
Dark Web Takedowns in 2023 | An Overview for CISOs
Reviewing the top three dark web takedowns of 2023 will give CISOS clear insights about why these marketplaces were targeted and disbanded by law enforcement teams, and also discover how dark web monitoring can help them stay one step ahead.
An overview of marketplaces and forums: From malware to ransomware
Reviewing dark web forum and marketplaces takedowns is vital when you are in the cybersecurity business.
For law enforcement teams the work of dissolving dark web forums and their main cybersecurity activities is a game of jack-a-mole where concentrated efforts to shutdown marketplaces can result in hackers creating and transitioning a replacement dark web site in days.
Threat actors can use encrypted apps like Telegram, to communicate en masse and share with their hacker network the location of new forums and marketplaces.
How does law enforcement target and takedown cybercriminals?
Cyber crime, criminals, and their technical infrastructure worldwide make international collaboration essential for the authorities.
Authorities split this task into tackling critical cyber incidents and combating the long-term activities of cyber criminals and their enablers on the dark web.
They follow a proactive approach that typically looks like disrupting the cybercrime business model by targeting the specific online ecosystem.
The U.K. National Crime Agency define the cybercrime ecosystem in five key pillars:
- Infrastructure
- Financial services
- Initial access & compromise
- Marketplaces & forums
- The location of victims
One way to see how authorities takedown the marketplace’s criminal infrastructure is to look at the example of intelligence gathering for Operation SpecTor.
“Europol has been compiling intelligence packages based on troves of evidence provided by German authorities, who successfully seized the marketplace’s criminal infrastructure in December 2021. These target packages, created by cross-matching and analysing the collected data and evidence, served as the basis for hundreds of national investigations.” reads the press release published by the Europol. “The vendors arrested as a result of the police action against Monopoly Market were also active on other illicit marketplaces, further impeding the trade of drugs and illicit goods on the dark web.”
Let’s now take a look at a selection of marketplace takedowns that cover a wide range of criminality; malware, stolen data, ransomware, credit card fraud, organised phishing attacks, extortion and more
A look at the dark web marketplace takedowns in 2023 (Plus, what does it mean for your cybersecurity strategy?)
1: Kingdom Market
What did this marketplace sell? Kingdom Market was a darknet marketplace where 42,000 offerings from drugs, criminal services, scams and malware were up for grabs. The announcement was made by German law enforcement that Kingdom Market had “fallen” in late last year after a global takedown operation.
When was this marketplace shut down? December 2023.
Key takeaways for CISOs in 2024:
- The closure of Kingdom Market serves as a testament to the international collaboration and coordination involved in the fight against organized cybercrime.
- Understanding the widespread coordination of malware campaigns on the dark web is important. CISOs can use dark web monitoring tools, like this solution by CybelAngel, to uncover and monitor cybercriminal discussions on dark web marketplaces.
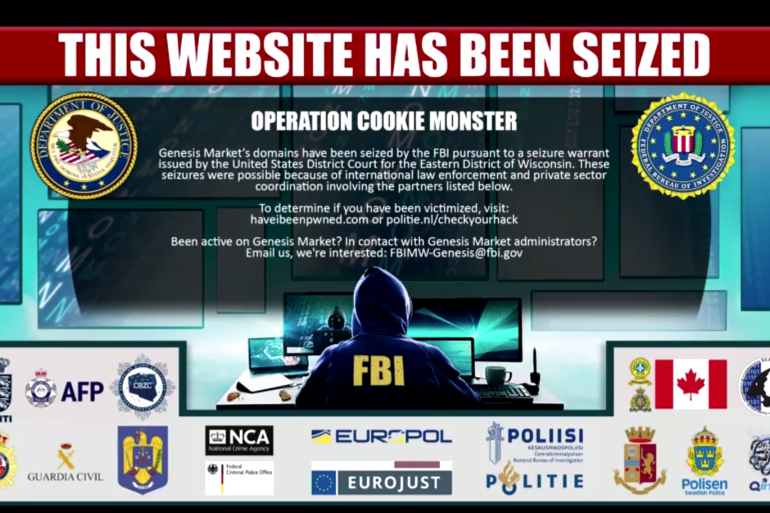
2: Genesis
What did this marketplace sell? Genesis was a marketplace that enabled users to access and share a comprehensive range of illicit login data, facilitating online fraud like credit card fraud, phishing and more. Users there had the opportunity to purchase a variety of critical information, such as passwords, alongside other components of a victim’s “digital fingerprint” like browser history, cookies, autofill form data, IP address, and geographical location
When was this forum shut down? April 2023.
Key takeaways for CISOs in 2024:
- Will Lyne, head of cyber intelligence at the NCA, said Genesis was “an enormous enabler of fraud” and one of the most significant marketplaces for buying login information.
- Shortly after Genesis was taken down in April during “Operation Cookie Monster” a mirror version of the market was hosted on the darknet as reported by the BBC. Cybercriminal users of Genesis were reportedly wary of the new onion site.
- CISOs in turn should be wary. The subsequent mirrored version of the previous site shows how quickly new dark web marketplaces can spring up, ready for round two.
3: Monopoly Market
What did this marketplace sell? Monopoly Market was an illegal dark web marketplace that was mainly used by cybercriminals for illegal activities like buying and selling drugs. This shutdown was coordinated by Europol, together with authorities from nine countries from inside and outside the EU. The operation, codenamed SpecTor sting shut down 288 vendors.
When was this forum shut down? April 2023.
Key takeaways for CISOs:
- Law enforcement conducted the largest international operation against darknet trafficking to date with the takedown of this marketplace. The compiled intelligence from this sting served as the basis “for hundreds of national investigations.”
- The takedown of the Monopoly Market should serve as a lesson to CISOs to the profitability and viability of specialist dark web marketplaces. It was reported that Monopoly collectively earned vendors at least $18 million in revenue. The operator of this marketplace earned a reported $900,000 in commissions.
- CISOs can investigate dark web marketplaces and access in-depth knowledge through RFI, with our dedicated security researchers and Cyber Threats team analysis.
Looking ahead to 2024: CISOS, cybersecurity and the dark web
PwC in their “What’s important to CISOs in 2024” report found that building cyber resilience was a priority for 2024. They found that CISOs are unable to “keep up.” In today’s fast paced dark web climate, they need to pair dark web monitoring with cybersecurity.
We hope that brushing up on missed takedowns and seeing where new threat actors are popping up can help you to quickly keep a pulse on the dark web as a busy CISO looking ahead to 2024.
Two important takeaways for CISOs:
1: Dark web monitoring is essential: Understanding the coordination of malware campaigns and cybercriminal discussions on the dark web is vital for cybersecurity strategies. CISOs can leverage dark web monitoring tools to uncover and monitor these discussions.
2: New marketplaces can quickly emerge: Even after the takedown of prominent dark web marketplaces, replacements can quickly appear. CISOs need to remain vigilant and be aware of the potential for new dark web marketplaces to emerge and adapt their cybersecurity strategies accordingly.
3: Dark web intelligence matters: At CybelAngel we share in-depth Threat Notes with our clients that are prepared by our expert REACT team with our clients to provide contextualized profiles on threat actors, including emerging dark web marketplaces as well as the evolution of key threat actors. You can find out more about these reports and our dark web monitoring services here.
Wrapping up
That is it for this blog.
We take time-consuming guesswork out of cyber threat intelligence.
Here at CybelAngel we share in-depth Threat Notes prepared by our expert REACT team with our clients to provide contextualized profiles on threat actors, including emerging dark web marketplaces as well as the evolution of key threat actors. To find out more, request more information about CybelAngel here.
We hope that part three of this dark web blog series was insightful.
You can can read these published topics in this series:
- What is Dark Web Monitoring?[Plus, How Will it Evolve in 2024?]
- Understanding Dark Web Intelligence: How Cybercriminals Share Intel
Follow our social media pages, LinkedIn and Twitter, to check out fresh content drops in this series, as we take a deeper look at the dark web.