Understanding Dark Web Intelligence: How Cybercriminals Share Intel

Table of contents
In this in-depth guide on dark web intelligence, we explore the core methods used by the cybercriminals to spread methods and strategies, like forums and marketplaces, as well as communication channels like Telegram, Discord, Dread Jabber, Tox, Wickr and more.
Welcome back to part 2 of our 5 part dark web monitoring series. This guide is for CISOs and their teams who are looking for a quick dark web intelligence primer for 2024. In this guide, we’ll dive into newer (and old favorite) ways that cybercriminals share intelligence on the dark web.
Catch up with the entire five part series:
- What is Dark Web Monitoring?[Plus, How Will it Evolve in 2024?]
- Understanding Dark Web Intelligence: How Cybercriminals Share Intel
- Dark Web Takedowns in 2023 | An Overview for CISOs
- Top Threat Actors on the Dark Web | 2023 Recap
- What New Deep Web Vulnerabilities are Targeting Your Brand?
The significance of the dark web in intelligence sharing
The dark web can be used for as a place for ordinary exchanges for example in cases of political dissidence or for users who want to ensure private communication.
But mainly, the dark web is a thriving underground community for cybercriminals.
Platforms such as RECON, Nemesis, Russian Market, Genesis, White House Market, Monopoly, Hydra, Alphabay, Hansa, and Dream, etc. have gained notoriety on the dark web for this very reason. Cybercriminals also utilize surface web sites or privacy-focused hosting solutions, like I2P to share intelligence.
Newer channels are increasing in popularity for different reasons.
Beyond drugs
The dark web is probably best known as a drug marketplace and as a supply chain for black market pharmaceutical sales or other illegal contrabands like weapons.
However, here are some other basic ways it is used by threat actors that are relevant:
- Sales of payment cards at scale (amounting to millions of cards)
- “Fullz” or full identity packs for identity theft
- Supplies/tools to commit cybercrime
- Cybercrime-as-a-service is offered by experienced hackers and cybercriminals
- Malware -as-a-service where ransomware gangs or individuals seek to sell leaked data
This of course is a non exhaustive list.
At CybelAngel we share in-depth Threat Notes prepared by our expert REACT team with our clients to provide contextualized profiles on threat actors, including emerging dark web communities.
Unveiling how cybercriminals communicate on (and off) the dark web
The dark web, all things considered, is a fitting name for the sheer networks of information distribution that exist on it.
Its sheer size can lead to a lot of questions, particularly for non cyber professionals who want to understand if data can be controlled, if it has been leaked onto the dark web.
Here is a basic F.A.Q rundown of what is important to know.
How do cybercriminals and ransomware gangs communicate?
We’ve briefly mentioned that specific forums and marketplaces like RECON, Nemesis, Russian Market, Genesis and White House Market help cybercriminals to stay in the loop.
But what are the differences and what forms of intelligence are shared on each?
First let’s look at the differentiators between the two core elements of the dark web.
What are the differences: Dark web forums and markets?
Cybercriminal marketplaces are typically like e-commerce sites on the internet, where buyers can rate sellers, sites generally have an escrow system, and mirror typical marketplaces seen on the internet.
Forums are more discussion focused (but do note that forums are also used as marketplaces, where discussions take place in the form of in private messages and payment can be made through escrow). Forums are places where cybercriminals typically go to discuss vulnerabilities and share wisdom, tactics and techniques. They also cater to community-led discussion, from selling individual personally identifiable information and login credentials to corporate assessments and secrets.
The main takeaway to note in the difference between marketplaces and forums is that marketplaces are automatic.
Are hackers guaranteed anonymity on dark web forums?
Yes, for the most part.
That is a huge part of their appeal.
According to a CISA report (Cybersecurity and Infrastructure Security Agency), there are several barriers to entering forums and marketplaces on the dark web to ensure that members are legitimate hackers.
These criteria can include:
- Invitation only communities
- Entry is only possible based on nationality or political alignment
- Entry is accelerated with payment
- Vouching is a necessary step for entry
- Hackers may be asked to show proof of cybercrimes committed
However, forums are particularly at risk from law enforcement. Now let’s look at different platforms that exist outside of the dark web and which offer extensive privacy options.
Are there other platforms for exchanging intelligence?
Yes, there are several that offer more convenience for threat actors.
Telegram is an end to end encrypted, cloud based, Russian owned messaging app. It is well regarded for its significant privacy features, like the Secrets Chats and self-destructing messages option. Telegram’s privacy policy emphasizes that “If Telegram receives a court order that confirms you’re a terror suspect, we may disclose your IP address and phone number to the relevant authorities. So far, this has never happened.”
Discord is a voice, video, and text chat app that’s used by millions and beloved by cybercriminals, as a hang out channel where users can push to talk within private rooms. As a popular gaming channel it is widely used by lower skilled actors but it is also used by more sophisticated cybercriminals to exploit vulnerabilities via phishing, malware distribution and much more. Discord’s privacy policy is less liberal in comparison to Telegram and states that, “Discord provides user information to law enforcement when we are in receipt of enforceable legal process.”
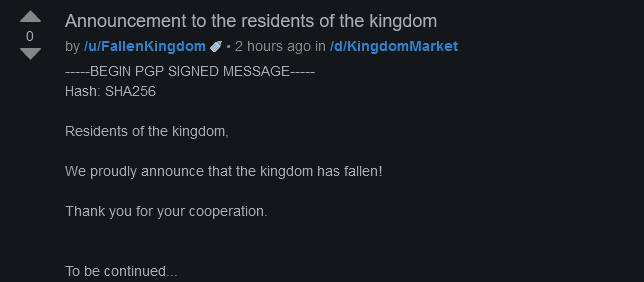
Dread is the Tor version or deep web forum styled like Reddit (it has no affiliation to Reddit). It is a popular dark web platform with a wide range of communities and discussions, including those related to cybercrime. In the screenshot below you can see an example of a post made by German authorities after the seizure of the Kingdom Market marketplace on the dark web.
Jabber is an Austrian computer and mobile app that lets you make, receive, and manage calls on your University phone extension. It also allows you to check voicemail and access other voice services. It benefits from stringent privacy laws based on its H.Q.’s location. It’s privacy statement confirms that, “Austria currently has no data retention laws. It would be illegal for us to retain data longer then directly necessary for running this service. In Austria, a public court can order us to cooperate with law enforcement agencies to help with a criminal investigation. Such an order is only possible if the supposed criminal offense is punishable by at least a year in prison.”
Tox is a secure messaging and video-calling protocol that enables direct communication with encryption. However they provide less leeway than the other contenders in this list. They have confirmed that within their privacy policy that “individual cases may arise in which we are legally obliged to pass on your data on official orders as and insofar as this is necessary for the purposes of criminal prosecution or to avert danger by police or other authorities.”
Wickr is an American owned software company (It was acquired by Amazon in 2021), that provides an instant messaging app to enable users to share end-to-end encrypted and content-expiring messages. Again it does not ensure a Telegram level of data privacy. It’s support centre states that “Wickr is committed to operating in an environment of complete transparency and to cooperating with law enforcement while respecting each individual’s right to privacy.”
Last year mounting evidence suggested that Telegram was a concrete favorite for cybercriminals who exchange and share vulnerabilities when planning cyber attacks.
Why are more cybercriminals sharing intelligence before data breaches?
Is there a method to their madness?
Yes, absolutely.
Typically planning and preparation is precise. Bespoke and encrypted Telegram channels are popular for leveraging large scale attacks. Cybercriminals have the ability to exchange messages individually or in groups, and also send or receive large data files with complete peace of mind.
Reports like the Lancope-Ponemon “Cyber Security Incident Response” report and IBM’s “Cost of a Data Breach Report 2023” highlight how cyber attacks are an extensive business model now.
So it makes sense that they are more and more meticulously planned and supported by shared community intelligence.
IBM data shows that the average costs of global data breaches continues to climb (in 2023 it increased by 15% to USD $4.45M compared to 2020).
What is the best strategy to follow when your data leaks on the dark web?
We’ve created a full incident response guide to this very question which you can read here. It concerns vendor breaches but the same logic applies to all data breaches.
Wrapping up: 4 key takeaways
Here is a quick recap of the key takeaways you need to know.
1: The dark web is a thriving underground community for cybercriminals: Forums like Dread have gained notoriety on the dark web for facilitating cybercriminal intelligence.
2: Cybercriminals communicate through forums and marketplaces: Different platforms on the dark web serve different purposes. Cybercriminal marketplaces function like e-commerce sites where buyers rate sellers, while forums serve as discussion platforms for cybercriminals to share tactics, techniques, and vulnerabilities. These platforms offer anonymity through various mechanisms such as invitation-only communities and vouching.
3: Additional platforms outside the dark web for intelligence exchange: Telegram, Discord, Reddit, Jabber, Tox, Wickr etc. are platforms commonly used by cybercriminals to communicate and carry out scams. Each platform has varying levels of privacy and cooperation with law enforcement, with some being more secure and others more susceptible to surveillance.
4: Cybercriminals share intelligence to support meticulously planned attacks: Sharing intelligence about data breaches and cyber attacks has become essential for cybercriminals to execute their attacks more effectively. With the average costs of data breaches increasing, cybercriminals rely on community intelligence for planning and support for the maximum effect.
That is it for this dark web blog.
Stay informed and follow our dark web monitoring series via our blog and social channels. Follow us on LinkedIn and Twitter to check out all fresh content in this series.

