Can Money Buy Ransomware Happiness?

Table of contents
Ransomware is experiencing rapid growth as a cyber attack — impacting everyone from private individuals to cities, from enterprises to non-profit organizations to government agencies. According to the Beazley Group’s recent report, “The Enduring Threat of Ransomware,” there was a 25% increase in the first quarter of 2020 compared to the previous quarter. This acceleration of ransomware attacks is driven, in large part, by the increasingly rich payouts and abetted by the economic and workplace disruption caused by the COVID-19 pandemic.
Ransom payment on the rise
In an attempt to safeguard their business and restore their data, when hit by ransomware, many firms are asking themselves the question, “Should we pay or not to pay the ransom demand?” This dilemma seems to be more relevant than ever; in fact, according to a recent report by Coveware, in Q1 2020, the average enterprise ransom payment increased to an average of $111,605, up by 33% from Q4 of 2019. It seems there are businesses who believe that paying ransomware is a viable option.
A quick solution?
Some companies believe paying a ransom demand can be the fastest – and cheapest – way for their organization to restore stolen data and return to full productivity on behalf of their customers, shareholders, or partners. This business decision weighs the ransom amount against lost data, restoration of business and reputation, among a host of other impacts. As important, these decisions are predicated on the assumption that the data will be returned in an operable condition. Businesses operating in time-sensitive and life-impacting sectors (hospitals or schools, for instance) are often deciding to pay what is determined to be a relatively small amount of money to overcome the ransomware attack in comparison to the impact of lost data or systems being disabled. Companies point to examples of non-payment, such as the City of Atlanta, that was attacked in March 2018 by the infamous SamSam ransomware. City officials made the decision not to pay the ~$50,000 bitcoin ransom demanded by the cybercriminal. This decision has been widely criticized as the attack forced the City’s staff to switch to pen and paper for more than a week before being able to restore its IT operations and resulted in the city incurring $2.6 million on emergency efforts to respond to the attack. 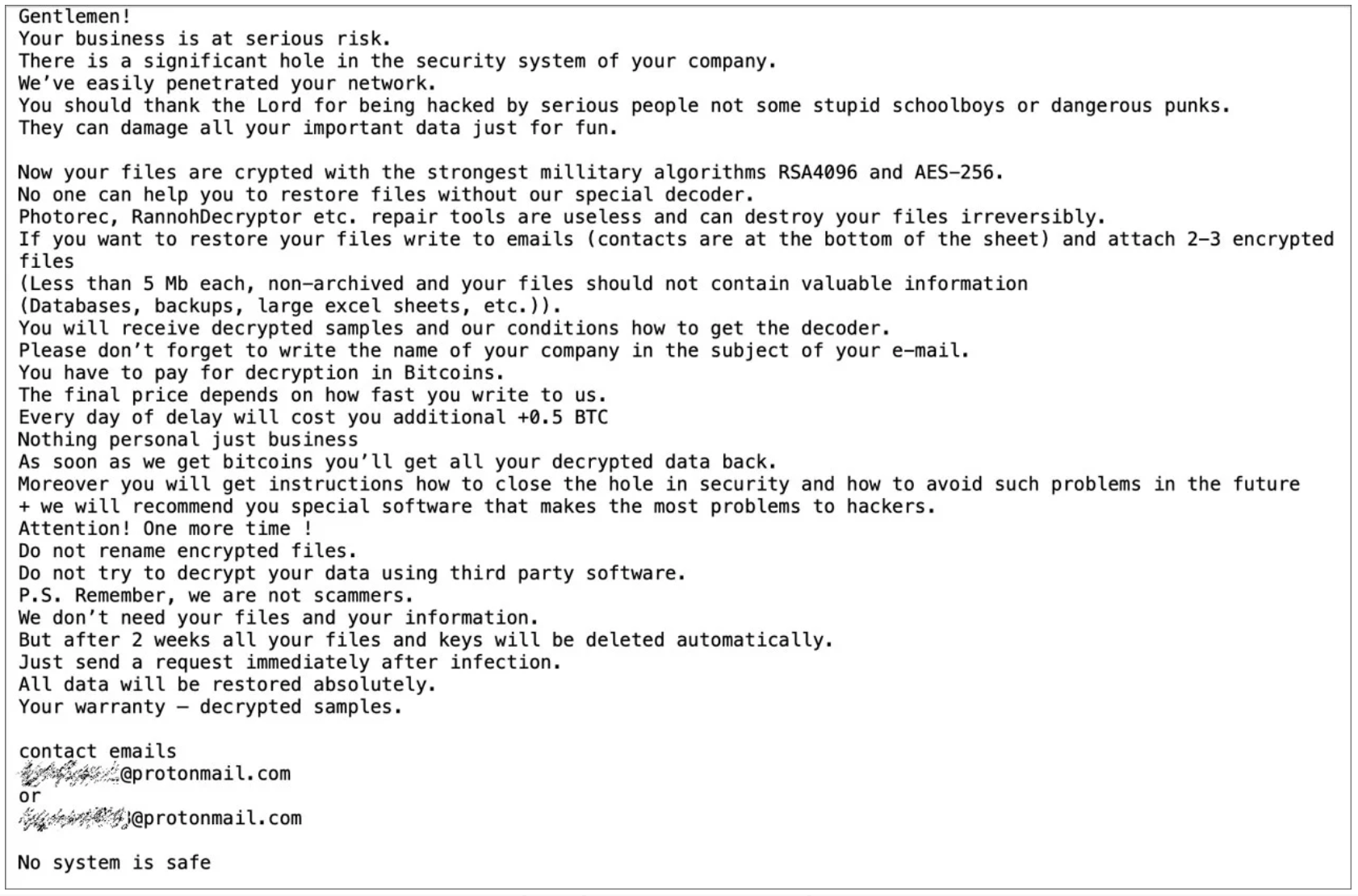
Sample Ransomware Note
Don’t do it! – why paying the ransom could be a bad idea
Nonetheless, when asked, a majority of security professionals will immediately advise that you should never pay a ransom if your systems have been infected by malware demanding to unlock your files in exchange for money. But what are the reasons why you shouldn’t do it?
You might earn the title of Rich Uncle Pennybags
A first concern with paying off criminals is that your firm will be known as an organization willing to pay, and once money is exchanged, malicious actors may continue to target your business. This could potentially label you as Rich Uncle Pennybags. This could make your business a frequent target by cybercriminals. As ransomware gangs usually are in competition with each other, it is unlikely that cybercriminals will share information on ransom payers. Moreover, as hackers try to maximize their profit when estimating the value of the ransom demand, once the target pays it is very likely that no further budget could be allocated by the victim to the payment of a potential second ransom, thus reducing the cybercriminals’ interest in carrying out a second attack. Despite this fact, it is interesting to know that the different ransomware present some similarities; hence, it has been suggested that highly successful ransomware gangs might in the future evolve into new threat groups, it is possible that those “old friends” in disguise will target organizations known to be easy prey.
Will you REALLY be able to regain access to your files?
The real issue that one should take into account is the actual outcome of the transaction. Indeed, It’s important to note that paying the ransom does not guarantee that the victims will get the decryption key or tool required to regain access to the infected system or hostage files. Despite the fact that figures suggest that 96% of the time, paying the ransom results in the victim receiving the decryption tool – with nearly 93% percent of data recovered – the amount of recovered files depends on the type of ransomware. Some ransomware – such as Ryuk for instance – seem to have relatively low data recovery rate, while others are close to 100%. Knowledge of the recovery rate of the ransomware that hit your firm is impossible, and so seems to be the solution to our dilemma.
And… at what cost?
In addition to considering the uncertainty related to the efficiency of the decryption keys while deciding to pay a ransom, one should also bear in mind the recovery cost related to the ransom payment. While hackers try to convince their victims that the ransom payment will provide a quick and cheap solution to restore the locked files, a recent study shows that only 26% of organizations that paid the ransom ever received their data back; whereas, 56% of organizations who did not pay, but had a good backup were able to restore their data.
Now what?
It is undoubtedly true that the decision to pay a ransomware demand remains a legitimate dilemma for most victims. It is a question that must be carefully pondered, with acknowledgement of risks and in concert with various stakeholders: cybersecurity experts, legal counselors and law enforcement. But there are some steps you can take to avoid even putting yourself in such a situation and build in advance your resilience against cyberthreats such as ransomware.
1. Offline Backups
Keeping offline backups of your sensitive files enables your organization to restore your data without having to deal with cybercriminals. If kept offline, your backup files are safe from hackers’ hands and ready-to-use if needed. Just remember to keep the backup information up-to-date!
2. Educate your employees
As CybelAngel discussed in a previous blog post, one of the most common ways malware and ransomware get into an organization is through spear phishing and social engineering, with somebody somewhere downloading a poisonous file or clicking on a malicious link in an email. Training users remains a very efficient way to avoid malware penetrating your organization’s perimeter.
3. Invest in threat prevention and hunting
Your in-house security teams and technology are doing a great job in protecting your perimeters, but threats can come from different routes or unexpected ways. In your cybersecurity budget, be sure to include providers of next generation security solutions using advanced technologies like machine learning to spot data leaks or threats targeting your organization is the best way to protect your organization from ransomware attacks.
Cybercriminals don’t advertise the names of corporations they plan to attack; and once the corporation is targeted, it is often too late to prevent harm. What is even more worrisome is these ransomware attacks have occurred on a massive scale. One of the best steps you can take to protect your digital assets is to take charge of your digital footprint with digital risk protection solutions. Using CybelAngel’s platform, you can detect leaks and vulnerabilities — yours, your supply chain, and your third party’s. Taking actions to thwart the hackers and cyber criminals before they wreak havoc on your enterprise. CybelAngel’s digital risk protection and data safeguarding is comprehensive. To learn more, contact us.