US Telecom Giants Under Siege: ‘Salt Typhoon’ Cyber Assault Linked to China

Table of contents
Reports by cybersecurity researchers over the last months have exposed massive infiltration campaigns targeting the backbone of American internet access by chinese hackers.
But in a nutshell, what exactly do you need to know about the alleged Beijing backed Salt Typhoon hacking group?
In this blog we will review the cybercrime situation so far, the impact of state-sponsored botnet campaigns, and the takeaways you should be sharing with your SOC team.
Wiretapping reports: The story breakdown from the WSJ
On September 26th, 2024 the Wall Street Journal reported an advanced persistent threat actor, dubbed the “Salt Typhoon”, was targeting the US internet service providers.
On October 5th, the paper then reported that Verizon and AT&T, along with Lumen Technologies, juggernauts of the US internet service provider industry, were infiltrated by the Salt Typhoon group, sparking probes into the issue by US intelligence officials as well as private sector cyber security researchers.
The Wall Street Journal report clarified the panic over this outage in security, as it noted that “U.S. officials are racing to understand the full scope of a China-linked hack of major U.S. broadband providers, as concerns mount from members of Congress that the breach could amount to a devastating counterintelligence failure.”
The Chinese embassy did not respond to direct requests to comment on this attack, but tensions are evident as a spokesman for the Chinese Embassy in Washington, accused the U.S. of fabricating evidence about China’s involvement in these attacks.
Understanding the Salt Typhoon hacking group
The Salt Typhoon group, otherwise styled as GhostEmperor or FamousSparrow, is a malicious hacker group with a fitting name. The US government and Microsoft researchers have confirmed that this group is linked to the Chinese foreign intelligence service. FBI analysts have noted that Salt Typhoon’s activity may be linked to China’s Ministry of State Security. In particular, it has been linked to APT40 (also known as Gingham Typhoon), a group known for its expertise in intelligence collection.
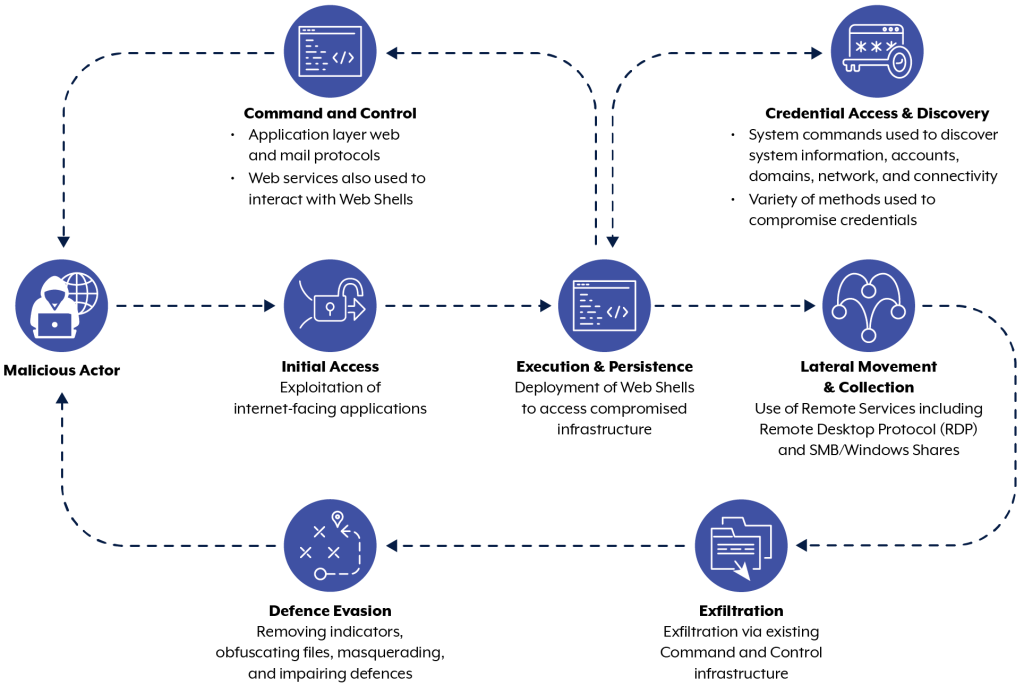
Believed to be in operation since since at least 2019, they primarily targeted entities and governments in North America and South East Asia.They are known for their ability to infiltrate complex network architectures by exploiting existing vulnerabilities, and specialising in espionage and data theft. Some researchers connect this group to the notorious exploitation of the ProxyLogon vulnerability. It targeted Microsoft Exchange servers around the world in 2021.
The name “Salt Typhoon” was given to the group through the Microsoft naming convention wherein “Typhoon” is associated with hacker groups with ties to China or the Chinese government.
What about the impact of breached national ISPs?
So far three US-based ISP companies seem to have been penetrated by the Salt Typhoon group: Verizon, AT&T and Lumen Technologies. None of these affected companies have commented publicly on this critical incident.
The investigations indicate that the hacker group was targeting the backdoors established by these companies to provide the US government with legitimate and judicially required surveillance and interception capabilities.This means, malicious actors not only were able to maintain access to critical infrastructure and information, they were gained surveillance over general internet traffic through the networks of AT&T and Verizon, together encompassing approximately 68%of American wireless traffic.
These network access obtained by the attackers could have been maintained for months or longer unnoticed. Internet Service Providers are companies that provide ways for people and companies to access the internet. They sell equipments like modems and routers, as well as email access, and network plans. These are all used widely by individuals, homes and companies for their day-to-day activities on the internet.
Broadband providers tend to be prime targets for APT groups, especially those backed by nation-states. They are targeted due to the sensitive nature of the data that they handle and the critical importance of the infrastructure involved. As ISPs tend to be one of the first and most important links in a supply chain network, compromise at this level can mean a range of risks.
These can look like:
- Intellectual property (IP) theft
- Sensitive data breach
- Malicious botnet campaigns
They target any critical industry that has devices connected to the internet or surveillance of a populations internet traffic. This in term causes a long term and deep impacts on a country’s economic and security capabilities.
Some notable patterns in recent Chinese cyberattacks
The Salt Typhoon attack is the latest in a series of attacks that have been tied to China-linked cyber threats.
Flax Typhoon
In September this year, the FBI identified and mitigated a massive botnet campaign by another group named “Flax Typhoon.” The FBI reported that this group, upon the direction of the Chinese government, had infected over 260,000 networking devices worldwide. 47.9% of these were found in the United States, followed by 8% in Vietnam and 7.2% in Germany. The campaign is believed to have started in May 2020 and has established a multi-tiered network with enterprise-grade control systems. These handled the large number of infected entities, over the next four years until it was discovered by 2024.
Volt Typhoon
Early this year, American law enforcement also disrupted another similar group dubbed “Volt Typhoon.” It primarily attempted to target the United States government and allies within the Five Eyes intelligence alliance. Volt Typhoon, also known as Vanguard Panda, Bronze Silhouette, among others, compromised thousands of devices around the world. It was publicly identified by Microsoft researchers in May 2023.
Volt Typhoon itself has been active since mid-2021. It uses malware that targets inter-connected systems with weak administrative passwords and outdated versions of systems. In 2023, the hacker group compromised the water supply system in Guam, a territory of the U.S. in the Pacific ocean. Though the systems remained intact and online until discovery of the malware, authorities were concerned about this threat. It was thought that it may have been to disrupt communications between USA and Asia in case of military escalation in the region. It was also reported as a move to deprive the American military station on the island from accessing the water supply.
Interested in reading more about phishing and ransomware threats targeting hospitals? Read our latest guide, Hospitals and Ransomware: An Invasive Sickness.
Wrapping up
Here is a speedy recap of the story so far:
- Salt Typhoon is the latest in a long list of cyber threat groups targeting critical American infrastructure. It has been attributed to the Chinese government’s foreign intelligence gathering and cyber espionage efforts.
- These attacks highlight the importance of cybersecurity when it comes to the future of geopolitical conflicts and national security concerns.
- Lawful interception systems and backdoors used by legitimate law enforcement authorities in critical communications infrastructures, seem to be the weak link. It was this link that that allowed malicious actors to gain access.
- Thorough and regular audit of access logs and unusual activity patterns for telecommunications companies and their customers are required.
- Debates on the lawful interception systems and backdoors incorporated into critical communication infrastructure have been renewed.
Interested in more great content? Check out our recent Microsoft SMB analysis blog. You can also follow our socials; LinkedIn, Twitter/X, and Facebook, to enjoy fresh content and analysis weekly.
