RansomHub: A Rising Danger in the RaaS Market

Table of contents
Ransomware is the ultimate cyber threat. With the rise of new ransomware-as-a-service (RaaS) groups, almost anyone can steal sensitive data and demand a payment in return. And a new player is on the market—RansomHub.
RansomHub is known for its double extortion strategy. Not only does it encrypt data, but it also threatens to publish it if the ransom is not paid. This has caused chaos across countless industries, leaving a trail of encrypted data and ransom demands for at least 210 victims this year.
Let’s uncover how RansomHub operates, analyze emerging trends, explore real-world examples of their attacks, and discuss how organizations can fight back.
1. What is RansomHub?
RansomHub hit the RaaS cybercrime market in February 2024, and it has since attacked at least 210 victims, with recorded impacts in countless industries, including critical infrastructure such as:
- Water and wastewater
- Information technology
- Government infrastructure
- Healthcare
- Food and agriculture
- Financial services
- Manufacturing
- Transport
- Communications
Formerly known as the Cyclops or Knight ransomware, RansomHub is known for its double extortion model.
How does RansomHub’s double extortion model work?
Threat actors can use RansomHub’s malware to encrypt and exfiltrate their victims’ sensitive data.
They then share a ransom note with a client ransomware ID and instructions on how to contact RansomHub via a unique URL. Victims generally have 3—90 days to pay a ransom. Otherwise, their sensitive information is published on a data leak site.
2. RansomHub in numbers
Since it appeared on the dark web, RansomHub has quickly gained momentum as one of the most prominent ransomware operations in the world. Here are some emerging trends to keep in mind.
Ransomware is a top cyber threat
RansomHub has tapped into a lucrative market. Ransomware accounted for 70.13% of detected cyberattacks worldwide in 2023, making it a weapon of choice for most threat actors—and a golden opportunity for RaaS gangs like RansomHub.
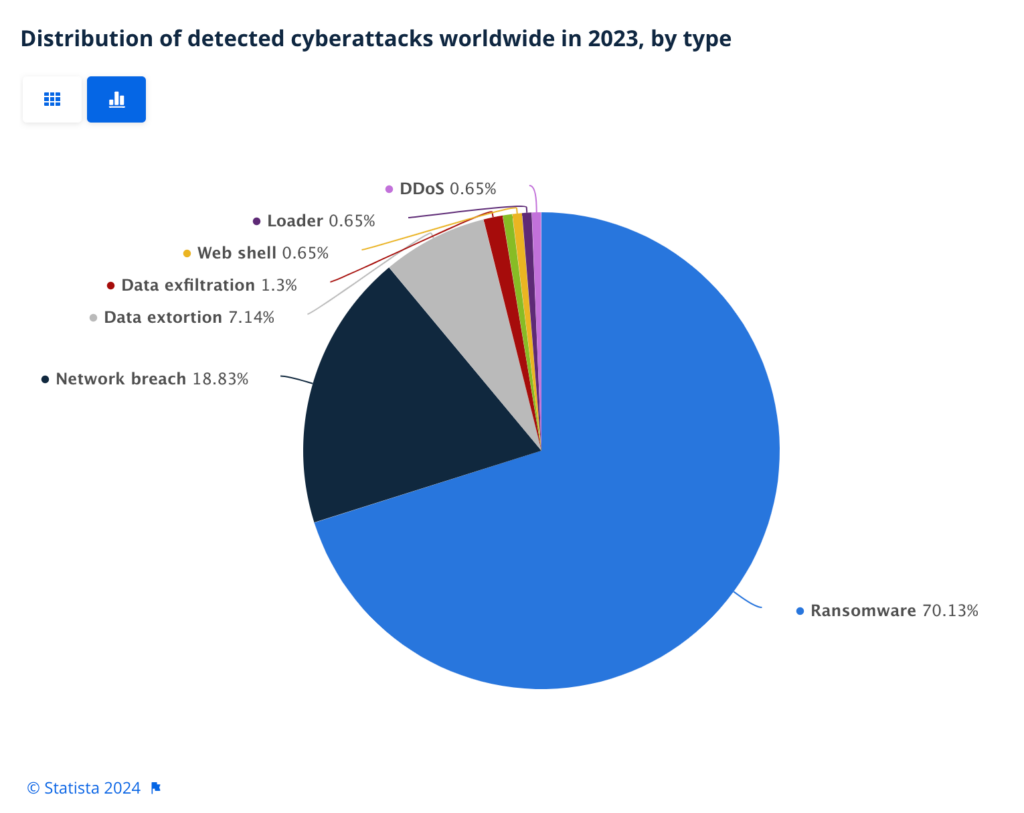
Pie chart showing the types of cyberattacks worldwide in 2023. Source.
RansomHub is overtaking LockBit
According to Infosecurity Magazine, RansomHub is the ‘number one ransomware operation in terms of claimed successful attacks’ (as of October 2024). This is partly due to LockBit’s takedown in February, as well as RansomHub’s strategy of targeting more experienced affiliates for its operations.

News headline showing RansomHub’s prolific status in the RaaS world. Source.
It’s rampant in the United States
When it comes to ransomware attacks in the US, RansomHub was the second most-detected variant in the third quarter of 2024. And it was very close to the leader, with a difference of only about 1%. This marks RansomHub as one of the biggest RaaS threats to US operations this year.
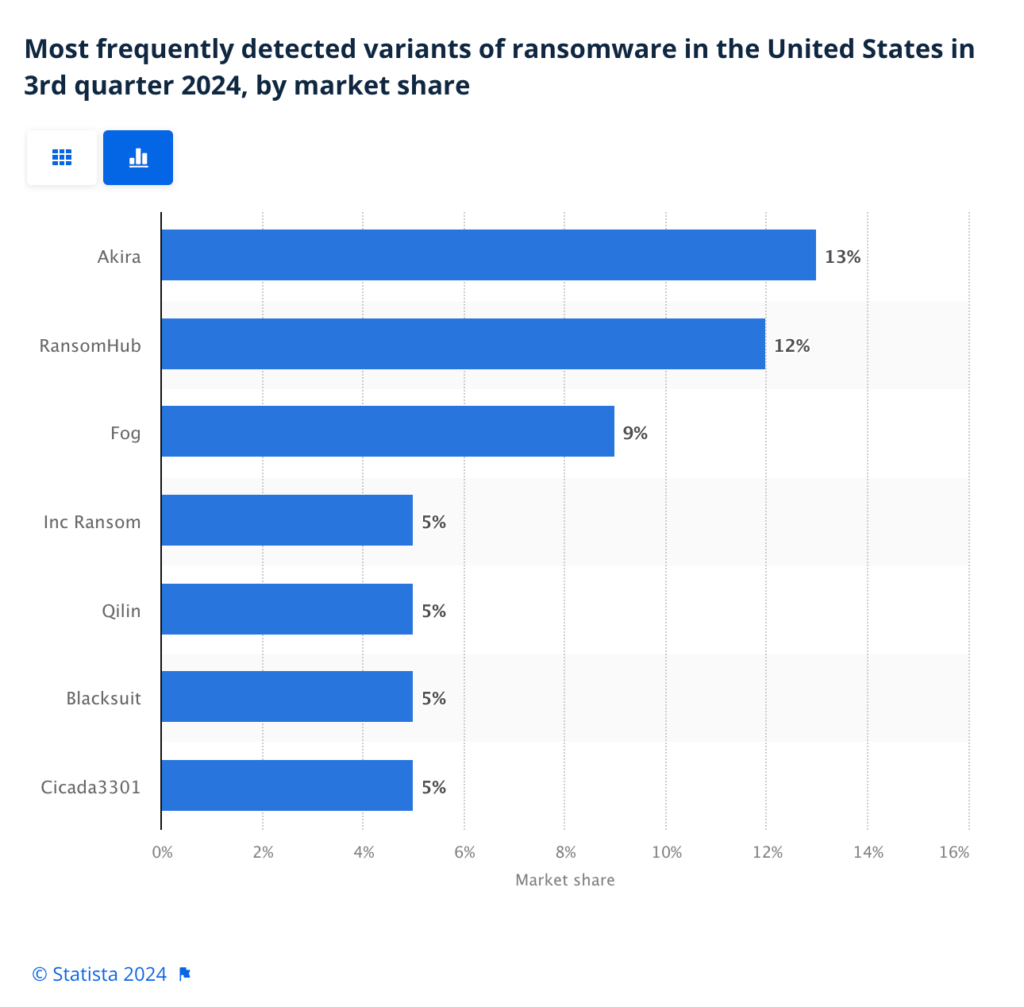
Graph showing most frequently detected ransomware variants in the US.
There are huge profits to be made
RansomHub is tapping into an aspect of cybercrime with lucrative rewards. In 2023, ransomware scams made $1.1 billion worldwide, which was a 140% increase from the year prior. This set a record for the greatest ransomware payments since the COVID-19 pandemic.

Graph showing the total amount of money received by ransomware actors globally. Source.
RansomHub’s activity is jumping up
The Hacker News has reported that RansomHub’s activity is on an “upward trajectory” with the following data showing its share in ransomware activity throughout 2024:
- Q1 2024: 2% of all ransomware attacks
- Q2 2024: 5.1% of all ransomware attacks
- Q3 2024: 14.2% of all ransomware attacks
This shows that RansomHub is here to stay—and it’s a key malware that CISOs should watch out for in 2025.
3. The RansomHub timeline
There have been many RaaS groups in recent years, from Ran$umbin to LockBit. But when did RansomHub become so prolific?
It all started with the largest-ever data breach in the US in February 2024, affecting 100 million individuals connected to Change Healthcare, a subsidiary of UnitedHealth Group.
Threat actors had stolen data from almost a third of all Americans, using the ransomware group AlphV.
However, when law enforcement took down AlphV and LockBit, the two largest ransomware gangs, the hackers used RansomHub to host the stolen data.
Since then, RansomHub has rapidly gained notoriety, with ransomware attacks on multiple high-profile organizations, governments, and critical infrastructure.
4. How a RansomHub attack works
There are several stages in a RansomHub attack, plus several terms and conditions that threat actors have to follow to use the malware.
The stages of a RansomHub attack
In a joint document released by the FBI, CISA, and several other organizations in August 2024, there’s a detailed breakdown of what a RansomHub attack looks like, under the alert code ‘AA24-242A’.
Here’s a quick summary.
- Initial access: Threat actors break into operating systems via common vulnerabilities and exposures (CVEs), such as CVE-2020-1472, where they take advantage of privilege vulnerability. They can also use phishing emails or password spraying.
- Discovery and defense evasion: The malware hub will scan the network, and then rename the ransomware software with innocent-looking tags, such as
windows.exe, to avoid detection. It can also sometimes disable endpoint detection and response in a process known as “EDR-killing.” - Privilege escalation and lateral movement: RansomHub ransomware can be used to create user accounts, gather credentials, and move through the network via techniques such as Remote Desktop Protocol (RDP) and Anydesk.
- Data exfiltration: Exporting the data is up to the affiliate, but generally they’ll use tools such as PuTTY, Cobalt Strike, or Amazon AWS S3 ransomware exports.
- Encryption: RansomHub uses an intermittent encryption algorithm called Curve 25519, with a unique key or ransomware identifier for each victim organization.
RansomHub’s terms of service
RansomHub has several caveats for people using its service, stating, “We do not allow CIS, Cuba, North Korea, and China to be targeted.”
It also stipulates that RansomHub affiliates can’t target non-profit organizations or re-attack people who have already paid a ransom.
Similarly, if cybercriminals fail to deliver a decryption key after the ransom is paid, then RansomHub will send one on their behalf.
“Affiliates must comply with the agreements reached during the negotiations and the requirements,” RansomHub has said. “If they don’t, please contact us, we will ban them and never work with them again”.
There is contact information available on RansomHub’s website for victims who encounter any issues with payment or retrieving their data.
5. Case studies: RansomHub in action
Despite only gaining notoriety in recent months, RansomHub has already amassed a large portfolio of high-profile victims, ranging from football clubs, to auction houses, to credit unions, and beyond.
When a football team lost its data…
In November 2024, Bologna FC reported that its company data had been stolen, and would likely be leaked.
A spokesperson stated, “Bologna FC 1909 S.p.a. would like to communicate that a ransomware cyber attack recently targeted its internal security systems.”
RansomHub claimed to have stolen 200GB of data, including players’ medical records, the club’s business plans, and financial documents.
When an entire city was affected…
Also in November 2024, RansomHub stated it was responsible for causing technology issues in Coppell, Texas.
The city WiFi service was affected, as well as court operations, library services, and ‘platforms for permits and inspections.’
It took several days to restore the government phone systems, and platforms for utility bills—meaning that authorities had to extend payment deadlines.
When a company lost $35 million…
Halliburton, a global supplier in the energy industry across 70 countries, suffered a ransomware attack in August 2024 that led to $35 million in losses.
It was forced to shut down its IT systems, and customers couldn’t connect to its services. The scope of the data breach is still under investigation.
When 700,000 people had their data stolen…
Patelco, a California credit union, discovered a data breach in June 2024—but it had been going on since May.
Hackers exposed the personally identifiable information (PII) of 726,000 people, including their names, social security numbers, and birth dates.
As part of the mitigation effort, victims have been offered two years of identity protection services.
When the Mexican government was targeted…
In November 2024, RansomHub claimed to have stolen 313 GB of data from the Mexican government.
It shared a sample of the data it claimed to have taken on their extortion portal, featuring “contracts, insurance, financials, confidential files.”
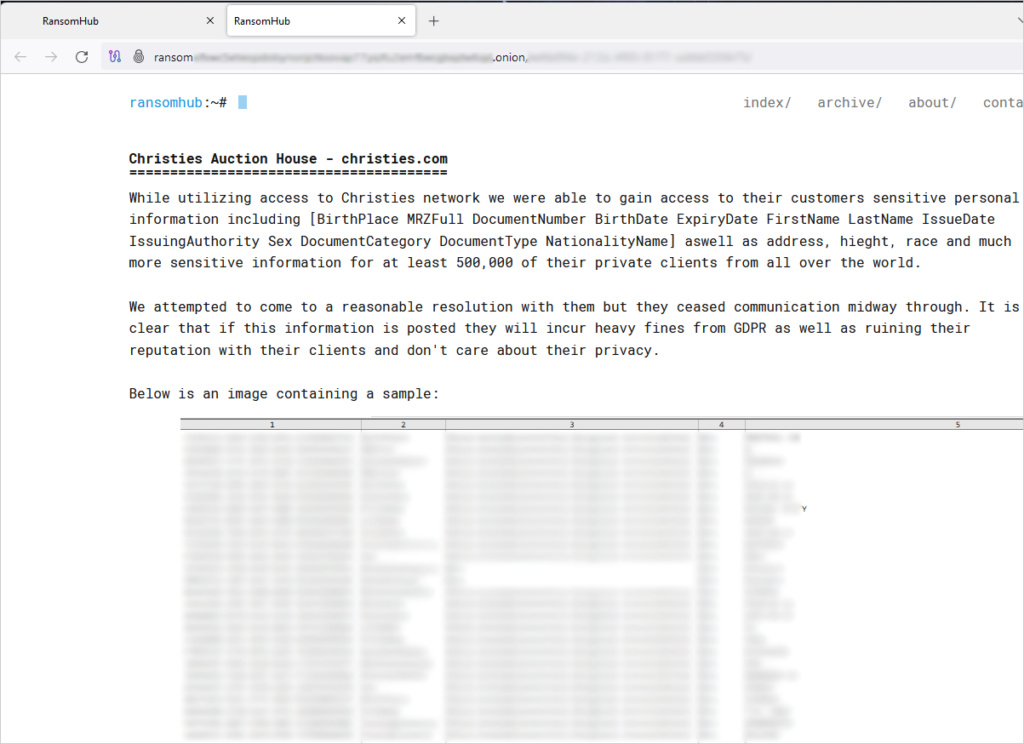
When Christie’s faced a new kind of auction…
Christie’s is one of the oldest and most prestigious auction houses in the world, with a history spanning over two centuries.
However, in May 2024, some of their client data was stolen by RansomHub, and Christie’s was listed on its extortion portal (see below).
6. Defending against RansomHub
The true cost of ransomware attacks can be astronomical. In its 2024 EASM report, CybelAngel found that the average recovery cost was $1.82 million, and ransom payments were $2.6 million. (And, of course, there’s the time cost.)
The highest cause of ransomware attacks is exploited vulnerabilities.
To avoid being targeted by RansomHub—and suffering the financial losses, regulatory penalties, and reputational damage that will follow—then companies need to identify their weak points and counteract them with the right security solutions.
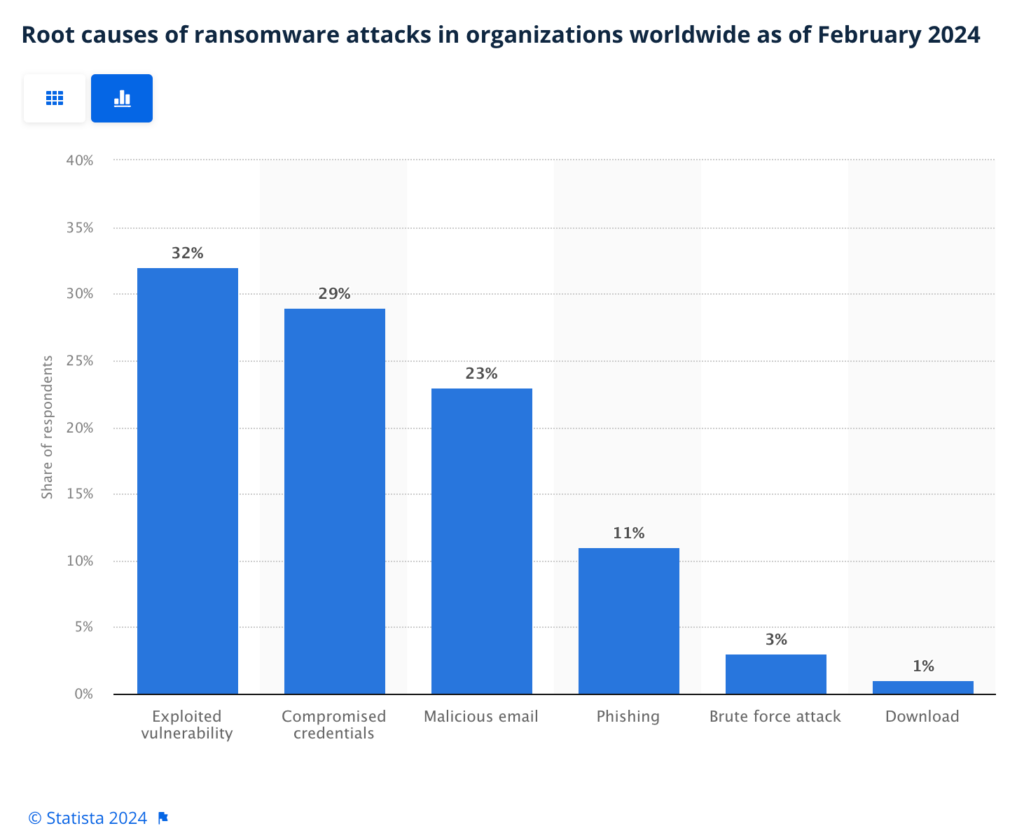
Graph showing the main causes of ransomware attacks. Source.
In the CISA ransomware guide, there are several core cybersecurity recommendations to protect against RansomHub.
CISA’s Tips to Fight Off RansomHub
- Recognize indicators of compromise (IOCs): In the guide, CISA lists file names, URLs, and IP addresses that could indicate that RansomHub’s malware has been installed on a device.
- Know RansomHub’s tactics, techniques and procedures (TTPS): CISA also lists common techniques used by RansomHub affiliates, such as mass phishing and abusing Microsoft Windows Management Instrumentation to launch malicious payloads.
- Create an incident response plan: CISA recommends quarantining or removing affected accounts, reviewing compromised networks, setting up new account credentials, reviewing unusual activity, and reporting the breach to them.
- Have a recovery plan, and keep offline, encrypted backups: This will ensure that even if your organization is subjected to a ransomware attack, you can mitigate the damage and restore systems quickly.
- Follow NIST’s password policies: When it comes to access controls, ensure that everyone has passwords that are at least 8 characters long, stored in industry-recognized managers, and implement lockout measures for multiple failed login attempts.
- Have multi-factor authentication: This can prevent criminals from gaining remote access to your system through phishing, in particular via emails and virtual private networks.
- Disable command-line and scripting activities: Threat actors often rely on these tools for their lateral movement workflows, so disabling them can block the ransomware from working.
You can also take advantage of threat intelligence and external attack surface management tools, such as CybelAngel, to safeguard your operations.
In the meantime, law enforcement is also working against ransomware groups. You may have seen the Bloomberg headline, ‘FBI dismantles malware system that took millions’ with regards to the Qakbot takedown, or the more recent LockBit operation, which froze 14,000 rogue accounts.
But ultimately, cybersecurity is everyone’s responsibility—and the key to ensuring that RansomHub cannot find easy targets.
Final thoughts
RansomHub is a stark example of how cybercriminals have turned hacking into a thriving business. But they aren’t unstoppable.
When companies, governments, and individuals work together, it’s possible to push back against ransomware threats—and thereby reduce the appeal of RaaS as an easy tool for cybercriminals.