How to Overcome Vulnerabilities in Digital Signatures

Table of contents
Why are digital signatures a cyber threat?
And, why should cybersecurity professionals review these vulnerabilities?
For businesses that handle significant volumes of sensitive data both within their operating system and through external channels, digital signatures are essential. They safeguard data integrity while ensuring that information remains accessible to authorized users.
Related content: Read our guide to EASM: 9 FAQs Every CISO Should Know.
Keep reading to learn how understanding the vulnerabilities of digital signatures could be key to protecting your company from security threats.
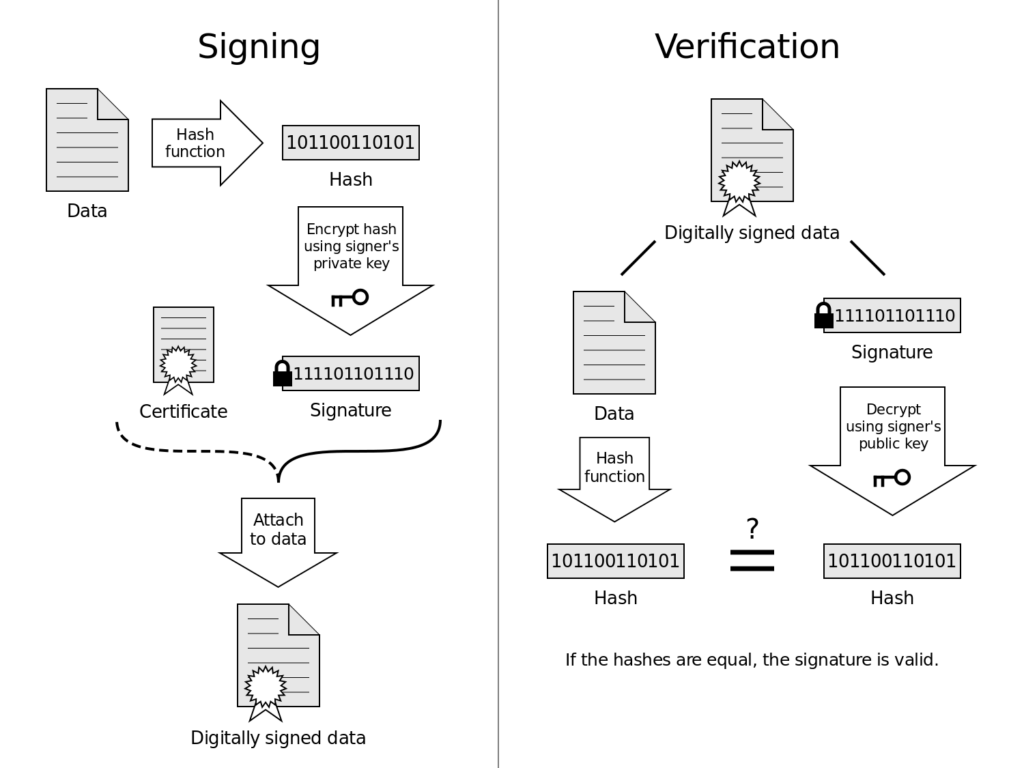
How do digital signatures work?
Firstly, let’s review how digital signatures actually work.
Digital signatures are encrypted electronic identifiers that verify the authenticity and integrity of digital documents, communications, or transactions.
They ensure that the data exchanged is from:
- A verified source and has not been tampered with
- Uses cryptographic techniques to facilitate these secure processes
Essentially, a digital signature is a mathematical technique used to validate the authenticity and integrity of a document. The process is based on the Public’s Key Infrastructure (PKI) and is two fold, relying on encryption and verification.
How does a PKI enhance network security?
Public Key Infrastructure (PKI) is a framework crucial for signature security, designed to deter malicious activity and enhance network security. It involves using cryptographic processes and digital certificates to authenticate users and devices, ensuring secure and private digital interactions across various platforms, from web browsers to internal organizational communications. PKI’s core objectives are maintaining the confidentiality of sensitive data and confirming the identity of the sender in real-time.
Now let’s review the security policies and security threats within digital signatures.
Private keys and encryption
Why are private keys important when it comes to data integrity?
An algorithm is used to generate a hash from the contents of the confidential document or file. This hash, a fixed length string, corresponds uniquely with the content of the document. This is then encrypted using the PKI.
The PKI, or asymmetric cryptography, generates two keys:
- One public key
- One private key
The signer uses the private key to encrypt (or “to sign”) the hashed data, creating a digital signature that authenticates the confidential data and its source.
Since the hashed value is unique to the confidential data, if the data integrity is altered in any way, the key would not verify encrypted data accurately. This indicates that the security and data integrity of this file has been compromised.
Cybersecurity takeaways
What to remember:
When this signed data is sent, it is sent along with a digital certificate containing authentication information about the sender’s identity and the corresponding public key. This digital certificate is issued by a certifying authority that must comply with local laws and regulation.
Decryption within digital signatures
- Once the hashed and encrypted data has reached its destination, the recipient’s software will decrypt the encrypted hash using the public key sent through the certificate.
- Then the recipient’s machine will generate fresh hash values for the raw data that was sent. If both values appear to be equal, the integrity of the document has been preserved, and validates the transaction.
Cybersecurity takeaways
What to remember:
Though digital signatures are effective and necessary for us to conduct our business online, they are not foolproof. Digital signatures have vulnerabilities and flaws that can be exploited by malicious actors targeting your business.
 Source : Center for Advanced Studies, Research and Development in Sardinia (CRS4), available here
Source : Center for Advanced Studies, Research and Development in Sardinia (CRS4), available here
Three digital signature security threats
Here are three core threats to review as a CISO.
1: Fraudulent digital certificates and social media phishing
The legitimacy of digital signatures are dependent on the certificate that authenticates the content and the signer. Though there are various reputable and legitimate digital certifying authorities that allow companies to obtain digital certificates, fraudulent and fake digital certificates are a growing issue in cyber security.
Why?
- Legitimate certificates available for purchase on the dark web
- There is a rising trend of malicious actors impersonating company executives
These fraud attacks begin with social engineering. Once hackers complete reconnaissance, through publicly available sources such as LinkedIn, they begin their attack to mislead the certification authority. Attackers use the top level domains of legitimate companies to mislead certificate authorities during the identification validation process.
Once this step is complete, the threat actor is free to purchase verified certificates which can be used to send their victims trustworthy-looking malware.
2: Stolen keys and malware
Another way malicious actors exploit digital signatures is through the PKI system.
Attackers can use brute force, social engineering, or other ways to steal private keys that belong to your organization, or to one of your third parties. These keys can then be used to sign malware, which is sent to you as a certified and secure folder, bypassing security measures such as browser filters and antivirus programs you may have installed.
A malware use case
For example, cybersecurity researchers discovered a malware that was digitally signed by using compromised keys of the multinational Taiwanese tech company D-Link. This malware, propagated by the malicious hacker group, BlackTech, is essentially a backdoor used to steal proprietary data, and target users of browsers such as Google Chrome, Internet Explorer, Microsoft’s Bing, among other programs.
Though D-Link has since revoked the stolen certificates and keys, BlackTech continues to use the revoked certificate as often even though antivirus softwares do scan for a certificate, they do not scan for the validity of the certificate.
3: Compromised detection systems
Compromised certificate authorities in turn compromise detection methods.
As digital signatures and their certifications become an underlying foundation of digital businesses, security of the digital landscapes rely heavily on certification authorities.
In 2011, often known as the worst year for certification authorities, digital certification giants including ComodoCA and the Dutch Certification Authority (DigiNotar) were compromised. This resulted in several fraudulent issuances of digital certificates across domains, including Yahoo, Google, Skype etc. A compromised certificate authority can lead to anything between economic fraud perpetrated by well known attackers to cyber warfare.
What are some examples of vulnerabilities?
But what is worse than a compromised certificate authority is a careless one.
Over the last few years those who actively use digital certificates have grown from a few large software manufacturing companies to many individual software developers and small companies. It is becoming increasingly difficult for certificate authorities to verify malicious activities, and also keep track in real time of who they are issuing authentic certificates to.
Intrusion detection is getting harder
Some certificate authorities require basic verification, like an individual’s passport, or the registration details of a company.
Therefore, a cybercriminal could legally purchase an authentic certificate to digitally sign their malware. In these cases, very often certificate authorities do not always recall the certificate, maintaining the authenticity of the certificate and leading to the spread of more dangerous software.
Today, hackers often use legally obtained digital certificates to make a mobile app seem safe, and then use it to attack your phone or install malware.
Let’s take a look these targeted mobile app incidents.
Malicious software insights: Digging into compromised mobile apps
These three mobile app vulnerabilities targeted behavior based users to gain access.
Vulnerability spotlight (CVE-2020-4099)
In 2020 researchers discovered the vulnerability (CVE-2020-4099) which found that if an application was signed using a key which was equal to or shorter than 1024 bits, the application would be vulnerable to forged digital signatures.
Therefore a malicious actor could potentially alter the app to include a backdoor or malware and forge the same digital signature to secure it again. The vulnerability was found on the mobile app HCL Verse, a mobile email application for Android phones. According to Google Play, today the application has over a million downloads.
Vulnerability spotlight (CVE-2023-12345)
In 2023, a critical vulnerability (CVE-2023-12345) was discovered in the popular mobile banking app from a major financial institution. The vulnerability stemmed from improper input validation on the server-side, allowing attackers to inject malicious code and potentially gain unauthorized access to sensitive financial data and user accounts.
This malware existed in the way the app handled Bluetooth connections, enabling an attacker within range to send specially crafted packets and exploit the vulnerability to potentially lead to data theft, device compromise, and other malicious activity.
The vulnerability affected both the Android and iOS versions of the app, putting millions of users at risk until a patch was released.
Vulnerability spotlight (CVE-2024-54321)
Another vulnerability (CVE-2024-54321) was found in a popular social media app in mid-2024, which could allow attackers to bypass authentication measures and gain unauthorized access to user accounts and private data.
The vulnerability was related to insecure storage of authentication tokens on the device, enabling an attacker with physical access to extract the tokens and impersonate the user. The app had over 500 million active users at the time, making the potential impact of the vulnerability significant.
Code signing abuse
Code signing is the process of digitally signing software to validate its source and integrity for its users. The software developers sign their software backed by a digital certificate to authenticate their code, confirming its originality and establishing the coder’s legitimacy. This process not only increases the reputation of the code, signaling that it is not malicious, but also plays a crucial role in maintaining the security and data integrity of internal codes, scripts, or packages within enterprises.
However, code signing can be vulnerable to abuse by hackers. They can still acquire a certificate, legally or illegally, to endorse their harmful code. The presence of a certificate and code signature may mislead detection methods. In the end, users believe that the software is safe and reputable.
How to protect the data integrity of your code?
To mitigate these risks, integrating threat intelligence and threat detection practices is essential. These measures can alert developers and security teams about potentially compromised certificates or unusual signing activities. Additionally, employing notifications for any anomalies detected during the code signing process can provide an early warning system. It then enables a prompt investigation and remediation efforts.
Moreover, securing the web server and infrastructure used for code signing processes against unauthorized access is fundamental.
Our external attack surface detection systems help cybersecurity teams deal with everything from planned ransomware attacks to dark web plots. Take a look at how we can help.
Cyber attack use case: SolarWinds
In 2021, the American software development company SolarWinds fell victim to a major cyber-attack conducted by a Russian hacking group. This incident highlighted the vulnerabilities present when there is a lack of robust linkage between the source code repository and the code signing system. The attackers were able to inject malicious code into the source code before it went through the digital signing process. This lead to an estimated infection of over 18,000 systems worldwide and causing billions in damages.
This cyber attack really underscores the critical need for comprehensive security measures, including advanced threat intelligence, strengthened threat detection capabilities, and effective notification protocols, to safeguard the integrity of code signing practices.
Little know execution vulnerabilities
A lesser known vulnerability is exploitable when digital signatures are being verified.
Here is what you need to know.
When executing a digital certificate, the algorithm tends to overlook the header storage size. Often, this space is used by software developers to add links or new content to the code without having to alter the main code and re-authenticate and re-sign it again. However, hackers can exploit this by adding dangerous content in this space. They can do this without ever having to change the content that is protected by the signature at all.
The verifying algorithm could potentially execute this dangerous content while executing the code, despite the security provided by the signature. Additionally, due to the digital signature, the malware is likely to not be detected by any firewalls as well.
Unfortunately, although this is not an illegal method, as they do not deface the signature, it is a grey area. Hackers can carry out malicious attacks within the realm of legality.
Be careful when it comes to these lesser known issues.
Digital signature security really is key
Digital signatures are vital for modern online business operations but are vulnerable to several exploits. As we continue to depend more on digital certifications, understanding these risks is imperative. So is implementing robust security measures to protect your data’s integrity.
For enhanced security, it is crucial to be as vigilant with digital authenticity as we are with physical security measures. Understanding the function and potential vulnerabilities of digital signatures is essential for maintaining robust cybersecurity.
Looking to learn more about security threats? Read our annual report executive summary or watch the report highlights from our CISO Todd Carroll.