30 Essential Cybersecurity Metrics to Track as a CISO

Table of contents
Find out 30 of the best KPIs to track in real time to stay ahead of cyber attacks and better control your risk management as a CISO.
“If you have to forecast, forecast often.”
Edgar Fiedler
An organization’s cybersecurity is a complex and always evolving beast.
But one thing that never changes?
It is the constant misalignment between CISOs, CIOs, and stakeholders over what cybersecurity metrics are actually important.
In this blog we rundown what security metrics are critical to measure in real-time, ad-hoc, and what you can side-step. We’ll also be covering some extra KPIs that can help cement smoother relationships with your board of directors and non technical reports.
Here is the full outline of KPIs here if you prefer to skim:
- Breach likelihood
- Incident rate
- Cost per incident
- Risk exposure
- Severity level of breaches
- Percentage of assets in inventory within policy
- Percentage of privileged accounts managed within policy
- Percentage of high-risk patches implemented within policy timeframes
- Mean time to detect (MTTD) security incidents
- Mean time to contain (MTTC) security incidents
- Mean time to remediate/resolve incidents
- Percentage of data centralized
- Percentage of data encrypted
- Backup frequency and recovery speed
- Percentage of employee/customer data exposed on the Dark Web
- Number of unidentified devices on the network
- Number of devices with unpatched software
- Rate of false positives in security alerts
- Number of threats detected and prevented by endpoint solutions
- Results from penetration testing and red team exercises
- External security ratings compared to peers
- Compliance with regulatory requirements
- Application security testing scores
- Volume of actual incidents versus intrusion attempts
- Results from tabletop exercises and attack simulations
- Percentage of watchlisted (high-risk) users
- Level of employee security awareness (e.g. phishing test results)
- Frequency of security awareness training
- Depth of network segmentation (e.g. IoT devices)
- Return on investment (ROI) for cybersecurity initiatives
- Bonus tip
Let’s dive into the full list.
1: Breach likelihood
Breach likelihood indicates the likelihood of a security breach if current attack trends continue, for example, like the recent Salt Typhoon APTs.
It is a predictive metric that estimates the number of potential security incidents an organization may face in the future, taking into account existing risks and security controls.
Here is a rough guide to calculate breach likelihood yourself:
- The total number of incidents (both successful and failed breach attempts)
- Third-party risk assessment scores
- Data from User and Entity Behavior Analytics (UEBA) solutions
You can use predictive modeling and analytics to determine the likelihood of future breaches and also potential associated costs.
2: Incident rate
The number of security incidents over time, i.e. an incident rate, is a granular metric that measures that provides colour into the frequency and volume of security incidents in your organization.
You can use it to measure:
- Increasing incidents
- Decreasing incidents
- Moderately stable incidents
It is a solid KPI to review your classic vulnerabilities like malware infections, data breaches, DDoS attacks etc.
3: Cost per incident
Number three is a no brainer for any CISO, especially when reporting on cybersecurity risks for upper management and boards.
IBM’s “Cost of a Data Breach Report 2024″ indicates that the average time to identify and contain a data breach remains approximately 277 days (about 9 months). They cite that the global average cost of a data breach in 2024 was USD 4.88 million, a 39% increase since 2020.
4: Risk exposure
Risk exposure is a risk looks at the potential for an organization to suffer losses from various cybersecurity threats.
It’s often calculated using the formula: Risk Exposure = Probability of Risk Occurring x Potential Loss/Impact. It’s goal is to help you make more informed decisions when it comes to your risk management strategies.
Did you know that you can avail of our M&A Cyber Due Diligence service? Find out more.
5: Severity level of breaches
Security teams like to use frameworks like the Common Vulnerability Scoring System (CVSS) to assess and quantify the severity of security vulnerabilities and incidents.
These can be boiled down to 4 main levels:
- Level 1: Low Severity (Minimal impact)
- Level 2: Medium/Moderate Severity (More significant impact)
- Level 3: High Severity (Significant harm)
- Level 4: Critical Severity (Catastrophic impact)
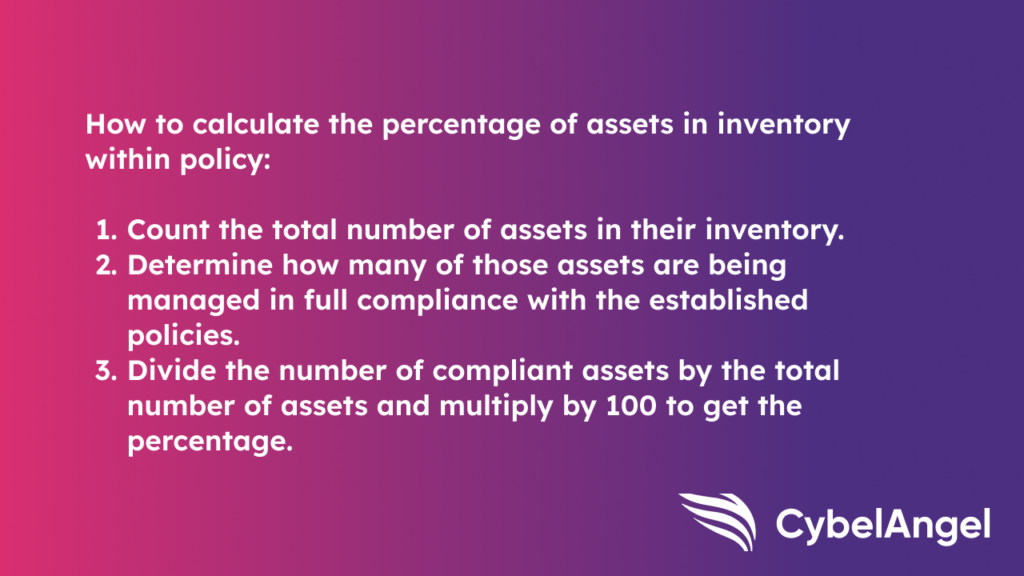
6: Percentage of assets in inventory within policy
Essentially this KPI records the percentage of company assets that are carefully accounted for, managed, and maintained in accordance with your organization’s policy.
It lets you know if you are on track with asset tracking, maintenance, and lifecycle management.
7: Percentage of privileged accounts managed within policy
PAM or Privileged Access Management (PAM) programs need to be accessed by CISOs to make sure that these privileged users’ access to sensitive systems meets cybersecurity program standards. It also needs to be automated! Forrester have reported on how “Manual paper- or spreadsheet-based solutions are insecure, expensive, don’t scale, and can’t be sufficiently audited.”
Here is a standard calculation to keep an eye on PAM programs:
(Number of PAMs within policy / Total number of privileged accounts) x 100
8: Percentage of high-risk patches implemented within policy timeframes
This KPI simply means how effectively you patch vulnerabilities within your organizations patch management policy.
It strong reflects on your cybersecurity posture in how quickly you address critical vulnerabilities, comply with policy and your overall patching cadence.
9: Mean time to detect (MTTD) security incidents
MTTD is a classic KPI in that it measures the average time it takes for an organization to detect an incident after it has occurred.
What you want is a low MTTD that showcases how fast your threat detection capabilities are. A short detection time= effective monitoring and rapid intrusion detection.
Good to know
Averages like MTTD and MTTR can be too technical for your board so keep everyone on the same page when it comes to understanding their exact meaning.
To share your organization’s MTTD you just need to measure the time between when each incident began and when it was discovered.
10: Mean time to contain (MTTC) security incidents
Mean time to contain (MTTC) is a benchmark for the typical time it takes for an organization to halt the spread of a security incident after it’s been detected. What you want is a low MTTC that showcases how swiftly your incident response team can stop a threat in its tracks.
Good to know
MTTC provides a more comprehensive view than MTTD alone, as it encompasses both detection and initial response. It’s a key indicator of your organization’s ability to limit the potential damage from security incidents.
For example, the recent Salt Typhoon attacks that targeted Verizon, AT&T and Lumen Technologies is an interesting use case to share with your team when explaining MTTC.
11: Mean time to remediate/resolve incidents

Mean time to remediate/resolve incidents (MTTR) measures the average time it takes for an organization to fully address and resolve a security incident from detection to completion.
Again, what you want is a low MTTR that showcases how efficiently your team can diagnose, contain, and resolve security issues.
When you have short resolution time, you showcase efficient vulnerability management.
Overall, MTTR provides a more comprehensive view than just detection time alone, as it encompasses the entire incident lifecycle.
12: Percentage of data centralized
This KPI measures the proportion of an organization’s total data that has been consolidated into a central repository or system from various security systems, and sources. A positive measurement means that data is more accessible for smoother decision-making.
13: Percentage of data encrypted
This metric transmits the total percentage of data in your organization that has been encrypted (at rest or in transit).
The higher percentage, the better it is for your security policies as it indicates reduced vulnerability to data breaches and unauthorized access. It also means you are meeting compliance standards.

14: Backup frequency and recovery speed
This is a no brainer and especially important when it comes to mitigating attack vectors.
In our annual report, we covered the important of backups.
Organizations that utilized physical backups for ransomware attacks in 2023 saw reduced average recovery costs to $1.6 million compared to those who paid the ransom. Additionally, 45% of these organizations successfully recovered within a week, showcasing the effectiveness of using backups in mitigating the impact of such cyber incidents.
It is advised to set internal KPIs for these two indicators.
This could look like:
- Backup Frequency: Aim for 100% (daily backups) for critical systems
- Recovery Speed: Set a target based on your Recovery Time Objective (RTO), e.g., 500 GB/hour
15: Percentage of company data exposed on the Dark Web
This KPI measures the proportion of an organization’s company data that has been found exposed on the Dark Web. It could resemble supply chain logistics, leaked plan sites of your company, sensitive customer data etc.
CybelAngel’s Dark Web Monitoring service is designed to detect and track this type of exposure. Find out how we scan and supply our customers with relevant incident data.
16: Number of unidentified devices on the network
If you want to cover all your potential security vulnerabilities and unauthorized access points on your network you need to track and monitor unidentified devices. Cybersecurity awareness training around personal devices and risky IoT devices is essential to protect your company’s network.
Learn more about these risks in our guide, ‘What are the Top Risks of Internet-Connected Devices?’
17: Number of devices with unpatched software
If you want to reduce your attack surface, timely patching cadences are essential.
There are a few simple steps to analyze this KPI:
- Implement vulnerability scanning tools for broader assessment
- Delegate a review of results against known vulnerabilities and available patches
- Track these patch levels across all areas of focus
- Keep an eye on trends so you bolster the feeling of preparedness
18: Rate of true positives in security alerts
The rate of true positives in security alerts directly reflects the accuracy and efficiency of an organization’s security detection systems.
You need to review the ratio of confirmed threats (true positives) versus the total number of generated alerts. In terms of what strategy works best, review en masse how your vendors communicate true positives.
19: Number of threats detected and prevented by endpoint solutions
How well is your endpoint protection software identifying and neutralizing potential threats? Ideally you want a high detection and prevention rate to stay safe and compliant.
20: Results from penetration testing and red team exercises
Simulating real world cyberattacks is a helpful exercise to review response times, downtime, controls, firewall issues, and generally prioritize how your team remediate together. A solid cybersecurity strategy should also prioritise company wide phishing attack exercises. After all, around 3.4 billion phishing emails are sent daily by cybercriminals, well over 1 trillion malicious emails a year.
Monitoring these metrics will also help you to stay compliant- a double win!
21: External security ratings compared to peers
According to Gartner, quantitative cybersecurity ratings are becoming more and more valued in the boardroom when assessing business relationships and risks.
This score generally ranges from 0-950. If you are looking for more specific advice on board reporting check out our latest guide for more colour on this topic.
22: Compliance with regulatory requirements
This is usually a very broad KPI but an essential piece of the puzzle. You need to create an industry specific and local framework for implementing and maintaining robust cybersecurity practices at your organization.
Reporting on your security posture without full visibility here is a no go.
23: Application security testing scores
AST scores help shine a light on the biggest issues in your applications so that your SOC teams can focus resources on addressing high-risk issues first.
Ideally, after reviewing your low score you’ll be be able to further highlight weaknesses in development of the app.
Good to know
They are also helpful when reviewing vendors and third parties to get a strong sense of their posture.
24: Volume of actual incidents versus intrusion attempts
With this KPI you want to see a decreasing ratio of incidents to attempts, while an increase could signal vulnerabilities.
How do you track this KPI? Here is what to do:
- Log intrusion attempts: Use IDS, firewalls, and security tools to record breaches.
- Record incidents: Document all security incidents and their impacts.
- Calculate your ratio: Divide actual incidents by total intrusion attempts for a specific period.
- Use SIEM tools: Aggregate and analyze data from various sources.
- Regular reporting: Consistent reports will allow you to spot trends.
25: Results from tabletop exercises and attack simulations
This KPI provides you with tangible evidence of how you and your team work in response to high level incidents. Looking at your overall results is a window into the agility of your team to response to high level incidents.
The minimum recommended frequency is annually, as suggested by bodies like NIST.
For helpful resources check out:
- CISA Tabletop Exercise Packages
- Artificial Intelligence Cyber Tabletop Exercise Series
- NCSC’s “Exercise in a Box
26: Percentage of watchlisted (high-risk) users
This may seem like a niche KPI but reviewing the proportion of users within an organization who have been flagged as high-risk or watchlisted will pay dividends. The people on this list can include:
- Previous employees who left the company
- Users with suspicious network activity
- Users with access to confidential data
- Users with a long history of poor behaviour
27: Level of employee security awareness (e.g. phishing test results)
The human element of cyber error is a huge link in the vulnerability chain. You should measure and report on how awareness and training initiatives are progressing to refocus you, your SOC team, and everyone else. For example sharing phishing test success rates with your entire organization is a great way to reinforce your messaging as a cyber leader.
Did you know that since ChatGPT’s launch, phishing email volume increased by 1,265%? Keep your team primed and poised for attack at all times.
28: Frequency of security awareness training
The power of an agile cybersecurity strategy lies in its training programs.
- Annual training: Mandatory annual cybersecurity awareness training is a basic recommendation.
- Ad hoc refresher training: Advised based on seniority and accesses etc.
- Situational training: Promotions, team changes or even changes to your cybersecurity environment means that you need to organise further training in this case..
- Newbie training: NIST recommends training for new hires within their first two months.
- Continuous learning: Everyday is a school day in cybersecurity and so most security measures mean this is a given.
29: Depth of network segmentation (e.g. IoT devices)
When it comes to protecting your attack surface, monitoring your levels of segmentation is essential especially when it comes to IoT devices.
Here is a mini guide to measuring this KPI:
- Number of VLANs
- Granularity of access controls between segments
- Percentage of IoT devices isolated in dedicated segments
- Frequency of segmentation policy updates and reviews
30: Return on investment (ROI) for cybersecurity initiatives
Perhaps the most obvious metric of the list. Calculating ROI is crucial for garnering budget support and ensuring cybersecurity investments.
By highlighting how specific investments will reduce risk or improve compliance, you’ll reduce friction for decision-makers to see the value in funding them.
Fun fact, a Forrester study found that CybelAngel offers customers a ROI of 359% of their investment, representing a total NPV of $2.66m.
31: Bonus tip
False positives are the cyber equivalent to a buzzing fly in your ear.
For CISOs, relying heavily on metrics like false positives can be misleading and inefficient. Despite a high volume of keyword mentions found on Github, which had over 94 million users in 2023, 98% of these were false positives—harmless references without real threat. Advanced technology like CybelAngel’s helps sift through this “noise” to provide clients with actionable, genuine risk alerts, resulting in a more-productive 11% rise in true positive alerts year-over-year, focused on actual risks on Github.
Prioritizing true risks and forget about false positives as a KPI in your eyeline.
Cybersecurity performance matters
Advocating for your team’s needs and resources, and sharing important metrics you’ve all achieved helps everyone.
You can find more palatable ways to communicate with management in our upcoming Ebook, The CISO Primer.
For now though catch up with the other blogs in this series:
- Your First 100 Days on the Job as a CISO [A Free Checklist]
- How to Navigate Board Meetings: A Primer for CISOs
Wrapping up with a KPI health check
Ultimately the best advice when it comes to sharing cybersecurity metrics comes from CybelAngel’s CISO, Todd Carroll, “A complex KPI which has to be explained will be ignored or misunderstood.”
Your valuable KPIs are only as valuable as your audience perceives them.
Whether you distill complex metrics down for board members, or cover more expansive topics for your SOC team, remember to:
- Use trusted data providers (that includes vendor security metrics!)
- Set up automated reminders and notifications for your key security performance indicators
- Constantly test and audit your incident response strategy to stay primed for real time incident reporting
- Key performance indicators are nothing without the buy in of your team! Get your team invested by regularly sharing key information security and cybersecurity improvements
With the right KPI best practices, you can swiftly protect your organization from external threats and safeguard business operations for the future.
