The Supply Chain Blind Spot: How FTP Servers Expose Financial Data

Table of contents
FTP might feel like a relic of the early internet. But for many vendors in the financial sector, it’s still in active use, and still exposing sensitive data. From plain text credentials to unaudited open directories, legacy FTP servers remain a weak link in modern supply chains.
And the problem isn’t always inside your perimeter. According to Verizon, 30% of breaches now involve third-party vendors, nearly double last year’s share. With attackers exploiting misconfigured file transfer protocols like FTP and SFTP, that’s a risk no financial organization can afford to ignore.
What is FTP/ SFTP?
FTP (File Transfer Protocol) and SFTP (SSH File Transfer Protocol) are used to upload files, automate data transfer, and exchange documents between systems.
While SFTP adds encryption via SSH, both rely on open ports, known IP addresses, and often outdated server software. This makes them attractive targets.
Here’s a mini glossary to keep in mind:
- FTP (File Transfer Protocol): A legacy method for transferring files between servers and clients. Transmits data and credentials in plain text unless extra layers are added.
- SFTP (SSH File Transfer Protocol): A secure alternative that uses SSH to encrypt both commands and data.
- SSH (Secure Shell): A cryptographic protocol that allows secure remote login and file transfers.
- TLS (Transport Layer Security): An encryption protocol used to secure data in transit.
- SSL (Secure Sockets Layer): A cryptographic protocol used to encrypt data in transit. Now considered outdated and replaced by TLS, but still referenced in terms like “FTP over SSL” (FTPS).
Why FTP still lives, and why that’s a problem
FTP should be obsolete.
But in financial services, it isn’t.
Many vendors (and even internal teams) still rely on standard FTP or SFTP to move large files, transfer bank statements, or handle batch reporting. It’s simple, well-supported, and embedded in legacy systems.
That convenience, however, comes with risk.
Legacy file transfer protocols like FTP and SFTP lack basic security features by default. Plain text authentication, weak access control, and poor visibility make them easy targets. They also allow anonymous access, making it easier for data leaks to happen.
Attackers know this. For example, Security Brief has reported that FTP port 21 is routinely scanned by bots looking for open services, exposed user accounts, or misconfigured permissions.
Unless TLS, SSH, or two-factor authentication is enforced, it’s just a matter of time before someone gets in. And exploiting these vulnerabilities is a rising trend, according to Verizon’s DBIR report.
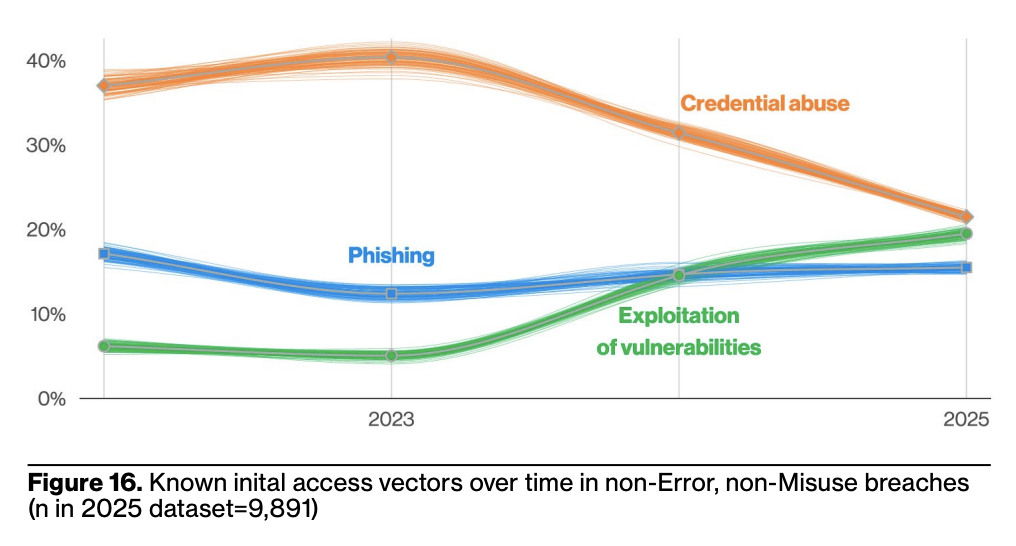
The third-party risk
It’s not just your infrastructure you need to worry about. Many supply chain providers still run their own FTP servers, and often without even basic security measures. That’s a problem for any financial organization trusting vendors with sensitive data.
These systems are often outside your direct control. Vendors ranging from document processors to payment platforms may still use legacy file transfer protocols to exchange large volumes of data. Too often, those servers are misconfigured, outdated, or forgotten entirely.
Here’s what poor vendor security typically looks like:
- Open directories exposed to the internet, no authentication required.
- User accounts protected by default or weak passwords.
- Login credentials transmitted in plain text over FTP.
- Unpatched server software with known vulnerabilities.
- No enforcement of TLS, SSH, or access monitoring.
These soft targets attract attention. According to the Verizon DBIR, 30% of breaches now involve third-party vendors, up from just 15% last year. Much of this is driven by vulnerability exploitation and business interruptions linked to insecure or legacy systems.

What attackers look for, and how they find it
Attackers use automated tools to probe for exposed FTP ports, weak SFTP servers, and unprotected IP addresses that hint at an unmonitored entry point.
They’re after open access and sensitive data. A misconfigured FTP server can reveal customer PII, financial reports, scanned documents, or authentication logs. And often without needing to bypass a firewall.
Here’s what makes a file server attractive to an attacker.
- Open FTP directories with no password protection.
- Known or reused default login credentials.
- Lack of TLS or SSH, enabling plain text interception.
- Server banners revealing outdated or unpatched server software.
- Weak password policies vulnerable to brute-force or dictionary attacks.
According to Verizon’s DBIR, 89% of breaches are financially motivated, and the finance sector continues to rank among the top targets.
Attackers are looking for structured, monetizable data. And unsecured file transfer protocol endpoints offer exactly that.
With brute-force attacks on FTP port 21 still common, scanning for vulnerable setups remains a low-cost, high-reward tactic for threat actors.

An FTP service case study
FTP port 21 remains a frequent target for brute-force attacks. In 2025, security researchers’ analysis, based on honeypot data, showed that attackers routinely scan for outdated or default configurations, and then attempt logins using massive lists of known breached credentials.
Many FTP services, especially in third-party environments, are still using basic authentication with no encryption, transmitting usernames and passwords in plain text.

In 2017, the FBI issued a warning about hackers who targeted FTP servers anonymously to access health data and blackmail business owners.

These aren’t rare edge cases. They’re a reflection of persistent hygiene gaps in how vendors manage file transfer protocols. And they’re precisely the kinds of exposures that sophisticated attackers look for first.
Why financial services are especially vulnerable
Financial institutions operate with some of the most complex vendor ecosystems, and some of the most attractive data for attackers. From core banking software to payment processors, legal vendors, HR platforms, and document services, data is constantly flowing in and out through third-party connections.
Legacy protocols like FTP and SFTP are often buried deep in these relationships. While they may handle simple file transfers or batch uploads, they also create unmanaged risk, especially when FTP server security is left to the vendor’s discretion.
Financial data is structured, predictable, and monetizable, which is exactly what attackers want.
A single exposed directory can reveal:
- PII exposure from loan applications or account onboarding
- SWIFT confirmation leaks or internal financial documents
- Login credentials for shared environments
- Data leaks that trigger regulatory scrutiny or compliance issues
The attack surface is only growing. With more vendors and more automation solutions stitched into daily operations, the potential for unauthorized access increases.
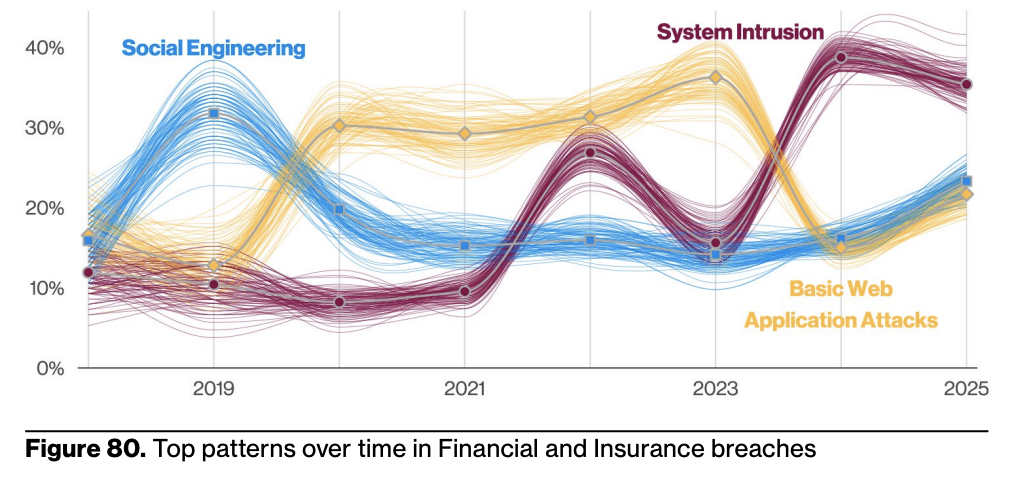
Here’s a breakdown of some of the attack mediums used by cybercriminals against the finance sector. Note that both system intrusion and basic web application attacks are major vectors.
What good FTP security (and vendor monitoring) looks like
Securing file transfer infrastructure (especially when it sits outside your organization) starts with visibility. You can’t secure what you don’t know is running.
For your internal teams, the fix starts with hardening your FTP or SFTP environments using the following best practices:
- Disable anonymous access and enforce strong, unique credentials.
- Use secure alternatives like SFTP or FTPS, never plain FTP.
- Require TLS or SSH encryption to protect credentials and data in transit.
- Audit file permissions regularly and limit access to only what’s needed.
- Apply patches and updates to server software as part of routine maintenance.
- Enforce two-factor authentication wherever possible.
But internal security is only half the picture.
Many exposures begin with vendors, file sharing platforms, hosted FTP services, or departments using third-party FTP clients with minimal oversight.
This is where continuous third-party risk management comes in.
You’ll want to:
- Discover and map all third-party file transfer assets, even ones not disclosed in contracts.
- Monitor for new or unexpected FTP servers appearing in your vendor environment.
- Identify unencrypted traffic, outdated protocol use, and SFTP vulnerabilities before attackers do.
- Integrate alerts and notifications into your existing security workflows for fast triage.
Tools like managed file transfer (MFT) platforms may offer stronger controls, but only if vendors configure them properly. For everything else, proactive monitoring solutions like external threat intelligence are your best bet.
Bonus checklist: What to ask your providers
When reviewing third-party file transfer practices, don’t assume “we use SFTP” means secure. Use these specific questions to cut through vague answers and surface real risk.
Technical configuration
- What protocols do you currently use for file transfer (FTP, SFTP, FTPS, MFT)?
- Is TLS or SSH encryption enforced for all file transfers?
- Which ports are open for file transfers, and are they restricted by IP allowlists or firewalls?
- Are login credentials encrypted in transit and at rest?
- How are user accounts created, managed, and deprovisioned?
Access control & permissions
- Do you allow anonymous access to any file transfer services?
- How is access to file directories and files controlled and logged?
- Do you enforce multi-factor authentication for all users with file upload or download access?
Monitoring & patching
- How often do you apply security patches to your FTP/SFTP servers?
- Do you actively monitor for brute-force attempts or unauthorized access?
- Are file transfer logs regularly reviewed for anomalies or abuse?
Exposure management
- How do you ensure that FTP/SFTP services aren’t exposed to the public internet unnecessarily?
- Do you conduct regular internal or third-party audits of your file transfer setup?
- Do you use any attack surface management tools?
- Can you provide a recent assessment or penetration test that covers your file transfer systems?
These questions help uncover not just technical gaps, but operational ones. And they create a baseline for evaluating who is exposing your supply chain security to unnecessary risk.
FAQs
Is FTP over SSL secure enough for sensitive data?
Not always. FTP over SSL (FTPS) can encrypt file transfers, but it depends on proper configuration. Weak ciphers, poor certificate handling, or open ports can still undermine data security.
What’s the difference between FTPS and SFTP?
FTPS uses SSL/TLS for encryption and runs over FTP, while SFTP uses SSH. SFTP is generally easier to secure through firewalls and has stronger default functionality.
Can FTP servers run securely on Linux?
Yes, many Linux servers support hardened configurations, but you’ll need to disable plain text auth, enforce strong permissions, and monitor logs carefully.
Are there secure file transfer tools for iOS?
Yes. Several secure file transfer apps support iOS, including SFTP and MFT clients. Just make sure they use end-to-end encryption and integrate with corporate access controls.
Final thoughts
Legacy FTP servers still risk financial data exposure, especially through vendors. Don’t let outdated protocols go unchecked. Having a secure file transfer protocol will reduce security risks and keep you one step ahead of cybercriminals.
CybelAngel can help you map legacy protocol risk and secure third-party asset exposures.

