Why is Time-to-Exploit Collapsing? [AI Threat Review]

Table of contents
Did you know that last year, nearly one-third of vulnerabilities were exploited on or before they’re publicly disclosed, creating “zero-day” scenarios where attackers move faster than defensive patch cycles? The time between when a vulnerability is disclosed and when attackers exploit it, known as Time to Exploit (TTE), has collapsed from 63 days in 2018 to just 5 days in 2024.
While artificial intelligence and large language models are accelerating this trend, the reality is more nuanced than headlines suggest. AI functions as a powerful efficiency multiplier rather than a revolutionary game-changer, amplifying existing attack methodologies while simultaneously creating new defensive opportunities. For European organizations navigating NIS2, the Cyber Resilience Act, and DORA compliance, understanding this evolving threat landscape isn’t just academic, it’s existential.
What do the numbers tell us?
The statistics paint a stark picture. In 2023, Mandiant analyzed 138 exploited vulnerabilities and found the average TTE had plummeted to just 5 days. Fortinet’s analysis of 97 billion exploitation attempts in 2024 confirmed this timeline. But the distribution reveals an even more urgent reality:
- 28% of vulnerabilities are exploited within 24 hours of disclosure
- 29% are exploited within one week
- 56% are exploited within one month
- 32.1% are exploited on or before disclosure date, meaning zero-day attacks before patches even exist
Compare this to organizational response times: companies take an average of 74 days to patch critical application vulnerabilities, 55 days for network vulnerabilities, and 32 days for edge devices like VPNs and firewalls.
This creates a systematic 6-20x vulnerability window where attackers operate freely before defenses catch up.
But here’s what the CVE-focused statistics miss: the vast majority of successful breaches don’t rely on newly disclosed vulnerabilities at all. They exploit persistent weaknesses, misconfigurations, weak credentials, and human factors that never receive CVE identifiers. While we measure TTE in days for documented vulnerabilities, attackers are simultaneously exploiting exposure windows that have existed for months or years.
Traditional “Patch Tuesday” monthly cycles, once considered industry best practice, are now dangerously obsolete. When attackers exploit vulnerabilities in hours or days, organizations patching on monthly schedules are fighting with one hand tied behind their backs.
How does AI actually accelerate attacks?
Recent research reveals AI’s actual capabilities in exploit development, moving beyond hype to documented evidence. In 2024, IBM researchers tested ChatGPT-4’s ability to exploit real-world vulnerabilities. When provided with CVE descriptions, ChatGPT-4 achieved an 87% success rate in exploiting one-day vulnerabilities.
Without those descriptions? Success plummeted to 7%.
This 80% performance gap reveals a critical truth: AI excels at accelerating exploitation when information is available, but struggles with novel vulnerability discovery. But AI’s impact extends far beyond CVE exploitation. LLMs are increasingly effective at identifying and exploiting common web application vulnerabilities that never receive formal CVE designations.
SQL injection automation
AI can analyze web applications to identify potential injection points, generate varied SQL payloads, and iterate based on error responses. This transforms SQL injection from a manual, time-intensive process to an automated reconnaissance capability. Organizations with exposed database interfaces face AI-powered probing that tests thousands of injection variations in minutes.
Credential stuffing and password spraying
LLMs enhance credential-based attacks by generating contextual password variations based on leaked credential databases, company information, and social media intelligence. AI analyzes naming conventions, common corporate password policies, and personal information to create highly targeted credential lists, dramatically increasing success rates for password spraying campaigns.
Phishing and social engineering
AI-generated spear-phishing emails achieved 54-60% click-through rates compared to 12% for traditional approaches, while reducing creation time from 16 hours to 5 minutes. This represents a 95% efficiency gain. LLMs craft personalized phishing content by analyzing target communications, writing styles, and organizational contexts scraped from public sources and data leaks.
Israeli researchers demonstrated CVE-focused acceleration potential by using Anthropic’s Claude-Sonnet-4.0 to generate 14 working exploits in just 15 minutes each, at a cost of roughly $1 per exploit.
Here’s what this means for your organization: the window between disclosure and weaponization has essentially disappeared for well-documented CVE vulnerabilities. Meanwhile, common application vulnerabilities without CVE identifiers, exposed credentials, and misconfigured services represent equally accessible attack vectors that AI can identify and exploit at scale.
Are threat actors already using AI?
Nation-state actors are deploying AI in operational campaigns. Google’s Threat Intelligence Group documented the first “just-in-time” AI-powered malware in November 2025. Russian APT28 deployed PROMPTSTEAL against Ukraine, using Hugging Face’s API to dynamically generate reconnaissance commands and exfiltrate documents during execution rather than hard-coding functionality.
OpenAI’s June 2025 threat intelligence report revealed they had disrupted 10 major malicious AI operations spanning China, Russia, Iran, North Korea, and other actors. Primary use cases included fake persona generation for social engineering, automated phishing content creation, and code development assistance.
AI-enhanced initial access techniques
Beyond CVE exploitation, threat actors increasingly use AI to gain initial access through non-CVE vectors. AI-powered tools scan exposed assets across an organization’s digital footprint, identifying misconfigured cloud storage, exposed administrative interfaces, leaked API keys, and vulnerable web applications. These tools correlate information from multiple sources, OSINT databases, code repositories, and breach databases to build comprehensive attack maps without relying on disclosed CVEs.
Rather than brute-force attacks, AI analyzes leaked credential databases, corporate structures, and naming conventions to generate highly targeted credential lists. AI-enhanced scanners identify SQL injection,cross-site scripting, authentication bypasses, and business logic flaws in web applications without requiring CVE databases.
In our threat actor monitoring, we’ve observed this dual-track approach: sophisticated actors maintain CVE exploitation capabilities while simultaneously scaling non-CVE initial access techniques using AI automation.
What can’t AI do yet?
Despite alarming capabilities, AI faces significant limitations. Research on web vulnerability reproduction found even the best LLM agents achieved only 22.5% end-to-end success rates. Complex binary exploitation remains beyond AI’s reach. LLMs achieved 10.5-57.9% success on Capture the Flag challenges but failed completely (0% success) on real-world production CVEs.
AI cannot autonomously discover novel vulnerabilities without existing documentation. The 87% vs. 7% success rate with and without CVE descriptions demonstrates AI’s fundamental dependence on human-generated information. However, AI excels at identifying patterns in exposed data and system configurations that human analysts might miss. While it struggles with novel zero-day discovery in compiled binaries, it effectively identifies misconfigured S3 buckets, exposed database instances, and leaked API credentials.
What other factors are driving faster exploitation?
Attributing the TTE collapse solely to AI oversimplifies a complex phenomenon. Mass scanning tools like ZMap, Masscan, Shodan, and Censys enable attackers to scan the entire IPv4 address space in under an hour. They can identify vulnerable systems within minutes of disclosure, a capability that predates modern LLMs by over a decade. These tools identify not just CVE-vulnerable systems, but also exposed administrative panels,misconfigured services, default credentials, and authentication weaknesses.
The money driving exploit development has intensified dramatically. Zero-day exploit prices have reached $5-7 million for iPhone and Android zero-click vulnerabilities, with 44% annual price inflation. Meanwhile, stolen credentials, database dumps, and access to compromised systems sell for hundreds to thousands of dollars, creating parallel economic incentives for non-CVE attack vectors.
Organizations published 40,009 CVEs in 2024, a 20% increase from 2023. Simultaneously, organizations’ digital footprints expand across cloud services, SaaS applications, third-party integrations, and shadow IT. Each expansion creates potential exposure points:misconfigured cloud storage,exposed development environments, and forgotten staging servers that may never appear in CVE databases but remain exploitable for years.
Beyond CVE-focused TTE metrics
While CVE-focused TTE metrics dominate security discourse, they represent only a fraction of actual attack vectors. The most common initial access methods don’t involve recently disclosed vulnerabilities at all.
Configuration vulnerabilities
Misconfigured cloud storage accounts for thousands of data breaches annually, yet these exposures rarely receive CVE identifiers. Organizations inadvertently expose S3 buckets with public read/write access, Azure blob storage with anonymous access, exposed database instances without authentication, and publicly accessible administrative dashboards.
These misconfigurations persist indefinitely until discovered, creating permanent vulnerability windows far exceeding the 5-day CVE exploitation timeline. Our digital risk protection services continuously monitor for these exposures across organizations’ expanding digital footprints.
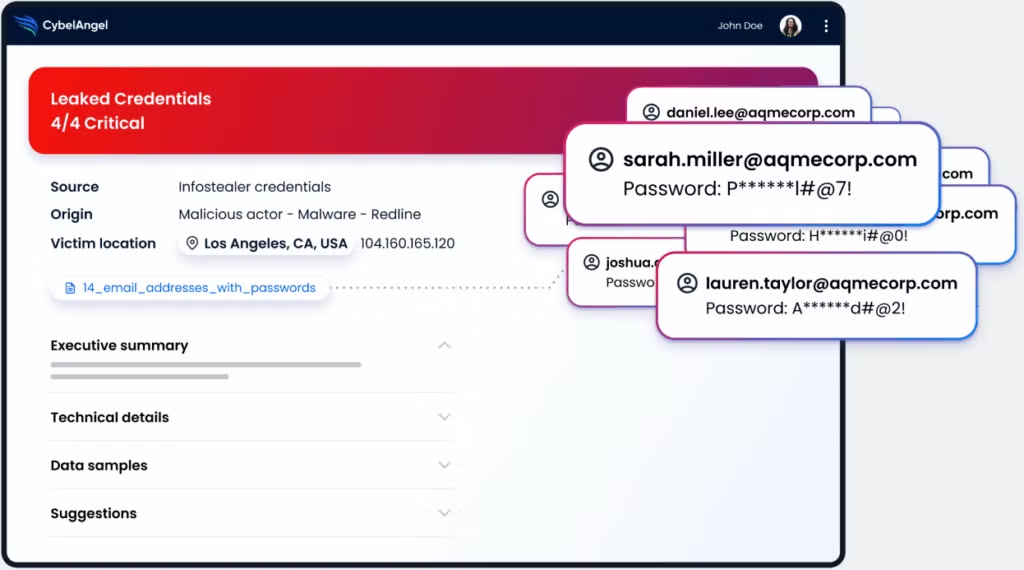
Credential-based access
Credential compromise remains the leading initial access vector, accounting for the majority of successful breaches. Unlike CVE vulnerabilities, these access vectors don’t have disclosure dates or patches. Exposed credentials remain valid until organizations detect and rotate them, often persisting for months or years.
CybelAngel’s credential monitoring specifically addresses this threat by detecting exposed credentials across surface, deep, and dark web sources before attackers weaponize them. We monitor breach databases and dark web forums for leaked employee credentials, scan code repositories for exposed API keys and passwords, and alert organizations to implement mandatory credential rotation upon detection.
Application-layer vulnerabilities
Common web application vulnerabilities often don’t receive individual CVE identifiers but remain widely exploitable. SQL injection remains prevalent in custom web applications and legacy systems. Cross-site scripting (XSS) enables session hijacking and credential theft. API vulnerabilities expose endpoints with insufficient access controls.
AI-enhanced scanning tools identify these vulnerabilities by analyzing application behavior, testing input validation, and probing authentication mechanisms. Organizations face continuous reconnaissance against custom applications that automated vulnerability scanners and CVE databases don’t address.
The time-to-detect gap
For non-CVE vulnerabilities, the relevant metric isn’t Time to Exploit, it’s Time to Detect. Organizations often remain unaware of exposed databases containing sensitive data, leaked credentials circulating in criminal forums, misconfigured cloud services accessible to anyone, and shadow IT assets outside security visibility.
This detection gap can persist for months or years, providing attackers with persistent access opportunities that dwarf the 5-day CVE exploitation window. CybelAngel’s platform specifically addresses this gap by monitoring organizations’ complete digital footprints for exposed assets, leaked data, and configuration vulnerabilities.
What do European regulations require?
European cybersecurity regulations have evolved to address both CVE vulnerabilities and broader security exposures. The NIS2 Directive requires organizations to address critical vulnerabilities “without undue delay” and establishes three-phase incident reporting: early warning within 24 hours, detailed notification within 72 hours, and final reports within one month.
The Cyber Resilience Act entered force in December 2024, with reporting obligations beginning September 2026. It mandates faster response for actively exploited vulnerabilities and addresses secure configuration defaults, minimizing attack surface, and protecting against common exploitation techniques including both CVE and non-CVE attack vectors.
France’s Military Programming Law (LPM) 2024-2030 goes further, requiring all software publishers to report significant vulnerabilities to ANSSI.ANSSI’s guidance emphasizes configuration hardening, access control, and credential management, recognizing that security extends beyond CVE patching.
Given the 5-day average TTE and 32.1% negative TTE scenarios, organizations need 24-72 hour emergency response capabilities for actively exploited CVE vulnerabilities, while simultaneously maintaining continuous monitoring for exposed credentials, misconfigurations, and data leaks.
What should organizations do now?
The collapsed TTE timeline and persistent non-CVE exposures demand comprehensive security strategies.
Implement continuous threat exposure management
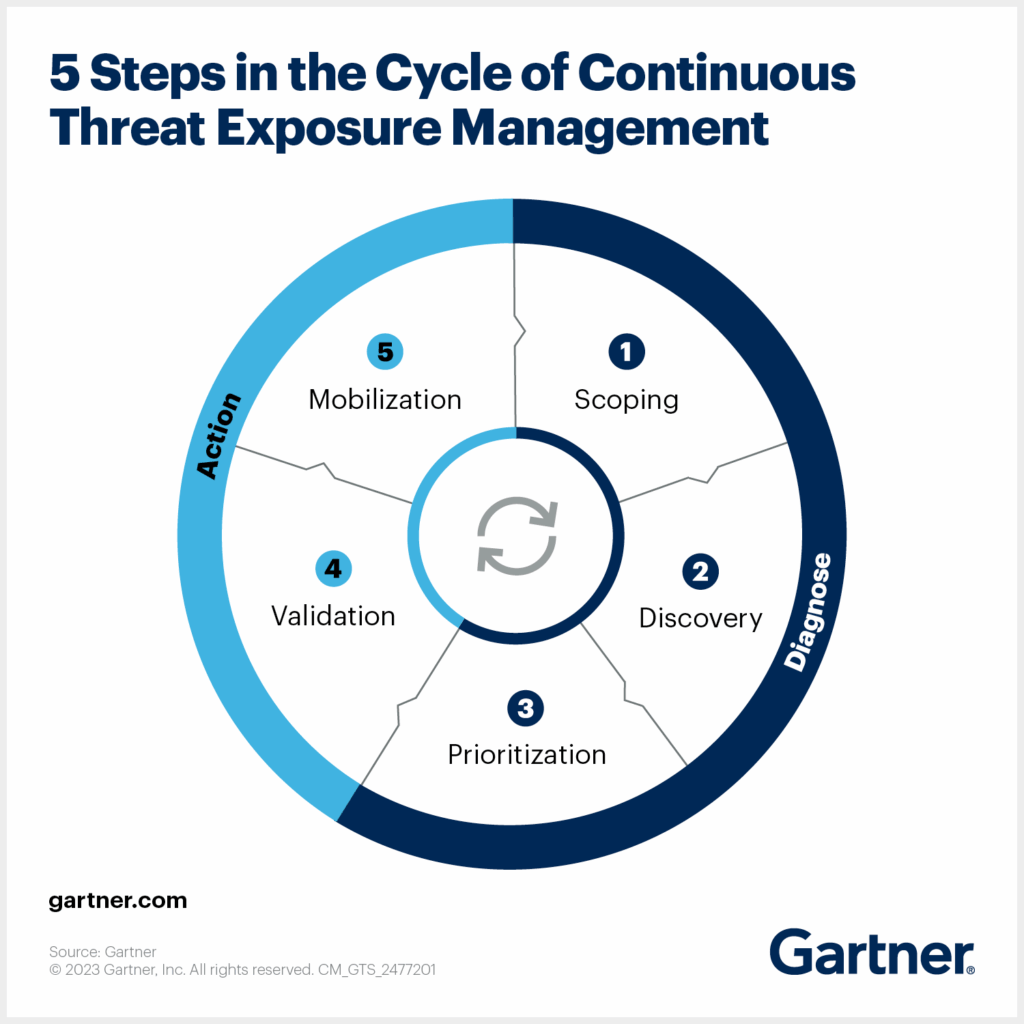
Continuous Threat Exposure Management (CTEM) must replace periodic assessments. With over 40,000 CVEs published annually, organizations must focus on the less than 1% that drive actual breaches, using CISA’s Known Exploited Vulnerabilities catalog and EPSS scoring.
Simultaneously, CTEM must extend beyond CVE tracking to monitor exposed cloud storage and databases, leaked credentials and API keys, misconfigured services and shadow IT, and exposed sensitive data across web sources.
Deploy Zero Trust architecture
When a third of vulnerabilities are exploited before patches exist, prevention alone cannot suffice. Microsegmentation, least-privilege access, and “assume breach” postures limit damage when exploitation inevitably occurs. Zero Trust particularly addresses non-CVE threats by requiring authentication for every access request, limiting lateral movement after credential compromise, and reducing blast radius from misconfigured services.
Monitor your complete digital footprint
Organizations must gain visibility into their entire attack surface, including assets that may never appear in CVE databases. CybelAngel’s platform provides continuous monitoring across surface, deep, and dark web sources, detecting exposures that traditional vulnerability scanners miss. This includes credential leak detection, exposed database monitoring, and misconfiguration alerts.
Reduce attack surface
Attack surface reduction provides the most sustainable defense. Disable internet-exposed management interfaces, harden VPN and firewall configurations, remove legacy systems and unused services, implement secure configuration baselines, and regularly audit cloud service permissions. Our attack surface management services help organizations identify and reduce these exposures.
Enhance detection and response
Detection and response capabilities compensate for inevitable prevention failures. Deploy EDR/XDR for rapid exploitation detection, implement behavioral analytics to identify zero-day patterns, maintain 24/7 SOC monitoring with threat intelligence integration, and establish anomaly detection for credential misuse.
When prevention fails, detection speed determines breach impact.
Can AI help defenders too?
Attackers weaponize AI to accelerate exploitation, but defenders gain equally powerful capabilities. Automated threat hunting at machine speed, anomaly detection across massive datasets, AI-enhanced SOAR platforms for rapid response,pattern recognition in exposed data across web sources, and automated analysis of configuration vulnerabilities enable security teams to operate at machine speed.
Defending against AI-enabled attacks requires email security with LLM-based content analysis,behavioral biometrics to detect deepfake attacks, Zero Trust policies limiting credential compromise damage, andanomaly detection for automated reconnaissance.
ANSSI’s AI security guidance provides European organizations practical frameworks for AI governance.
Wrapping up
Time to Exploit has collapsed from 63 days to 5 days over six years. One-third of CVE vulnerabilities are now exploited before patches exist. AI accelerates specific attack stages, particularly reconnaissance, phishing, and exploit generation, functioning as an efficiency multiplier amplifying existing trends.
However, the CVE-centric view tells only part of the story. The majority of successful breaches exploit persistent vulnerabilities that never receive CVE identifiers:misconfigured cloud services, leaked credentials,exposed databases, and authentication weaknesses. While organizations race to patch within the 5-day CVE exploitation window, attackers simultaneously exploit exposure gaps that persist for months or years.
Organizations that adapt, implementing 24-72 hour emergency patching, Zero Trust architectures, CTEM, attack surface reduction, continuous exposure monitoring, and AI-enhanced defenses. Stay ahead of threat intelligence services provide real-time monitoring of CVE exploitation, credential leaks, exposed infrastructure, and emerging attack patterns.

