Identify and Prevent a Ransomware Attack: REvil Soddinokibi Use Case

Table of contents
Identifying a ransomware attack
Ransomware made its appearance in 1989 with the malware PC Cyborg Trojan that encrypted user data and forced the victim to pay $189 to unlock their files. These malware attacks are accomplished by encrypting all or part of a computer or system. Attacks often cause irreparable data loss, even if the owner pays the ransom. Cybersecurity professionals continuously struggle to stay ahead of ransomware attacks. In this article, we will explain briefly the technical details of the malware and show you how to detect an attack and prevent it.
How ransomware enters a network? REvil/Sodinokibi use case
Phishing attacks are the most common vector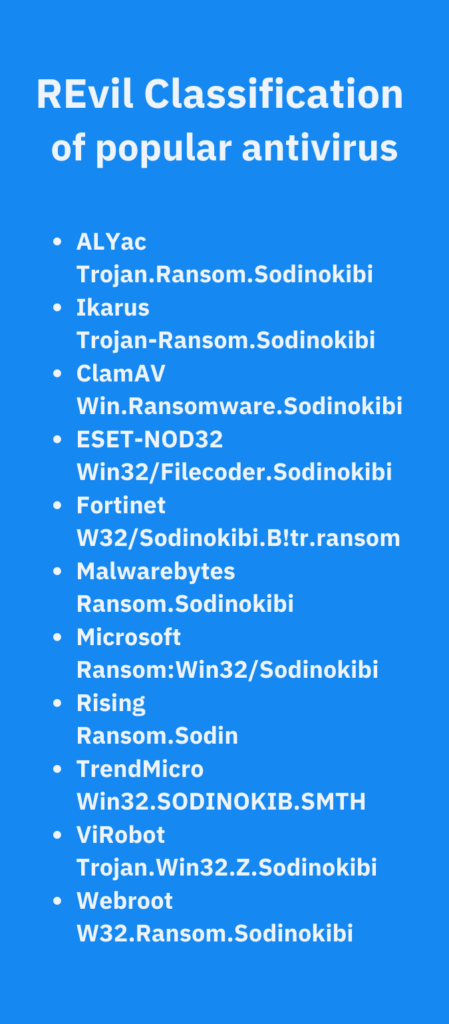 used to infiltrate a company’s perimeter. In this scenario, an email is sent with a link to download either executable or archive malware that encrypts your data — rendering it inaccessible — or enables the theft of your data. (See Figure 1 of common malware used to penetrate networks.)
used to infiltrate a company’s perimeter. In this scenario, an email is sent with a link to download either executable or archive malware that encrypts your data — rendering it inaccessible — or enables the theft of your data. (See Figure 1 of common malware used to penetrate networks.)
Some key aspects of a REvil/Sodinokibi attack include:
- The malware exploits vulnerabilities to escalate its privileges to the SYSTEM.
- Some extensions files and folders are on whitelists from the encryption process.
- The ransomware encrypts files locally and on network storage.
- It can also exfiltrate data on distant controllers.
Detecting a possible attack:
- A registry key SOFTWAREGitForWindows
- A .txt file containing a ransom note
- Encrypted files with a randomly generated extension
Preventing an attack
Some of the most common and effective practices for preventing a ransomware attack include:
- Regularly patch your computers and particularly the Bluekeep vulnerability link to RDP attacks : CVE-2017-0708 and CVE-2018-8453.
- If possible, deactivate RDPs or force extremely complex passwords, as malicious RDP bruteforce services are available on the Dark Web.
- Filter all email for executable files. Consider blocking emails with executable files.
- Always have a tested backup of your most critical data.
- Deactivate macros in Microsoft Office, particularly for external access.
- Activate Windows access control to prevent users from launching executables from local user folders (e.g: Local App Data; Temp, ProgramData).
- Consider isolating critical servers.
While all of the above are integral to a strong cybersecurity program, these miss the origination of many ransomware attacks. Most attacks start with vulnerabilities in your infrastructure, it seems that preventing being a ransomware victim should be as simple as securing your vulnerabilities. Unfortunately today’s CISOs and their staff are dealing with an ever-expanding attack surface that includes third-party cloud applications, connected storage devices, open databases, and perhaps worst of all are the shadow assets. According the Everest Group, 50% of all enterprise technology budgets are spent outside of IT’s purview. You cannot address vulnerabilities if you are blind to their presence. CybelAngel’s Asset Discovery and Monitoring, helps our customers to prevent attacks against vulnerable assets by:
- Shrinking digital footprint to impede reconnaissance of your IT ecosystem
- Preventing malware attacks against unpatched, internet-facing shadow assets
- Secured legacy infrastructure, especially as cyberattack surfaces expand with new OT and IoT technology
Our solution empowers enterprises to take back control of their critical assets by detecting and securing unsanctioned assets, decommissioned services and products — theirs or their partners’, cloud storage, or productivity applications. Giving organizations:
- Visibility of your external-facing shadow environment
- Prioritization, which allows security team to resolve high priority incidents without losing time dealing with false positives
- Actionable alerts give teams clear attribution of an incident — employee, third party, or partner
- Easy, hassle-free coverage that can be set up in a couple of hours. No additional FTE required, as a CybelAngel analyst leads the investigation.
Lessen your company’s odds of becoming a ransomware victim. Start your free Asset Discovery and Monitoring trial now. Our team is ready to help you protect ALL of your infrastructure, including your shadow assets. Start your trial now.