OSINT Done Right: A Guide for Security Teams

Table of contents
There’s more public data online than ever. And plenty more ways to misuse it. Cybercriminals can scan forums, scrape social media, and piece together details from forgotten websites. But when security teams turn that same data into intelligence, it changes the balance.
That’s the promise of OSINT. Not just gathering information, but using it with purpose. In this guide, you’ll learn how to build an OSINT framework that’s structured, repeatable, and built for action.
An introduction to open-source intelligence (OSINT)
Open-source intelligence (OSINT) is the practice of gathering and analyzing data from publicly available sources.
That could mean forums, public records, social media platforms, or forgotten web pages indexed by search engines. If it’s online and legally accessible, it’s fair game.
But OSINT isn’t just about collecting raw data. It’s about turning scattered, often messy, information into something useful.
OSINT can:
- Support threat detection
- Inform decision-making
- Expose risk before it’s exploited
And that’s why a structured approach matters. Because without a clear framework, OSINT efforts become ad hoc (easy to start, but hard to scale or trust).
Let’s walk through how to build one properly, using a model that reflects the full threat intelligence lifecycle.
What is OSINT? (And what isn’t it?)
As we said before, OSINT stands for Open-Source Intelligence. At its core, it means collecting information from publicly available sources, then analyzing that data to support security decisions.
But what sets OSINT apart isn’t the data itself. It’s the way it’s used. Not everything online counts as OSINT.
A random tweet?
Maybe.
A leaked password file on a dark web forum?
Probably.
But OSINT isn’t just about finding things. It’s about finding the right things, in context, and turning them into actionable intelligence.
Done right, OSINT helps you answer critical questions:
- Where are our digital assets exposed?
- What are attackers saying on social networks and forums?
- Which vulnerabilities are being targeted in real time?
It’s a powerful method, but it has limits. OSINT relies on publicly available data, not privileged access. That’s what makes it legal, ethical, and often overlooked (until it’s too late).
You’ll find OSINT tools used across cybersecurity, threat hunting, law enforcement, phishing detection, fraud investigation, and even national security.
But whatever the mission, the underlying techniques remain the same. And all of it happens via publicly-available information (PAI).
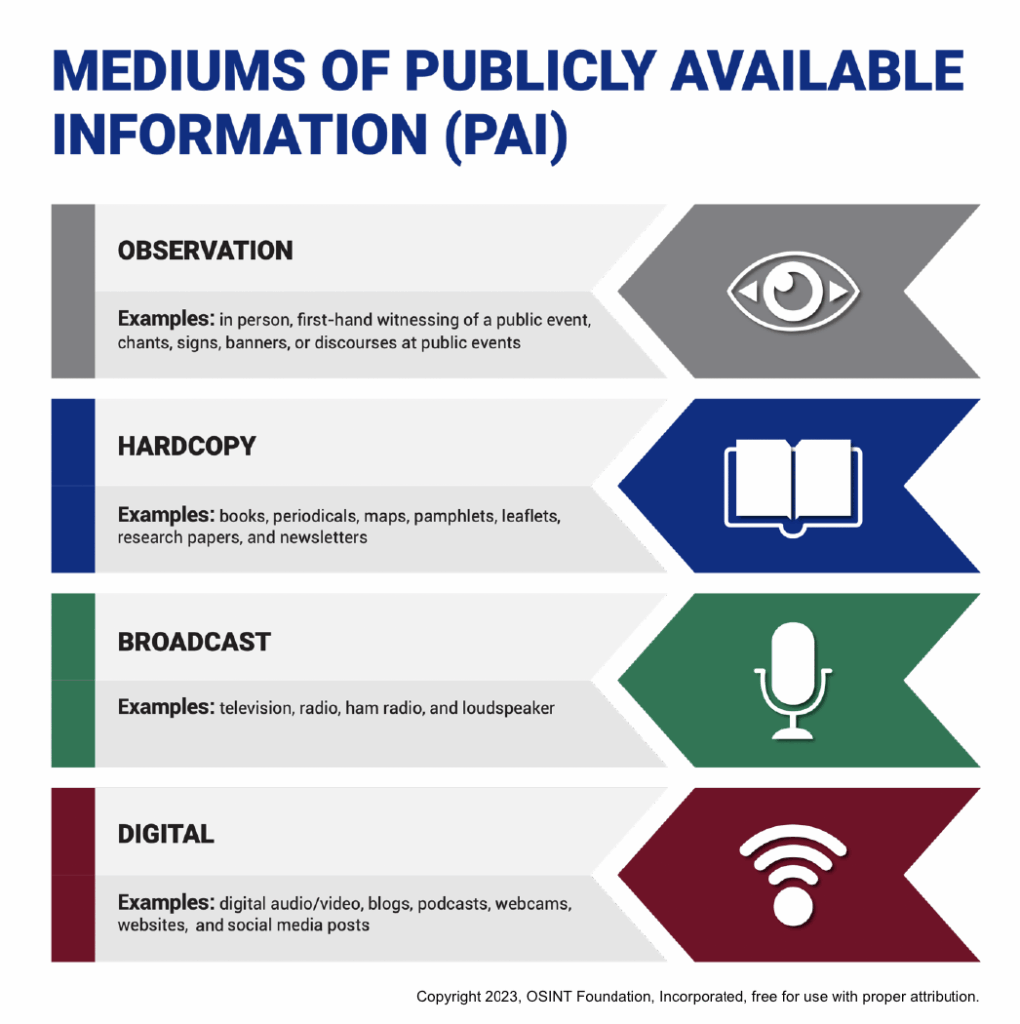
Why you need an OSINT framework
Remember, anyone can run a Google search. And anyone can scroll through Telegram or scrape a domain registry. But OSINT is about building a system that delivers reliable, repeatable insight. And that’s where a framework comes in.
Without structure, OSINT falls apart. For example, you might collect too much raw data, chase the wrong sources, duplicate work, or miss critical signals. Over time, your team could lose confidence in the process (or worse, in the results).
On the flip side, a solid OSINT framework gives you and your team focus.
It defines:
- Why you’re collecting the data
- What you’re looking for
- How to turn that data into something you can act on
It also builds in guardrails (legal, ethical, and operational) that help avoid missteps when OSINT practitioners are handling sensitive information.
Most importantly, a framework allows your OSINT research to scale. Whether you’re tracking phishing infrastructure, monitoring brand abuse, or supporting threat intelligence, you need a method that works across datasets, teams, and time zones.
That’s what the OSINT lifecycle is designed to do. Let’s break it down in more detail.
The OSINT intelligence lifecycle
OSINT isn’t just a single task. It’s a whole process that’s often called the ‘intelligence lifecycle.’ Here are its five phases.
1. Planning and direction
Start with intent. What questions are you trying to answer? Which threat actors, campaigns, or data types matter to your team?
This step sets your priorities. It’s also where you define legal boundaries and ethical limits, which are especially important when working with sensitive information.
2. Collection
This is where raw data comes in. You might collect it from search engines, forums, social media, public records, code repositories like GitHub, and more.
It can also include passive reconnaissance, monitoring domain registrations, scraping social media platforms, or harvesting metadata from public datasets.
Whatever publicly-available information (PAI) you use, the key is staying organized. Because without a clear strategy, you’ll quickly get overwhelmed.
This is where tools like CybelAngel can help.
CybelAngel can automate the discovery of exposed credentials, documents, and assets across the open, deep and dark web. Learn more about its threat intelligence solutions to see how.
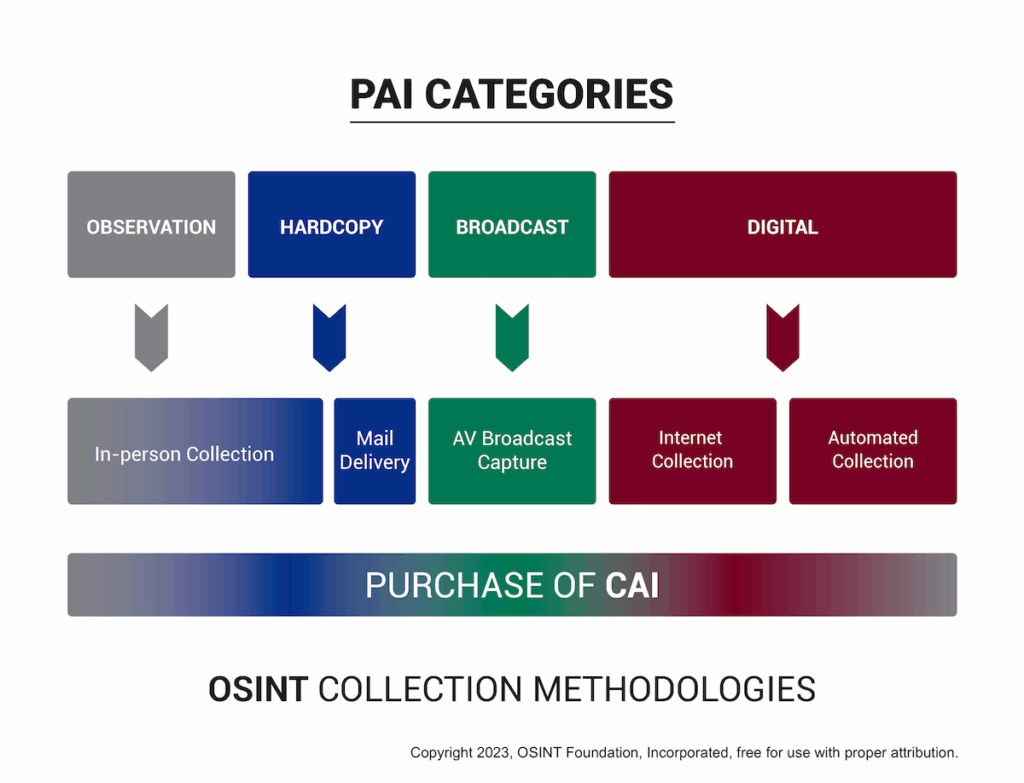
3. Processing and exploitation
Once collected, the data needs cleaning. That means de-duplicating results, extracting metadata, structuring formats, and removing irrelevant entries.
This forms the bridge between raw data and usable input. This is also where artificial intelligence, machine learning and APIs can help, especially when processing thousands of web pages, IP addresses, or social media posts.
4. Analysis and production
Now comes the thinking. You identify patterns, connect data points, and flag anomalies.
For instance, let’s say a phishing domain shares infrastructure with a known malware campaign. Or a social media account links to a GitHub repo full of ransomware samples.
This phase turns facts into context. And context into conclusions. Clear communication matters here, as your analysis must be understandable, even to non-technical teams.
5. Dissemination and feedback
Threat intelligence isn’t useful if it never leaves the analyst’s desktop. This phase is about getting insight into the hands of people who need it. That could be a SOC analyst, a threat intel lead, or a crisis response team.
Feedback loops also happen at this stage. You might ask questions such as:
- Did the intel help?
- Was it too late?
- Did it lead to action?
Use what you learn to improve the next round of collection and analysis.
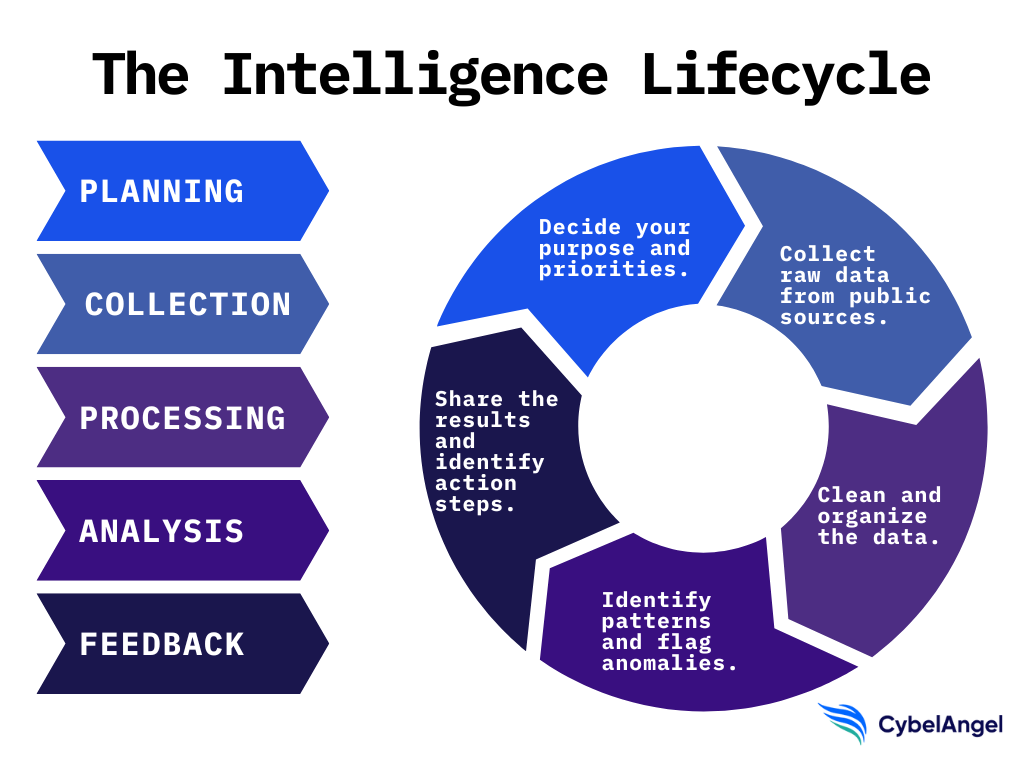
Together, these five phases create a repeatable loop. Each one strengthens the others. And as your OSINT practice develops, so too does your ability to stay ahead of emerging threats.
OSINT techniques, not just tools
Tools matter, but technique is what makes OSINT work. Without the right approach, even the best platforms can get lost in data. Here are some core tactics that every OSINT workflow should include:
- Search engine refinement: Using advanced operators (like Google Dorks to run even more targeted searches) to uncover indexed but forgotten content, like login pages, error logs, or exposed documents.
- Metadata extraction: Pulling information from images, PDFs, and documents to reveal file paths, timestamps, and user info. This is all useful for mapping infrastructure or identifying insider leaks.
- Social graph mapping: Tracking activity across social networks like LinkedIn, GitHub, or even TikTok to understand connections between threat actors, employees, or influence operations.
- Forum and dark web monitoring: Scanning marketplaces, encrypted chats, and paste sites for mentions of your organization, domains, or leaked data points.
- Passive DNS and IP tracking: Following infrastructure changes, DNS trails, and reused servers that point to phishing campaigns, malware infrastructure, or spoofed sites.
- Public code and repo analysis: Scanning GitHub or package managers for exposed credentials, configuration files, and open attack surfaces.
- Social engineering indicators: Watching for fake executive profiles, cloned websites, or impersonation campaigns designed to lure employees or customers.
The best OSINT workflows mix these techniques depending on the mission.
Building a repeatable OSINT workflow
If your OSINT process only works when one person runs it, it’s not a framework. It’s a habit. And habits don’t scale. A good OSINT program should work across teams, time zones, and use cases without breaking down.
- Define roles and responsibilities: Assign ownership early. Who collects the data? Who verifies it? Who flags threats or writes the reports? Clear roles avoid confusion and reduce missed signals.
- Standardize your sources and tools: Agree on where your intel comes from and which tools your team trusts. This could include social media platforms, dark web forums, search engines, or API-powered enrichment services.
- Create a collection rhythm: Decide how often your team collects OSINT. For some, it’s a daily scan. For others, it’s threat-driven. Whatever the cadence, document it. Keep track of when, where, and how data was gathered.
- Triage and prioritize findings: Not everything you collect needs a response. Define what counts as urgent (like leaked credentials or real-time phishing domains) and what can wait.
- Feed OSINT analysis into your existing systems: Integrate findings with your threat intelligence platform, SIEM, or case management tool. If data just sits in a spreadsheet, it doesn’t help anyone.
- Review and adjust regularly: What worked last quarter may not work in the next one. Hold regular reviews. Drop stale sources, promote new ones, and check how you’re evaluating the data along the way.
Ethical and legal considerations in OSINT
Just because data is public doesn’t mean it’s fair game. Good OSINT doesn’t just follow the rules. It respects the boundaries.
At the core of ethical intelligence gathering is intent. Are you collecting data to protect your organization, or to profile individuals without cause? Are you storing sensitive information responsibly, or archiving everything just in case?
Here are a few guardrails every OSINT methodology should follow:
- Stick to publicly available data: This means no hacking, bypassing paywalls, or scraping systems that explicitly prohibit it. If your collected data requires deception, it’s not OSINT. It’s a breach.
- Understand jurisdiction: What’s legal in one country might be a restricted source of information in another. This matters if you’re collecting data across borders or from international platforms.
- Avoid unnecessary collection of personal data: OSINT often intersects with names, emails, and even phone numbers, especially in social engineering or fraud investigations. If you don’t need it, don’t keep it.
- Don’t confuse visibility with consent: Just because something is posted publicly (on a forum or social media) doesn’t mean it was meant for you. Treat sensitive information with care.
- Secure your own data: The intel you gather (from IP addresses to leaked credentials) may itself become a target. Store and handle it like it matters, because it does.
- Train your team: Whether you’re in law enforcement, corporate security, or threat hunting, make sure everyone understands your ethical and legal standards. Consistency protects everyone.
Structured OSINT is powerful, but mishandled, it becomes a liability. A clear framework helps teams stay on the right side of the line, even under pressure.
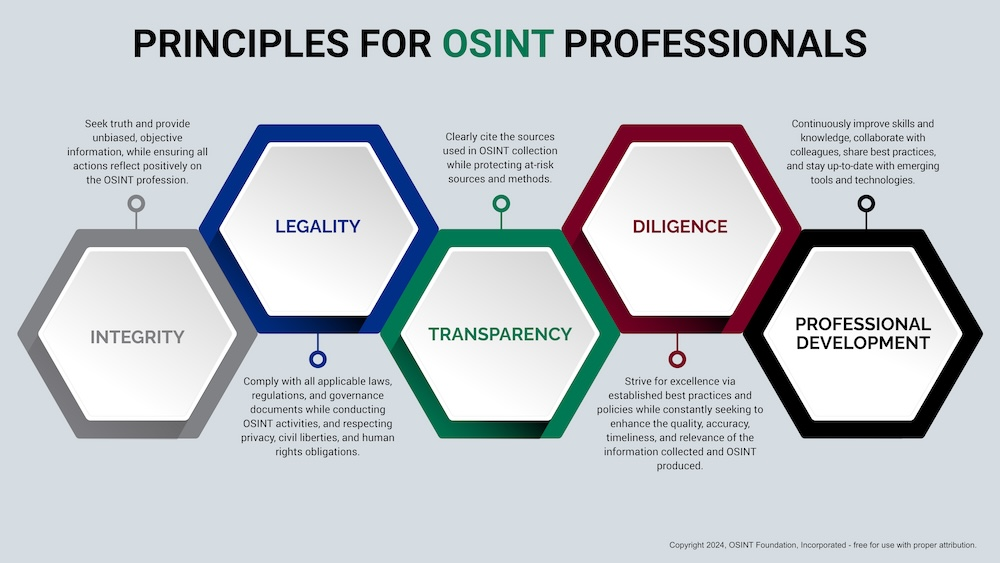
The OSINT Foundation, a US organization, lists five core values for professionals implementing OSINT, including integrity and legality (see below).
Where CybelAngel can help
Not every stage of OSINT needs to be manual. In fact, it shouldn’t be. The collection and processing phases can become a time sink, especially when you’re tracking large volumes of public data.
That’s where CybelAngel adds value.
The platform automates data collection from high-risk sources: exposed servers, misconfigured APIs, forgotten cloud storage, social platforms, and even hard-to-reach corners of the dark web. It also handles the processing step, structuring raw data, enriching it, and prioritizing what matters most.
This leaves your team free to focus on analysis and response, where human judgment is hardest to replace.
CybelAngel helps OSINT teams:
- Monitor a wide range of publicly available sources in real time
- Detect threats like phishing kits, credential leaks, and sensitive data exposure
- Track threat actors across forums, social media, and infrastructure
- Turn large datasets into actionable intelligence without adding analyst overhead
- Integrate findings into your existing security stack through APIs and alerts
Whether you’re running a full threat intelligence program or starting to formalize OSINT workflows, CybelAngel brings scale to the work you already do.
Talk to us to find out more about its threat intelligence capabilities.
FAQs about OSINT
Is OSINT legal?
Yes, as long as you’re gathering data from publicly accessible sources without deception or unauthorized access. Using OSINT for espionage, surveillance without cause, or data misuse crosses legal and ethical lines.
Where did OSINT come from?
Open source information has roots in wartime broadcast monitoring, with formal adoption in US intelligence traced back to the 1940s. It gained renewed attention post-9/11, when the US established the DNI Open Source Center to improve national security through public data use.
What are the biggest challenges in OSINT?
- The overwhelming volume of data
- Evaluating the reliability of data sources
- Staying within ethical and legal boundaries
- Avoiding duplication or “amateur crowd-sourcing” pitfalls
Are there OSINT certifications or professional groups?
Yes. There’s a big open-source intelligence community, including the OSINT Foundation, OSMOSIS, and IntelTechniques. Certifications like Open Source Certified (OSC) or OSIP help standardize ethical and legal best practices.
Can OSINT detect cyberattacks in real time?
When structured properly, yes. OSINT helps surface early signs of phishing, leaked data, and hacker infrastructure, particularly during passive reconnaissance phases.
What tools or platforms should I use for OSINT?
It depends on your goals. Popular tools include search engines, metadata extractors, dark web crawlers, and social media monitors. Platforms like CybelAngel help automate large-scale collection and processing so you can focus on analysis.
Is social media a good source for OSINT?
Absolutely. Social platforms often reveal phishing scams, executive impersonation, or leaked credentials before traditional security tools do.
Can OSINT be automated?
Parts of it can, especially collection and processing. Using automation reduces manual workload and helps flag high-risk findings faster.
Conclusion
OSINT is about turning public information into insights that protect your brand. A well-built OSINT program helps you move faster, stay focused, and avoid missteps.
And with automation platforms like CybelAngel, you can streamline collection and processing, freeing your team to analyze what really matters.

