The Ultimate Cybersecurity Posture Checklist [25+ Tips]

Table of contents
Cybercrime is a costly and growing issue for governments and businesses worldwide, which is why countries like the US and the UK invest in cybersecurity like never before. The US will spend $13 billion in 2025, and the UK has set aside £25 million to help allies battle cybercrime.
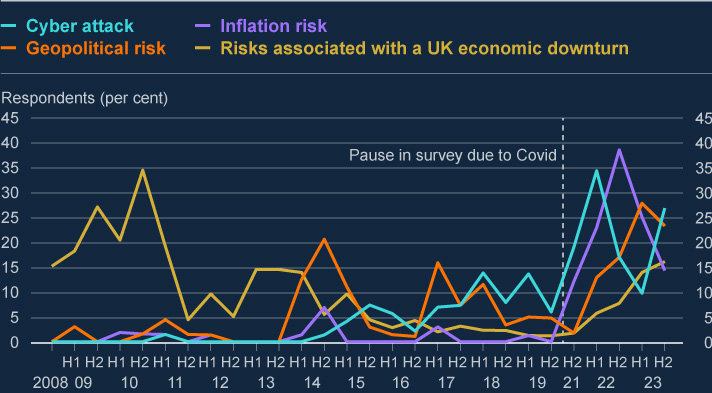
A 2023 survey by the Bank of England shows that many businesses perceive cyber attacks as a major risk as well, with 70% of respondents citing that a “Cyber attack” was their number one concern.
Unfortunately, most of them have already faced serious attacks, showing the need for a strong cybersecurity posture. This means using the right tools and ensuring all employees know and follow security best practices.
All in all, the future of cybercrime is bright, with expected losses of $9.5 trillion in 2024, but the same can be said about cybersecurity, as governments and businesses keep showing interest in improving their cybersecurity posture and cyber risk mitigation.
Today, we’ll explain why cybersecurity posture matters and share our cybersecurity posture checklist for businesses interested in protecting their data and minimizing damage from potential attacks, so let’s dive right in!
What is risk posture and why it matters?
When someone mentions posture, you instantly think of keeping your body in the right position so that you don’t face aches and pains later in life. Cybersecurity posture is the digital equivalent: it’s about having the right security measures in place so that you don’t have to deal with cyber threats, like malware and ransomware, among many others from the threat landscape.
A strong cybersecurity posture stops data breaches and hacks through a combination of internal policies, external standards, and technology: data encryption, authentication, access control, vulnerability management, and automated threat detection.
Additionally, companies can improve their security posture by staying up-to-date with regulatory compliance laws as well as following best practices to reduce security risks.
However, you can’t just set it and forget it in the cybersecurity world. Your organization should evaluate your security status constantly and create a well-defined security program that meets the requirements of the organization and all users.
In summary, companies can’t ignore the importance of cybersecurity any longer unless they want to lose money, face legal problems, and damage their own reputation.
Keen to improve your security posture? Keep reading to find out!
Our cybersecurity posture checklist
Now that you understand why cybersecurity posture matters, you should conduct a cybersecurity risk assessment. Our cybersecurity posture checklist can help your company identify potential risks associated with your company’s digital infrastructure and develop strategies for mitigating security threats. Is it time for a preemptive security posture?
A friendly reminder: If you’re feeling overwhelmed by the whole process or have more important things to handle, don’t worry. Contact CybelAngel for a free demo and let us do the heavy lifting.
1. Update software regularly
Many organizations underestimate the power of software updates, but they’re one of the easiest ways to boost your cybersecurity. They can fix security holes and bugs, hence keeping your systems safe. We suggest enabling automatic updates on all devices. With the automation of updates, you won’t miss any important patches.
2. Use strong passwords
It goes without saying that your passwords should be somewhat complex and hard to guess (a mix of letters, numbers, and symbols). That way cybercriminals will have to work overtime to hack your systems. A password manager can help you create and store your passwords securely and enhance data protection.
3. Enable two-factor authentication (2FA)
Two-factor authentication (2FA) is a second form of verification that will make it harder for cybercriminals to access your accounts. We suggest using a trusted authentication app for better security than SMS-based 2FA.
4. Backup data regularly
Regular data backups protect against data loss, so schedule backups somewhere secure like a cloud service or offsite storage. This ensures you can recover your data if something goes wrong.
5. Use antivirus software
One of the easiest ways to keep hackers at bay and ensure data security is to install good antivirus software on all your IT assets. Remember to keep it updated so it guards against the newest cyber threats.
6. Install a firewall
Firewalls block unauthorized access to your network. We suggest using both hardware and software firewalls for the best protection and network security.
7. Secure your Wi-Fi network
Aside from installing firewalls, you should also ensure your Wi-Fi network is secure so that no one without access can use it. You can do this by changing the default router password and using WPA3 encryption.
Pro tip: Rename your network to something unique to avoid revealing the router brand and improve information security.
8. Role-based access control and zero-trust security
Controlling who can access sensitive information reduces the risk of data leaks, so we suggest using a role-based access control. That way, only those who need access will have it.
Experts even suggest deploying zero-trust systems that will verify and validate everyone without exceptions. This is important because more people work in hybrid environments, which makes it harder to manage access control.
9. Get your employees on board and spread security awareness
A study by Elevate Security found that 8% of people caused 80% of security-threatening errors, which is why you must teach all your employees to recognize phishing and other common security attacks. For instance, you can simulate cyberattacks to test their readiness and reinforce training.
Additionally, the 2023 US Treasury report suggests that better teamwork among victims can help battle cybercrime. It encourages sharing information about cyber threats, especially AI-related ones and recommends joining ISACs (Information Sharing Analysis Centres) and NIST (National Institute of Standards and Technologies) for best practices.
10. Use encrypted information
To keep your data safe during transmission, use encrypted email and messaging services. That way, your communications will remain private and secure. We also suggest using full-disk encryption on all devices that store sensitive data. Encrypting critical information protects it from prying eyes.
11. Monitor network activity and user behavior
Observing network activity can help you catch unusual behavior early and improve the organization’s security posture. You can do this with network monitoring tools and intrusion detection systems.
The same goes for user behavior. Excellent behavior analytics tools and alerts for abnormal activities can help you detect unusual actions that may indicate threats.
Companies that found their own breaches, rather than being told by others, saved about $1 million on average. Involving the police or another security agency also helped cut costs.
12. Implement physical security measures
Keeping a close eye on your network sometimes isn’t enough. That’s where physical security controls and measures come into play. Remember that physical security is just as important as endpoint security, so make sure you secure server rooms with locks, keycards, and surveillance cameras. This way, only authorized people will have access to your data.
13. Regularly review security policies
Having security policies is a great security measure but you must review them regularly to keep them up-to-date and effective. Schedule these reviews at least once a year. Or after significant changes to your systems.
14. Conduct security audits
The best security measure is prevention. That being said, regular security audits should become a part of your security strategy. Unfortunately, you can’t conduct these tests alone.
You should hire a reputable external surface management company like CybelAngel to audit your systems and detect weaknesses and misconfigurations in your defenses.
Third-party auditors provide a real review of the situation and can offer valuable insights and security tips, so don’t think twice about hiring a cybersecurity company for this task. Just make sure it’s a reputable one with a proven record.
15. Patch management
Managing patches keeps your software unpenetrable and up-to-date. Automated tools can help streamline the whole process and schedule regular patching sessions.
16. Secure mobile devices
The past few years have taught us that we can work from home and even on the go using our phones. If your employees keep valuable data regarding your business on mobile devices, we suggest using mobile device management (MDM) solutions to enforce security policies on all devices.
Pro tip: You can prevent unauthorized use and theft by limiting physical access to devices, such as laptops and other portable devices. We suggest locking them up when not in use.
17. Implement data loss prevention (DLP)
Data prevention loss (DLP) tools can help your security managers monitor and control data transfers, hence preventing data leaks. We also suggest setting rules to control how sensitive data is shared and moved.
18. Use multi-factor authentication (MFA) and hardware keys
Changing passwords too often can make people create easy-to-guess passwords. To stay safer and increase security posture levels, use multi-factor authentication and hardware keys.
19. Disable unused services and ports
Hackers see unused services and ports as entry points for attacks. Luckily, you can prevent potential attack surfaces by regularly reviewing and disabling those you no longer need.
20. Continuous monitoring of third-party vendors
Aside from employees, you should also make sure service providers and third parties follow your security standards. You can achieve this by setting access rules and conducting regular audits.
21. Create a step-by-step incident response plan
The security measures we’ve mentioned should keep your business cyberattack-proof, but you should still have a step-by-step incident response plan just in case. This way, you will be prepared for security breaches and improve the overall security of your organization.
Additionally, you should regularly test your plan and update it to ensure it’s effective against security incidents.
22. Secure remote access to strengthen security posture management
Remote access also needs limiting because cybercriminals keep getting better at hacking businesses remotely. You can easily prevent this by using VPNs and strong authentication methods.
23. Use application whitelisting
Apps make our lives and business operations easier, but they can also serve as entry points for hackers. That’s why you should use application whitelisting, which means only approved apps run on your systems.
Pro tip: Regularly update the whitelist with new, trusted applications and remove ones your organization no longer needs or trusts.
24. Implement network segmentation
If you separate critical systems from less secure ones with VLANs and firewalls, you will automatically limit the spread of future attacks. That being said, network segmentation is your friend when it comes to cybersecurity.
25. Don’t forget about cloud security
Verizon says many attacks on businesses start with hackers getting into their emails. With the help of AI, these emails get better in the sense that the content of the messages sounds more fluent in English.
The ploys also sound more believable, making employees give out their entry credentials to cloud services. That’s why you should also invest in cloud security and train employees to handle these cyber threats.
26. Follow cybersecurity news and updates
Trusted newsletters and alerts for the latest cybersecurity trends and developments can help you stay ahead of new cyber threats.
27. Have cybersecurity experts on speed dial
Security teams can find and fix weak vulnerabilities in your security and handle risk management, so don’t hesitate to contact a cybersecurity company for help. They will conduct both automated scans and manual penetration tests in real time using internal and external testers, while you sit back and relax.
How do you know if a company has a good security posture?
A company’s security posture shows how well it can defend against cyber threats. Some of the key signs of a good security posture include:
- Well-defined rules and procedures, updated regularly.
- Frequent assessments to find and fix vulnerabilities.
- Use of multi-factor authentication and strict access limits.
- Regular cybersecurity training for all staff.
- A clear plan for handling cyber incidents, with regular practice drills.
- Use of firewalls, antivirus, and regular software updates.
- Frequent security checks and compliance with regulations.
- Encryption of sensitive data and strong backup procedures.
- Sharing threat information with other organizations.
- Ongoing tracking of network and system activities.
- Ensuring partners and vendors meet security standards.
One company known for having a good security posture is Microsoft. They have robust security measures, regular risk assessments, and comprehensive employee training programs.
Start building a strong security posture today
In conclusion, security posture refers to security posture assessment, and while our cybersecurity posture checklist should cover all your bases, consider contacting us for a complete cybersecurity posture assessment.
We’ll find vulnerabilities within your systems and help you create a strong cybersecurity framework. So, don’t hesitate to request a demo today!


