
Three Ransomware Trends to Watch in 2021
2020 is the Year of Ransomware
2020 is unprecedented in many ways, including ransomware attacks literally booming. According to Gartner, twenty-seven percent of malware incidents reported in 2020 can be attributed to ransomware. This is particularly concerning given the average ransom payment in second quarter of 2020 was $178,254. 2020 may indeed be “The Year of Ransomware.” Ransomware gangs are all over the trade and business news. The announcement of Maze Team’s retirement in November is driving a lot of speculation. Some say their retirement report is a smoke screen, which will help Maze to rebrand in 2021 — evolve and retain their fame. While others believe members of the gang are planning to join other ransomware gangs and continue their career of ransomware attacks. 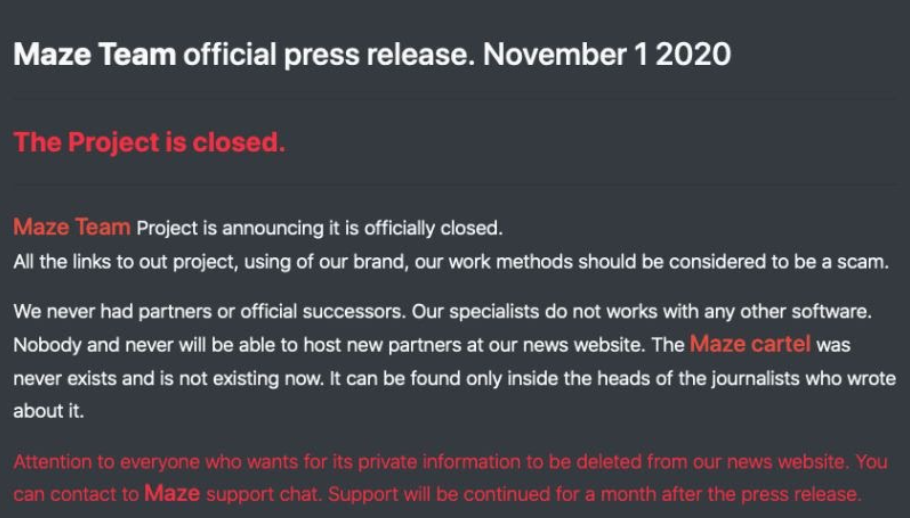 So, what should we expect in 2021? The following are 3 ransomware trends of ransomware to watch. Spoiler alert, all 3 trends will contribute to putting more and more pressure on victims and speed the move to a robust ransomware-as-a-service ecosystem.
So, what should we expect in 2021? The following are 3 ransomware trends of ransomware to watch. Spoiler alert, all 3 trends will contribute to putting more and more pressure on victims and speed the move to a robust ransomware-as-a-service ecosystem.
1 – Growing use of VIP dark web forums for data leak advertising
One of the latest trends observed is ransomware gangs advertising about data leaks and breaches. In this use case, advertising means ransomware gangs are talking more and more about their prey and their success on private VIP. These gangs often use secure messaging apps such as: Discord or Telegram, or private forums where membership is not easily given to new users. The new ransomware-as-a-service ecosystem is well organized. To sell their “product,” gangs advertise their latest malware or evolution to trusted members. Some forums are so selective that they do not hesitate to ban some users, if they don’t respect their skills, experience, longevity, or associations. During the 2020 summer, CybelAngel analysts investigated a Lockbit ransomware attack. We observed a user advertise about the breach on a highly select forum. The user was banned from the forum a couple of days after this error in judgement. Another example of this type of advertisement is the screenshot below. This post shows the DarkSide gang using the Russian-speaking XSS Forum to share news about stolen data management. This forum is very selective; accepting a new member is a long and difficult process. 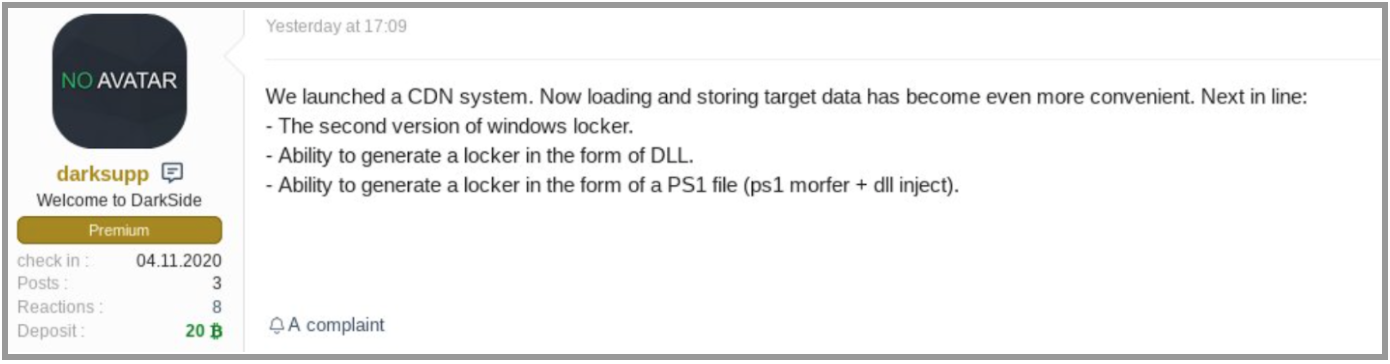 In this post, DarkSide states the gang has created a new generation of data storage in Iran to keep all the data stolen safe until the victim pays the ransom. This links to the next trend — data breach specific websites dedicated to stolen information dumping.
In this post, DarkSide states the gang has created a new generation of data storage in Iran to keep all the data stolen safe until the victim pays the ransom. This links to the next trend — data breach specific websites dedicated to stolen information dumping.
2 – Creation of dedicated websites for each leak
At CybelAngel, we help our customers when they are victims of a ransomware attack. We noticed that gangs have started to create specific homemade Tor websites to share the branched data of victims. After gangs steal data, some generate a vanity onion url address dedicated to the breach. These vanity onion urls are uniform in that most use of the name of the victim company in the url. The victim, and more widely the people who have access to the url, can find all the details of the breached data shared by the gang on such websites. This action puts more pressure on the victims, as a link can be shared very easily and can easily be accessed by journalists. Ransomware victims have to consider the attack as a data breach as some files are easily accessible on the network. The REvil is one of the ransomware gangs using this tactic — see the example below. 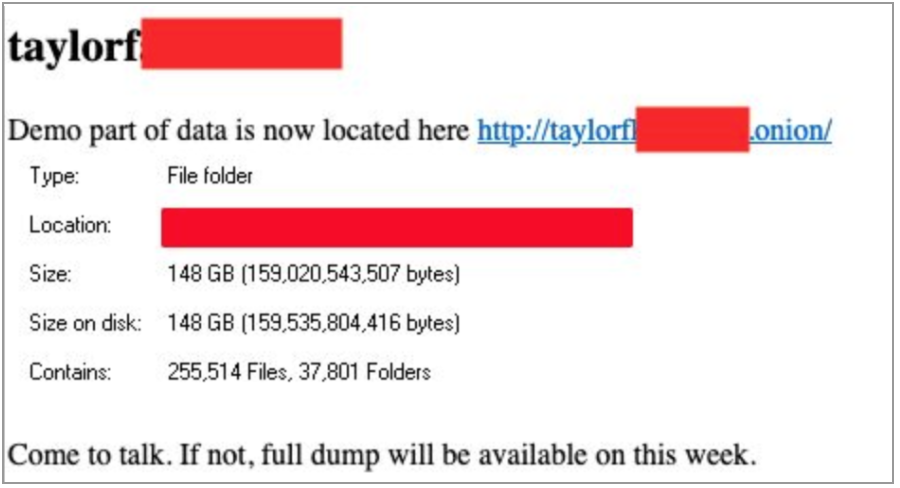 The Ragnar Locker gang has been seen threatening their victim by advertising the leak on a hacked Facebook account with a sponsored public run post. Both observed processes aim to increase pressure on victims by making public the attack they undergo and therefore their weaknesses.
The Ragnar Locker gang has been seen threatening their victim by advertising the leak on a hacked Facebook account with a sponsored public run post. Both observed processes aim to increase pressure on victims by making public the attack they undergo and therefore their weaknesses.
3 – The phone is the latest weapon
Speaking of pressure… There is nothing like receiving a call from the ransomware gang which holds the your company’s leaked data. ZDNet notes cold-calling is the latest tactic utilized when some companies try to recover from a ransomware attack on their network using backups without paying the ransom. Security researchers say ransomware gangs began using this technique in the late summer of 2020. Some of these gangs are even subcontracting the cold calls to an outsourced call center. As of today, only two ransomware gangs are using this technique: Conti and Ryuk. We are keeping a watchful eye on this new practice; it may increase and spread across the ransomware ecosystem. CybelAngel exhaustively scans the entirety of the internet, including the ransomware gangs landscape for any mention of our customers. If a customer is victimized, we minimize damage by identifying the leak source and locations where data is for sale. Gain a better understanding of your company’s digital risk, request a complimentary customized data exposure dashboard. You’ll be surprised what confidential data is leaking for your company. Data leaks are inevitable, but damage is optional.