What do Rising Construction Industry Attacks Mean?

Table of contents
The construction industry is embracing artificial intelligence and automation to improve efficiency, but what about the risks?
Recently, the Architecture, Engineering, and Construction (AEC) industry has been targeted with cyberattacks aimed at extorting funds and disrupting business operations.
Unfortunately, construction companies are not prepared for cyberattacks, according to a new survey. Between 2019-2020, data breaches in the construction sector increased by 800%.
So, what can be done? Let‘s take a look at why cyberattacks are happening, what’s at stake, and how companies can reinforce their digital defenses before the next breach hits.
Emerging threat landscape
Since 2020, data breaches and cyberattacks on the construction industry have grown.
Between 2023 and 2024, ReliaQuest found that the construction sector had topped the list of spearphishing victims. The research firm also found that credential exposure comprises 75% of all cybersecurity alerts.
In one incident in 2019, a construction management company suffered a ransomware attack, leaving 30 employees unable to work for 10 days while having their data held for ransom. The incident cost the company over $100,000 in lost productivity and a $60,000 Bitcoin ransom to restore the data.
Cyberattacks against the construction industry have risen in the past 5 years:
- December 2019: Canadian construction company, Bird Construction, suffered a ransomware attack where the threat actors demanded $9,000,000 CAD in exchange for decrypting 60GB of ransomed data.
- January 2020: French construction behemoth Bouygues announced that threat actors were holding 200GB of data.
- August 2023 – July 2024: 481 construction organizations were listed on data-leak websites, increasing 34% from the previous year.
Why do construction companies face cybersecurity risks?
Construction companies continue to face growing cybersecurity risks as the industry rapidly embraces digital transformation.
Here’s why they’ve become prime targets:
- Low cybersecurity maturity: Compared to industries like finance or healthcare, construction often lacks dedicated cybersecurity teams or robust defenses, leaving the industry vulnerable to cybersecurity threats.
- High-value contracts and payments: Construction projects involve large sums of money, frequent wire transfers, and complex supply chains, making it difficult for construction firms to detect scams and invoice fraud.
- Widespread third-party access: Construction companies work with a variety of subcontractors, vendors, and other third parties to conduct daily business, leaving potential digital doors open to attackers.
- Sensitive project data: Construction firms store blueprints, access controls, and infrastructure details, especially critical for government or defense projects. That makes them a target not just for criminals but also for espionage.
- Operational downtime is costly: Hackers know that construction projects can‘t afford to meet delays, especially when constructing public service buildings. Many construction firms are paid quickly by contractors or suppliers, making them lucrative targets.
- Legacy systems and site-based networks: Many construction companies rely on outdated software, unprotected networks, or shared devices like tablets and laptops that don’t follow enterprise-grade protocols.
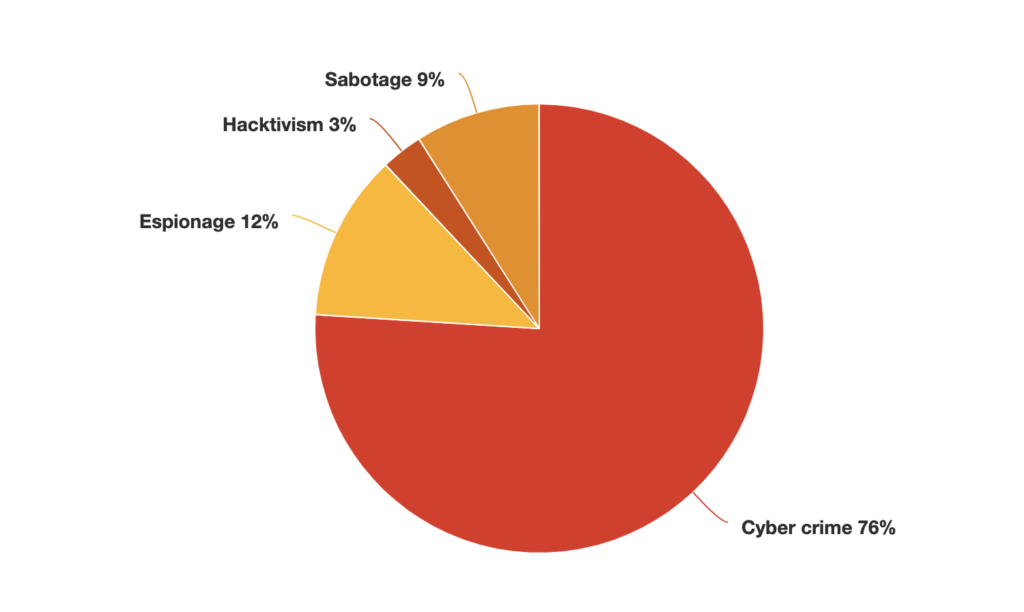
Key attack vectors
Cybercriminals thrive on vulnerabilities and slow-moving responses. In the construction sector, hackers exploit the industry‘s reliance on decentralized teams, third-party providers, and a lack of construction site tech.
- Social engineering and phishing: Due to the reliance on third parties and contractors, most construction firms will experience a phishing attack, according to researchers. Hackers aim to defraud firms by tricking them into releasing sensitive information that can be used to access payment information or credentials. A lack of internal security training makes these types of attacks more common and profitable.
- Third-party software: Construction firms rely on collaborative tools to coordinate dispersed teams; however, commonly used tools such as Building Information Modeling (BIM) are prime targets for data breaches.
- Ransomware attacks: Ransomware affects nearly all industries; however, the construction industry is particularly vulnerable due to high-pressure deadlines, unsecured digital footprints, and complex supply chains.
- Supply chain vulnerabilities: Construction projects often involve an array of professionals with varying cybersecurity knowledge, making them a target. Shared access across systems and a lack of visibility increase the likelihood of an attack.
- Internet of Things (IoT) devices: Devices such as mobile phones, laptops and tablets are often used on-site for coordination. When devices aren‘t configured for security, attackers use that opportunity to gain unauthorized access.
- Cloud exploitation: Construction firms rely on cloud storage to coordinate projects and contractors; however, these cloud environments are usually not configured properly, leaving them open to threats.
Cybersecurity risks of BIM systems
The aggregation of BIM data adds complexity and vulnerabilities to the construction sector. BIM systems collect and store sensitive project data such as architectural designs, cost estimates, and infrastructure schematics in shared digital environments accessed by multiple stakeholders.
Often, these systems have misconfigured access controls, making it difficult to detect which users are authentic and which could be potential cybercriminals. Suspicious online activity often flies under the radar, leading to more digital insecurity, data breaches, and ransom threats.
Here are some ways BIM systems can be exploited:
- Credential theft: To gain access to systems, threat actors use social engineering, malware, or phishing attempts to acquire authorized credentials. Unless Multi Factor Authentication (MFA) or other authentication procedures are followed, there‘s no way to know who is a legitimate user.
- Vulnerabilities to unauthorized entry: Many construction firms don’t monitor BIM environments in real time, or at all, giving threat actors ample time inside company systems. Without proper data logs or alerts, forensic investigation after the attack is more difficult, leading to future attacks.
- Intellectual property theft: Cybercriminals can steal or alter BIM data inside the platform before demanding a ransom for the stolen data. In the worst case, hackers can leak confidential information to data leak sites, exposing the project to security concerns.
Inside the Bouygues Construction ransomware attack
In 2020, French giant Bouygues Construction shut down its entire network after ransomware infected its systems. The ransomware attack was orchestrated by Maze, a threat actor group active since 2019.
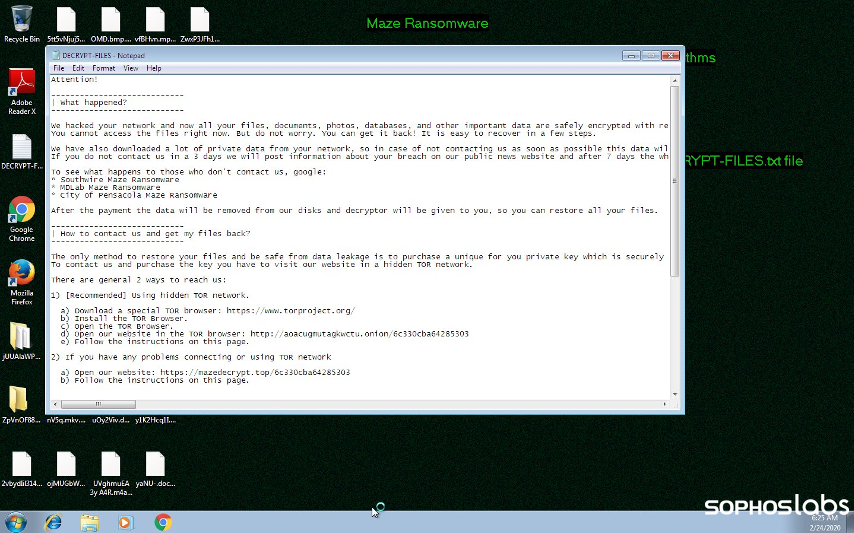
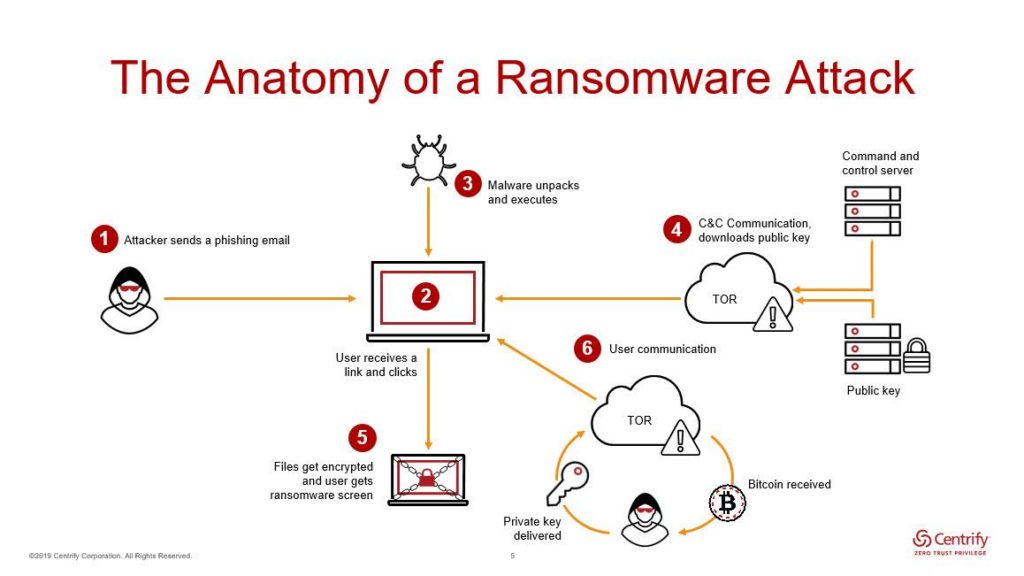
1. Initial access
Maze ransomware is known to use social engineering and phishing emails to obtain an entry point into target systems. Maze is also known to conduct reconnaissance for several days prior to an attack to map known vulnerabilities within the system.
In an observation by CloudFlare, Maze threat actors are known to scan the Microsoft Active Directory to find authorized users to use in social engineering campaigns.
2. Lateral movement and privilege escalation
Once inside the Bouygues Construction systems, the malware moves fast to spread across the network, infecting as many systems as possible. Threat actors used privileged escalation to move up the administrative tree.
Once a hacker has access to the main administration account, they can quickly take over entire networks.
3. Persistence
To resist removal from systems, threat actors install backdoors into a network so malicious software can be reinstalled if it‘s discovered and removed.
When experiencing an attack, companies may go straight to reboots, password changes, or software updates to counter the attack; however, this rarely works in the face of an attack when the threat actors can lurk in the shadows.
4. Encryption and ransom
Once the malware has infected sufficient systems, threat actors encrypt important data and exfiltrate it to their own network.
During the Bouygues Construction attack, threat actors claimed they encrypted 237 computers and exfiltrated 1,000 Terabytes of data. Extortion risk climbs when threat actors threaten to release the information unless the ransom is paid.
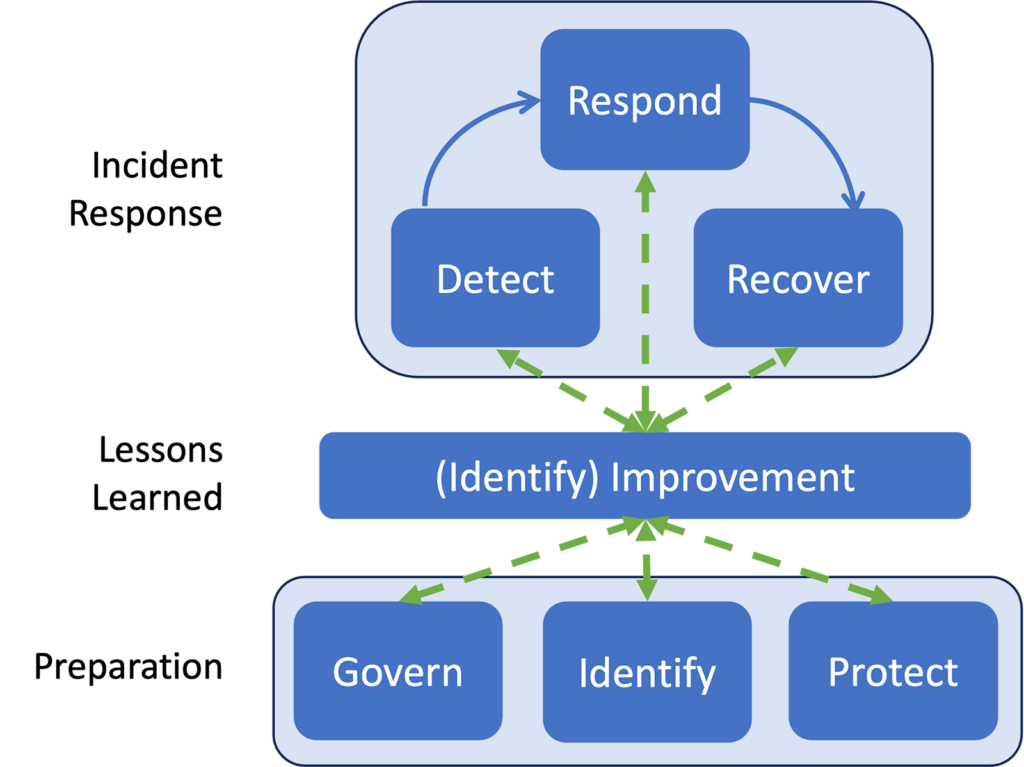
How to respond to cyber incidents in the construction sector
To avoid facing cyber incidents on a large scale, construction companies must have a plan to respond to incidents as they occur.
In the wake of a cyberattack, it‘s important to focus on containing the attack, eradicating imposters or malware, and working through remediation efforts.
- Isolate the affected systems. Disconnect compromised devices from the network to contain the potential spread of malicious software.
- Preserve logs and artifacts. Logs allow investigators to retrace the attacker’s steps, identify compromised systems, and pinpoint the method of intrusion. Evidence may be required by regulatory bodies to report the attack.
- Block suspicious IPs or domains. Attackers rely on Command and Control (C2) tactics to exfiltrate data. Blocking suspicious IPs and domains sever the link that threat actors have to the system.
- Communicate the attack to internal stakeholders. Ensure alignment within the organization to coordinate effectively, isolate affected systems, and escalate incidents.
- Report the incident to the authorities. Share indicators of compromise (IOCs) with CISA or law enforcement. This helps build threat intel across the industry. In the EU, under DORA regulations, major incidents must be reported within 24 hours.
Protect sensitive data from cyber threats
Taking appropriate cybersecurity measures is essential to protect businesses from financial losses and reputational damage.
As new technologies like artificial intelligence (AI) and automated workflows take hold in the construction sector, effective cybersecurity measures will be absolutely critical to safeguarding digital infrastructure and project data.
- Enable multi-factor authentication (MFA) to add an essential layer of defense against unauthorized access across all systems and cloud services.
- Restrict access to sensitive data strictly by user roles, following the principle of least privilege to minimize potential exposure.
- Regularly audit and secure BIM systems and cloud-based tools to prevent vulnerabilities from misconfigurations or insecure integrations.
- Apply timely updates and patches to all software and firmware to close known security gaps before they can be exploited.
- Adhere to regulatory compliance to avoid legal penalties and demonstrate cybersecurity accountability.
- Conduct a risk assessment of third-party vendors to identify and mitigate external risks in your project ecosystem.
- Develop and routinely test an incident response plan aligned with NIST standards to ensure preparedness and minimize damage during a cyber crisis.
- Invest in employee training on robust cybersecurity best practices so they can recognize threats like phishing, malware, and social engineering tactics.
- Recognize that data protection is a long-term investment, where short-term hurdles are outweighed by the resilience of strong cybersecurity practices.
Get started with CybelAngel
Start your cybersecurity journey with a trusted partner. CybelAngel can help you implement cybersecurity measures to prevent devastating data breaches.
