What is External Attack Surface Management (EASM) and How Can You Secure It?

Table of contents
Taking Cybersecurity Beyond the Obvious with EASM
In 2005, a group of about 25 people posing as landscapers tunneled into the vault of the Banco Central bank in Fortaleza, Ceará, Brazil, making off with approximately US$71M. It was the largest bank robbery in Brazil’s history and, despite the lack of a cybersecurity breach, it’s also a valuable lesson in external attack surface management. Keep reading, we’ll come back to that. Earlier this year, Gartner® identified external attack surface expansion as the number one trend in cyber security and risk management. However, in conversations with cybersecurity professionals, CybelAngel has discovered that awareness and knowledge around external attack surface varies widely across the industry—differing across geographical regions and organizational maturity. In this article, we’ll take a step back to answer a few baseline questions: What is an external attack surface? If it’s all already external, how can it be expanding? And most importantly…what can you do to secure it?
What is an external attack surface?
While you may find yourself hearing about the external attack surface a lot more lately, it has always been there. It’s all the ways that someone on the outside can find their way inside your business-critical digital systems. Think of the external attack surface as a set of doors and keys: Doors are internet-facing assets such as servers, applications, APIs, domains, IoT devices, cloud buckets, etc. Keys are credentials (often weak passwords or stolen login information obtained via phishing attacks or purchased on the dark web), public APIs and vulnerabilities like misconfigured access points or services that basically leave your doors unlocked. When organizations first begin to focus on protecting their external attack surface, they typically think in terms of their known assets, like those mentioned above (servers, applications, etc.). As their security strategy matures, many progress to addressing shadow IT, which are assets and services that their IT and security teams are unaware of but that are still owned by the organization. Looking solely at those areas, it’s clear how an external attack surface can and will expand just based on an organization’s own internal growth—but that’s not what we’re talking about when we refer to the trending expansion of the external attack surface.
Why is the external attack surface expanding?
At the turn of the century, “cloud computing” was about as familiar as “external attack surface” is right now. It had existed in concept for decades but the technology really began to take off about 15 years ago, improving, evolving and gaining prominence at an astonishing rate. Cloud computing had already put organizations on a path to rapidly-increasing globalization and decentralization of operations…and then COVID-19 happened and the decentralization of systems also became a decentralization of people and workplaces in ways and at speeds never seen before. This is why the external attack surface is now receiving more attention and concern. It’s not that attack surfaces were static before but now, between the cloud and the pandemic, their growth has gone from slow and predictable to explosive and unpredictable. Your external attack surface isn’t just your own anymore—it’s the extended attack surface of your entire ecosystem of suppliers, distributors, partners and vendors who, in turn, bring along their own supply chains with varying levels of maturity in security practices. Their threats are now your threats. It’s a vast spiderweb and it’s easy to see why it can be so hard to control. Simply carrying out routine business with other companies will increase risks in your own systems and processes. For example, CybelAngel recently found airline passengers’ personal information exposed—not by the airline itself, but by a third-party flight comparison website.
How can you secure your extended external attack surface?
Doors are inherently a security risk but an attacker typically needs the keys in order to compromise a system. IBM’s recent Cost of a Data Breach report found that compromised credentials (19%) and phishing (16%) are the top two attack vectors, and that ransomware attacks have grown more frequent and costlier, averaging $4.54M per breach. Despite the unimaginable size of the external attack surface these days, securing it may seem deceptively straightforward: Make sure you’ve locked all the doors and stowed the keys safely away. But the thing is…what if you don’t know that a door is a door? To an attacker, a door is not just “the thing with a handle and a lock,” it’s any exploitable weakness. At Banco Central in Brazil, the “door” was the floor. This is the lesson of the Fortaleza bank robbery: You have to think like an attacker. In order to secure the extended external attack surface, you need to go beyond perimeter-centric defenses, beyond the obvious. This means adopting an outside-in approach with External Attack Surface Management (EASM). EASM is the practice of continually seeking out and addressing possible exposures (doors) that cybercriminals could use to access your digital ecosystem. It would be nice to think that EASM can be accomplished with diligence and firm business processes, but securing digital technology requires digital technology—and securing today’s hyper-complex, decentralized global business operations requires technology with specific capabilities.
What to look for in EASM systems
The goal of EASM is to eliminate blindspots and achieve full visibility of all your digital assets with a continuously updated inventory—i.e., to make sure you know where all the doors are, and that they’re closed and locked. An EASM solution should continuously monitor and detect exposures on your extended external attack surface, which includes both the assets you own as well as assets of yours that appear in your third-party ecosystem. It should provide you with timely, high-quality alerts—actionable and prioritized by criticality, with full contextual detail about the exposure, so your security team can immediately start remediation efforts before any damage is done. The solution should have a full suite of tools to handle critical security risks such as credentials leakage, typosquatting threats, or intellectual property exposure, to fully prevent multi-vector cyberattacks. Key focus areas should include:
- Vulnerable shadow IT
- Publicly accessible sensitive data
- Critical credential leaks
- Malicious domains that are often used for phishing attacks
- Dark web activity
The image below provides additional detail on what to look for in an EASM solution: 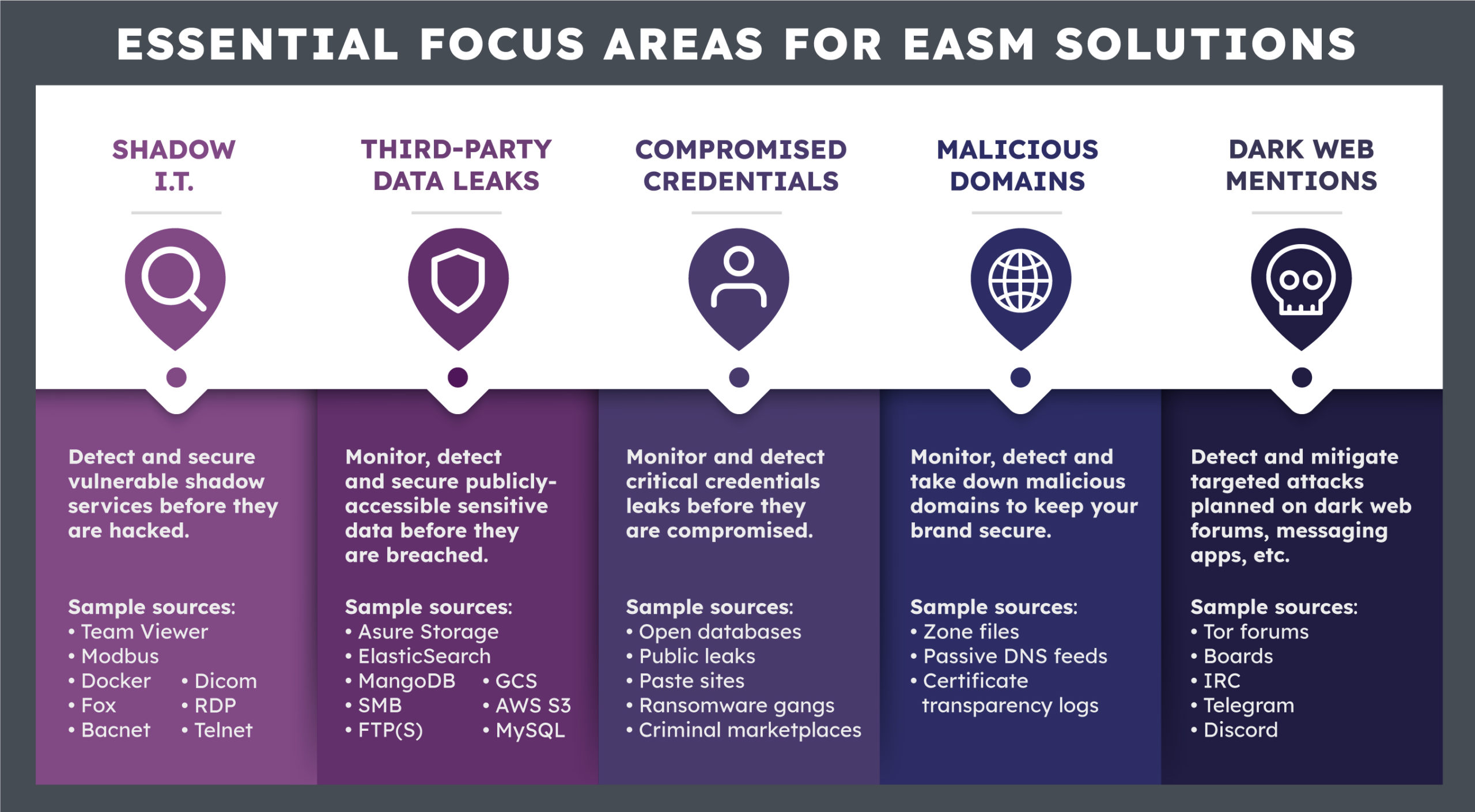 Your company has doors, both real and hypothetical—and they’re not always where you think they are. Cybercriminals know how to find the most unlikely doors and the most unsecure keys, but with the right EASM solution, you can ensure issues are remediated before malicious actors can take advantage of them.
Your company has doors, both real and hypothetical—and they’re not always where you think they are. Cybercriminals know how to find the most unlikely doors and the most unsecure keys, but with the right EASM solution, you can ensure issues are remediated before malicious actors can take advantage of them.
Wondering if your organization has some open doors? Find out in just three business days with CybelAngel’s complimentary External Exposure Scan.