US Tax Season Equals BEC Attacks

Table of contents
Tax season creates ideal condition for phishing attacks
The Tax Man cometh — and so do cybercriminals. When there is a high volume of private data transmitted, cybercriminals increase their attacks. So, right now before U.S. taxes are due, the probability is high that cybercriminals will phish for sensitive data via email. An Egress report shares that 95% of IT leaders surveyed say that company data is at risk on email; and 83% of organizations have suffered data breaches via email in the last 12 months. Clearly organizations do not want to be fooled by cyber attackers more than once. These days one of the most prevalent cyber attack is Business Email Compromise (BEC), which is a cyber attack designed to gain access to business data or to extract money via email fraud. 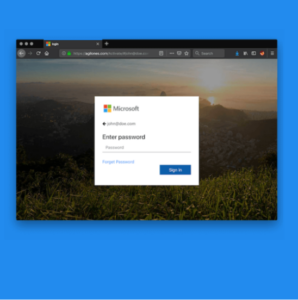 The FBI warns that in BEC attacks, hackers are targeting users of Office 365 and Google G Suite. The most prevalent bait used in phishing emails is Microsoft Office. In fact, Microsoft lures are in half of the phishing emails used to steal credentials. The goal? Cybercriminals are seeking account access or account credentials. These phishing lures include emails that look like they are part of the Microsoft Office 365 enterprise lineup and the Teams collaboration platform. These emails attempt to fool users into inserting account credentials into a fake login screen (see image at right) or fool users into clicking on links that download malware. Did you know that SSL no longer indicates a safe site? The Phishing Activities Trends Report shares that 80% of phishing sites examined in late 2020 used SSL. Criminals up their game every day to fool people. With phishing on the rise, the most common form of business email compromise is invoice or payment fraud. Those who are responsible for email threat mitigation know that phishing conditions are ideal during tax season to steal sensitive data. Plan your defense for this year’s phishing season. Look for these common attacks to business email.
The FBI warns that in BEC attacks, hackers are targeting users of Office 365 and Google G Suite. The most prevalent bait used in phishing emails is Microsoft Office. In fact, Microsoft lures are in half of the phishing emails used to steal credentials. The goal? Cybercriminals are seeking account access or account credentials. These phishing lures include emails that look like they are part of the Microsoft Office 365 enterprise lineup and the Teams collaboration platform. These emails attempt to fool users into inserting account credentials into a fake login screen (see image at right) or fool users into clicking on links that download malware. Did you know that SSL no longer indicates a safe site? The Phishing Activities Trends Report shares that 80% of phishing sites examined in late 2020 used SSL. Criminals up their game every day to fool people. With phishing on the rise, the most common form of business email compromise is invoice or payment fraud. Those who are responsible for email threat mitigation know that phishing conditions are ideal during tax season to steal sensitive data. Plan your defense for this year’s phishing season. Look for these common attacks to business email.
Common BEC attacks
When cybercriminals attack via business email, they are usually looking for account credentials or to steal your organization’s money. So it makes sense that four of the most common BEC attacks involve money transactions. Educate employees to be wary of these common BEC attacks.
- Payroll Diversion. Criminals will send fraudulent emails to employees requesting to change direct deposit info from a legitimate employee’s bank account to a criminal’s account or to a pre-paid card.
- Mergers and Acquisitions Fraud. In this scenario, criminals pretend to be an executive of the victim’s company and request that funds be transferred to a third party.
- Supplier Invoicing. In this instance, a criminal will try to appear as if they are a vendor that your company already does business with and send a request to update bank information for payment of outstanding invoices. This type of scam can lead to the highest losses because they involve paying large dollar amounts to suppliers.
- Gift Card Scam. Criminals in this scenario will pose as an employee with authority and send an urgent email requesting assistance to purchase gift cards and send serial numbers so the gift cards can be sent right away.
Popular attack vectors
The goals may be similar, but attack vectors vary when it comes to BEC attacks. Popular techniques used to compromise accounts include the following:
- Credential re-use attacks
- Malicious attachments
- Man-in-the-middle attacks (when a criminal covertly modifies chats between two people)
- Social engineering attacks
- Spear phishing
Common victims for BEC attack
We have discussed that account compromise is the common goal of attacks via business email. The victims of business email compromise are usually one of these:
- CEOs and management
- Company financials
- Account compromise
Compromised credentials can lead to account takeover, which is one of the most damaging forms of BEC attacks. Account takeover involves using phishing emails to hack an executive or employee account and then using those qualifications to request invoice payments to vendors. To avoid account takeovers, see our blogpost, How to stop account takeovers before they start. In this blogpost, we recommend these steps to avoid account takeover:
- Set up multi-factor authentication
- Do not open emails from people you do not know
- Use a URL scanning service to test the veracity of links
- Train employees about cybersecurity
- Monitor for exposed employee email addresses and passwords
Take precautions to prevent falling victim to BEC attacks. If you suspect account compromise, contact CybelAngel and ask about our Account Takeover Prevention service. And be sure to ask for a free cybersecurity assessment. Find out for yourself how much of your data is easily available and vulnerable to attack. Top organizations around the world rely on our threat prevention services — and so can you. With CybelAngel, companies get ahead of criminals before their networks are attacked via business email. Whatever the email system used, CybelAngel can detect and secure compromised accounts. We can’t keep the tax man away, but we can keep your business email safe 365 days a year, even during phishing season. Because data leaks are inevitable; but with CybelAngel, damage is optional.