Keymous+: The Hacktivist Collective Redefining DDoS Warfare

Table of contents
Emerging in 2023 and expanding rapidly between February and September 2025, Keymous+ is making waves globally.
The self-titled hacktivst collective is known for its crippling Distributed Denial of Service (DDoS) attacks across a wide variety of industries and geographies.
Their cyber attacks emphasize scale and obfuscation, often involving thousands of sources, widespread IP/ASN spoofing, and the use of DNS amplification techniques to maximize bandwidth, making attribution increasingly difficult.
Let‘s dive into the world of Keymous+ to better understand how they operate, who they‘re targeting, and what they‘re aiming to achieve.
Who is Keymous+?
Keymous+ is a hacktivist group that emerged in 2023. However, in 2025, the North African hackers increased their frequency of attacks.
Over 700 DDoS attacks globally were self-attributed to Keymous+, with victims in France, India, Morocco, the UAE, Israel, Sudan, and Saudi Arabia. However, only 249 of those attacks have been independently confirmed.
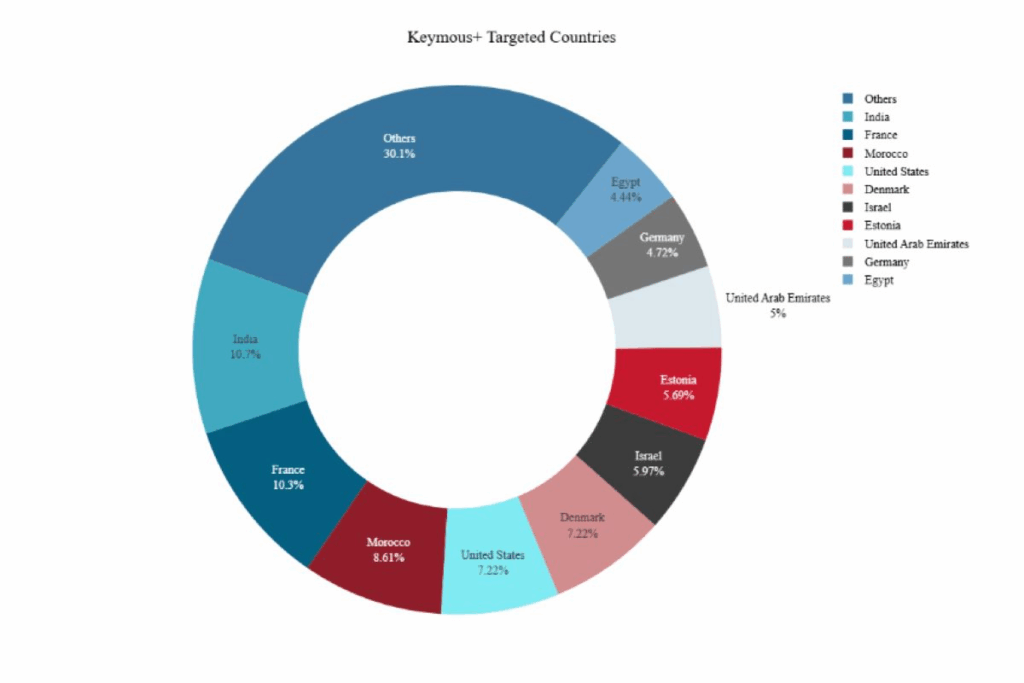
Government entities comprise 27.6% of their targets, making them the primary focus of Keymous+ operations, while Telecoms (10%) and Financial services (6.5%) are the next most-targeted sectors.
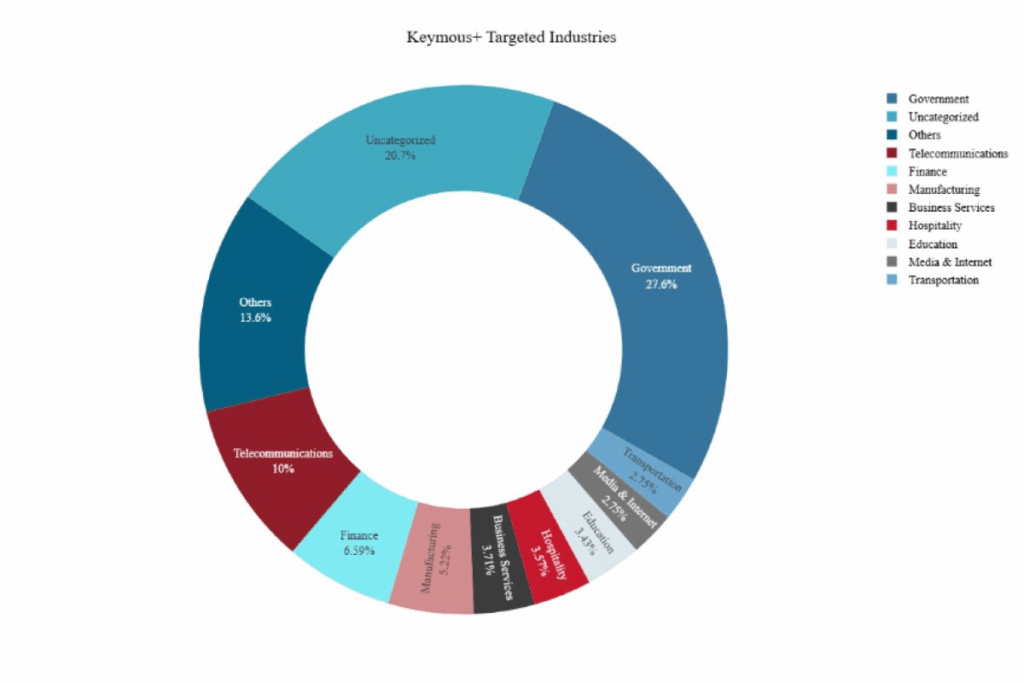
It‘s clear that the group goes after high-value targets to cause maximum damage. The threat actor profile performed by NETSCOUT underlines the opportunistic nature of attacks, while the concentration of attacks in the Middle East and North Africa suggests geopolitical motivations.
What are their motivations?
Despite being a hacktivist group, Keymous+ has a clear lack of ideological consistency. They espouse slogans like “Hack for Humanity”, aligning with other popular hacktivists such as #OpIndia and #OpIsrael, but act contrary to any supposed beliefs. For this reason, analysts have classed them as opportunistic hackers.
How is the group organized?
According to Telegram threat intelligence, Keymous+ has a unique setup, different from many other hacker groups.
The Keymous+ team is comprised of:
- “Alpha Team” is in charge of data breaches and leaks, although in recent months, they have been observed as inactive.
- “Beta Team” focuses exclusively on DDoS attack operations.
Keymous+ threat actors are therefore more effective, separating their workforce to get more done in less time.
The Keymous+ approach: EliteStress and DDoS-for-hire
Keymous+ cyberattacks are one prong of their approach. As hybrid threat actors, they not only launch attacks but also sell commercial products to prop up their activity.
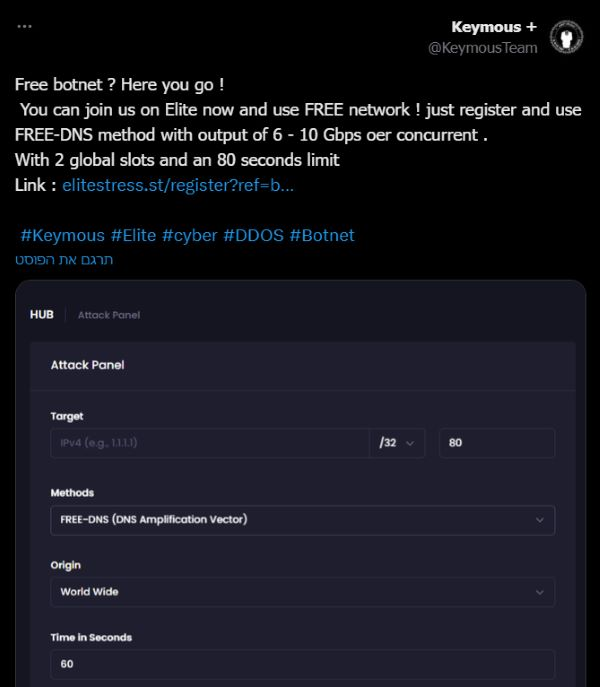
EliteStress, a supposedly self-made platform that features a comprehensive attack panel, makes it easier for threat actors to bypass modern DDoS protection systems. Although the group doesn‘t publicly admit to ownership, they do advertise the service on Telegram and X to attract new users.
The pricing for the platform ranges from €5 per day to €600 per month, making it affordable for most hackers.
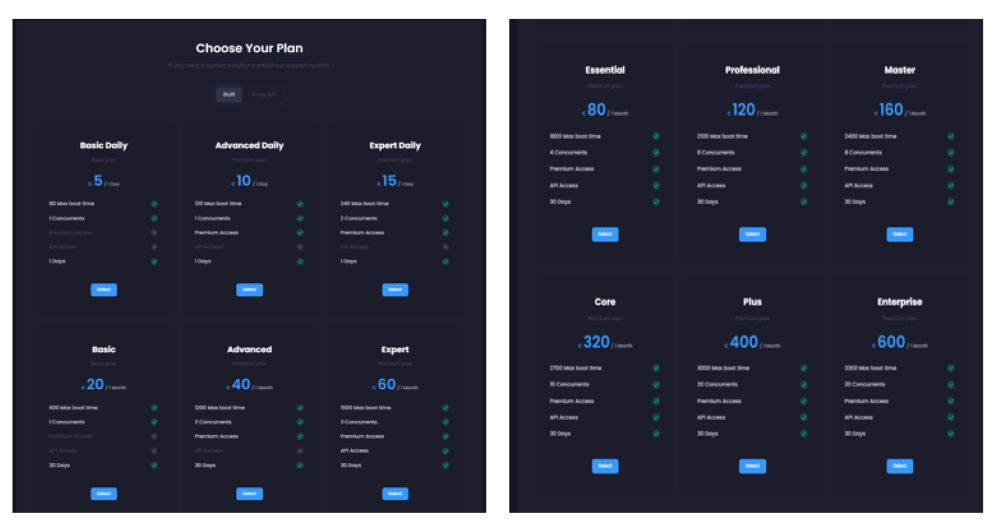
What does EliteStress do? Apart from providing DDoS-for-hire services, the platform also:
- Includes DNS amplification attack infrastructure, helping threat actors leverage public DNS servers to amplify traffic volumes.
- Can perform User Datagram Protocol (UDP) flood attacks targeting specific ports and protocols.
- Provides advanced HTTP/2 flood techniques that can overwhelm web servers with legitimate-looking requests.
- Allows spoofed SSH or ICMP traffic to execute brute-force attacks while evading attribution.
EliteStress boasts stable performance, with bots, tools, and connections to external platforms. Telegram handles like “Join_Elite” try to draw new users in by sharing discounted services or integration with Telegram bots.
Partnerships with other hacker groups
The launch of EliteStress attracts cooperation with other hacktivist entities—leveraging each other‘s skills and geography to launch grand-scale attacks. Experts suggest that collaborations may also serve as marketing opportunities to promote shared infrastructure.
According to open-source intelligence, Keymous+ has been linked to other threat actor groups such as NoName057(16), DDoS54, Mr Hamza, AnonSec, Rabbit Cyber Team, Hunter Killerz, and Moroccan Dragons.
In one case, the Keymous+ group joined forces with other hackers to launch “Red Eye Op.” However, little information about this operation is public.
Keymous+ TTPs: Case studies and attack methods
Many of the alleged methods used in Keymous+ cyberattacks are speculative and require further confirmation from independent sources.
The TTPs used by Keymous+ are as follows:
| Tactic | Technique | Procedure | Explainer |
|---|---|---|---|
| Resource development | T1583 Acquire Infrastructure | Use of DDoS-for-hire services | Leverages EliteStress, a DDoS-as-a-Service platform. |
| Initial access | T1190 Exploit Public-Facing Application | Targeting web vulnerabilities | Exploits vulnerabilities in public facing web applications to intiate DDoS attacks, verified via Check-Host.net. |
| Execution | T1569 System Services | DDoS attack execution | Deploys EliteStress to flood target systems with traffic, disrupting the availability of websites and services. |
| Command-and-Control (C2) | T1071 Application Layer Protocol | Telegram-based coordination | Uses Telegram to coordinate attacks, select targets, and provide proof of attacks. |
| Collection | T1596 Search Open Technical Databases | Reconaissance via Check-Host.net | Employs Check-Host.net to verify target downtime and share evidence, enhancing visibility and credibility. |
| Impact | T1498 Network Denial of Service | High volume DDoS attacks | Conducts DDoS attacks against high-visibility sectors. |
| Exfiltration | T1537 Transfer Data to Cloud Account | Data sharing via Telegram and X | Shares attack outcomes and proof-of-distribution on Telegram and X, recruiting support and publicizing impact. |
| Collaboration | T1588 Obtain Capabilities | Alliances with hacktivist groups | Partners with other hacker collectives including, NoName057(16), DDoS54, Mr Hamza, AnonSec, Rabbit Cyber Team, Hunter Killerz, and Moroccan Dragons. |
Observed attack vectors for Keymous+ attacks include:
- DNS amplification: Threat actors exploit misconfigured DNS servers to amplify traffic volume against targets.
- UDP floods: High-volume floods using UDP packets are used to overwhelm bandwidth and services.
- TCP SYN floods: Attackers send massive SYN requests to exhaust server resources.
- Layer 7 HTTP floods: Application-level floods target websites and APIs.
- Collaborative botnet attacks: Hackers partner with other groups to scale up attacks.
- IP/ASN spoofing: IP source addresses or the network ID are falsified, obfuscating traffic origins.
- Website defacement: Targets government and institutional websites to cause humiliation.
- Opportunistic data exfiltration: While there is limited evidence, some DDoS campaigns suggest data theft.
- Psychological operations: Social media platforms such as Telegram and X are used to amplify impact and claim responsibility.
To better understand the hacktivist collective, let‘s delve into the latest news from observed attacks throughout 2025.
1. German banks, companies, and government authorities’ sites go down after DDoS attack
Working together with prolific Russian hackers NoName057(16), Keymous+ used their expertise to take down several key German websites in April 2025. Sites affected included the web portal for the federal and state government, the federal tax office, the Bavarian state bank, and multinational corporation Lidl.
2. Telecoms disrupted across France
In July 2025, Keymous+ claimed responsibility for a DNS amplification attack against telecom providers in France. The hacktivists overwhelmed the telecom‘s services by exploiting misconfigured DNS servers. Claimed victims included SFR, the second-oldest mobile operator, and Bouyges Telecom, the third-oldest operator in the country.
3. Sudan hacktivism affects critical infrastructure across the country
In August 2025, the hacktivist collective went after Sudan, focusing on government and critical infrastructure. Websites affected included the Federal Government, the Ministry of Finance, the Sudan Railway Corporation, the Taxation Chamber, and Sudatel Telecom Group. The motivation of the attack seems to be bringing an end to the current civil war.
4. Disruption to government services in Morocco
In September 2025, Keymous+ claimed to have attacked government websites in Morocco, including the Ministry of Health and Morocco‘s National ID Portal. However, third parties have yet to confirm this attack.
5. Hacktivists disrupt Pakistan during ongoing Kashmir conflict
In November 2025, Keymous+ narrowed in on Pakistan, taking down numerous state sites as geopolitical tensions continue to rise in the region. Notable sites compromised by the DDoS attacks include Saif Power Limited, Ufone Pakistan, the Water and Development authorities, and an electric power supplier. Some experts suggest that these attacks may be falsified or exaggerated for publicity.
Practical solutions for CISOs to prevent Keymous+ attacks
Preventing cyber threats before they escalate is essential for maintaining good security posture. Especially if your organization is located within regions that face geopolitical conflict or align with sectors that support critical infrastructure.
- Treat suspicious activity as a persistent threat: Keymous+ is known for persisting within IT ecosystems. Design your incident plan around persistence, speed, and scale, ensuring rapid detection, thorough forensics, hardening protocols, and regional escalation pathways. Running regular tabletop exercises that simulate repeated activations can be a useful way to prepare teams.
- Prioritize telemetry and vendor SLAs: Retaining high-resolution NetFlow and PCAPs at the edge ensures fast access for the first minutes of an event, keeping flow telemetry at scale for accurate DDoS attack source detection.
- Harden edge and application controls: It‘s important to strengthen your defenses at the edge of networks and within applications to better weather an attack. Enabling SYN cookies and adjusting TCP settings reduces the likelihood of a SYN flooding attack, while bot protection (such as using CAPTCHA) helps teams to spot and slow down automated attacks.
- Coordinate regionally: If your organization is spread across geographies, coordination is your best bet. Ensure ISPs are configured to block “fake” traffic and apply filters when needed, set up clear escalation pathways with reputable providers local to the region, and map regional dependencies (including DNS, CDNs, and transit providers) in case regional providers are impacted.
FAQs
What are the early warning signs of a Keymous+ attack?
Catching the early signs of an attack is essential to thwarting a hacker‘s goals. Early detection reduces downtime, reduces reputational damage, and prevents attackers from using the initial compromise for deeper intrusions.
Organizations should look out for suspicious activity such as:
- Sudden spikes in traffic from unusual geographies (especially from North Africa and the Middle East, where many hackers are located).
- Repeated SYN/UDP requests that overwhelm servers.
- Unauthorized admin logins, especially if they fall outside your timezone.
- Social media chatter claiming responsibility for attacks against your sector.
How can you protect your organization against rising DDoS attack threats?
DDoS attacks overwhelm the target server, network, or application with traffic, causing it to go offline. Often, attackers use malware to infect IoT devices, adding the victim‘s systems to an existing botnet, causing further damage to more targets in the future.
To decrease the chances of experiencing a DDoS attack, organizations can harden their DNS infrastructure, such as disabling open resolvers and implementing query rate limiting. A web-application firewall (WAF) is a useful tool for mitigation, while establishing connection limits can limit TCP SYN floods by validating digital handshakes per IP address.
How can organizations protect themselves against becoming part of a botnet?
Becoming part of a botnet compromises your cybersecurity efforts as an organization. To reduce this risk, leverage packet-level insights for network detection and response (NDR) solutions.
Investigating cyber threats in real-time by leveraging packet-level data to identify suspicious activity across your IT ecosystem supports critical infrastructure security.
What is the rate of malicious traffic that has been observed during a Keymous+ cyberattack?
To measure cyberattacks, researchers look at the rate of data arriving in your network and whether it can saturate the provisioned transit.
Individual Keymous+ attacks have been observed peaking at 11.8Gbps; however, collaborative attacks have peaked at 44Gbps. An approximate 4x increase in attack bandwidth indicates a large botnet network, usually reliant on DDoS-for-hire resources.
What infrastructure is used by Keymous+ to launch their attacks?
Keymous+ uses a wide variety of infrastructure to launch its attacks. TOR exit nodes, public cloud instances, compromised Internet of Things (IoT) devices, commercial VPN/proxy services, and directly infected hosts enable the hacktivist collective to continue damaging private and government organizations.
According to analysts, most source IPs appear to be spoofed, leveraging modern DDoS-for-hire platforms that offer simple dropdown menus to spoof Autonomous System Numbers (ASNs) and IP addresses from major service providers and cloud platforms.
How does Keymous+ use Telegram to orchestrate their attacks?
Keymous+ hacktivists use the social media platform Telegram to coordinate and promote their attacks. Telegram is used as a propaganda tool to legitimize their image as a hacktivist collective, attracting followers, sympathizers, and potentially new recruits.
Telegram boasts less oversight than other social media platforms, allowing threat actors to share files and circulate tools, scripts, and instructions to boost cyber attacks.
For threat intelligence purposes, Telegram posts can provide insights into potential indicators of compromise (IoCs) such as IP addresses, domains, and usernames.
What additional risks do Keymous+ attacks pose?
According to NETSCOUT researchers, the scale and variety of sources indicate that Keymous+ leverages multiple botnets to execute its DDoS attacks. This means that each time an organization is compromised, it could be added to the botnet for future attacks.
Wrapping up
The growing threat of hacktivism requires organizations to be prepared for sustained attacks at an increasing scale. Hackers are becoming stronger with each innovation, making it more important than ever to keep systems and threat detection methods up to date.
CybelAngel can support your threat intelligence efforts, strengthening your security posture in uncertain times. CISOs and security professionals can stay one step ahead with real-time threat monitoring to sidestep targeted attacks.

