Infostealer Credentials: The Hacker’s Disguise

Table of contents
If you celebrate Mardi Gras, you know how fun it is to put on a mask and pretend to be someone else for a little while. At the end of the night, the mask comes off and you’re back to your day-to-day life. But for hackers, every day is Mardi Gras — and with stolen credentials, you are the disguise they use to get what they want. In 2022, more than 3,000 companies fell victim to ransomware attacks* and stolen credentials were the number one attack vector. Also referred to as “infostealer credentials,” they’re the ideal choice for a hacker — a costume that enables malicious actors to infiltrate your infrastructure undetected. Take a look at the screenshot below; these are actual stolen credentials that CybelAngel has found. 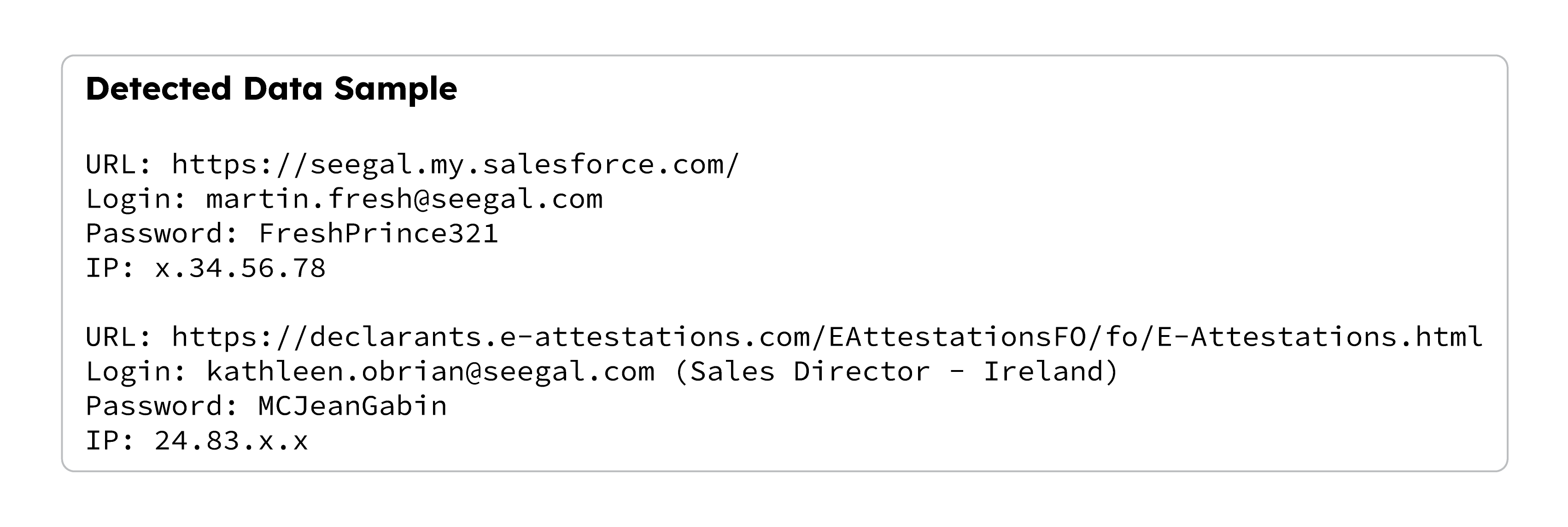 Of course we’ve anonymized them for security, but if we hadn’t, you could use this information to access real systems. After all, as far as those systems know, you’d be “Martin the CISO” or “Kathleen the Sales Director.” Disguises don’t get any better than this.
Of course we’ve anonymized them for security, but if we hadn’t, you could use this information to access real systems. After all, as far as those systems know, you’d be “Martin the CISO” or “Kathleen the Sales Director.” Disguises don’t get any better than this.
The World is the Hackers’ Carnival
Infostealer malware has led to a parade of success for cybercriminals. From Medibank to Uber, the biggest attacks we saw in 2022 were initiated through stolen credentials that were then sold on the dark web. The situation is getting worse via multi-factor authentication (MFA) attacks — in fact, according to the Microsoft Digital Defense Report 2022, we know that “Malware as a service has moved into large-scale operations against exposed IoT and OT in infrastructure and utilities as well as corporate networks.” The same report estimates that “the volume of password attacks has risen to an estimated 921 attacks every second — a 74% increase in just one year.” It’s important to recognize that titles and roles have little to do with the issue. It’s always Fat Tuesday for hackers — they’ll gorge on any credentials they can get and that means everyone in an organization is at risk. If you have employees, you are exposed. They can and will be impersonated. But don’t despair; you still have options to protect yourself.
Unmask the Cybercriminals
In an ideal world, a hacker would never get your credentials, but once they do, you need to act fast. Just because a hacker dons a mask, it doesn’t mean he gets to attend the ball. With the right tools, you can intercept compromised credentials before they are weaponized. CybelAngel’s Account Takeover Prevention module scans unprotected databases and detects data dumps in the clear and dark web. We’ve already detected over 13 billion exposed, stolen, and compromised credentials, including OKTA, ADFS, and VPN credentials. Every week, our scanners pick up 20M credentials from infostealer malware. More importantly, our customers tell us that we’ve detected credentials no other competitor was able to send their way. Not just random data, but insights that fuel remediation efforts:
“The incident reports on Infostealer credentials CybelAngel sent were critical. They contained a lot of information that enabled us to act quickly on them.” – Cybersecurity Engineer Manager, IT Services
Our world-leading External Attack Surface Management platform is designed to give you the visibility you need into critical exposures through actionable insights. Additionally, we’ll put a dedicated analyst at your service to help you navigate and contextualize the threats. Costumes and disguises don’t belong in the business world. Learn more about CybelAngel’s Account Takeover Prevention solution and let us show you how it can put a stop to the hackers’ carnival and keep you in control of your credentials.
* Source: CybelAngel REACT Team investigation. This number is just the tip of the iceberg, as it doesn’t take into consideration companies who pay the ransom (so the shaming post never appears) or data from ransomware gangs who don’t operate a blog.