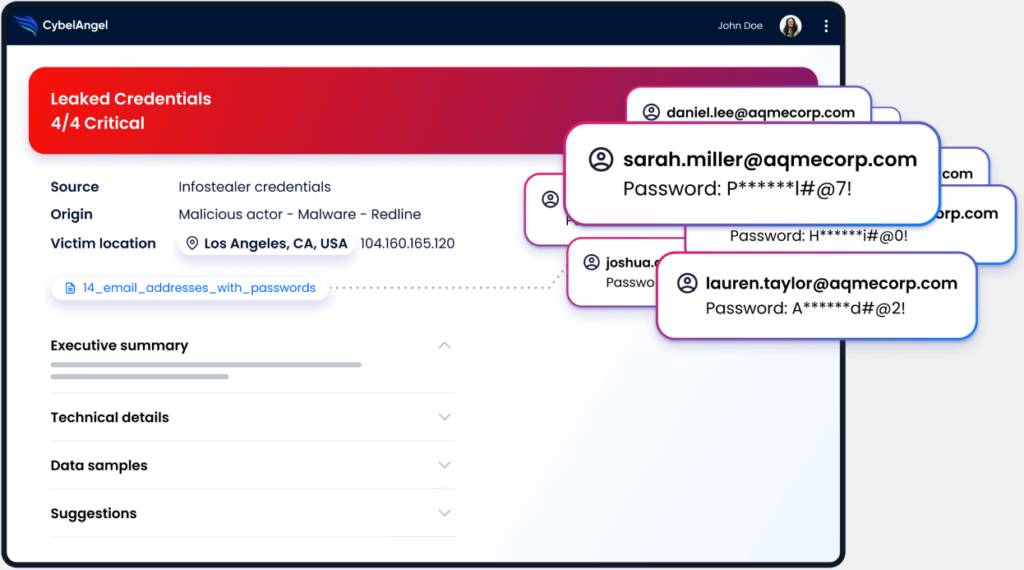
In today’s evolving work environments, companies face significant challenges in detecting compromised or stolen credentials. Verizon’s 2025 Data Breach Investigations Report found that human factors were involved in around 60% of data breaches, including phishing, stolen or misused credentials, and routine user errors—confirming that people remain a major contributor to security incidents.
CybelAngel’s Credential Intelligence solution continuously scans the internet to detect compromised credentials through three key methods: