights—in just four business days Tailored to Your Needs No more automatic, inconsequential scores. An expert team of analysts build in-depth Cybersecurity Due Diligence Reports that include insights into:
- Exposed intellectual property
- Cyber risks with potential to impact valuation and brand reputation
- Cyber risks tied to the technical integration
- Benchmarks against similar industry players
- Mitigation recommendations or you can ask about CybelAngel’s mitigation services
Remediation And should you find critical exposures, CybelAngel offers on-demand remediation services to speed up the integration process. Interested? Fill out the demo form on the bottom of this page to get started.