Digital Vigilance: 7 Strategies for Enterprises to Combat Online Threats

Table of contents
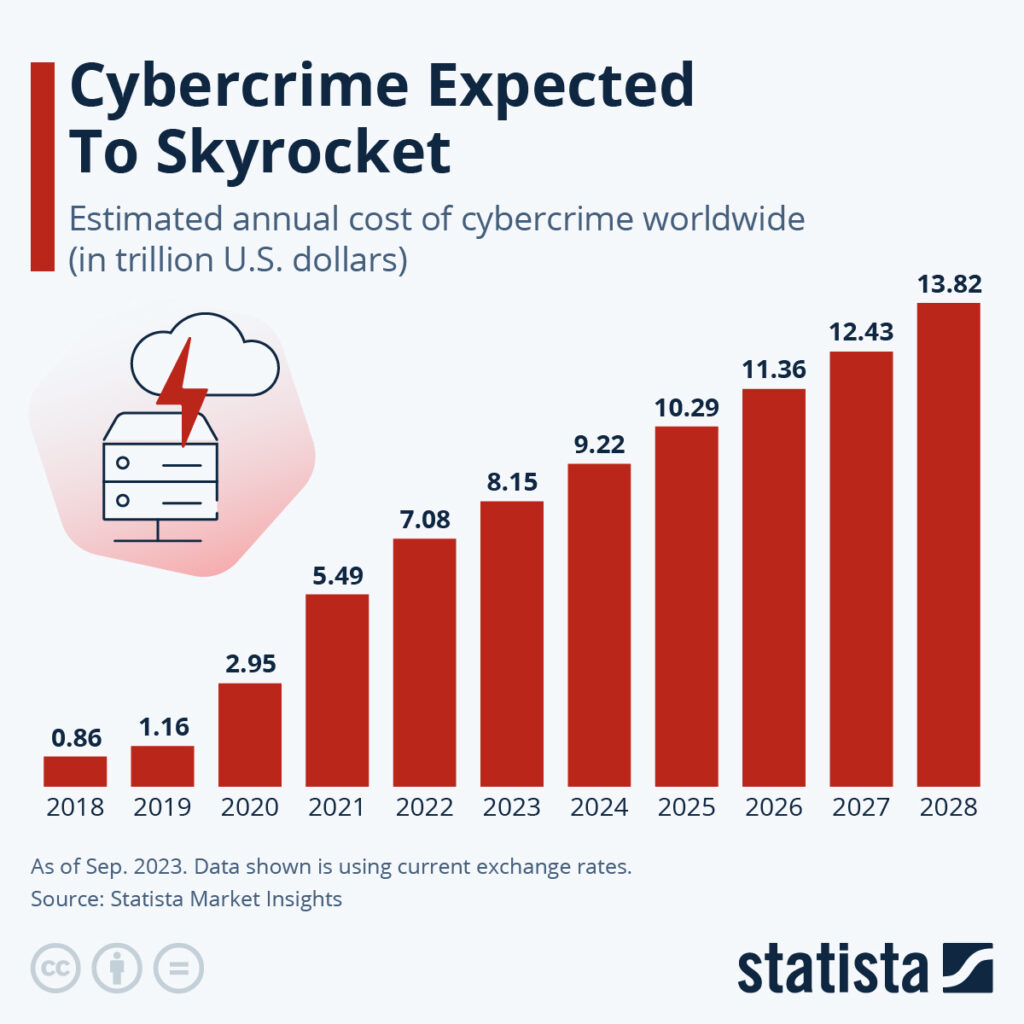
Cybercrime is growing daily, and will cost the world over $10 trillion annually by 2025.
With that being said, businesses of every size, especially enterprises should take this security threat seriously and part and parcel of that is understanding the sphere of digital threat intelligence.
So, what does that entail?
In this article, we’ll explore the digital threat landscape, discuss common cyber attacks, explain how cybercriminals work, and share proven strategies to help enterprises battle digital threats. Let’s dive right in!
What is digital threat intelligence?
Digital threat intelligence is basically the practice of gathering, analyzing, and applying intel about current or potential threats that target the digital assets of organizations.
The various types of threat intelligence include:
- Strategic intelligence: High-level trends and risks, useful for long-term planning.
- Operational intelligence: Actionable insights on specific threats and campaigns, aiding in immediate defense strategies.
- Tactical intelligence: Information on tactics, techniques, and procedures (TTPs) used by threat actors.
- Technical intelligence: Specific data like Indicators of Compromise (IOCs).
With the help of actionable intelligence, senior IT decision-makers understand where threats come from and how they can impact their organization.
Automation plays a key role in processing large volumes of threat data and minimizing false positives. This data supports various use cases, such as threat hunting, incident response, and improving Security Operations Center (SOC) workflows.
Integrations with Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) systems enhance these capabilities.
Common digital threats for enterprises
Let’s start by discussing some of the most common digital threats:
Malware attacks
Malware, short for malicious software, is a common cybersecurity threat. Attackers can hide it in app downloads, mobile websites, or phishing emails and text messages.
Once a device is compromised, threat actors can steal personal information, location data, financial accounts, and more.
Common types of malware include:
- Virus: This type of malware infects clean files and spreads when people use those files. It can quickly corrupt or erase data on a device.
- Trojan: Unlike viruses, Trojans don’t replicate but can be just as harmful. They resemble legitimate software and cause problems once inside the device.
- Spyware: This malware spies on users and collects data like browsing habits, logins, credit card details, and other personal information.
- Cryptojacking: Cybercriminals install software on a victim’s device to use their computing resources for mining cryptocurrencies without their knowledge.
- Rootkit: Rootkits can be hard to detect and remove once embedded because they’re made with gaining administrative control of a device in mind.
- Worm: Worms exploit the flaws of operating systems and infect networks of devices through local networks or the internet.
- Ransomware: This type of malware locks or encrypts data on a victim’s device and demands a ransom to give back access.
- Adware: This type of malware isn’t always harmful because it shows unwanted ads to people, making them install other more dangerous malware.
- Botnet: This is a network of compromised devices remotely controlled by attackers to perform large-scale attacks or send spam.
- Fileless malware: Unlike traditional malware that relies on files, fileless malware operates in a system’s RAM, using legitimate programs to infect the computer.
- Mobile malware: This malware targets mobile devices with various types of malicious code designed for these devices.
Social engineering attacks
Social engineering exploits human error rather than technical flaws. The victim is tricked into giving away sensitive data or installing malware on their device by a cybercriminal posing as a trustworthy source.
Types of social engineering attacks include:
- Phishing: Phishing involves sending emails that trick the recipient into revealing confidential information or downloading malware by clicking on a link in the message.
- Spear phishing: A more targeted version of phishing, where the attacker gathers information about the victim and pretends to be someone the victim knows and trusts.
- Vishing (voice phishing): In this attack, the imposter uses phone calls to deceive the target into providing sensitive information or granting access to a system. While often targeting older individuals, vishing can be used against anyone.
- Smishing (SMS phishing): The attacker uses text messages to deceive the victim into providing personal information or clicking on malicious links.
- Baiting: The attacker entices the victim with a promise of something appealing, like a gift card, to trick them into revealing sensitive information such as login credentials.
Supply chain attacks
Supply chain attacks infect legitimate applications and spread malware through source code, build processes, or software updates. Attackers often look for weak network protocols, server setups, and coding methods to steal data and compromise software building and updating.
They change source code and hide malicious content, making threat detection harder. They’re especially dangerous because they affect applications signed and certified by trusted vendors.
Attackers might also hide malicious code in automated updates for hardware or firmware parts or pre-install it on physical devices.
“Man in the middle” (MitM) attacks
MitM attacks mess with the communication between two parties, such as a user and a mobile application. The attacker can monitor conversations, steal sensitive data, and impersonate both sides.
Examples of MitM attacks include:
- Wi-Fi eavesdropping: The threat actor sets up a fake Wi-Fi connection to intercept users’ data, such as login details and payment information.
- Email hijacking: The attacker impersonates a legitimate organization’s email address to trick users into revealing sensitive information or transferring money.
- DNS spoofing: This is one of the types of DNS attacks that redirect a user to a fake website posing as a legitimate one. The goal of this attack is to divert traffic or steal login credentials.
- IP spoofing: The attacker uses a fake IP address to resemble a real website and deceives users into using it.
- HTTPS spoofing: The threat actor uses “HTTPS” in the URL of a malicious website to make it look safe and trick users into thinking the site is secure.
Denial of service (DDoS) attacks
A denial-of-service attack happens when a hacker takes control of numerous devices. Then, they use the devices to overwhelm a target system, such as a website, causing it to crash because of the overload. This type of attack is known as a distributed denial of service (DDoS).
Learn how to prevent DDoS attacks.
IoT devices attacks
IoT devices, such as industrial sensors, face various cyber threats, such as hijacking devices for DDoS attacks and accessing collected data without authorization. Malicious cybercriminals attack misconfigured IoT devices due to their large numbers, widespread distribution, and often outdated operating systems.
Zero-day attacks
Zero-day attacks exploit vulnerabilities in software, operating systems, or networks that manufacturers remain unaware of. For instance, when a technology vendor releases a new version of something with a loophole, hackers can take advantage of it to access your data.
Injection attacks
Injection attacks include inserting harmful input into web application code. This can result in exposing sensitive data, causing denial-of-service (DoS) incidents, or compromising the entire system.
Key types of injection attacks:
- SQL injection: Hackers insert SQL queries into input fields or forms. If the application is vulnerable, these queries execute within the database, posing a potential threat since many web apps use SQL databases. Another form is NoSQL injection, targeting databases that don’t follow traditional data models.
- Code injection: Attackers inject malicious code into vulnerable applications. When executed by the web server, this code acts as part of the application.
- Cross-site scripting (XSS): In XSS attacks, attackers inject JavaScript-containing strings into applications. When victims’ browsers execute this code, it can redirect them to harmful sites or steal session cookies, particularly if the application can’t sanitize inputs properly.

Password attacks
Password attacks happen when hackers try to guess, force their way in, or trick users into giving away their passwords.
Here’s how they do it:
- Password spraying: Hackers use the same password on many accounts. For instance, over 3.5 million Americans use “123456.”
- Brute force attacks: Hackers use software to try lots of different username and password combinations until they find the right one. They often use logins stolen from marketplaces on the dark web, where people use the same passwords for different accounts.
NOTE: Cyber due diligence, can help prevent password attacks among other things.
Digital threat intelligence: 7 ways to prevent digital threats
As you can see, cybercriminals target your company’s data, money, and assets by finding flaws in your IT setup and catching your staff off-guard. That’s why you should invest time and money into protecting your company from cyber-attacks.
Here’s how:
1. Let CybelAngel keep your business safe!
Consider hiring a reputable cybersecurity firm like CybelAngel for security evaluations, penetration testing, and ongoing threat monitoring. Our highly-trained security team can discover and fix flaws and prevent potential attacks that your security teams might miss.
We offer external attack surface management services made with enterprises in mind. Our threat intelligence program includes:
- Asset discovery and monitoring: Our attack surface monitoring includes real-time scans to recognize exposed assets.
- Data breach prevention: We can detect and prevent data leaks.
- Account takeover prevention: We monitor for compromised accounts.
- Dark web monitoring: CybelAngel can identify threats on the dark web.
- Domain protection: We can also keep your domains safe from cyber threats.
Our EASM platform also provides remediation, M&A cyber due diligence, and special threat investigations. Here’s how these services can improve the security of your enterprise:
- Remediation: Assisting in mitigating identified threats and vulnerabilities.
- M&A cyber due diligence: Evaluating the cyber risks associated with mergers and acquisitions.
- Special threat investigation: Conducting detailed analysis of specific threats to a company.
These services can handle intermediate and long-term cyber risks, hence boosting the security posture of enterprises. However, if you’re confident that you can handle digital threats yourself, here’s a list of helpful tips:
2. Create security policies and practices
Having security policies and practices in place can guide you on how to handle issues in case they happen.
- Develop clear practices and policies: Explain common online attacks and prevention methods. Also, mention the consequences for employees who violate these policies.
- Control physical access: Make sure that only authorized people can access company devices, especially laptops and cell phones, as they can be easily stolen or misplaced.
- Dispose of devices properly: When disposing of company devices, reset them to factory settings to prevent any sensitive information from falling into the wrong hands. Never discard a device without doing this step to protect your company’s data.
3. Enhance your technology
Make sure that your technology isn’t outdated. If it is, replace it, then follow these steps:
- Encrypt your data: Prioritize protecting your data over anything else. Make it unreadable without a key so that even if hackers breach your system, they can’t use the data.
- Keep software and apps up to date: Apply patches the same day they’re released to protect against new potential threats.
- Restrict software installation: Limit who can install software on your network and keep a record of all installations.
- Delete unused software: Regularly remove unused apps to prevent them from becoming future attack points. Also, don’t use cheap or open-source software.
- Remove unsupported software: Uninstall software that is no longer supported or updated by vendors.
- Know what connects to your network: Keep a list of all authorized devices to block unauthorized ones, hence blocking external threats.
- Limit account privileges: Use access control systems to give employees access only to what they need.
- Use antivirus software: Install antivirus software to stop ransomware and malware.
- Implement strong firewalls: Choose firewalls that monitor traffic and alert you to suspicious activity or external threats.
- Leverage cloud security: Encrypted cloud backups can help secure your data and recover it if attacked. However, evaluate the security of your cloud program before doing so.
- Secure your Wi-Fi network: Turn off beacon frames to make your network invisible to outsiders.
- Practice robust password management: Never use the same password for multiple accounts. Instead, use various strong passwords and consider a well-encrypted password manager.
- Implement dual-factor authentication (2FA): Require a second security element for logging in to make it harder for hackers.
- Protect IoT devices properly: Secure all connected devices, such as printers and cameras, as carefully as your computers.
- Consult white-hat hackers: Have ethical hackers test your network for vulnerabilities and provide recommendations for a good security tool or cybersecurity company.
4. Train your employees
Negligence drives 90% of data breaches, so make sure that everyone working with you knows how serious they can be. Here’s a list of a few important tips:
- Question unusual requests: Encourage employees to verify any strange requests (sudden demands for money) with the manager.
- Don’t use public Wi-Fi: Tell employees to use encrypted VPNs or mobile data instead of public Wi-Fi to keep their connections secure.
- Don’t share information: Advise your team(s) to be careful about what they share on social media because cybercriminals can use this information to impersonate them.
- Verify remote access requests: Teach employees to always confirm with the IT department before giving anyone remote access to their computer.



5. Leverage artificial intelligence (AI) for cybersecurity
AI is more than a buzzword in threat intelligence. It helps businesses detect threats by analyzing large amounts of data using advanced algorithms.
AI and machine learning can spot indicators of compromise in networks and systems, hence improving digital risk protection. It also learns from past mistakes to improve threat detection and automatically isolate compromised systems.
Lastly, it works well in various IT environments, enables proactive security operations, and improves overall cybersecurity.
6. Keep your customers posted
Tell your customers why you collect their information and how you use it. Make it clear that you won’t ask for sensitive data like social security numbers or bank details through texts or emails. If they get any suspicious messages, tell them to let your company know.
7. Proper incident response
If your system gets breached, follow these steps:
- Understand the attack: Figure out how the hackers got in and shut down the security threat immediately.
- Check your network: Inspect each section of your network to ensure they haven’t left anything behind that could cause future problems.
- Rebuild safely: Once a department is clear, start reinstalling apps and programs. Only reconnect parts of the network that have been checked and secured.
- Restore from backup: When it’s safe, reconnect to your backup cloud databases to restore your data and continue business operations securely
Wrapping up
In conclusion, security threats won’t stop anytime soon, so you must take security controls into your own hands to protect your organization.
The safety strategies listed above should get the job done but also consider hiring a cybersecurity company that offers cyber threat intelligence services for peace of mind.
Digital threat intelligence feeds important information that can help you keep your data safe, but it can’t do much without professional help. That being said, request a demo today and discover how our threat intelligence services can step up your security game!
