What’s On the Dark Web? Your Guide to the Biggest Players in 2025

Table of contents
What can we expect from the dark web in 2025? As a hidden part of the Internet, the dark web is an ideal base for many cybercrime networks, hosting illegal marketplaces, anonymous forums, unethical software, and more.
From the rise of AI-driven cybercrime to growing global crackdowns, this blog explores the key players, emerging trends, and what businesses and individuals should prepare for in the year ahead.
1. What is the dark web?
The dark web is a portion of the Internet that is inaccessible to normal search engines.
Unlike Chrome, Bing, or Firefox, people can’t access the dark web without certain software or configurations. For example, they might need to log in via Freenet or the Tor browser, which uses onion routing to encrypt data via several different nodes.
While the dark web is not inherently illegal, it does host a range of illegal content, hidden services, and illicit activities.
Types of dark web illegal activity include:
- Hosting ransomware as-a-service (RaaS): RaaS malware can hack and encrypt sensitive data, only restoring it when a ransom payment is made.
- Selling stolen data: PII leaks can be highly profitable on dark web marketplaces, with details such as credit card information being sold to the highest bidder.
- Crypto-laundering: Cybercriminals can use the dark web to cut cryptocurrency trails, such as Bitcoin, and hide their origins. For instance, Europol took down ChipMixer in 2017, ‘one of the darkweb’s largest cryptocurrency laundromats.’
- Distributing illegal content and products: Due to the anonymity of dark web Internet users, anyone can circulate unethical content, counterfeit products, and illegal drugs without fear of reprisals.
2. Who are the biggest cybercrime gangs on the dark web?
The dark web market hosts a variety of cybercriminal groups, ranging from state-sponsored actors to independent ransomware gangs. These groups operate globally, leveraging sophisticated tools and networks to execute large-scale attacks and maintain anonymity.
Let’s explore some dark facts and trends about these threat actors.
State-sponsored threat actors
State-sponsored threat actors are cybercriminal groups supported or directly managed by government agencies on the darkweb market. They often carry out attacks that align with their country’s political, economic, or military goals.
Main state-sponsored players
- APT28 (Fancy Bear): A Russian cyber espionage group, known for its focus on NATO countries and disinformation campaigns.
- Andariel: A hacking group linked with North Korea, and responsible for cyber espionage towards aerospace and defence organizations.
- APT41(Winnti, BARIUM, Double Dragon)**: A group known for espionage and financial cybercrimes, believed to be affiliated with the Chinese government—and wanted by the FBI (below).

What to expect in 2025
In 2025, state-sponsored actors are expected to continue using the dark web for politically motivated cyberattacks. Countries like Russia, China, and North Korea are suspected of harboring or directly funding these groups.
We may also see collaborations between state-sponsored gangs, pooling resources for more devastating attacks. However, rivalries over dark web marketplaces could also lead to turf wars, disrupting their operations and creating new risks for businesses.
For example, while Russian cyber gangs have waged information warfare against Ukraine, using botnets to disseminate propaganda, Ukrainian hackers have responded by exposing the sensitive data of high-ranking Russian officials.
Infostealer threat actors
Infostealer threat actors specialize in malware that harvests personal data without consent, such as login credentials, bank accounts, and social security numbers. Their tools often spread through phishing campaigns or compromised software downloads, enabling crimes such as identity theft.
Main infostealer players
- Redline Stealer: A widely used malware that targets credentials stored in browsers and applications.
- Vidar: A malware-as-a-service tool, offering customizable data-theft capabilities.
- Raccoon: Known for targeting small businesses, this malware can steal credentials and cryptocurrency wallets. This year, a Ukrainian pled guilty to running the malware operation.
What to expect in 2025
The proliferation of IoT and 5G devices will provide new attack vectors for infostealer gangs. As AI becomes more accessible, hackers may use AI-driven tools to automate data theft on a massive scale.
Social media and gaming platforms are increasingly being used to recruit inexperienced hackers, further expanding these gangs’ reach. For example, Europol has warned the criminals will use coded messages and ‘gamification tactics’ to encourage minors to commit crimes.
Cryptocurrency threat actors
Crypto-laundering threat actors specialize in stealing and hiding the origins of their cryptocurrency. Cryptojacking involves secretly mining for cryptocurrency via the victim’s device.
Main cryptocurrency threat actors
- Lazarus Group: An allegedly North Korean-backed group notorious for stealing billions in cryptocurrency to fund its country’s economy and weapons programs.
- TeamTNT: A threat actor responsible for cryptojacking attacks, using malware to illegally mine for cryptocurrency.
What to expect in 2025
With cryptocurrency prices fluctuating, crypto-laundering gangs can capitalize on market volatility to conceal illicit funds, and use botnets to illegally mine cryptocurrency data.
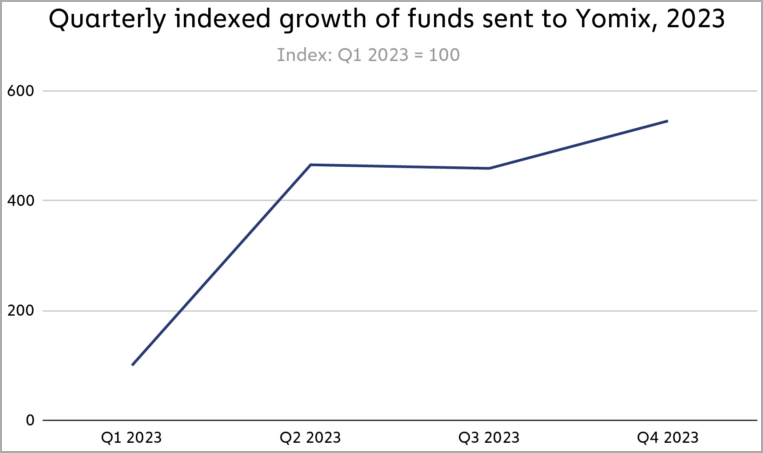
They can also take advantage of legitimate software to hide their tracks. For example, YoMix is a bitcoin mixer used by the Lazarus Group to launder their stolen cryptocurrency profits, with a massive influx of laundered funds in 2023.
Ransomware threat actors
Ransomware threat actors use malware to lock users out of their systems, demanding payment to restore access. These groups often operate on a ransomware-as-a-service (RaaS) model, renting their tools to affiliates in exchange for a share of the profits.
Main ransomware players
- LockBit: A dominant RaaS group that continues to innovate its malware to bypass security measures—and recipient of a dramatic law enforcement takedown in 2024.
- BlackCat (ALPHV): Known for targeting high-profile companies with tailored attacks, and also shutting down in 2024.
- RansomHub: A new entrant, rapidly gaining traction as a leader in the RaaS market, following the takedown of its competitors.
What to expect in 2025
The takedown of major groups like LockBit, AlphaBay and Hansa in 2024 demonstrates improved global collaboration among law enforcement agencies. However, this will likely lead to the rise of new, decentralized groups like RansomHub.
Ransomware gangs are also expected to diversify their tactics, targeting smaller companies and individual users to maximize their reach. Businesses should prepare for more sophisticated ransomware campaigns, potentially leveraging AI to exploit security gaps.
3. Dark web FAQs
The dark web raises many questions for businesses and individuals alike. Let’s take a look at some of the most common concerns.
What’s the difference between the deep web vs dark web?
The deep web refers to all online content not indexed by search engines, such as virtual private networks and internal business systems.
The dark web, on the other hand, is a small part of the deep web that requires special tools like the Tor browser to access.
Businesses can use deep and dark web monitoring tools to keep track of stolen credentials or mentions of their brand to protect against cyberattacks.
What is the Tor browser?
The Tor browser, short for The Onion Router, is software that allows users to access the Tor network. Originally developed by the U.S. Navy, it anonymizes Internet activity by routing data through multiple servers, masking your IP address.
The Tor project gained notoriety for enabling illegal marketplaces like the Silk Road, a black market taken down by the FBI in 2013—and countless cybercriminal service providers ever since. Still, the Tor dark web browser also remains a vital tool for privacy-conscious users.
Is it illegal to browse the dark web?
No, it is not illegal to browse the dark web. While it can be used for illegal activities, there are also perfectly legitimate forums, social networks, and communities.
For example, the CIA has a dark web site for anonymous reporting services. Plus, dark web search engines can also allow political dissidents to bypass government censorship, or for journalists to safely engage with whistleblowers.
Is the dark web dangerous?
Yes, the dark web can be a dangerous and unpredictable space. While it has legitimate uses, it’s also a hub for cybercriminals, hackers, and other threat actors.
For instance, dark web websites could be infected with malware, or designed as scams to gather stolen data. Tools such as VPNs can make it somewhat safer to browse, but people should still exercise extreme caution whenever visiting web pages on the darknet.
What is dark web surveillance?
Dark web surveillance involves monitoring information on the darknet, such as to identify compromised credentials being sold, or to track forums to anticipate (and prevent) cyberattacks.
Cybersecurity tools like CybelAngel’s external attack management (EASM) platform can help businesses monitor the dark web effectively. By providing real-time insights into threats, these tools enable companies to safeguard their brand and prevent data breaches before they occur.
Wrapping up
From state-sponsored groups to ransomware gangs, criminal activity is innovating at a rapid pace on the dark web. Businesses must stay vigilant and proactive in addressing these threats, using tools like CybelAngel to monitor dark web activity and protect their assets.

