Security vulnerabilities have real-world consequences

Table of contents
My name is Sunil and I work in Security Operations. This is my story about how I told the Board of Directors that cyber-attacks are preventable. The truth is, I don’t want to spend this spring reinstalling operating systems for my employer. If our company does not prevent a cyber attack, our system could suffer so much damage that we’d have to burn down our systems and start over. If you did not know, the more your data is at risk, the more your business is at risk. That is why I was invited to attend a Board meeting with our CISO. I wanted the meeting to go well. Lockdown was rough. I wanted to spend my free time going outside with my friends. I wanted to take the dog for a walk — and I don’t even have a dog. The main thing I knew for sure, is that I did not want to spend my spring reinstalling operating systems after a bad cyber attack.
Meeting with the Board of Directors
This was my first time at a Board meeting. The CISO had his presentation ready, but I had no idea what the Board of Directors might ask. We stood by until we came upon the agenda. The CISO started his presentation by saying, “Our company faces a changing business landscape, just like most companies these days. During the lockdown, we had three major IT initiatives that increased risk to our data security, which increased risk to our business.” The CISO showed his first slide: 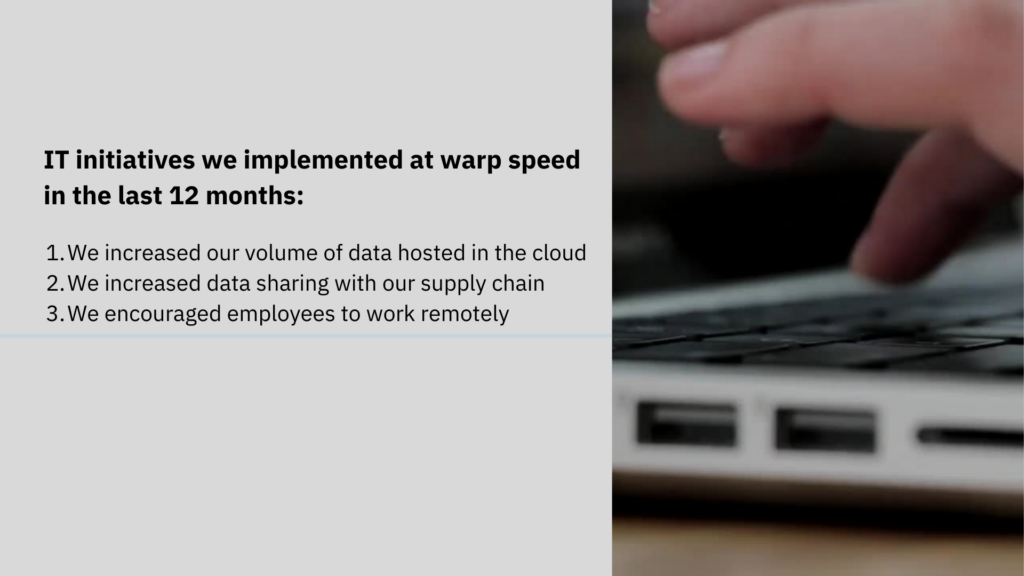 “These changes increase our attack surface exponentially, which increases risk to our business,” the CISO said, “Further, our supply chain network is under attack and we do not have visibility into the security of the data we share with them. Hackers can attack our data in the cloud, through shared software in our supply chain, and via our own employees logging into our network from unsecured devices.” After some discussion, the Board said they wanted to hear from a Subject Matter Expert in Security Operations. That was me, so I sat up, all ears.
“These changes increase our attack surface exponentially, which increases risk to our business,” the CISO said, “Further, our supply chain network is under attack and we do not have visibility into the security of the data we share with them. Hackers can attack our data in the cloud, through shared software in our supply chain, and via our own employees logging into our network from unsecured devices.” After some discussion, the Board said they wanted to hear from a Subject Matter Expert in Security Operations. That was me, so I sat up, all ears.
Likelihood of supply chain attacks
“Hi, Sunil, thanks for joining us today,” the Chairman started, “We hear about this growth in the attack surface for our organization, what’s the real likelihood of a supply chain attack? Our supply chain is our business partners. If we have security protocols in place, why is there still a risk?” My pulse sped up till I could hear it in my ears, as I said, “Thank you, sir. To your first question, what’s the likelihood of a cyberattack on our company? 100% likelihood. We have cyber attacks every day, some we prevent because we know about them — and some we don’t because we do not know about the asset vulnerability. In fact, we have to forecast losses from data breach because we know there are unknown risks from our supply chain, from shadow IT assets, from phishing attacks, and account takeovers, just to name some of our major threats.” This drew muffled concern from the Board. The Chairman’s attention weighed on me as he said, “please go on.” I continued, “The second question is if we have security protocols, why is there still a risk? It comes down to visibility, as the CISO mentioned earlier. We do not have visibility into all the assets where our data is hosted. Yes, we have security protocols in place with our vendors. But we cannot control the human element. We cannot verify that there were no misconfigurations, which often happens with cloud storage, such as Google Cloud Storage buckets and Azure Blob and AWS S3 buckets. Even our Microsoft Exchange Server is vulnerable to attack. People make mistakes, and through those errors, our data becomes vulnerable. What we need is visibility into where we are vulnerable. And there are security tools for that — but we don’t have them,” I said.
What’s the worst that could happen?
The CFO asked, “what’s the worst that could happen if we don’t get these security tools?” “The cyber attacker could live in our network forever, disrupting our business. Shutting down our activity. Preventing us from working with our customers, and partners,” I answered. “Do you want to know how this works?” I asked, “Yes, go on,” the CFO answered. “Here’s how it works, After a hacker gains access to a network, their goal is to establish persistent access that will remain even after the initial vulnerability is fixed. Persistent access means that the hacker can move around our network and exploit whatever systems and accounts they want. Then they infect our network with ransomware and hold our data for ransom, or they sell it on the Dark Web or run other exploits. And it never ends.” “Recovering from this kind of attack is not easy.” I continued “When a hacker has persistent access to our network infrastructure, the only way to secure our network is to burn it to the ground and rebuild it. This means that if we have a major cyberattack, even if we already spent our budget on new IT initiatives, we would need to start over, and spend quite a bit more”. Another member of the board spoke up “So, you think this is a real-life threat that we face?”. “Yes,” I replied, “You may have heard of the recent SolarWinds incident, a supply chain attack in which the US suffered a major data breach. SolarWinds provides software to manage IT infrastructure. When they shared an infected software update with their clients, over 17,000 companies unknowingly allowed cybercriminals to gain access to their networks. The point is, if the supply chain for SolarWinds can get hacked, ours can, too.” I felt my confidence build and my voice settle: “If our network is infected with code that allows hackers access, we risk not only our network, but we also risk compromising our supply chain. We don’t want persistent infiltration by cybercriminals on our network. This is a situation that we can prevent.”
Security vulnerabilities have real-world consequences
The Chairman interjected, “Are you telling me, security vulnerabilities have real-world consequences?” “Yes, sir” I replied, “recovering from a cyber attack is not easy. We need to accept that our security vulnerabilities could result in damage to our network infrastructure and compromise our supply chain. We know that our IT initiatives last year had rushed implementations — so there are bound to be errors. Now we need to secure any vulnerable asset. As long as we do business in the cloud, we need to take a defensive stance to protect our strategic assets.” The Chairman turned to the Board and said, “are there any other questions?” “I’d like to see that forecast for losses from a data breach,” said the COO, to which everyone nodded in agreement. The Chairman of the Board thanked us and we were excused. Once in the hall, I looked at my manager and asked, “so how’d that go?” “We’ll know for sure when the budget comes out.” said our CISO, adding “You did great. Thanks, Sunil. Good job.” I breathed a sigh of relief. I knew our company needed to implement those initiatives last year, but we did not complete the job. I was sure we have unsecured data outside our visibility. For my part, I hope we can implement a tool for data breach prevention. Then I could enjoy spring without worrying so much about cyber threats. Because leaks are inevitable; but damage is optional.