The Global Impact of Aviation Cyberattacks

Table of contents
The aviation industry is under attack. Cybercrime has continued to rise over the past 5 years as IT security measures struggle to keep up.
The European Aviation Safety Agency (EASA) estimated a monthly average of 1,000 airport cyberattacks in 2020, with a 600% increase in aviation cyberattacks reported between 2024 and 2025.
The consequences of poor aviation threat management are huge. During peak time in a large airport, 1 hour of operational disruption has an estimated cost of $1 million. Disruptions and delays continue to cost airlines in the aftermath of an attack, too—in one case, an airline had to cancel over 1,200 flights due to a cyberattack.
Let‘s examine the changing threat landscape in the aviation sector and how airlines can improve their information security practices.
Escalating threat landscape
A review of cybersecurity challenges in the aviation industry from 2022 found 71% of hackers were focused on stealing login details to gain access to IT systems. Of those attacks, 25% were DDoS attacks, and 4% of cybercriminals aimed to corrupt file integrity.
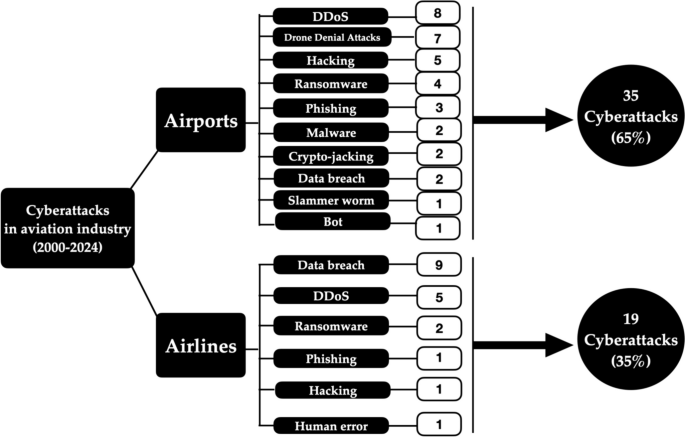
Sophisticated attacks pose a threat to the entire aviation supply chain:
- DDoS attacks: Hackers overwhelm systems with excessive internet traffic, causing systems to go down. DDoS attacks are difficult to prevent, since many airports across the US use technology that is often outdated (and in some cases over 30 years old).
- Ransomware: Cybercriminals gain access to unauthorized systems through malicious software. Ransomware attacks are known to paralyze essential operations such as baggage handling (BHS), building management systems (BMS), and flight management (FMS). Airlines are reluctant to report ransomware attacks to protect their reputation.
- Data breaches: Once inside a system, cybercriminals can exploit vulnerabilities to leak data, leaving passengers and staff vulnerable. In one documented case from San Francisco, a data breach occurred using an employee’s credentials to gain access, endangering airport staff safety.
- Worm attacks: Airlines are particularly vulnerable to worm attacks due to outdated legacy systems. For now, worm attacks are in the minority and don‘t pose a significant threat.
- Phishing and social engineering: Threat actors use deceptive emails, phone calls, or messages to trick employees into handing over sensitive information used to gain access to systems. Scattered Spider in their attacks against airlines impersonated employees and contractors to deceive IT help desks, and ended up being granted access.
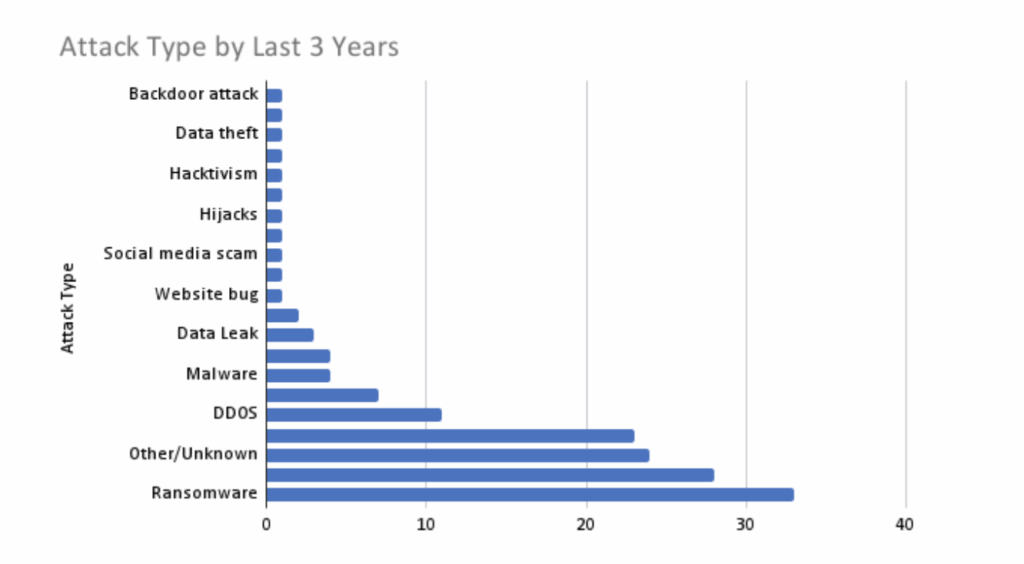
Major aviation cybersecurity incidents
The transportation sector has experienced a rise in cybersecurity incidents over the past 5 years. Aviation, described as a “system of systems,” is comprised of many technologies, people, and processes, leaving the supply chain open to threats.
In 2025, the aviation world saw a string of attacks on prominent US and EU airlines. This isn‘t new—over the past 5 years, cyber attacks on the aviation industry have been steadily growing. However, security professionals warned that the problem will only intensify.
“We are pushing decades-old aviation systems to handle high-demand travel 24/7, and the cracks are showing. Even without a cyberattack, outdated technologies and fragile logistics can lead to massive disruptions,” stated Jiwon Ma, senior policy analyst at FDD’s Center on Cyber and Policy Innovation.
To better understand the recent cyberattacks, let‘s look in detail at each attack and how hackers were able to bypass airline cybersecurity.
1. Cathay Pacific (Hong Kong), May 2018
In March 2018, a brute-force attack locked out 500 Cathay Pacific employees from their accounts, triggering immediate security alerts that led to the discovery of the breach.
An investigation revealed that data from 9.4 million passengers had been exposed. It was discovered that keylogger malware was installed in 2014 on Cathay Pacific‘s networks, where threat actors harvested credentials for years before the attack.
The Hong Kong commissioner, Stephen Kai-yi Wong, stated, “It is quite clear that contraventions aside, Cathay adopted a lax attitude towards data governance, which fell short of the expectation of its affected passengers and the regulator.”
In 2020, the Information Commissioner’s Office (ICO) fined Cathay Pacific Airways £500,000 for failing to protect customers’ sensitive data.
2. Japan Airlines (Japan), December 2024
Japan Airlines experienced a DDoS cyberattack during the busy New Year travel period. The attack affected 28% of all Japan Airlines flights, causing delays to all flights and suspending ticket sales, especially at Tokyo‘s central Haneda Airport. The network disruption took six hours to restore regular operations, and no sensitive data was exposed.
3. WestJet (Canada) June 2025
WestJet experienced a cyberattack that disrupted internal systems and its mobile app, causing delays to flight bookings for 5 continuous days. While flight operations remained unaffected, it did result in financial loss for the company and reputational damage. WestJet has not confirmed whether sensitive information was leaked.
4. Hawaiian Airlines (USA) June 2025
In late June 2025, Hawaiian Airlines experienced a cybersecurity incident that disrupted parts of its IT infrastructure, though flight operations and safety remained unaffected. The nature of the incident was not disclosed; however, Reuters speculates that it could be indicative of a ransomware attack.
5. American Airlines (USA) June 2025
American Airlines suffered a widespread outage with its flight information computer system due to an incident that caused connectivity issues. A source from an affected airport in the U.S. stated there were issues with internal systems, flight bookings, check-in, ticketing, and baggage tagging.
While details about the incident itself have not been released, a flight tracker showed more than 40% of American Airlines flights were delayed, and 7% were canceled.
Scattered Spider: The latest cybercriminal group behind airline attacks
A recent string of cyber attacks on the airline sector by the cybercriminal group Scattered Spider highlighted the need for more cybersecurity measures.
The hackers relied heavily on impersonation and bypassing multi-factor authentication (MFA) through help desk manipulation to conduct their attacks.
MITRE ATT&CK techniques used by Scattered Spider
| Tactic | Technique | Description |
|---|---|---|
| Reconnaissance | T1589 | |
| Gather Victim Identity Information | Collected employee details from LinkedIn and public sources. | |
| T1583.001 | ||
| Acquire Infrastructure: Domains | Registered fake domains (e.g., airline-sso.com) for phishing. | |
| Initial Access | T1566.001 | |
| Phishing: Spearphishing via Email | Used fake login portals and impersonation to steal airline employee credentials. | |
| 1598.002 | ||
| Phishing for Information: Voice | Vishing help desks to reset multi-factor authentication (MFA) or passwords. | |
| T1656 | ||
| Impersonation | Pretending to be airline staff to gain trust and access. | |
| T1078.002 | ||
| Valid Accounts: Cloud Accounts | Gained access using stolen or reset credentials. | |
| T1190 | ||
| Exploit Public-Facing Application | Exploited unpatched servers or apps (e.g., ForgeRock CVE-2021-35464). | |
| Execution | T1059 | |
| Command and Scripting Interpreter | Used PowerShell and Bash for script execution. | |
| T1219 | ||
| Remote Access Software | Deployed AnyDesk, TeamViewer, Teleport. | |
| T1569.002 | ||
| System Services: Service Execution | Created services to run payloads. | |
| Persistence | T1556.006 | |
| Modify Authentication Process: MFA | Registered attacker-controlled MFA devices. | |
| T1133 | ||
| External Remote Services | Used VPNs and Citrix for long-term access. | |
| T1219 | ||
| Remote Access Software | Deployed tools like TeamViewer, AnyDesk, and Teleport. | |
| Privilege Escalation | T1068 | |
| Exploitation for Privilege Escalation | Used vulnerable drivers to disable security tools. | |
| T1484.002 | ||
| Domain Policy Modification: Trust Modification | Altered SSO configurations to maintain access. | |
| Defense Evasion | T1562.001 | |
| Disable or Modify Tools | Deployed malicious drivers to kill EDR/AV. | |
| T1217 | ||
| Browser Information Discovery | Stole session cookies and browser history. | |
| T1564.008 | ||
| Hide Artifacts: Email Hiding Rules | Created inbox rules to delete security alerts. | |
| Credential Access | T1003.003 | |
| OS Credential Dumping: NTDS | Extracted domain controller credentials. | |
| T1552.001 | ||
| Unsecured Credentials | Searched for stored passwords and secrets. | |
| T1528 | ||
| Steal Authentication Tokens | Hijacked OAuth and SSO tokens. | |
| Discovery | T1083 | |
| File and Directory Discovery | Enumerated sensitive files and source code. | |
| T1580 | ||
| Cloud Infrastructure Discovery | Mapped cloud resources and IAM roles. | |
| T1538 | ||
| Cloud Service Dashboard | Used AWS Systems Manager Inventory for lateral movement targets. | |
| Lateral Movement | T1021.001 | |
| Remote Services: SMB/Windows Admin Shares | Used PsExec and RDP to move across systems. | |
| T1563.002 | ||
| Remote Services: Cloud Management Console | Pivoted within cloud environments using AWS and Azure consoles. | |
| Collection | T1530 | |
| Data from Cloud Storage | Accessed OneDrive, SharePoint, and Slack for sensitive data. | |
| T1213.002 | ||
| Data from Information Repositories: SharePoint | Searched for VPN guides, MFA setup docs, and help desk instructions. | |
| Exfiltration | T1567.002 | |
| Exfiltration Over Web Service: Cloud Storage | Uploaded stolen data to MEGA and other cloud platforms. | |
| T1074 | ||
| Data Staged | Aggregated data in centralized locations before exfiltration. | |
| Impact | T1486 | |
| Data Encrypted for Impact | Deployed ransomware (e.g., BlackCat) to encrypt ESXi servers. | |
| T1657 | ||
| Financial Theft | Extorted victims via double extortion (data leak + encryption). |
Vulnerability chain in the aviation sector
The interconnected nature of the aviation sector carries inherent risk. Between digitized communications and equipment, functions such as air traffic control, maintenance systems, and booking platforms, cybersecurity infrastructure is essential to protecting airline security.
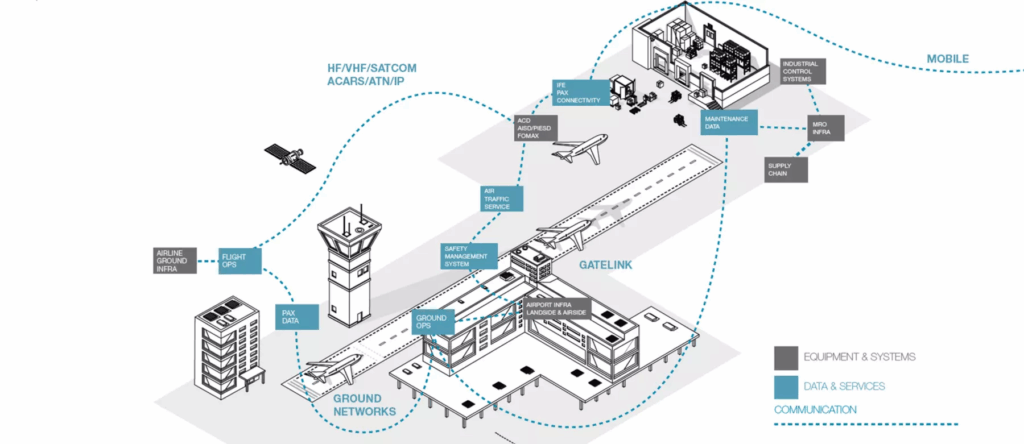
Threat actors target vulnerabilities within IT infrastructure to perform their attacks:
- Wi-Fi connections: Publicly available Wi-Fi in airports and in-flight are vulnerable to attacks. Threat actors can gain access to navigation and air traffic control systems through vulnerable Wi-Fi connections, disrupting daily operations and posing a risk to passengers and staff.
- In-flight entertainment systems: In-flight entertainment is connected with aircraft wiring, providing an opportunity for attackers to gain access. In one documented case, a security expert hacked into the aircraft’s in-flight entertainment system and used an existing vulnerability to steer the aircraft. The breach was the result of default passwords and IDs being used in the Thrust Management Computer.
- Air traffic control (ATC) systems: The interconnected air traffic control systems are crucial for the aviation industry to operate safely. To exploit these systems, hackers find entry points to the system through the interconnected networks linking ATC with airlines, airports, satellites, and weather services. Additionally, outdated software and hardware often lack appropriate modern security protections.
- Satellite navigation (GPS): GPS systems utilize NAVSTAR satellites to direct aircraft, however, the system isn‘t without vulnerabilities. Hackers can perform attacks on SATCOM (satellite communications) by interrupting non-safety communications via Wi-Fi or vulnerable radio frequencies.
- Automatic Dependent Surveillance-Broadcast (ADS-B): The ADS-B, a system aircraft use to identify themselves, however, it’s vulnerable to spoofing when the signals aren’t encrypted or verified, making it easy for attackers to intercept and fake flight data.
What are the main motivations behind aviation sector attacks?
The motivations behind airline cyberattacks are multifaceted. For some hackers, the aim is financial gain, where sensitive data is sold on the dark web.
For others, the motivation is political or ideological. Some cybercriminals are nation-state actors in disguise, performing disruptive activities to cause chaos to adversaries of the state.

In a joint investigation by the CISA and the U.S. Department of Justice, it was discovered that a Russian state-sponsored APT actor targeted dozens of U.S. state government and aviation networks.
The recent 2025 Scattered Spider attacks are suspected to be motivated by financial gains and publicity. The recent success attacking big names from across the globe has brought the group global fame, making it likely they will “rise and repeat” attacks on different sectors.
How can the airline industry mitigate cyber threats?
The FAA in the U.S. and the EASA in Europe have increasingly issued guidelines for the aviation sector to help mitigate rising cyber threats.
Since the COVID-19 pandemic in 2020, phishing attacks against airports and airlines have risen, particularly to steal information, data, and conduct extortion schemes. The EATM-CERT detected 15,493 accounts of 30 airlines that were offered for sale on the dark web, worth over €400,000.
To successfully mitigate risk and stop cyber attacks on airlines, good cyber-hygiene and preventative strategies are necessary.
Prevention
- Use a cybersecurity framework. NIST was developed in the US to help businesses protect themselves against cyber threats. Using the NIST framework can help airlines map the risks inherent in their systems before they evolve into devastating threats.
- Identify and document network asset vulnerabilities. Documenting hardware and software, third-party vendors, and internal and external interfaces is essential to evaluating cyber risk.
- Limit access privileges. Knowing who has access to different systems helps prevent unauthorized access. An activity log of users with granted access can help better track access.
- Use multi-factor authentication (MFA). Security standards such as MFA ensure that only registered users are accessing systems. These preventative measures reduce the likelihood of airline data breaches from threat actors.
- Patch and update systems regularly. When outdated software or hardware is used, hackers can exploit known vulnerabilities, granting them access to systems.
Detection
- Utilize real-time threat intelligence. Using technology to scan and monitor IT environments for anomalies ensures threats are caught before they escalate.
- Use automation. AI technology can predict future threats based on patterns in historical data, helping to stay on top of evolving threats.
- Proactively detect stolen credentials. Notify users as soon as compromised credentials are detected. Credential intelligence platforms such as CybelAngel can also investigate the cause of the breach, helping cybersecurity teams patch vulnerabilities.
Response & recovery
- Create an incident response plan. Responding to a threat quickly ensures that damage is mitigated. The CISA provides a getting-started guide in conjunction with NIST protocols.
- Simulate cyberattacks and train employees. Most cyberattacks are successful because of human error, making cybersecurity training extremely important to preventing future attacks.
- Maintain offline backups of all sensitive data. Backing up sensitive data in offline servers ensures that files won‘t be held to ransom, even if a malware attack is successful.
- Communicate transparently and abide by regulations. In some cases, it’s legally required to report a cybersecurity incident to the proper authorities. ICAO advises reporting threats that could pose a significant risk to aviation safety.
FAQs
- Why has the aviation industry become a prime target for cybercriminals?
The main goal of threat actors is to harvest information for espionage or profit. The aviation industry has a wealth of high-value data that can be sold on the dark web. Operational complexity also ensures that hackers can perform attacks undetected, giving threat actors more security. - What are the most common attack vectors used against airlines?
Phishing and website fraud are the largest attack vectors in the aviation sector, accounting for 70% of all attacks. Although ransomware attacks on airlines and airports are in the minority, hackers do use ransomware to target third-party suppliers. - What are the financial and reputational consequences of a successful cyber attack on an airline? Successful airline cyberattacks carry a burden of financial loss, regulatory fines, and legal claims. In 2024, Delta Airlines experienced a cyber incident that cost $550 million—a steep price to pay for insufficient cybersecurity infrastructure. When sensitive customer data is exposed, it creates reputational damage with further financial losses in future bookings.
- When are hackers likely to attack the aviation industry? Cybercriminals target transport and aviation during peak holiday periods due to the high traffic, low vigilance, and maximum disruption potential. Airline cybersecurity during peak periods is usually strained due to understaffing, making them a target for ransomware, phishing, and DDoS attacks.
- What role do third-party vendors play in an airline’s cyber risk? Third-party vendors play a critical role in airline operations, but also introduce significant cybersecurity risks if the providers are themselves not cybersecurity compliant. Proper vetting of third-party vendors is crucial to combat airport security threats.
- What are the critical first steps an airline CISO should take to map out their external attack surface? Begin mapping your external attack surface by defining the boundaries of all systems, as attackers often use vulnerable endpoints to gain access. Understanding the complexity of your attack surface is crucial to preventing future attacks.
- How can proactive monitoring and data leak detection help prevent flight cancellations and major disruptions? Automating the detection of threats in your attack surface helps airlines predict potential flight delays before they take effect. AI technology can also predict previously unknown factors based on data, mitigating the risk of major disruptions.
Wrapping up
Threat actors have steadily increased cyberattacks on the airline industry over the past 5 years. The plethora of sensitive information the aviation industry has access to, such as credit card information, has caused a surge in phishing and data breach attacks.
Peak season cyber threats during busy holiday periods are on the rise, especially due to the understaffing at airport locations. To combat these rising cyber threats, airlines have to pay close attention to their IT ecosystem, focus on securing airline operations, and better evaluate third-party risk. CybelAngel can help amp up cybersecurity intelligence without the fuss.

