PLAY Ransomware: The Double-Extortion Gang

Table of contents
There‘s a new ransomware player on the scene. PLAY ransomware has wreaked havoc on organizations across the globe, resulting in major financial loss.
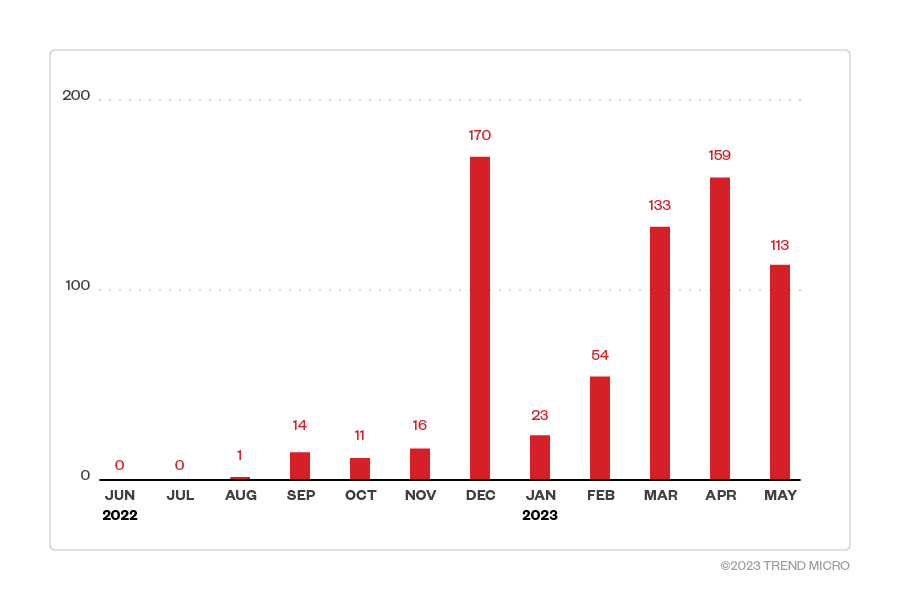
Since the group‘s inception in 2022, PLAY has performed as many as 170 cyber attacks in a single month.
Let‘s see how PLAY ransomware is exploiting vulnerabilities to perform attacks and how organizations can take action.
What is PLAY ransomware?
Starting in June 2022, PLAY, also known as Playcrypt ransomware, has performed ransomware attacks on a wide variety of businesses and critical infrastructure in North America, South America, and Europe.
The naming of the threat group comes from the encryption extension .play added after the malware takes effect.
PLAY threat actors focus on multi-extortion tactics, such as double extortion, which involves exfiltrating an organization’s data before encrypting it.
Who does PLAY ransomware target?
PLAY threat actors don‘t discriminate when it comes to planning their cyber attacks. Large enterprises with plenty of financial resources are the preferred victims for PLAY.
Additionally, the PLAY cybercriminals spread attacks worldwide, from the US, the UK, Europe, to Australia. One notable observation is that post-Soviet countries don‘t appear on PLAY‘s victim list; however, there‘s no direct evidence to suggest this is intentional.
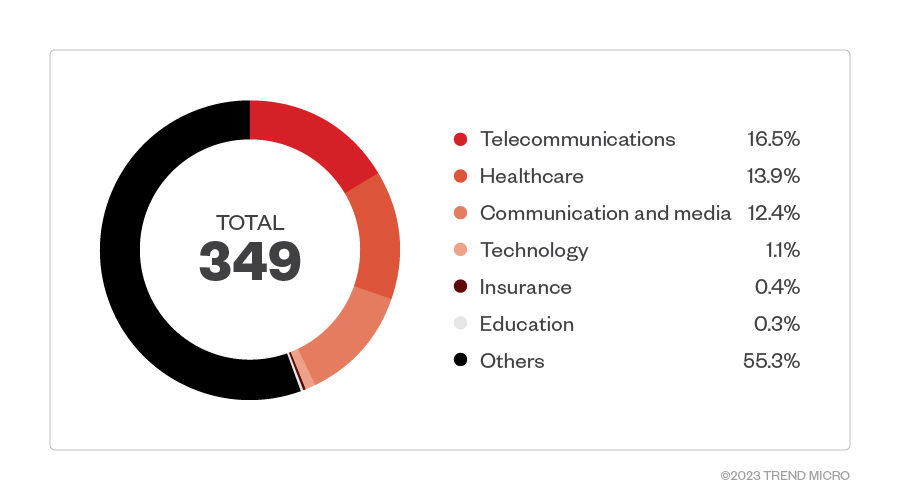
Telecommunications and healthcare are among the top sectors targeted by PLAY ransomware threat actors. High-value, high-pressure environments are often targets for ransomware due to gaps in cybersecurity. Additionally, companies with large data sets are targets because of the value on the dark web.
How does a PLAY ransomware work?
PLAY ransomware attacks are sophisticated and ever-evolving, making the group difficult to crack down on.
As of May 2025, the FBI was aware of 900 affected victims and growing within the US. In their investigation, the FBI and CISA found that PLAY operated as a closed ransomware group, rather than employing affiliates, to “guarantee the secrecy of deals,” according to the group‘s data leak site.
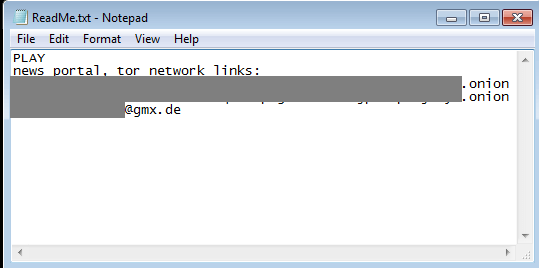
The threat actors deploy a ransom note that doesn‘t state a ransom demand or payment instructions, but instead, victims are instructed to contact the hackers via email to regain the encrypted files.
Let‘s dive into the different stages of the attack to discover how PLAY is exploiting high-payload organizations.
Stages of a PLAY ransomware attack
PLAY ransomware uses a variety of tactics and techniques to compromise a target. To perform their reconnaissance, the group uses Grixba, a custom-built reconnaissance tool, to scan the victim‘s network using WMI or WinRM and identify other tools that could be compromised and used for lateral movement. AdFind, a legitimate tool found in the Microsoft Active Directory, is used alongside Grixba to retrieve information on a target.
Once the ransomware gang has enough information, they move to gaining initial access. In observed cases, PLAY threat actors gain control of a victim‘s IT networks through the exploitation of vulnerabilities. Servers that are rented out or exposed unintentionally become prime targets. PLAY has also been observed to target specific vulnerabilities within Fortinet FortiOS, such as CVE-2022-42475, CVE-2023-27997, and CVE-2024-21762.
Specifically within Microsoft systems, PLAY has used vulnerabilities within the Microsoft Exchange Server to allow authenticated remote code execution (RCE), also called ProxyNotShell exploits. PLAY threat actors can then take control of an Exchange server remotely without an employee knowing.
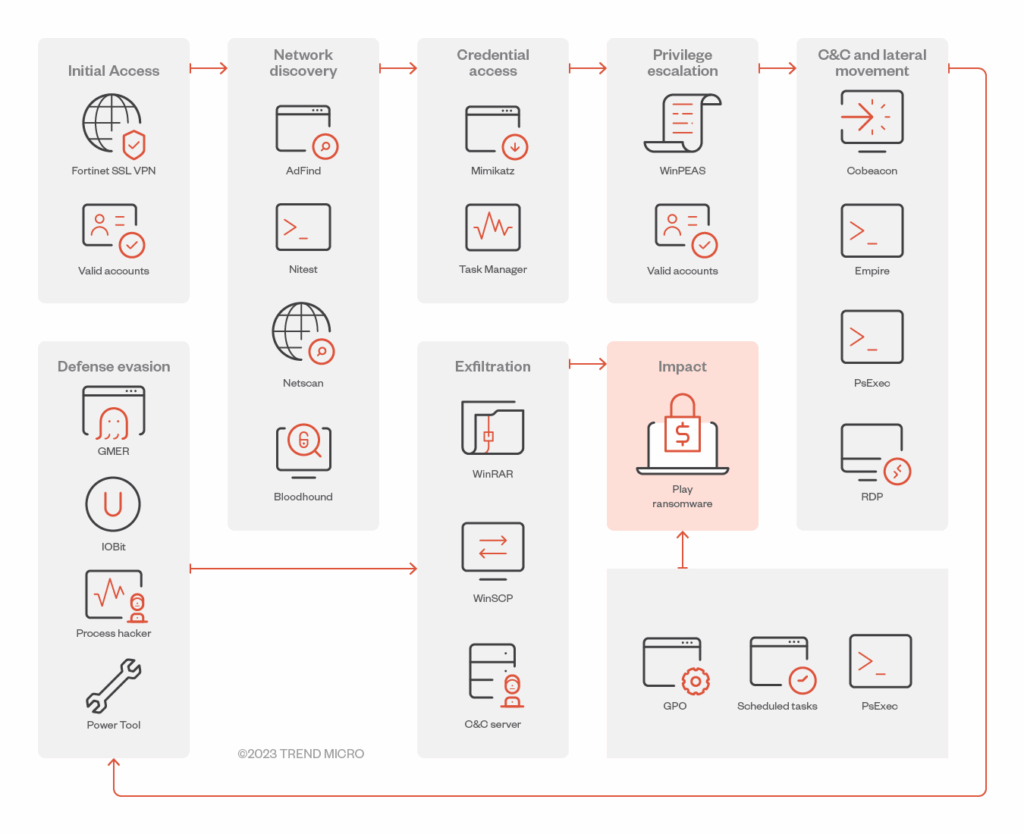
Once inside the system, PLAY hackers mask their activities using LOLBins and tools such as AnyDesk, NetScan, and Advanced IP Scanner. Other tools PLAY often use include Cobalt Strike, System BC, Empire, and Mimikatz for lateral movement while remaining undetected. Usually, the payloads are spread throughout the Active Directory environments to reduce risk.
To encrypt and exfiltrate files, PLAY utilizes intermittent encryption, where data is partially encrypted within files to evade legacy malware detection systems.
The PLAY ransomware group uses a double extortion model, encrypting systems after exfiltrating sensitive data. The ransom note appears as a readme.txt file, directing victims to contact PLAY ransomware with an email address ending in @gmx.de or @web.de . To pressure victims into paying the ransom demand, the ransomware group threatens to publish the exfiltrated data on their own Tor leak site.
PLAY ransomware has a variety of TTPs that are used to gain access to unauthorized systems. Below is a table of the tactics and techniques used in a typical PLAY ransomware attack.
PLAY ransomware TTPs


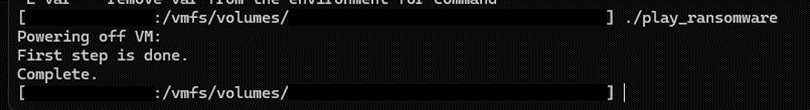
ESXi Linux variant
In 2024, cybersecurity researchers discovered a new Linux variant of PLAY ransomware. The ESXi variant invokes shell commands specific to the ESXi environment to conduct tasks such as powering off all running Virtual Machines (VMs), listing machine names, and setting the welcome message of the ESXi interface to the campaign-specific ransom note.
Common PLAY ransomware Indicators of Compromise (IoCs)
There are warning signs of a PLAY ransomware attack, even if attackers aim to be as stealthy as possible.
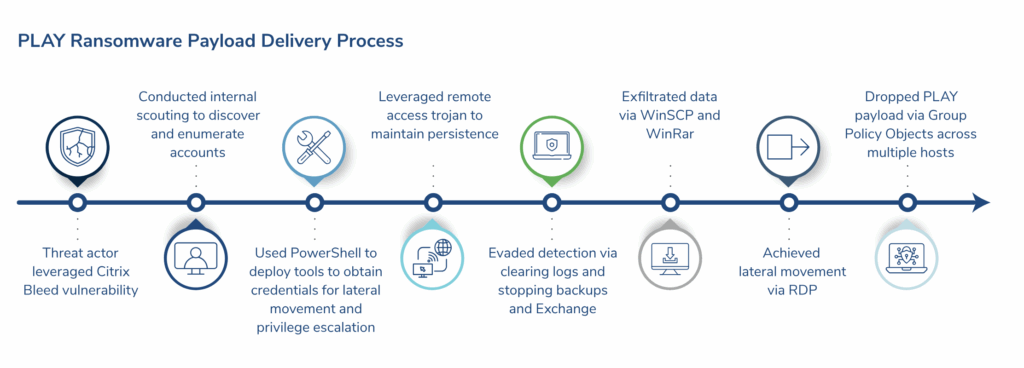
Here are some observed PLAY ransomware IoCs:
- Custom reconnaissance tools: PLAY uses a custom tool to gather intelligence before an attack called
Gt_net.exeor Grixba. It‘s designed to gather intelligence such as active hosts and IP ranges, network routes, remote access tools, and browser history before storing the collected data in a password-protected ZIP file. - Gain backdoor access: To perform attacks without employees noticing, PLAY uses a malicious backdoor access
SVCHost.dllis designed to mimic a legitimate Windows componentsvchost.exe. - Move laterally through systems: To move through networks without attracting attention, PLAY uses
PSexesvc.exea customized version of a legitimate tool, PsExec, to perform Remote Desktop Protocol (RDP). This allows the attacker to run commands or deploy payloads on other machines without physical access. - Bypass endpoint security defenses: To disable endpoint protection, PLAY ransomware uses
HRsword.exe. The riskware modifies system settings to prevent the security software from restarting and even shuts down other security tools. - Ransomware payload: In the final stage of a PLAY attack, hackers run
Hi.exeto execute the ransomware payload. Files are encrypted using AES-RSA hybrid encryption to speed up the process, before the ransom note is sent.Hi.exealso ensures that the ransomware doesn‘t affect the operating system, so victims can still pay. - Encryption tag: Encrypted files affected by PLAY ransomware contain the tag
.PLAY. - Ransom note: In a PLAY cyberattack, a ransom note with
PLAY_README.txtorReadMe.txtis placed in multiple directories to incentivise victims to make the ransom payments.
Defend against PLAY ransomware
PLAY ransomware uses known vulnerabilities and co-opt legitimate tools to infiltrate an unauthorized network. To limit potential adversarial use of networks, follow the advice from the CISA that aligns with cross-sector cybersecurity goals.
Follow these PLAY ransomware mitigation tips to protect your IT ecosystem:
- Implement a recovery plan Follow the NIST guidelines to appropriately identify cyber threats and safeguard company property.
- Require difficult passwords and change them often PLAY threat actors use harvested credentials to access unauthorized systems. Changing passwords often and requiring longer passwords mitigates the threat of co-opted credentials.
- Enable Multi-Factor Authentication (MFA) The CISA stresses the importance of enabling multi-factor authentication for webmail, VPN, and accounts that access critical systems. Otherwise, attackers can take control of valid accounts and grant themselves access.
- Update offline backups Regularly updating offline backups keeps sensitive data secure in case of a ransomware attack. Offline backups are disconnected from the network, taking the power away from the hacker.
- Monitor network traffic Use a monitoring tool to look for indicators of compromise, such as unusual network traffic patterns or communication with known command-and-control servers. Identifying threats early lowers the risk of a crippling attack.
- Beware of VPNS Play ransomware uses VPNs as a stealthy entry point into target networks, often in combination with stolen credentials or misconfigured systems. Protect VPNs from abuse by restricting VPN access to authorized IP ranges, and use geo-fencing to stop attackers from remotely accessing systems.
- Tighten access controls To further enumerate vulnerabilities, PLAY ransomware actors use Windows Privilege Escalation Awesome Scripts (WinPEAS) to search for additional privilege escalation paths. Be sure to only provide necessary access and remove users when access is no longer needed.
FAQs
- Will an antivirus program protect my network from PLAY ransomware? Unfortunately, PLAY ransomware operators have tools designed to disable antivirus programs. The CISA has advised that PLAY actors use GMER, PowerTool, and IOBit to disable antivirus software.
- Does PLAY ransomware use phishing in the initial stage of an attack? Although phishing isn‘t commonly used by PLAY to gain initial access, in some cases, phishing emails have been observed to harvest credentials to escalate an attack. Some victims receive threatening phone calls after an attack to pressure them into paying the ransom.
- How does PLAY ransomware use PowerShell? PowerShell is a built-in Windows automation and scripting tool that PLAY ransomware hackers use to move stealthily through an IT system. PowerShell scripts are used to disable Microsoft Defender to turn off or bypass Microsoft Defender protections. PowerShell can also give other threat actors higher permissions to help the group perform a cyber attack.
- What is a PLAY ransomware binary? In order to execute an attack while flying under the radar, PLAY threat actors use a custom PLAY ransomware binary to carry out encryption. PLAY recompiles its ransomware binary for each attack, with each binary having a unique hash. This is how PLAY hackers get around antivirus protective measures.
- Will stolen data end up on the dark web? The PLAY group uses a double extortion ransomware model, meaning that if victims don‘t comply with the ransom demands, their data will be leaked onto the dark web. In 2023, a Swiss IT company and service provider for government agencies, Xplain, was hit by PLAY ransomware. Originally, the hacker group sent portions of the data over to their leak site, however, after denying the attack and refusing to pay the ransom, the 65,000 government documents were leaked to the dark web.
Wrapping up
Protecting against high-threat ransomware actors can be daunting to face when companies are not properly protected with appropriate cybersecurity architecture.
Detecting threats such as PLAY ransomware early ensures that threats don‘t escalate, protecting daily operations and ensuring customer data safety.
To stay ahead of evolving ransomware tactics, try CybelAngel to protect employee credentials from falling into the wrong hands and prevent data breaches from causing reputational and financial damage.
