The Ultimate Compliance Checklist: NIS 2 and DORA Standards

Table of contents
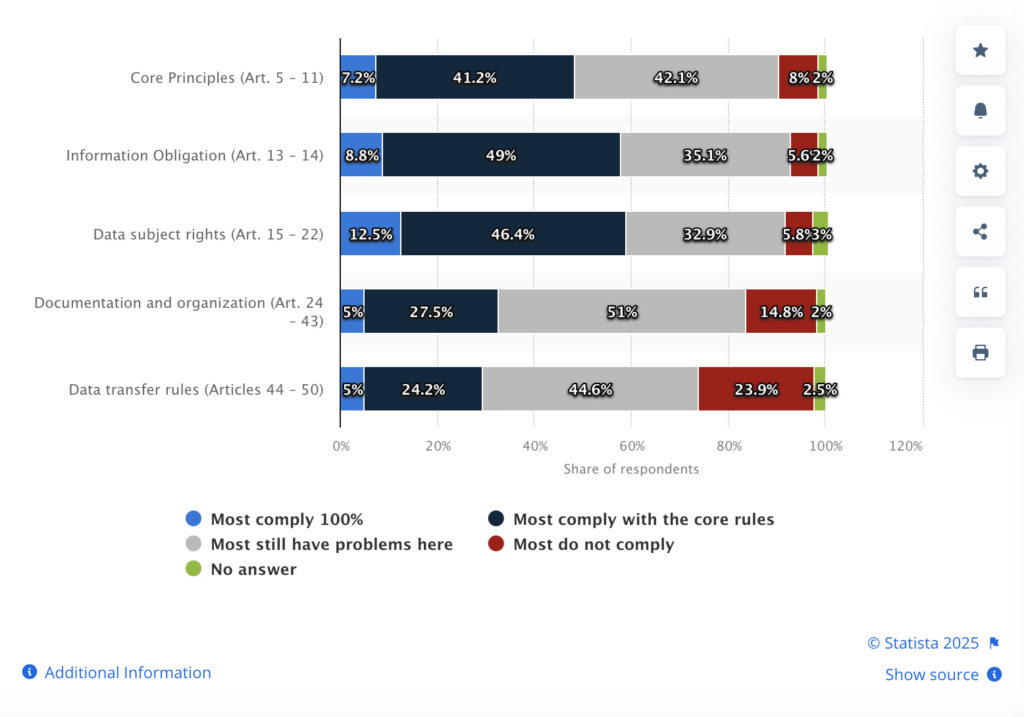
How compliant is your organization?
In 2023, 45% of respondents stated that most companies were experiencing problems with GDPR compliance, and 24% stated they were not compliant at all.
As the demand for compliance grows, how can organizations stay on top of risk mitigation?
In this checklist guide, we‘ll share our insights to support the implementation of NIST 2 and DORA guidelines.
Using DORA and NIST 2 to address cyber threats…
A cybersecurity checklist is essential to improving your organization‘s security posture and addressing potential threats, such as data breaches that can result in losses.
The Digital Operational Resilience Act (DORA) used in conjunction with the NIST 2.0 framework, can support organizations with security best practices and streamline security efforts.
What is DORA compliance?
DORA is an EU regulation that took effect on 17 January 2025 to strengthen the IT security of financial entities and ICT third-party service providers, such as cloud or data analytics services.
The regulatory requirements aim to manage cyber risks for financial institutions holistically across the European Union.
What is the NIST 2 framework?
The NIST Cybersecurity Framework 2.0 was released by the U.S. National Institute of Standards and Technology (NIST) on February 26, 2024.
The framework supports organizations in managing their cybersecurity risks by offering adaptable high-level outcomes to enhance assessment, prioritization, and communication of cybersecurity efforts.
How can DORA and NIST 2 regulation help your organization?
Organizations must adhere to certain regulatory requirements to provide security assurance to clients and customers and meet stringent security requirements.
Here are the benefits of using both frameworks together to achieve compliance:
- Improved governance: DORA‘s new Govern function helps organizations know what is happening in each corner of their technology ecosystem. While NIST 2 focuses on integrating cybersecurity into systems and management. Governance provides structure for an organization to build cyber resilience and a proactive cybersecurity posture.
- Comprehensive risk management: Using DORA and NIST 2 together supports organizations in creating a well-rounded risk management strategy. Holistic risk assessments ensure that vulnerabilities are uncovered before they can be exploited.
- Better incident response: Detecting and responding to cyber threats promptly can improve the organization‘s recovery from cyberattacks. Implementing DORA and NIST 2 supports organizations in making incident response a priority and not an afterthought.
- Third-party oversight: DORA imposes strict monitoring on third-party ICT providers, while NIST 2 helps evaluate third-party risks as part of an overall cybersecurity program. This dual layer of oversight reduces supply chain vulnerabilities.
- Regulatory compliance: Both frameworks help ensure alignment with international regulations and standards, boosting trust with stakeholders and reducing potential legal risks.
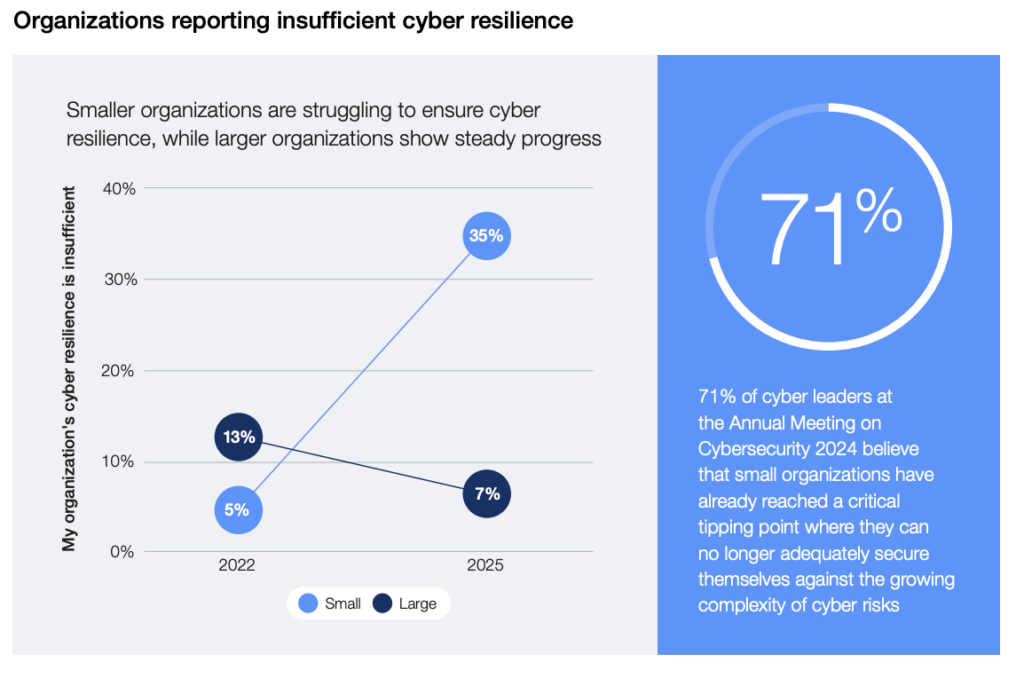
49% of public-sector organizations indicate they lack the necessary talent to meet their cybersecurity goals. Utilizing a framework to mitigate cybersecurity risk can be helpful to organizations of all sizes to maintain coverage without requiring too many additional resources.
The end goal of guidelines such as NIST 2 or DORA is to enable compliance from the ground up, to deter cybercrime and to maintain public confidence.
Cybersecurity Audit Checklist: 12 ways to implement the NIST 2 framework & DORA
How do you begin implementing NIST 2 and DORA? Where should you start?
To start implementing better security awareness and enhanced network security, take a look at our comprehensive cybersecurity checklist to achieve better compliance and security.
1. Scope Determination
The organizational context for implementing NIST 2 includes considering the mission, stakeholder expectations, dependencies, and legal, regulatory, and contractual requirements surrounding the organization’s cybersecurity risk.
Under DORA, determining the scope is included under the Govern core **function to establish clear frameworks for decision-making, accountability, and transparency.
- What is the organization‘s mission? Consider the company‘s vision and mission statements and marketing strategy to identify risks that might impede implementation.
- Who are the stakeholders that will have an impact on the cybersecurity plan? This can involve identifying stakeholders that could pose a risk to implementation and adoption and the cultural expectations of employees.
- What are the cybersecurity expectations of internal and external stakeholders? Consider the ****privacy expectations of customers, business expectations of partnerships, and compliance expectations of regulators.
2. Gap Analysis
Systematically evaluate your organization’s current security measures against industry standards to identify weaknesses and areas for improvement. Compare your current protocols and measures against the NIST 2 and DORA frameworks to identify gaps.
3. Develop a comprehensive risk management plan
Risk management offers a strategic approach to identify, analyze, and address an organization’s cyber vulnerabilities to minimize threats.
Developing a risk management plan involves:
- Identifying potential risks and conducting a risk assessment to evaluate the likelihood of risks impacting the business.
- Assessing risk management strategies such as strong security controls, data encryption, and regular system updates.
- Documenting risks as they occur, such as using MITRE to support cataloging of cyber risks.
4. Establish clear roles and responsibilities
To implement best cybersecurity practices, it‘s important to establish clear roles and responsibilities to foster accountability throughout the organization.
- Identify how leadership is responsible and accountable for managing cyber risk.
- Document risk management roles throughout the organization for increased transparency.
- Conduct periodic management reviews to measure areas for improvement.
5. Identify asset management risks
Managing asset risks refers to the process of managing an organization’s digital and hardware assets to reduce the risk of an attack.
- Maintain an up-to-date inventory of all digital and physical assets, including IoT devices, software, and services.
- Continuously monitor platforms for software and service inventory changes.
- Maintain documentation of expected network ports, protocols, and services.
- Create a plan for securely destroying information and hardware when it is no longer needed.
6. Establish an incident response plan
In both NIST 2 and DORA frameworks, managing and responding to incidents is a key component of risk mitigation.
Developing an incident response plan involves:
- Incident management: Detect, categorize, and prioritize risks within existing systems.
- Incident analysis: Identify the root cause of the incidents and actions to be taken.
- Incident response reporting and communication: Communicate the incident to relevant stakeholders and authorities and the steps being taken to contain the threat.
- Incident mitigation: Focus on mitigating damage from risks, including running antivirus software and remediating compromised endpoints to contain threats such as malware.
- Incident recovery plan: Identify how to restore compromised data, such as maintaining the integrity of backups. This stage includes detecting indicators of compromise (IoC) like file corruption or other integrity issues.
7. Create an organizational cybersecurity policy
A cybersecurity policy sets out guidelines and procedures that an organization follows to protect digital assets and sensitive information from cyber threats.
A robust cybersecurity policy should include:
- Firewalls: Monitor incoming and outgoing network traffic to better prevent unauthorized access.
- Strong passwords: Ensure that all passwords meet security standards and that multi-factor authentication (MFA) is enabled for all users.
- VPNs (Virtual Private Networks): Provide secure network connection internally and externally.
- Antivirus/Antimalware Software: Proactively prevent potential threats such as malware attacks, ransomware attacks, and other tactics used by cybercriminals.
- Intrusion Detection/Prevention Systems (IDS/IPS): Implement IDS for real-time monitoring of network traffic to detect suspicious activities.
- Network Access Control (NAC): Limit unauthorized access by controlling permissions to the network based on user identity to reduce threats from insiders.
8. Strengthen third-party risk management
Third-party vendors pose a risk to organizations if they are not kept to the same security standards as internal stakeholders.
- Apply the principle of least privilege: Users are given the least level of access to do their job effectively.
- Utilize a VPN: Ensure secure remote access protocols by utilizing a VPN to provide secure, encrypted connections for external vendors.
- Involve third-party service providers in cybersecurity measures: Communicate and involve third-party providers in planning and communicating your cybersecurity plan to ensure all parties are compliant.
- Security assessments: Conduct security assessments of your third-party vendors to ensure compliance.
9. Perform risk assessments
Reduce security breaches to critical systems by conducting regular risk assessments.
When beginning a risk assessment, consider the following:
- Assess threats and vulnerabilities to critical assets: Identify potential threats to sensitive data and vulnerabilities within current systems.
- Implement security controls: Apply measures like firewalls, encryption, and multi-factor authentication to mitigate risks.
- Conduct regular penetration tests: Periodically test your security protocols through simulated attacks to identify vulnerabilities and solutions to cyberattacks such as phishing or malware attacks.
10. Conduct compliance audits
To meet compliance standards, organizations must meet certain compliance requirements. For example, healthcare providers must consider HIPAA, and organizations conducting business within the European Union must consider GDPR.
Organizations can consider the following:
- Communicate compliance standards to all internal stakeholders and external vendors.
- Integrate compliance requirements into existing security policies.
- Identify gaps within existing systems, policies, and protocols and make a plan to address them.
- Evaluate compliance often to ensure continuous protection.
11. Implement operational resilience measures
Operation resilience refers to security architectures that are managed with the organization’s risk strategy to bounce back after an attack. Resilient organizations continually work to adapt to changes and risks that can affect business continuity.
Resilience measures can include:
- Risk assessments: Regularly evaluate risks and update measures based on emerging threats.
- Penetration testing: Simulate cyberattacks to identify and address vulnerabilities.
- Regular backups: Continuously back up critical data in real time, including securely storing backups offline to prevent corruption from attacks.
- Employee training: Conduct cybersecurity awareness programs to minimize risks like phishing.
- Tabletop exercises: Test incident response plans through simulated scenarios.
- Audits and compliance checks: Align with regulations and frameworks, such as GDPR, ISO 27001, or PCI DSS.
Resilience measures should be implemented holistically across the organization for proper data protection and data security.
12. Facilitate organizational change and awareness
To promote change and awareness, organizations must provide cybersecurity awareness training to keep cybersecurity incidents to a minimum.
Drive organizational change and cybersecurity awareness by:
- Conducting regular training: Provide basic cybersecurity awareness and training to all users, including employees and third-party vendors.
- Training users to recognize tactics used by cybercriminals: Users should be aware of tactics such as social engineering attempts and be able to identify suspicious activity such as phishing emails. Ensure users comply with basic cyber security hygiene like patching software, choosing secure passwords, and protecting user credentials.
- Continuously improving efforts: Periodically assess or test users on their understanding of basic cybersecurity practices, including annual refreshers or specialized training for identified vulnerabilities.
Ensure DORA compliance with CybelAngel’s comprehensive cybersecurity solutions
Navigating the many regulatory requirements needed to become compliant is challenging for every organization. DORA and NIST 2 are recent examples of regulatory compliance becoming the norm across multiple sectors.
How will you remain compliant as new benchmarks arise?
CybelAngel‘s External Threat Intelligence platform can improve your security posture and mitigate risk:
- Prioritize risk by level of severity to streamline compliance documentation.
- Identify the origin of each threat to support operational resiliency.
- Notify users of compromised passwords to prevent data breaches.
Discover how CybelAngel works seamlessly with the DORA and NIST CSF 2.0 framework to improve your regulatory compliance.

