Top Threat Actors on the Dark Web | 2023 Recap

Table of contents
Emerging and rising top threat actors on the dark web demanded attention in 2023; from malware experts to state sponsored cyber cyberattacks. These actors had a tremendous global impact in fueling illegal activities and cybercrime. In part 4 of our dark web monitoring series, we offer a brief recap of what CISOs need to consider for 2024.
Have you missed parts I-III?
Catch up with this series here:
- What is Dark Web Monitoring?[Plus, How Will it Evolve in 2024?]
- Understanding Dark Web Intelligence: How Cybercriminals Share Intel
- Dark Web Takedowns in 2023 | An Overview for CISOs
Which dark web threat actors dominated in 2023?
Regardless if you’ve worked within the cybersecurity world for long, you’ve undoubtedly felt curious about which dark web threat actors represent the most risk to your company’s security.
Threat actors, also known as cybercriminals, cyber threat actors or malicious actors, are individuals or groups who deliberately inflict harm upon digital devices or systems.
While less central to your day-to-day activity as a CISO, following the biggest perpetrators of cyber threats on the dark web is an important part of dark web monitoring intel.
From this article:
- Examine 4 areas within the dark web where specialised threat actors ranked as top threats in 2023
- Learn how these dark web threat patterns could impact your threat outlook for 2024
- You’ll be equipped with more dark web threat trend insights as a CISO
1: State-sponsored threat actors
State sponsored threat actors, also known as a nation state actors, government-sponsored entities are involved in cyber activities such as espionage, sabotage, and offensive actions to promote their nation’s interests.
A list of the dominant nation state threat actors in 2023:
- APT 28 (Fancy Bear)
- APT 29 (Cozy Bear)
- Emissary Panda
- APT 33
- Charming Kitten
- Lazarus Groups
- Midnight Blizzard (NOBELIUM)
How do these threat actors impact you?
State sponsored threat actors have a global impact. The wreak havoc because of the wealth of government resources that are at their disposal and because of how highly skilled they are. According to the New York Times, Iranian hackers used “malware to infiltrate the computers of its rivals and mapped out the networks the hackers had broken into, providing Iran with a blueprint of foreign cyberinfrastructure that could prove helpful for planning and executing future attacks.”
Official advice from CISA counsels that CISOs should keep software up to date and prioritize the patching of known exploited vulnerabilities to strengthen operational resilience against these threat actor.
Cyber threats use case: Microsoft
Microsoft were the targets of a nation-state attack on January 12th 2024, that targeted their corporate systems. Reports have circulated that these threat actors were able to access the email accounts of some members of its senior leadership team in late 2023.
An internal investigation by the corporate giant named threat actor, Midnight Blizzard, a Russian state-sponsored actor also known as NOBELIUM.
Microsoft in response to this incident noted on their blog that, “Given the reality of threat actors that are well resourced and funded by nation states, we are shifting the balance we need to strike between security and business risk – the traditional sort of calculus is simply no longer sufficient. For Microsoft, this incident has highlighted the urgent need to move even faster.”
What is the cyber threat outlook for 2024?
In 2024, the impact of geopolitics on the realm of cyber warfare has become more apparent, particularly in relation to operational technology (OT) and industrial control systems (ICS) environments.
Cybersecurity experts need to consider:
- Developing resilient OT/ICS infrastructures
- Implementing stringent cybersecurity protocols, including dark web monitoring
- Employing mechanisms that include incident response professionals to help coordinate response efforts without being monitored by these nation state threat actors
2: Infostealer threat actors
An information stealer, also known as an “infostealer” or “stealer,” is a specific type of malware, often in the form of a Trojan virus. This malicious software is designed to deceive and secretly gather sensitive information. Its main objective is to extract personal data from any compromised computer.
A list of the dominant infostealer threat actors in 2023:
- LummaC2
- Raccoon Stealer
- Redline Stealer
- Rhadamanthys
- Vidar
- StrelaStealer
- Gozi
- AZORult
How do these malware threat actors impact you?
Monitoring infostealer malware ecosystem—whereby anyone can buy valid login credentials for a target should be a continued priority for CISOs and SOC teams. Malware threat actor groups will continue to leverage underground markets on the dark web to directly target organizations, their third-party servicers and business process outsourcers (BPOs).
What is the cyber threat outlook for 2024?
Cybersecurity experts need to consider:
- Third parties and BPOs in their risk management programs
- Using application or token-based MFA methods
- Employing robust network intrusion detection software, including rapid detection of suspicious account activity will be especially resilient
- Maintaining and following an established incident response procedure
Cyber threats use case: Latitude Financial
Latitude Financial, an Australian financial company, was subject to a vicious cyber-attack in March 2023 that resulted in the theft of personal information. A forensic review alongside Australian law enforcement revealed that approximately 7.9 million Australian and New Zealand driver license numbers were stolen, with around 40% provided within the last decade. 53,000 passport numbers were also compromised as well as 6.1 million records, dating back to at least 2005, were also stolen. These records contained sensitive information including names, addresses, telephone numbers, bank account numbers, credit card details, and dates of birth.
Latitude Financial (ASX: LFS) received a ransom demand from the criminals behind the cyber-attack and publicly declined to pay this ransom. The company’s CEO, Bob Belan, commented that the company had been focused on safely restoring IT systems, staffing levels and enhancing cybersecurity protections to returning to normal operations.
3: Ransomware threat actors
Ransomware is an incredibly effective business model that is easily facilitated by dark web forums where small and big players alike can offer up their RaaS (ransomware as a service) skills.
Leveraged ransomware threat patterns by these cybercriminals include:
- Software vulnerabilities e.g. via zero-day vulnerabilities and novel zero-day techniques
- Phishing
- Remote desk protocol (RDP)
A list of the biggest ransomware actors in 2023
- LockBit
- The Cl0p gang (also known as TA505)
- Alphv/BlackCat
- Black Basta
- Vice Society
- Royal
- Everest
- Scattered Spider (also known as UNC3944)
What is the cyber threat outlook for 2024?
Cybersecurity experts need to consider:
- The U.S. Cybersecurity and Infrastructure Security Agency describes this Russian speaking ransomware group, The Cl0p gang, as “driving global trends in criminal malware distribution
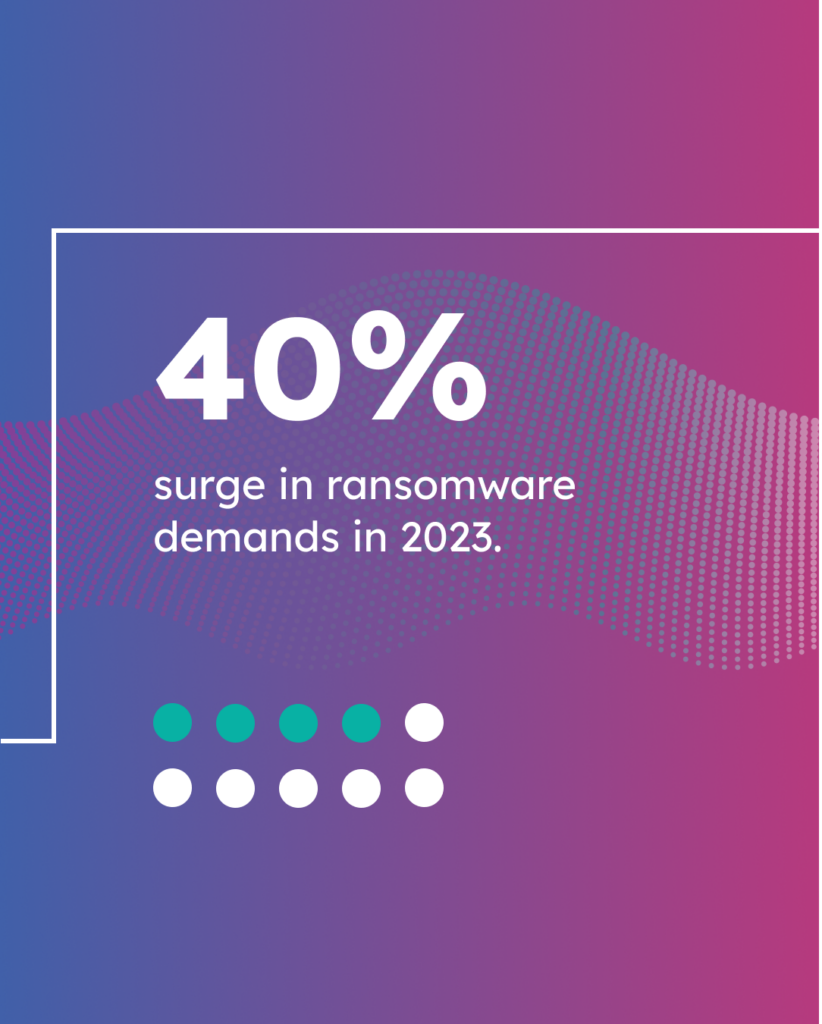
- CybelAngel data from 2023 unveiled an increase in ransomware demands by 40%
- CISOs can access clear analysis about ransomware attacks as well as study two 2023 use case within CybelAngel’s new annual report
6 actionable ways to defend against emerging threat actors
Prime your cyber defenses with these six clear cut action items to implement in 2024.
- Dark web monitoring: Dark web monitoring enables CISOs and their SOC teams to gain visibility on illegal activities on the dark web and to identify incoming cybersecurity threats and stolen information.
- Carry out specialized threat investigations: Organizations should tap into special threat investigations to gain full visibility on dark web threat actors when needed, e.g. during M&A proceedings.
- Access cutting edge threat intelligence: The CybelAngel REACT team offer specialized threat reports to all clients and field requests for ad hoc reports as part of an external request. These reports can assist with contextualised and extensive threat actor profiling. ADD IMAGE OF DARK WEB REACT GUIDE
- Analyst accompaniment: The need for 24/7 human facing support is imperative when it comes to reviewing threats as part of wider dark web monitoring. CybelAngel analysts work alongside you and your SOC team to shape a contextualized incident report to remediate quickly.
- Deploy dark web awareness training: Because sophisticated threat actors often depend on human error, employee training is an important line of defense. Security awareness training can cover anything from recognizing dark web threats like malware and ransomware campaigns, to dealing with the outcomes of data breaches on the dark web.
- Service Provider: Selecting the best dark web monitoring service provider is critical. When issues arise you will require an experienced team to help steer the right incident response.
Wrapping up
That is it for part four of our dark web monitoring series.
You can follow new publications linked to this dark web monitoring series on LinkedIn and Twitter.