
How to Prevent DNS Attacks
Why are DNS attacks so dangerous? And more importantly, how do they rank in the threat landscape?
Complexity is the order of the day in today’s cybersecurity landscape. CISOs face a myriad of threats that can compromise their organization’s digital assets, reputation, and bottom line. One of the most critical areas of concern is the Domain Name System (DNS).
This is not a concern for no reason.
The DNSFilter Annual Security Report for 2024 noted significant increases in detections across various threat categories compared to 2022. These included a 32% increase in botnet detections, 40% increase in malware detections and a 106% increase in phishing detections. What is more is that data showed a shocking 1250% increase in blocks for new malicious domains registered within 24 hours.
Today let’s explore the four basic types of DNS attacks and six core best practices to prevent DNS attacks.
Looking to learn more about DDoS attacks? Read our sister guide, “How to Prevent DDos Attacks.”
What is a DNS attack?
A DNS attack is a type of cyber assault that targets the Domain Name System (DNS), a key component of the internet infrastructure. It is responsible for translating human-readable domain names into machine-readable IP addresses.
In short, DNS acts as the phonebook of the internet. With the DNS, users can easily navigate to their desired websites without memorizing complex numerical IP addresses.
Before DNS attacks occur, cyber attackers must have exploited vulnerabilities in the DNS protocol or infrastructure. Usually, DNS attacks can have various objectives. These include redirecting traffic to malicious websites, intercepting sensitive data, or overwhelming DNS servers to cause service disruptions. These attacks can be highly sophisticated and difficult to detect, making them a significant threat to organizations of all sizes.
What does a DNS attack do?
Reports from the survey conducted by the Neustar International Security Council (NISC) show that 72% of global organizations have been exposed to domain name system (DNS) attacks in the past 12 months.
In fact, 61% of the affected organizations were targeted multiple times, while 11% were victimized regularly, leading to a loss of around $924,000, according to the 2020 Global DNS Threat Report.
DNS attacks can also lead to:
- Data theft
- Erosion of trust with customers
- Issues with service providers
- Reputation damage
- Website and general internet traffic downtime
- Malware infections
What is the purpose of a DNS attack?
Put simply, a DNS attack compromises the integrity, availability, or confidentiality of the targeted DNS infrastructure. Attackers can achieve a range of malicious goals, including stealing sensitive information, redirecting traffic, disrupting services, and concealing malicious activities.
However, DNA consists of two separate components: authoritative servers (answer-hosting) and recursive servers (answer-finding). While attacks against authoritative servers may include reconnaissance, unauthorized updates, and subdomain attacks, attacks against the recursive services may range from DNS cache poisoning (DNS spoofing) to NXDOMAIN and Phantom Domain.
A successful DNS attack can have devastating consequences. As a CISO, you must prioritize DNS security and implement robust measures to prevent, detect, and respond to these threats.
How is DNS used by hackers?
Hackers can use DNS to facilitate attacks in various ways, such as amplification, tunneling, and DNS hijacking.
DNS amplification attacks are a type of DDoS attack, also known as a distributed denial of service. During one a hacker exploits vulnerabilities in DNS servers. This the amplifies the volume of internet traffic directed at a target, thus maximizing the impact of the attack.
DNS tunneling is an attack where a hacker bypasses security measures and exfiltrated data or establishes covert communication channels. They do this by encapsulating malicious traffic within legitimate DNS queries.
DNS hijacking, also known as domain theft, is simply the act of compromising DNS servers or manipulating DNS records. An attacker achieves DNS hijacking by gaining control of a domain name by stealing the login details of the owners. This then redirects internet traffic to malicious websites or intercept sensitive data.
Why should you care about the security of your DNS?
Companies worldwide manage hundreds or even thousands of domain names. Domain protection is big business.
But why?
Well the devastating consequences of DNS attacks are not to be underestimated, even amongst tech giants like Google.
In October 2023, Google mitigated the largest DDoS attack to date, peaking above 398 million rps. They noted in their blog detailing this incident that in terms of scale,“…This two minute attack generated more requests than the total number of article views reported by Wikipedia during the entire month of September 2023.”
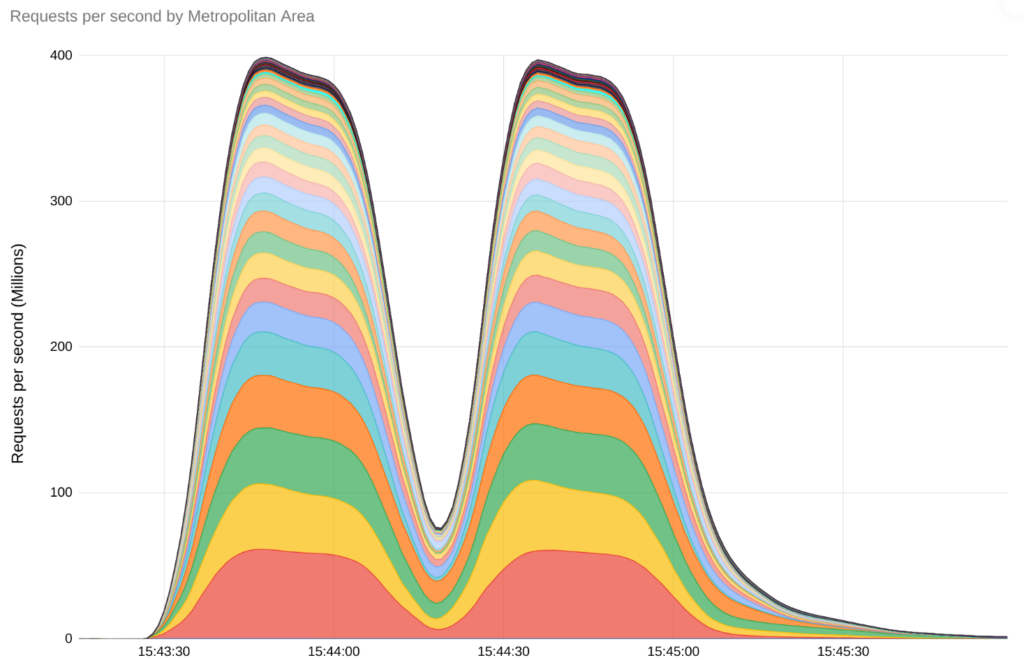
Beyond the classic cyberattack related technical disruptions, like load balancing and maintaining network security, the potential impacts of DNS attacks infect every aspect of your business.
What are some of the potential impacts of DNS attacks on your organization? Plus why you should care.
- Financial losses: DNS attacks can lead to significant financial losses. As stated in the IDC report, you could lose a considerable amount of money from service outages, lost productivity, and the costs associated with incident response and remediation.
- Data breaches: Compromised DNS infrastructure can enable attackers to intercept sensitive data. This could lead to costly data breaches and potential legal liabilities.
- Reputational Damage: Successful DNS attacks can erode customer trust and tarnish your organization’s reputation. Once you’re unable to build a solid reputation as an organization, you could lose business opportunities and a competitive disadvantage.
4 common types of DNS attacks
There are four common types of DNS attacks. As chief information security officers (CISOs), you must know the various types of DNS attacks to effectively defend your organization’s DNS infrastructure.
Let’s review these 4 common types of attacks and how they can affect your online presence.
1: DNS tunneling
DNS tunneling is a technique that allows attackers to bypass security measures and firewalls by encapsulating malicious traffic within legitimate DNS queries. This enables them to exfiltrate data, establish covert communication channels, or deliver malware payloads. Specifically, attackers perform DNS tunneling by gaining access to a compromised system, internal DNS server, domain name, and the authoritative DNS server.
To mitigate the impact of DNS tunneling, you must implement strict DNS query filtering and validation. In addition, you’ll also need to actively monitor DNS traffic for anomalies and suspicious domain names and restrict outbound DNS traffic to authorized DNS servers.
2: DNS Hijacking
Also known as domain theft, DNS hijacking is a type of attack that involves gaining control of a domain name through malicious means. In DNS hijacking, the DNS servers are usually the first component to be compromised. In other words, the DNS records are manipulated to redirect traffic to malicious websites. Primarily used to steal sensitive information (login credentials), DNS hijacking can also be used to distribute malware and conduct phishing attacks.
For instance, the “Sea Turtle” cyber espionage campaign in 2019 targeted various organizations, including telecommunication and government agencies in the Middle East and North Africa.
How was this DNS hijack conducted?
The attackers simply hijacked the DNS services of these organizations and redirected users to actor-controlled servers. Access to these DNS records was possible as the threat actors compromised the registrars and registries to modify existing records and direct legitimate users to spoofed websites where their credentials were readily harvested.
3: DNS Flood Attacks
A DNS flood attack is a type of Distributed Denial of Service (DDoS) attack that floors DNS servers with a high volume of malicious DNS queries in an attempt to disrupt DNS resolution for that particular domain.
Think of DNS servers as phonebooks. If a user is unable to find the DNS server, it’ll be impossible to look up the address in order to request a particular resource. Once the DNS resolution is destroyed through a DNS flood attack, the website and API are compromised.
In fact, it also affects the ability of a website to respond to legitimate internet traffic. Due to their large volume of traffic, it could be difficult to differentiate flood attacks from normal heavy traffic as the traffic always comes from a multitude of unique locations.
What does a DNS flood attack do?
DNS Flood attacks simply query the website or API for accurate records on the domain, thereby mimicking legitimate traffic. For example, in September 2016, the Mirai botnet launched a massive DNS flood attack that temporarily crippled several high-profile services, such as Dyn, a major DNS provider. This flood attack disrupted access to popular websites like Reddit, Twitter, and Netflix for several hours.
4: DNS Spoofing
Also known as DNS cache poisoning, DNS spoofing is a type of DNS attack where an attacker exploits vulnerabilities in the DNS server’s cache. Basically, the DNS server is manipulated to redirect traffic from a legitimate website to malicious ones.
The process begins when the threat actor sends fake DNS responses to the DNS server, with the objective of tricking it into caching the wrong IP address in place of an authentic domain name. When users attempt to lookup the authentic website, they are redirected to the fake website created by the attacker, which entirely mirrors the original website.
What happens during a DNS spoofing attack?
With DNS spoofing or cache poisoning, the attackers are able to gain access to malicious information from the users, including their login credentials, credit card details, and personal identifiable information (PIN).
One of the most notable DNS spoofing attacks this year so far was in March 2024. In March 2024, cybercriminals launched a large-scale DNS spoofing campaign targeting financial institutions and their customers. The attackers were able to poison DNS caches and redirect users trying to access legitimate banking websites to fake phishing sites designed to steal login credentials.
Cybercriminals launched a large-scale DNS spoofing campaign targeting financial institutions and their customers.
he attackers were able to poison DNS caches and redirect users trying to access legitimate banking websites to fake phishing sites designed to steal login credentials.
How to prevent DNS Attacks: 6 best practices to get behind
There’s no doubt about it. DNS attacks can have severe and devastating consequences, especially for the cloud environment, which solely depends on DNS to connect users across apps, services, and applications.
Implementing best practices to improve the overall defense of your organization’s network and operating system is not just smart, but necessary.
Here are six best practices to secure your networks and operating systems:
1: Implement DNS Security Measures:
According to Gartner, DNS security is an indispensable measure to improve the defense of your network. In fact, it is one of the reasons protective DNS now exists as a key measure to protect your cloud environment against network threats.
2: Deploy Domain Name System Security Extensions (DNSSEC)
As a DNS security measure, you can protect your system by deploying Domain Name System Security Extensions (DNSSEC) to ensure the integrity and authenticity of DNS data, thus preventing DNS spoofing and cache poisoning attacks. In addition, DNS filtering and validation mechanisms can help detect and block malicious DNS queries, such as those used in DNS tunneling attacks.
3: Enable multi-factor authorization
You can prevent unauthorized access or changes to all your DNS management interfaces and domain registrars. This can also block domain hijacking attacks.
4: Implement regular monitoring and auditing DNS infrastructure
Continuously monitor DNS traffic for anomalies, suspicious domain names, and patterns that may indicate ongoing attacks or compromised systems. Therefore, it could inform your cloud security team to launch mitigation and arrest the DNS threat as soon as possible.
5: Review your DNS configurations regularly
Conduct regular reviews on DNS configurations, DNS zone files, and records to identify unauthorized changes or potential misconfigurations that attackers could exploit. Logging and alerting mechanisms as part of regular monitoring of your infrastructure can help detect and respond to DNS-related security events promptly and in a timely manner.
6: Incorporate DNS attacks planning into your incident response
Another surefire way to protect your systems from DNS attacks is by developing and maintaining an incident response plan. This could be tailored to address DNS attacks, outline roles and responsibilities, and step-by-step procedures to contain, investigate, and recover.
Bonus: Effective communication channels
Robust communication channels and protocols should be established to properly coordinate with internal stakeholders, providers, team members, external partners, and other relevant authorities. In the event of DNS attacks, remember to test and update your incident response plan through simulations. That way you will ensure its effectiveness and identify possible areas of improvement.
Following these best practices, you can significantly reduce the risk of your cloud environment falling victim to random DNS attacks.
Apart from that, these measures will help protect your organization’s key digital assets, offset vulnerabilities to ensure that you avoid cyberattacks.
Protect your external attack surface with CybelAngel
With CybelAngel, you can enjoy the peace of mind that comes from our EASM solution designed specifically to protect your business from external attacks. Request a demo today to see how our platform works.