How to Alleviate Cyber Friction Between the Board, CEO, and CISO

Table of contents
Cyberattacks don’t just stop at the IT team’s desk. They can stall operations. Affect investor confidence. Knock millions off a company’s market value (sometimes overnight).
Ultimately, cybersecurity isn’t a technical issue; it’s a boardroom issue. And yet, in many organizations, there’s a disconnect.
This blog will unpack the barriers to communication between security teams, the board of directors and beyond, along with hands-on best practices for aligning security and business goals, moving forward.
An introduction to cyber friction
The board wants clarity. The CEO wants confidence. The CISO wants to be heard.
But what they often get is cyber friction, with misaligned priorities, misunderstood risks, and meetings where everyone leaves with a slightly different view of what just happened.
This isn’t just inconvenient. It’s risky. Miscommunication between executives and cybersecurity leaders can delay decisions, mask cyber vulnerabilities, and weaken the threat response.
Here are just a few examples.
- Only a third of executives believe that cyber reporting is essential for business growth.
- Less than 50% of CISOs are involved in core business decisions.
- CISOs and CEOs don’t see eye to eye on AI and resilience rules, with a 13% gap in how confident each group feels about staying compliant.
The good news?
This gap can be closed.
But it takes deliberate effort, starting with a shared understanding of why cyber friction exists in the first place.
Cyber friction: The main stakeholders
Before we explore the origins of cyber friction, it’s important to understand the main c-suite roles that are affected by it:
- CISO (Chief Information Security Officer): Leads the organization’s cybersecurity strategy, aiming to protect the business without slowing it down.
- Chief Information Security Manager (CISM) / Security Leader: Works under or alongside the CISO. They manage specific areas like incident response, vulnerability assessments, or information security programs.
- CSO (Chief Security Officer): Controls the organization’s entire security strategy (both physical and digital). This role is senior above the CISO, or it might be merged.
- CIO (Chief Information Officer): Oversees the organization’s overall information technology strategy, sometimes sharing responsibilities with the CISO role for security operations.
- CTO (Chief Technology Officer): Builds and implements technology to serve customers. While the CIO works on internal information systems, the CTO focuses on customer-facing tech.
- CEO (Chief Executive Officer): Is responsible for the company’s overall direction, growth, and performance. Also accountable for risk management—including cyber risk.
- Board of directors: Provides oversight and governance. Board meetings ensure the business is making sound decisions, managing risk well, and protecting shareholder value.
Each of these roles comes with its own priorities.
This makes cybersecurity governance a balancing act—trying to align different goals without letting anything slip through the cracks. And that’s when cyber friction starts to show.
The 4 causes of cyber friction
Cybersecurity friction doesn’t come out of nowhere. It builds through missed signals, unclear reporting lines, and conversations where the business speaks one language, and the security team speaks another.
Let’s break down why it happens.
1. Language gaps between risk and reality
Executives want answers to questions like: Are we exposed? Are we covered? What’s our risk if X happens? But when they get a 20-slide deck on patching cycles or intrusion attempts, the message gets lost.
It’s not that the CISO isn’t doing their job. It’s that cyber risk often isn’t framed in the language of business. And when there’s a translation gap, decisions slow down. Or worse, they get made without the right context.
2. Competing incentives and timelines
The board is focused on quarterly performance. The CEO is managing growth, shareholder confidence, and operational risk. The CISO, meanwhile, is often looking at long-term cybersecurity posture and threat trends.
That means priorities don’t always line up. A security investment might delay a product launch. Or a quick integration might increase risk exposure. Without alignment, security can be seen as a blocker, even when it’s actually protecting the business.
3. Organisational structure can get in the way
In many companies, the CISO reports to the CIO. That can work, but it can also bury the cybersecurity program under broader IT priorities. And when the CISO doesn’t have direct access to the CEO or board meetings, it’s harder to elevate the right risks at the right time.
4. Cybersecurity only gets airtime after an incident
For some boards, the CISO only enters the room when something goes wrong. That reactive model turns cybersecurity into a firefighting exercise, not a strategic function.
(It’s like only checking your brakes after the car skids!)
How to reframe cybersecurity in business terms
If CISOs want a seat at the table, they need to translate security risks into business risks.
When boards hear about “DORA compliance,” “MITRE ATT&CK,” or “API security testing,” they’re often left guessing at the real-world impact.
What they need to hear is: What’s at stake? How bad could it get? What’s the cost if we don’t act?
From technical risk to business impact
Let’s take an example. Instead of saying:
“We’ve identified several unpatched vulnerabilities in our environment.”
Try:
“We’ve found weaknesses in systems that process customer orders. If exploited, they could shut down online sales for days, and cost us £4–6 million in lost revenue.”
That second version does two things:
- It ties the risk to a core business function.
- It gives leadership something to work with (cost, time, and exposure).
This shift builds trust. It also shows the CISO understands the business, not just the tech.
Use familiar terms
Executives are already used to thinking about financial risk, legal risk, operational risk. Cyber risk should be framed the same way.
Instead of saying:
“We blocked 10 phishing emails this month.”
Try:
“We blocked 10 phishing emails this month. But if just one had slipped through, we would have risked a data breach that could permanently damage customer trust. However, our team is ready with a disaster recovery plan to mitigate this.”
Avoid information overload
It’s easy to drown leaders in dashboards, threat maps, or long lists of KPIs. But too much detail creates confusion, not clarity.
Focus on telling a story:
- What’s our current risk posture?
- Where are the gaps?
- What are we doing to close them?
- What do we need—from budget, people, or prioritisation—to do that faster?
This kind of communication shows that cybersecurity isn’t separate from the business. It is the business.
Getting the reporting structure right
Even the clearest cybersecurity strategy will struggle if the reporting lines are wrong.
Who the CISO reports to can shape how risks are prioritised, how quickly decisions get made, and how visible security becomes at the executive level. And right now, that structure varies wildly between organisations.
When the CISO reports to the CIO
In many companies, the CISO reports into the CIO. That can work, but it also comes with challenges.
- CIOs are often focused on enabling the business through tech: systems upgrades, cloud migrations, new platforms. Their job is to keep things running smoothly and support growth.
- IT security, on the other hand, is about managing risk, protecting data, and sometimes slowing things down to do things safely.
That tension can put the CISO in a difficult spot, especially if budget or visibility depends on another executive’s priorities.
Better structures bring clarity
More mature organisations are sometimes moving toward models where the CISO reports:
- Directly to the CEO (47% of CISOs already do this), or
- To a board-level risk or audit committee, or
- Has a dual reporting line (e.g. to both the CIO and the CEO or board)
These structures help elevate cyber risk to the same level as financial or legal risk—where it belongs.
They also make it easier for CISOs to raise concerns, push for investment, and take part in strategic conversations early, not after the fact.
Access matters as much as structure
Formal reporting lines are one thing. But real impact comes from regular access. If the CISO only gets access to board meetings after a breach, it’s already too late.
Instead, CISOs should be part of:
- Quarterly risk assessments
- Incident simulations and penetration testing
- Strategic planning initiatives
- Security training programs
What metrics should CISOs be sharing?
It’s not just what you report. It’s how you report it, and to whom.
CISOs often feel pressure to justify their budget or prove their value. But dumping raw data into a board pack won’t cut it. Executives need insights, not noise.
The key is to tailor your reporting for different audiences. What the board needs is not the same as what the CEO needs. And neither of them want a list of how many firewalls you’ve patched this month.
For the CEO: Focus on business alignment
Your CEO is asking, “Are we protected, and are we positioned to grow safely?”
Your reporting should help them answer that.
Useful cybersecurity metrics for your CEO cybersecurity strategy include:
- Risk reduction over time: Tied to business operations or revenue streams.
- Incident response readiness: Time to detect, respond, and recover.
- Cost vs. risk trade-offs: Show how controls reduce business risk, not just spend money.
- Cyber risk heatmaps: Simple visuals that highlight business impact, not just technical severity.
For example, if you showcase the potential cost of a data breach compared to investing in cybersecurity, then CEOs are likely to pay attention.
Tweet from National Cybersecurity Alliance showcasing data breach costs. Source.
For the board: Show trends, posture, and exposure
Boards need to understand your exposure in plain terms, and how that’s changing. This enables executive cyber risk management at the highest level.
When it comes to CISO and board communication, you should include these cybersecurity metrics:
- Top strategic risks: Link them to business functions (e.g. “Ransomware in our supply chain could halt operations”)
- Benchmarking: Show how your maturity or controls stack up against peers or regulatory frameworks such as NIST or CISA.
- Scenario-based reporting: Identify the likely impact of a specific threat, and describe your response plan.
- Policy and compliance updates: Focus on fast-moving areas like AI, privacy, and operational resilience.
For everyone: Be visual, contextual, and consistent
Use red-yellow-green indicators. Show change over time. Tie every number to a business function, a potential loss, or a recovery plan. This helps decision-makers connect the dots without needing a crash course in cybersecurity.
When done right, reporting becomes more than a formality. It becomes the way you shape decisions, set priorities, and keep cybersecurity on the agenda—not just after an incident, but all the time.
How boards and CEOs can strengthen cybersecurity posture
On the other side of the fence, boards and CEOs can’t afford to treat cybersecurity risk as an IT problem. It’s a business risk that investors, regulators, and customers are watching closely.
Here’s what proactive leadership looks like…
- Treat cybersecurity like a business priority: Allocate time on the board agenda—not just when something goes wrong. Make cyber a standing topic in risk committees, M&A planning, and digital transformation reviews.
- Show interest in potential security issues: When leadership show interest in cybersecurity professionals’ insights, everyone else will pay attention, too.
- Invite CISOs into strategic conversations early: Involving cybersecurity leaders early leads to smarter, more secure business decisions. And it shows that security isn’t a blocker—it’s an enabler when it’s part of the plan from day one.
- Invest before the data breach (not just after): 30% of companies are increasing their cyber budget by 6-10% this year. Invest in cybersecurity proactively, instead of patching things up when the damage is already done.
- Understand the bigger picture: Cyber incidents can trigger everything from stock price drops to regulatory investigations. And recovery is expensive. Spending on cybersecurity could save countless headaches in the long run.
Gartner has found that 69% of CIOs and technology executives will prioritize cybersecurity risks in 2025. Other boards need to follow their example, or risk falling behind.
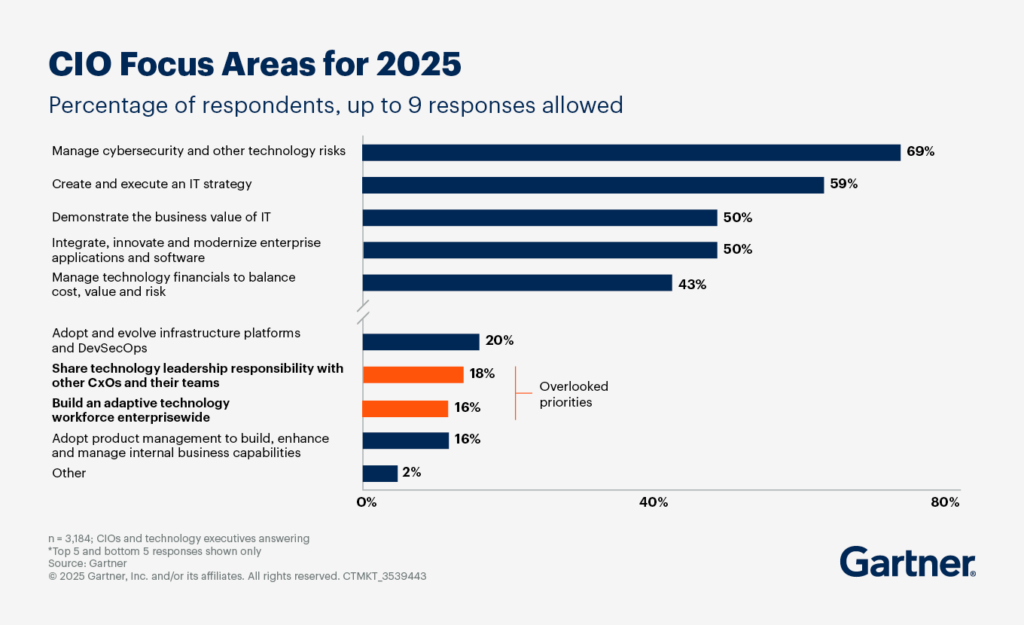
Gartner report showing CIO focus areas for 2025. Source.
Closing thoughts
Closing the gap between the board, CEO, and CISO isn’t just about better reporting. It’s about shared responsibility.
When leadership teams speak the same language, cybersecurity stops being a point of friction and becomes a source of strength.

