The Global Security Implications of Volt Typhoon

Table of contents
Cybersecurity experts have raised alarms over the growing threat posed by China APT groups as the tensions between the U.S. government and the Chinese government have risen in recent years.
Volt Typhoon, an Advanced Persistent Threat group (APT), came onto the world stage in 2021, seeking to undermine U.S. critical infrastructure and weaken U.S. military readiness in the Pacific in the event of a conflict over Taiwan.
The cyber espionage group focuses on gaining unauthorized credential access through Living-off-the-Land (LOTL) techniques to blend into legitimate system activity and avoid detection.
Let’s examine their tactics and explore strategies to defend against the growing threat of the PRC‘s cyber operations.
Who is Volt Typhoon?
Volt Typhoon, known by the aliases Bronze Silhouette, Vanguard Panda, Insidious Taurus, Dev-0391, and Voltzite, is a cyber-espionage group linked to the Chinese state that has been active since 2021.
The group focuses on undermining U.S. national security, utilizing network device compromise to exploit vulnerabilities in outdated firmware, weak credentials, or misconfigured settings.

Who does Volt Typhoon target?
Volt Typhoon targets U.S. critical infrastructure, including communications, manufacturing, utilities, transportation, construction, maritime, government, IT, and education sectors.
According to the Cybersecurity and Infrastructure Security Agency (CISA) and the NSA, the hacker group has launched attacks on:
- U.S. Department of Energy (DOE)
- U.S. Environmental Protection Agency (EPA)
- U.S. Transportation Security Administration (TSA)
- Australian Signals Directorate’s (ASD’s) Australian Cyber Security Centre (ACSC)
- Canadian Centre for Cyber Security (CCCS), a part of the Communications Security Establishment (CSE)
- United Kingdom National Cyber Security Centre (NCSC-UK)
- New Zealand National Cyber Security Centre (NCSC-NZ)
Experts agree that the choice of targets is not consistent with traditional cyber espionage or intelligence gathering operations—instead, Volt Typhoon threat actors are seeking to gain lateral movement within IT systems to disrupt functions.
Youtube video reporting on Volt Typhoon hacking activity operating in the U.S.
Timeline of activity
Volt Typhoon is unlike other cyber espionage efforts as Volt Typhoon mainly seeks to cause disruption and chaos.
As FBI Director Christopher Wray noted, “China’s hackers are targeting American civilian critical infrastructure, pre-positioning to cause real-world harm*to American citizens and communities in the event of conflict.”
Here‘s a breakdown of Volt Typhoon‘s activity since its inception in 2021:
- 2021: Activity from Volt Typhoon was first noticed in mid-2021, targeting critical infrastructure organizations in Guam and the U.S. The hack focused on communications, manufacturing, utility, transportation, construction, maritime, government, information technology, and education sectors. Behavior observations suggested that the threat actors intended to perform espionage and maintain access without being detected for as long as possible.
- May 2023: Microsoft and the CISA disclose details about Volt Typhoon‘s malicious activity within US critical infrastructure.
- December 2023: Reports indicate Volt Typhoon has targeted Hawaii, Guam, the West Coast, and Texas, focusing on military strategic locations.
- January 2024: The FBI disrupts Volt Typhoon’s botnet, wiping malware from compromised routers used to mask the group‘s cyber espionage activities.
- February 2024: Authorities uncovered a compromised IT environment in Guam, a US territory home to a large US military base. The hack focused on disrupting U.S. infrastructure organizations in communications, energy, transportation systems, and water and wastewater systems sectors.
- March 2024: An investigation led by the “Five Eyes” agencies, an intelligence sharing alliance between Australia, Canada, New Zealand, the United Kingdom, and the United States, confirmed that the People‘s Republic of China (PRC) was seeking to disrupt critical services in places of military importance to the US through the Volt Typhoon cyberattacks.
- June 2024: Volt Typhoon breaches a Singapore-based telecommunications company, SingTel, thought to be a test run for future attacks on U.S. telecom providers.
- **November 2024: **The FBI conducted a court-authorized disruption of Volt Typhoon‘s KV Botnet that infected end-of-life Cisco RV320/325 routers and Netgear ProSafe routers that lacked proper security patches.
How does Volt Typhoon operate?
The group operates using stealthy cyber-espionage techniques, relying on Living-off-the-Land techniques (also called LOTL attacks) instead of malware, making attacks harder to detect.
In the wake of LOTL attacks, the CISA issued an alert (CISA advisory AA23-144A) to spread awareness.
A typical Volt Typhoon attack utilizes the following TTPs:
| Attack Technique/Tactic | Description |
|---|---|
| Exfiltration and data staging | Adversaries transfer stolen sensitive data to an external location, often staging it centrally for easier access. |
| Credential theft | Volt Typhoon steals credentials from target systems using the Local Security Authority Subsystem Service (LSASS). |
| Cracking passwords offline | To remain undetected, Volt Typhoon cracks passwords offline using the command-line tool Ntdsutil.exe to create installation media from domain controllers. |
| Persistence | Hackers maintain system access by routing traffic through compromised small office and home office (SOHO) network equipment, including routers, firewalls, and VPN hardware. |
| Command and Control (C2) | Volt Typhoon establishes C2 channels using customized open-source tools, including KV Botnet malware. |
| Edge devices | Edge device exploitation of routers, IoT sensors, or industrial controllers allows hackers to gain unauthorized access to systems and credentials. |
| Living off the Land (LOTL) binaries | Threat actors use built-in system tools instead of malware to avoid detection. Hands-on-keyboard activity is common. |
| Lateral movement | Hackers explore compromised networks using PowerShell, WMIC, and the ping command, occasionally verifying if they are in a virtualized environment. |
Diving Deep: Volt Typhoon TTPs Analysis
1. Reconnaissance
Volt Typhoon actors conduct extensive reconnaissance before commencing an attack. According to industry reporting, Volt Typhoon actors use FOFA—a Chinese-developed internet asset search engine that indexes devices and services exposed online—to search for already exposed IT infrastructure.
Interestingly, the US authorities found that Volt Typhoon hackers targeted the personal emails of key network and IT staff to fly under the radar.
2. Initial Access
To obtain initial access, threat actors commonly exploit vulnerabilities in legitimate software used by a company, including Fortinet, Ivanti Connect Secure (formerly Pulse Secure), NETGEAR, Citrix, and Cisco.
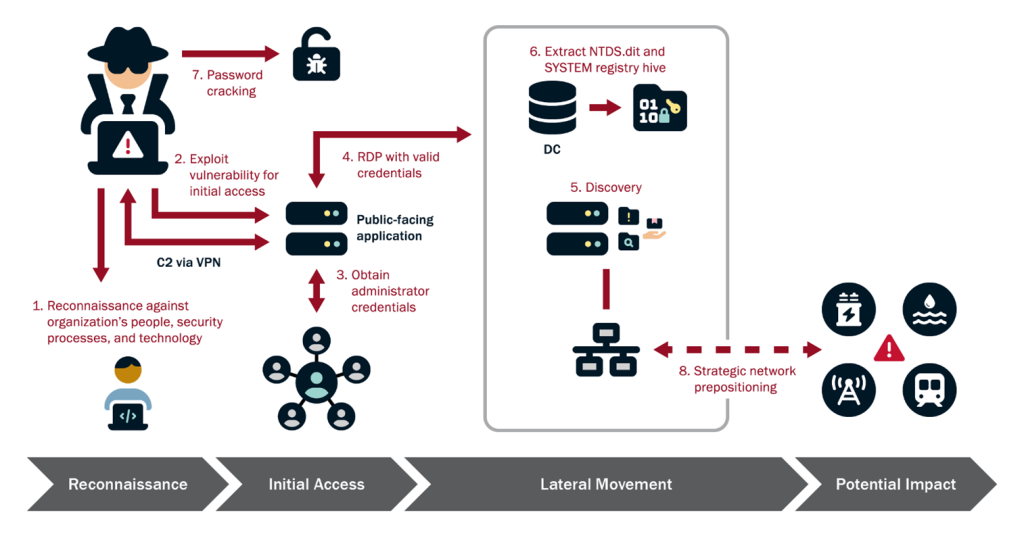
Hackers may use available exploit codes for known vulnerabilities, however, Volt Typhoon has also been known to exploit zero-day vulnerabilities.
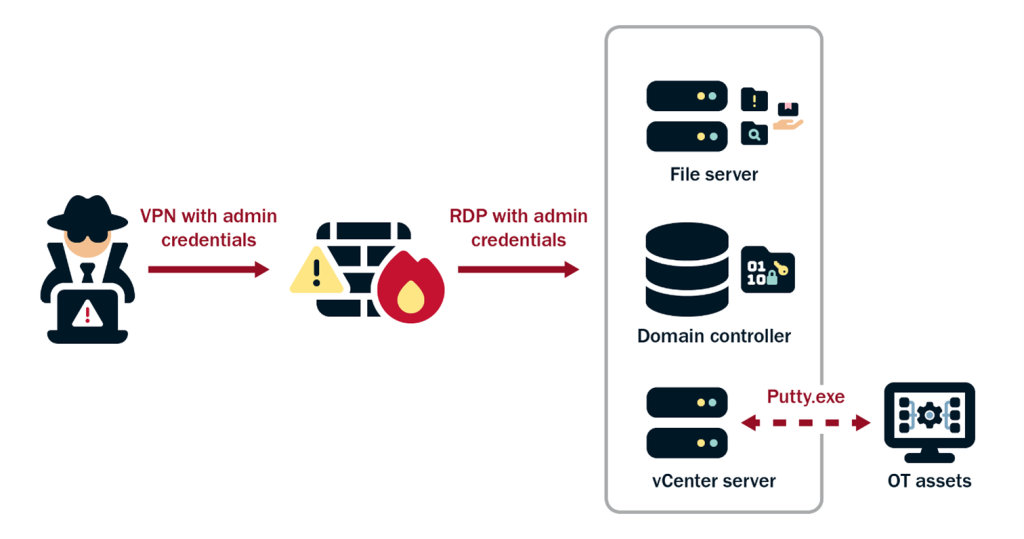
Once the hackers gain access, they shift to establishing persistent access through VPN sessions connected to victim environments to discreetly complete more intrusion activities. This tactic provides a stable foothold in the network while blending in with regular traffic, reducing the chance of detection.
In one confirmed attack, Volt Typhoon actors gained access by exploiting CVE-2022-42475 in a network perimeter FortiGate 300D firewall that had not been patched. Evidence of buffer overflow was found within the Secure Sockets Layer (SSL)-VPN crash logs.
3. Execution
Volt Typhoon differs from many state-sponsored actors as they rarely use malware during a cyberattack. The group instead focuses on hands-on keyboard activity via the command line and other native tools and processes known as Living-off-the-Land (LOTL).
According to Microsoft‘s reporting, commands appear to be exploratory or experimental, with hackers adjusting and repeating commands multiple times.
The PRC state-sponsored cyber group also uses legitimate but outdated versions of network admin tools, providing them a foothold in a network.
In one cyberattack, the hackers downloaded an outdated version of comsvcs.dll a legitimate Microsoft Dynamic Link Library (DLL) file. The actors used this .dll with MiniDump and the process ID of the Local Security Authority Subsystem Service (LSASS) to dump the LSASS process memory and obtain credentials.
In another attack, Volt Typhoon hackers were seen using Magnet RAM Capture (MRC) v1.20 on domain controllers to record the memory. The group extracted sensitive data such as credentials and in-transit data not typically accessible on disk. Additionally, they install Fast Reverse Proxy (FRP) to secretly control infected systems.
4. Evasion
To remain undetected, Volt Typhoon primarily relies on camouflaging its activity through LOTL techniques. Hackers also work hard to hide their activity with more stealthy TTPs.
In one attack, Volt Typhoon obfuscated FRP client files BrightmetricAgent.exe and SMSvcService.exe inside the ScanLine port scanning tool, by compressing them with Ultimate Packer for Executables (UPX)—helping hackers to evade detection.
In another investigation, it was observed that Volt Typhoon selectively clears Windows Event Logs, system logs, and other technical artifacts to further obfuscate their attacks.
Mitigation and detection
To mitigate risk and improve the detection of threat actors, organizations should take proactive security measures as outlined by the CISA and invest in remediation efforts.
X post from the NSA detailing the results of their investigation.
Key steps for Volt Typhoon mitigation include:
- Patch and update internet-facing systems since these are most at risk of exploitation.
- Implement comprehensive logging of all systems in an out-of-band location that cannot be tampered with.
- Use automation to review all logs and detect IoCs (indicators of compromise).
- Restrict administrative privileges to tools such as PowerShell, WMI, and command-line utilities to prevent unauthorized use.
- Plan for APT intrusions with an appropriate incident response plan.
- Protect authorized credentials to stop hackers from gaining unauthorized access.
- Monitor for unusual API calls in cloud environments, especially those involving changes to security groups, configuration of cloud resources, or access to sensitive data.
- Use endpoint detection and response (EDR) solutions to identify anomalies in system activity.
- Enable multi-factor authentication (MFA) across all systems to validate users.
- Enhance network segmentation and monitoring to limit lateral movement possibilities for threat actors.
- Protect edge devices by staying up-to-date with software patches and updates, deactivating functions that are not required, and periodically reviewing end-of-life (EOL) edge devices before EOL occurs.
Enhance Threat Intelligence with CybelAngel
Espionage campaigns pose a real risk to organizations globally due to interconnected supply chains. According to the CISA, tactics such as LOTL are effective because many organizations don‘t implement security best practices that are capable of detecting malicious activity.
CybelAngel can help your organization stay ahead of cyber threats before exploited vulnerabilities become company-threatening.
The fight against cyber espionage is not just about reacting to threats—it’s about staying ahead, anticipating attacks, and ensuring the digital world remains secure.
