Discover
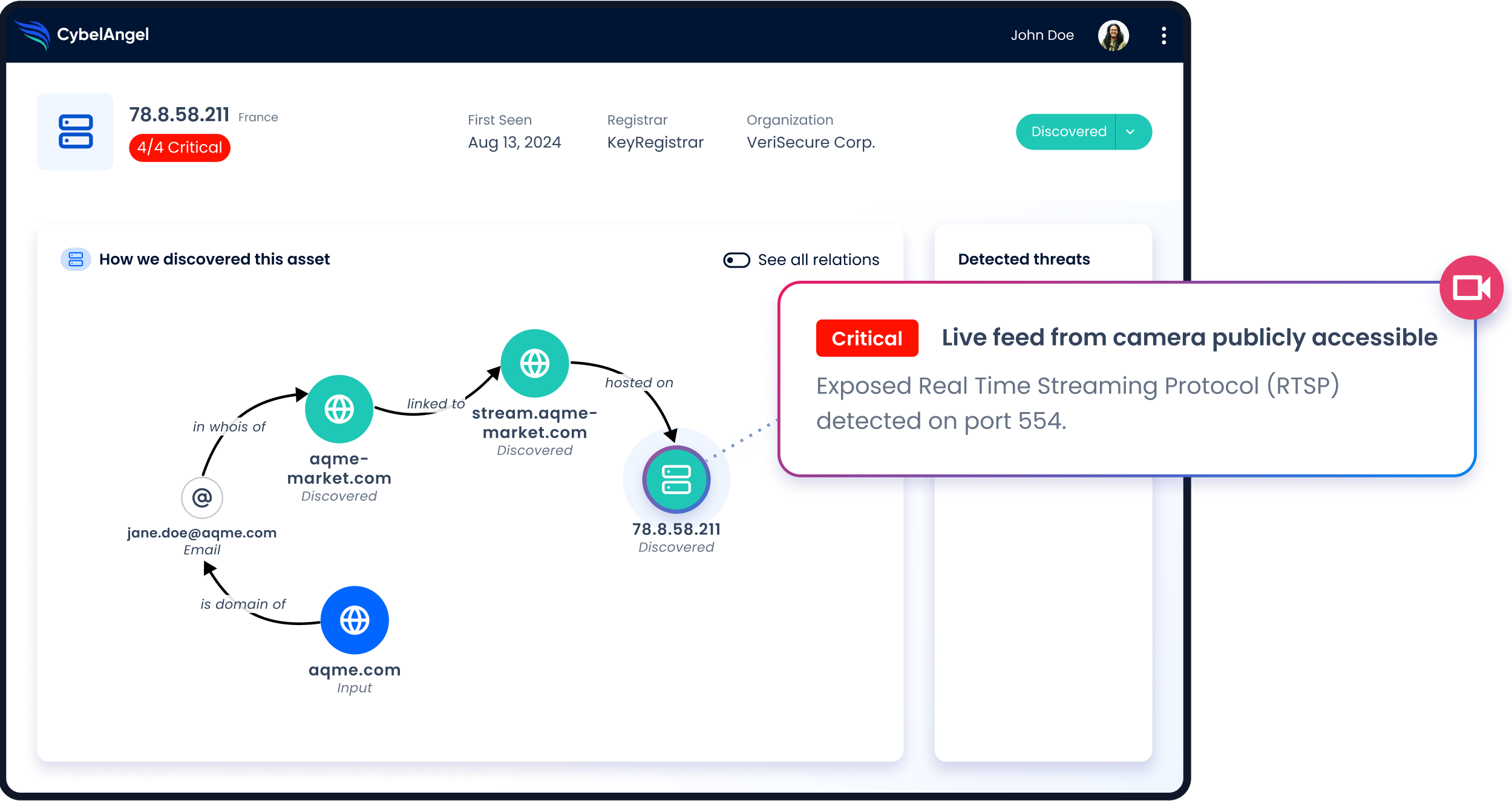
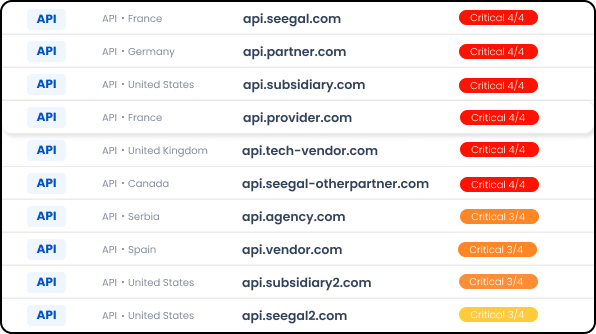
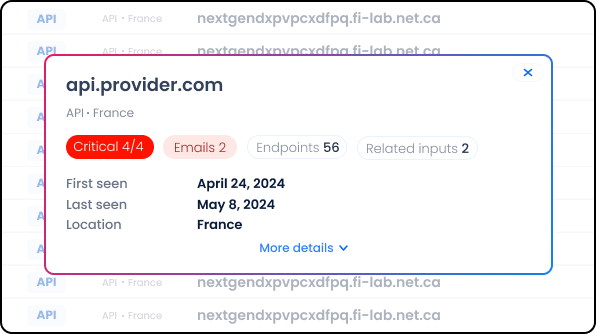
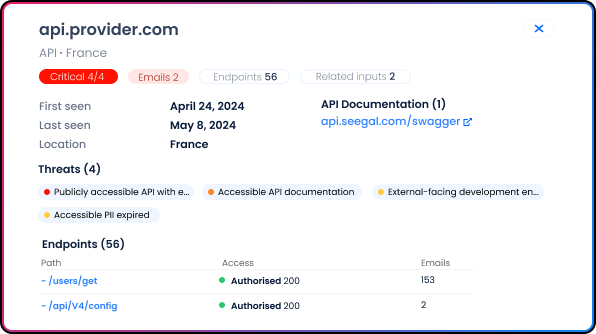
Shadow assets set up by employees, third parties, and fourth parties. We specialize in detecting shadow assets such as connected file servers, SaaS solutions, databases, industrial systems, DevOps tools, remote desktop services, and IoT devices.