Understanding DORA: What Financial Institutions Need to Know (2025)

Table of contents
Resilience is a concept that’s been gaining traction in the cybersecurity space over the years. For EU member states, resilience has become a guiding principle for the European Commission to crack down on cyberattacks and the disruption they cause.
The Digital Operational Resilience Act (DORA) has officially come into force since 17 January 2025 and applies to financial entities and ICT supply chains within EU member states.
The new legislation aims to tackle the rising threat landscape within the financial sector and mitigate risks to both businesses and consumers.

Let‘s explore how the new DORA regulations will affect financial entities and how you can stay compliant.
What is DORA and why is it important for financial entities?
The Digital Operational Resilience Act (DORA) is an EU regulation that was entered into force on 16 January 2023 and came into effect on 17 January 2025 to strengthen the IT security of financial entities and ICT third-party service providers, such as cloud services or data analytics services.
New regulatory technical standards (RTS) were implemented by three European Supervisory Authorities (ESAs)—the European Banking Authority (EBA), the European Insurance and Occupational Pensions Authority (EIOPA), and the European Securities and Markets Authority (ESMA) to ensure that all financial entities such as banks, insurance companies, investment firms and crypto-asset service providers in Europe are resilient in the face of rising cyberattacks.
DORA helps maintain regulatory technical standards in a changing world…
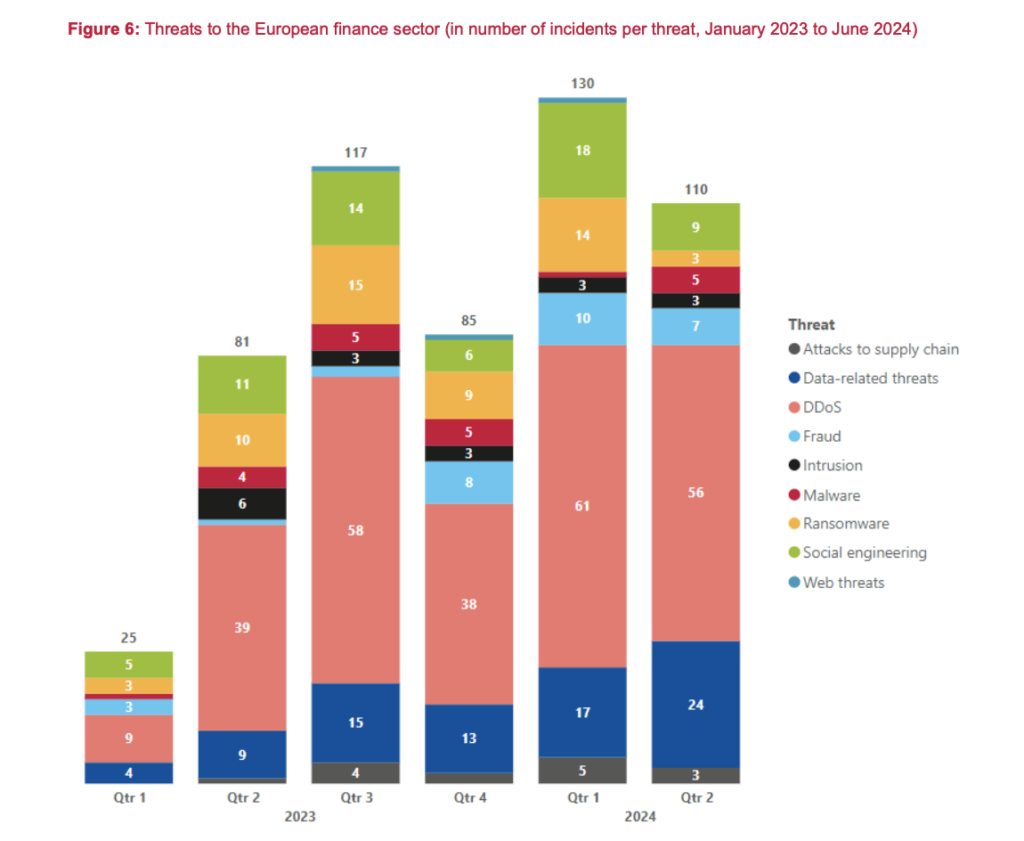
The financial sector is increasingly dependent on technology, increasing operational risk. DDoS attacks from Russian hacktivists in the ongoing war against Ukraine have increased steadily from 2023-2024, leaving financial service providers vulnerable to data breaches.
When there isn‘t a framework to adequately manage cyber risks, this can lead to disruptions of financial services across Europe. The effects of cyberattacks begin to ripple out to all levels of society, including companies, core services, and, in the worst case, affect the stability of the economy.
Implementing DORA regulations across financial services throughout the European Union increases cyber resilience, fostering trust between institutions, businesses, and citizens.
How does DORA differ from previous cybersecurity regulations?
In the ever-changing landscape of cybersecurity regulations, the European Union opted in 2023 to increase the scope of security policies—leading to the creation of DORA.
Before setting DORA regulatory requirements, risk management regulations for financial institutions in the European Union primarily focused on ensuring that firms had enough capital to cover operational risks.
The new regulatory requirements align the former patchwork of initiatives into one holistic framework.
The timeline
Back in 2005, the European Union Agency for Cybersecurity (ENISA) was created to lay the foundation for cybersecurity, acting as a bridge between the public and private sectors.
In 2019, ENISA enacted the Cybersecurity Act (CSA) to provide support to EU Member States in key areas such as the implementation of the NIS Directive, Cyber Resilience Act and Cyber Solidarity Act.
In 2022, the EU updated the framework for cybersecurity across 18 critical sectors with the NIS2 Directive. EU Member States were required to define national cybersecurity strategies to better respond to threats and minimize operational disruption.
The Cyber Resilience Act (2024) established common standards for hardware and software, while the Cyber Solidarity Act (2025) aimed to improve the preparedness, detection, and response to cybersecurity incidents across the European Union.
The new Digital Operational Resilience Act (2025) addresses a critical gap in EU financial regulatory requirements. Before the act, financial institutions were not required to adequately protect against risk from information and communication technology (ICT).
DORA regulations address the regulatory gap for financial services
With the implementation of DORA compliance, financial institutions are now required to follow strict guidelines for safeguarding against ICT-related incidents.
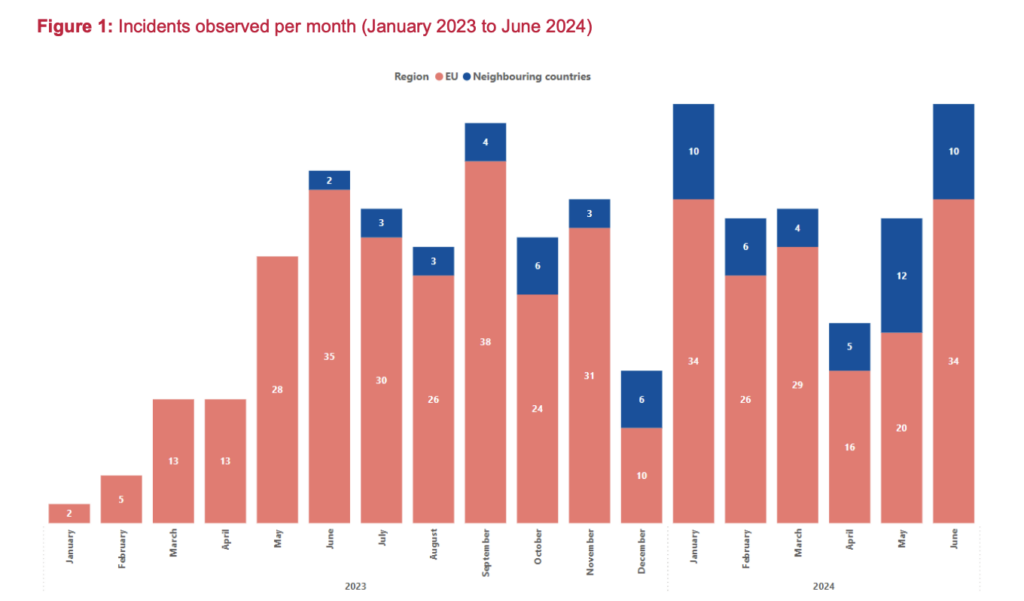
DORA regulations explicitly target ICT systems by introducing rules for ICT risk management frameworks, incident reporting, digital operational resilience testing, and oversight of ICT third-party risks.
Previous NIS2 regulations focused on protecting against external threats, while DORA takes cybersecurity regulation a step further, emphasizing operational resilience.
What are the key pillars of DORA compliance?
DORA compliance covers 5 pillars to address organizational policies and procedures, and specifies regulatory technical standards.
The 5 pillars are:
- ICT risk management: Process mapping of ICT assets for critical business functions.
- Incident reporting: Guidelines for standardizing reporting incidents and cyber threats, including a root-cause analysis and reporting of these improvements.
- ICT third-party risk management: Policy for registering ICT service providers and continuous monitoring of critical ICT third-party service providers.
- Digital operational resilience testing: Regulatory framework for managing threats such as establishing testing programs based on threat-led penetration testing (TLPT).
- Information sharing: Guidelines for sharing cybersecurity information to better address cyber risks and vulnerabilities.
How does DORA impact third-party risk management in the financial sector?
Before implementing DORA, it was identified that the regulatory standards for critical ICT third-party service providers went beyond the empowerment given to the European Supervisory Authorities (EBA, EIOPA and ESMA).
DORA was established to give a more holistic view of threats so that financial institutions could mitigate the potential risks that ICT third-party dependencies may cause.
When outsourcing critical functions, DORA regulation requires financial service providers to:
- Comply with DORA regulations from day one. Financial entities are required to vet third party ICT service providers according to DORA‘s standards. This means that contracts can only be entered into once these requirements are met.
- Conduct ongoing audits. Financial institutions must conduct regular audits to determine the risk of a third-party provider. ICT third-party service providers must cooperate with all ongoing audits overseen by the competent authorities.
- Update third-party contracts with DORA requirements. Contracts with third-party service providers must include detailed information about the service provider and ICT security measures. Such information can include the location where the services will be provided, the locations of data storage, and data protection provisions in case of an attack.
- Include third-party contractors in training programs. Financial entities are required to include their ICT third party providers in training programs to improve cyber resilience.
- Develop water-tight exit strategies. When a contract between the ICT service provider and the financial institution is dissolved, there is still a responsibility to ensure protection against potential threats. Exit plans need to be documented, tested, and reviewed regularly to prove compliance.
- Termination in case of non-compliance. DORA explicitly states that if an ICT third-party provider is unwilling or unable to comply with the regulations, the financial entity must exit the contract.
The mutually collaborative oversight framework helps manage the business relationship between the third-party provider and the financial institution to better mitigate cyber risks such as supply chain vulnerabilities.
What role does incident reporting play in DORA compliance?
Incident management and reporting are a critical component of DORA compliance.
Managing ICT-risks ensures that threats can be quickly identified, responded to, and mitigated, preventing threat actors from compromising business continuity.
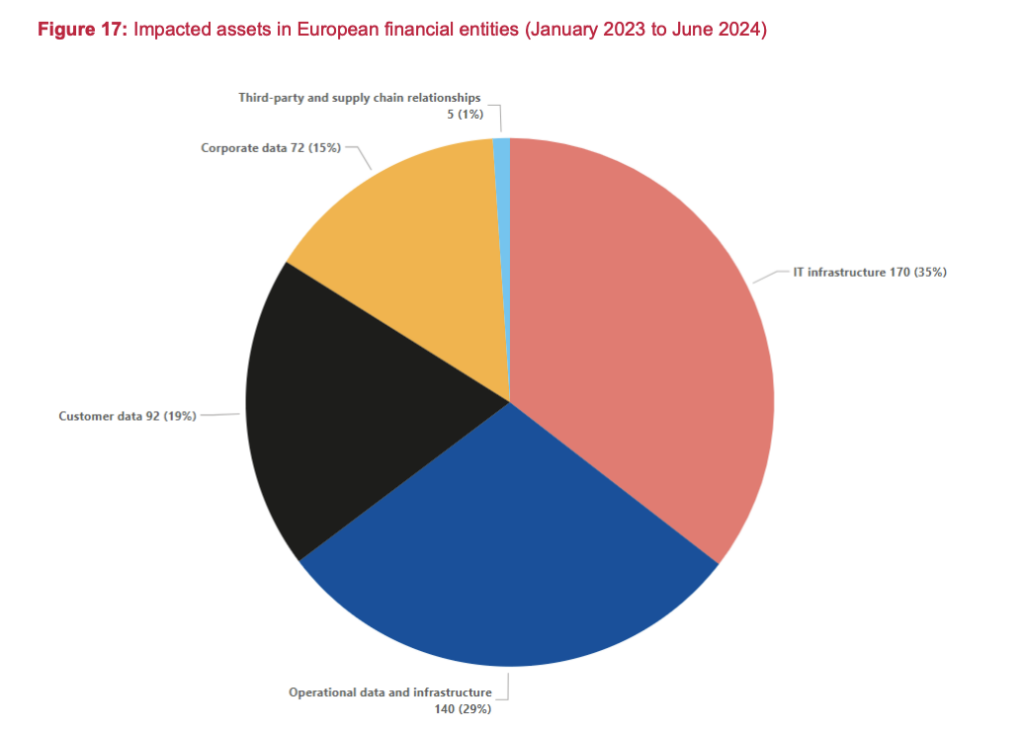
DORA mandates that financial institutions:
- Report on all major ICT-related incidents to the competent authority. Financial entities must be proactive, notifying the authorities when a cyber threat affects service users or clients.
- Inform clients without delay as soon as a major ICT-related incident occurs and outline which measures have been taken to mitigate the incident.
- Analyze the root cause of the incident, regardless of whether mitigation measures have already been implemented.
Incident management is essential for transparency between institutions, the government, businesses, and citizens across all EU member states.
For example, if one bank is targeted with an attack, then other financial institutions across the EU member states can be made aware of potential threats and mitigate them before more services are affected.
What are the potential penalties for non-compliance with DORA?
From online banking to quick mobile payments, every part of our financial lives revolves around the ICT infrastructure provided by financial institutions.
This reliance on digital systems to drive the economy means that any kind of disruption can lead to losses.
Here are the consequences of EU financial institutions failing to comply with DORA:
- Non-compliant organisations can incur fines up to 2% of their global annual turnover or €10 million—whichever is higher.
- Organisations may also face 1% of their daily global turnover as a fine for each day of non-compliance.
- Critical third-party ICT providers may face fines as high as €5 million for failing to comply.
- Regulatory authorities may limit or suspend non-compliant organisations’ business activities until they achieve full compliance.
- In severe cases, non-compliance can result in a temporary suspension of operations, effectively halting business.
Even financial institutions outside the EU may face penalties for non-compliance. Any financial entity operating within the EU, or any business connected to the EU financial sector, is required to integrate DORA compliance to continue operations within the European Union.
How can organizations prepare for DORA implementation?
Implementing the DORA regulatory framework can feel daunting. With so much to consider, it‘s important to lay out a realistic plan to ensure compliance.
Here‘s a checklist to get started:
- Run a risk assessment: Establishing an ICT risk management framework is the core of DORA regulation. Assign clear roles and responsibilities for risk management, including conducting a gap assessment to see any possible blind spots in your existing risk management framework.
- Create a remediation plan: Prioritize actions based on potential risk. Start with the prevalent gaps in your ICT risk management framework and identify how policies can be updated to align with DORA.
- Audit third-party ICT service vendors: Ensure existing and future third-party providers are fully compliant with DORA. You may need to update contracts and internal policies.
- Perform regular penetration testing: Perform a penetration test and scenario-based testing that simulates real-world cyber threats at least once per year.
- Prepare reporting infrastructure: Set up standardized reporting templates and keep detailed records of all your compliance efforts for timely reporting to competent authorities.
- Set up a knowledge base for threat intelligence: Collect and share information for detecting and mitigating cyber threats to better mitigate threats.
- Conduct employee training: Train employees in digital operational resilience to better support your DORA compliance efforts. Training programs include the importance of cybersecurity, and how to protect your organization from cyber threats.
How can AI and automation help in achieving DORA compliance?
Automation streamlines complex legal and compliance tasks, enabling financial services to efficiently address cyber threats, while minimizing operational disruptions and additional costs.
Financial systems can use automation to:
- Improve operational resilience: Proactively manage compliance and mitigate risks.
- Enhance accuracy and efficiency: Minimize human error and increase productivity in achieving continuous compliance.
- Reduce operational costs: Lower the personnel and time required for compliance.
Here‘s how you can use AI for DORA compliance:
- Standardize risk management frameworks. Scale risk management processes with automation across multiple departments and geographic regions.
- Lower incident response time. Monitor key risk indicators in real time to quash threats and improve response time.
- Leverage automated testing. Deploy automatic testing across ecosystems to validate resilience without taking away time and resources from internal teams.
Ensure DORA compliance with CybelAngel’s comprehensive cybersecurity solutions
CybelAngel has a range of cybersecurity solutions that go hand-in-hand with DORA regulations.
Use CybelAngel to generate detailed incident reports including TTPs (Tactics, Techniques, and Procedures), so you can remediate quickly, utilize our unique AI model to gather more detail on threats in real-time, and scan your entire IT ecosystem to flag threats before they escalate.
Learn more about how you can meet DORA compliance regulations with CybelAngel.

