How Have Infostealers Evolved in 2024?

Table of contents
In 2024, the world of infostealers is evolving beyond anything we could have imagined. From leveraging emerging technologies, to the exploitation of cryptocurrency data, cybercriminals are constantly innovating their infostealing malware to reach more victims, and have a longer-lasting impact.
In this blog, you’ll explore the 12 main ways that it’s changing in 2024. By staying ahead of the current trends, you’ll be better equipped to tackle each new cyber threat head-on.
Interested in our beginner’s guide to infostealers? Find everything you need to know over on this blog.
You’ll also discover what we can expect from infostealers in future years, along with 5 tried-and-tested best practices to stay one step ahead.
What are infostealers?
An infostealer, or information stealer, is a type of malware (malicious software) that “steals” sensitive information.
For example, infostealer malware extracts all the logs within your computer, as well as the document within it. Infostealer malware extracts:
- Login credentials: Including usernames and passwords
- Financial information: Such as credit cards, bank account details, and cryptocurrency wallets
- Personal data: Like social security numbers, passport details, or personally identifiable information (PII)
With access to sensitive data, cybercriminals can run fraud, account takeovers, sabotage, dark web sales, and more.
What’s the difference between infostealing and ransomware attacks?
An infostealing attack is done secretly to commit fraud or account takeovers, whereas a ransomware attack will encrypt the stolen data and demand a “ransom” payment to restore it.
Data that is then exfiltrated by infostealer malware (especially stolen credentials) is often sold in dark web marketplaces and purchased to launch ransomware attacks
How do infostealers actually work?
There are several different types of infostealer malware, including:
- Keyloggers: Record what’s typed on a keyboard to gather sensitive information
- Clipboard hijackers: Intercept the information you’re copying and pasting
- Browser stealers: Steal data from web browsers, such as saved logins and browsing history
- Form grabbers: Capture data from online forms, such as when you’re completing a shopping transaction






Now that you understand the basics of infostealing, and how it can exploit different vulnerabilities, let’s explore the main trends in 2024 to be aware of.
12 infostealer trends and takeaways for 2024
So, what’s the scope of infostealing in 2024? And what can we learn from it? Here’s an overview of the threat intelligence landscape for this year—and what you can do about it.
1. Anyone can use an infostealer tool
In 2024, anyone can purchase an infostealer malware. And it’s highly affordable, with pricing starting as low as $120 per month.
Infostealing is accessible to almost everyone, with malware-as-a-service (MaaS) tools available on the dark web, or via Telegram and Discord forums.
Plus, the technical knowledge required to use them is minimal, making infostealing malware one of the easiest tools for cybercriminals to use.
Takeaway: Information stealer malware has become more accessible, affordable, and user-friendly than ever.
2. Infostealers are using artificial intelligence, too
In the past year, 225,000 ChatGPT credentials have been found on the stealer logs market. And infostealing AI account details has increased by 36% in the past five months alone.
Artificial intelligence (AI) provides a unique opportunity for infostealer cyberattacks, because people often share sensitive information about their work and personal lives when interacting with the tool.
Takeaway: If infostealers can access someone’s ChatGPT account, then they can also access a whole host of personal data along with it.
3. Infostealer attacks are on the rise
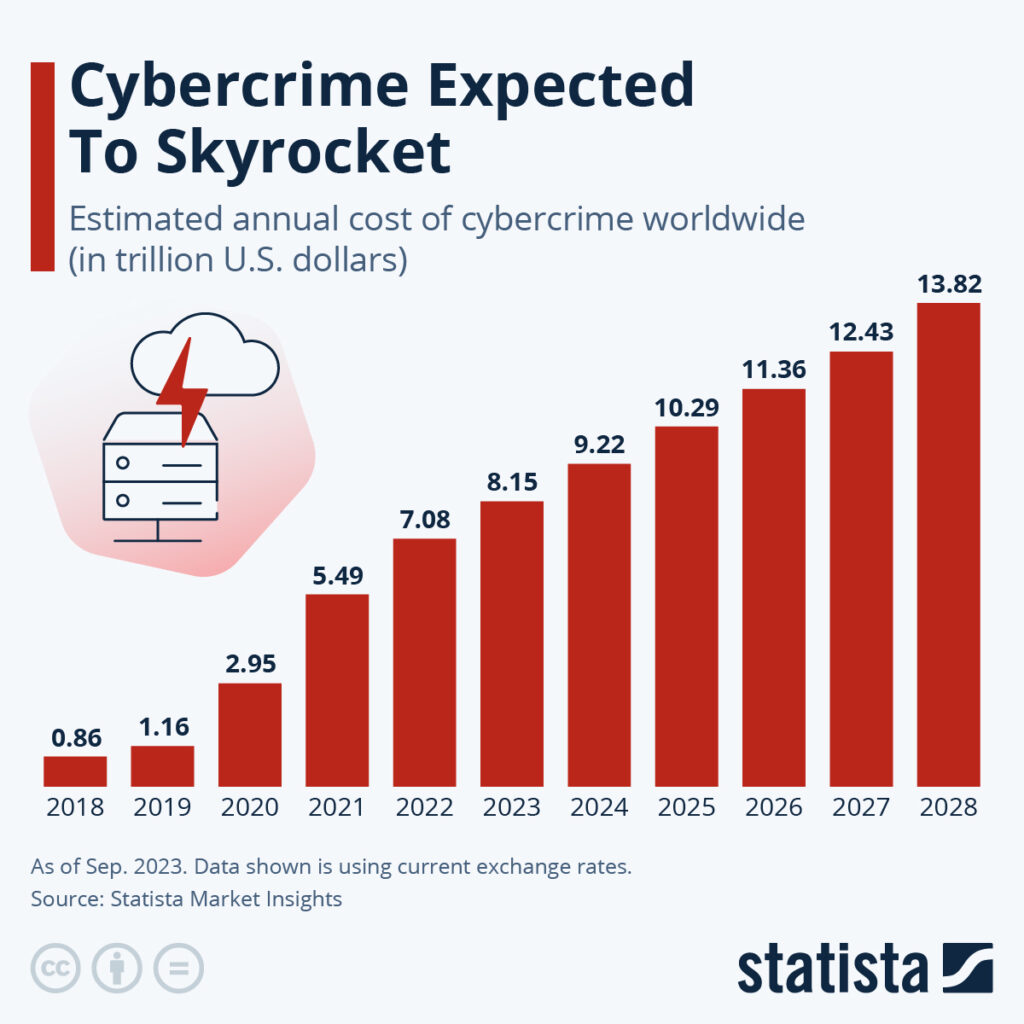
Infostealer infections have risen by 6000% since 2018. And these figures can only continue to skyrocket along with the global spread of cybercrime—of which the annual cost is expected to hit $10.29 trillion in 2025.
As the world becomes increasingly digitalized, there are even more vulnerabilities for cyber threat actors to exploit—and infostealing is no exception.
Takeaway: Infostealing is a rising cybersecurity threat, meaning it should be a top priority for every individual and organization.
4. There are new and emerging threat actors
There are lots of infostealing platforms out there, and plenty more stealers are being created every year.
Here are the variants that command and control most of the market:
- RedLine: A malware that steals saved credentials, autofill data and banking information
- Raccoon Stealer: A Russian password stealer and crypto stealer that targets autofill logs, cryptocurrency wallets, and more
- Vidar: A trojan malware that can steal sensitive information via a computer virus
There are also other emerging players including Rhadamanthys, LummaC2, META stealer , and StrelaStealer.
Malware innovation was particularly focused on infostealers over the past year, as cybercriminals experiment and search for the most efficient ways to exploit apps, endpoints, and operating systems.
Takeaway: Infostealers are constantly innovating and evolving, meaning that we need to regularly review our own cybersecurity and antivirus measures to stay ahead.
5. Private sales are happening on the dark web
The sale of stolen credentials increased by 150% on the dark web last year. Hidden online marketplaces are a major hotspot for purchasing stolen data, and the victims often don’t find out until it’s too late.
And even if companies do discover the sale of stealer logs, buying back the data is risky, as it could be infected with malware or a Trojan horse to further compromise the organization. Plus, there’s no guarantee that the stolen data will ever be completely removed from the dark web.
Takeaway: Organizations need to invest in dark web monitoring to be instantly aware of any leaked information about their company.
6. Third-party and supply chain risks are rising
This year, it’s estimated that 98% of companies are linked with a third party that has suffered a data breach (and 75% of these incidents are linked to cybercrime).
Even if you can avoid a data stealer, there’s no guarantee that your suppliers won’t fall victim to phishing emails, social engineering tactics, or a website stealer.
Takeaway: No matter how powerful your own cybersecurity functionality is, you’re only ever as strong as your weakest link. Cybercriminals can always infosteal from third parties and suppliers, instead.
7. The health and gaming industries are big targets
A 2023 study found that the healthcare industry suffers from 60% of all malware attacks—and most of these are via infostealers such as RedLine. These cyber attacks often leave additional malicious payloads which can wait months before taking effect, thus prolonging the incident response time and overall impact.
Infostealers also exploit the gaming industry, offering fake cheat codes and enhanced experiences to steal data. For example, in 2023, French gamers were invited to try a brand-new game via a Discord message, which was in fact an infostealer malware.
Takeaway: Due to their processing of extensive sensitive data, both the health and gaming industries are highly appealing to infostealer criminals.
8. Crypto wallets can be highly vulnerable
Speaking of gaming, a new infostealing malware called Realst has become a growing threat to both Windows and macOS users. It’s shared when people download fake blockchain games, and it can then steal access codes to their crypto wallets.
Cryptocurrency cybercrime can be a lucrative enterprise for infostealers, enabling them to target anyone’s finances through one simple malware download.
Takeaway: Crypto wallets are increasingly under threat from malware downloads across Microsoft Windows and macOS.
9. Social media can inspire infostealers
Any social media platform, from Facebook to LinkedIn, can be used by infostealers in stealthy ways. Infostealer malware will steal credentials related to your social media sites.
Here are just a few examples to be wary of.
- Social engineering: Infostealer malware will steal credentials related to your social media sites to create more convincing social engineering campaigns
- Data harvesting: Infostealers can review public profiles for information such as emails, phone numbers, location, and more
- Malicious links: Infostealers first compromise accounts and then encourage people to download or click on links leading to infect their systems with malware
- Phishing attacks: Infostealers access business pages and spread malicious malware as they trick people into interacting with them
Takeaway: Any information shared on social media can be used by infostealers, and they can equally mimic authentic-looking content to steal information, such as by impersonating brands.
10. MFA fatigue attacks are spurred on by infostealers
A multi-factor authentication/ MFA fatigue attack (also known as ‘MFA bombing’ or ‘MFA spamming’)has concrete ties to infostealer activity.
Infostealer malware is used to extract stolen credentials from machines, then those credentials are used to launch MFA attacks: If done persistently enough, the victim might eventually confirm the access via the notification, giving the infostealer access to their account permissions.
This is a form of social engineering, and it’s one way in which infostealers can get access to someone’s account.
Takeaway: Infostealers are highly creative in finding new methods to exploit their victims—and they’re also highly persistent.
11. One infostealer attack can open multiple vulnerabilities
A recent study found that one single attack from an infostealer can expose an average of 26 different business applications—compromising the wider digital ecosystem at an unprecedented scale.
This means that the potential consequences of an infostealing data breach can be catastrophic for any organization, exposing multiple endpoints and applications to further damage in the long run.
Takeaway: Infostealers can have lasting damage and expose multiple vulnerabilities, leading to long-term consequences that are difficult to recover from.
12. The Genesis Market Breach was a wakeup call
In 2023, the Genesis Market Breach brought together law enforcement teams from 16 countries to take down a stealer logs market with 80 million credentials.
Have you been targeted by criminals using #GenesisMarket ?
— National Crime Agency (NCA) (@NCA_UK) April 5, 2023
In the wake of an operation to take down the global online platform that sold stolen identities, people are being urged to check if they have been affected.
Find out how on our website ➡️ https://t.co/dBtnwpzwp7 pic.twitter.com/PTyLDOxbsR
This event marked a big step up for international law enforcement teams, headed by the FBI and the Dutch National Police, to fight back against infostealers. We can hope that this international collaboration will continue, as more agencies begin to recognize the threat of infostealing malware.
Takeaway: International authorities are increasingly working together to cmbat the growing dangers of infostealers.
The future of infostealers: What’s next?
As cybercriminals continue to develop their infostealing technology, we can expect to see more sophisticated malware over time. Innovation is happening all the time, and cybercrime is no exception.
Emerging technologies—such as AI—will continue to be exploited. Plus, these new systems can also be used to automate and optimize infostealing strategies—for example to create more convincing social engineering campaigns.
However, there has also been an increase in infostealer awareness. There have been several major international incidents, including the Genesis Market Breach, and we can only expect increased collaboration between security teams, tech firms, and CISOs over time to tackle the threat.
Additionally, people are investing more in cybersecurity measures, making it harder for malware to be deposited in their online systems. With stronger security functionality, infostealers won’t work as effectively, making them less attractive to cybercriminals.
How can I protect my company from infostealers?
There are five best practices for CISOs to keep their organizations safe from infostealing malware this year.
- Boost your cybersecurity measures: Adopt antivirus software, as well as external attack surface management (EASM) tools like CybelAngel to stop infostealers in their tracks.
- Educate your team: Make sure everyone understands the risks of infostealers, and recognizes common signs of an infostealing attack. Plus, encourage everyone to use MFA and strong passwords.
- Protect your data: Adopt strong data protection and encryption practices, and regularly monitor for any suspicious activity. Additionally, you should only collect necessary sensitive data, to minimize your attack surface.
- Monitor, monitor, monitor: Audit and monitor for any signs of infostealer behavior, and have a strong incident response plan ready to respond to it.
- Keep up to date: The infostealing world is constantly evolving, so you should, too. Collaborate with other experts, follow the latest developments, and follow the latest cyber threats to stay ahead of the infostealers.
By constantly monitoring and adapting your approach, you can protect your brand from infostealers, no matter how much they evolve in the coming years.
Interested in a demo? See our solution in action with an expert member of our team.
Conclusion
Infostealers are continuing to evolve and pose a growing threat to any organization. With the emergence of new technologies, and increasingly sophisticated cybercrime techniques, people are more vulnerable than ever to infostealing malware.
However, with the right tools and education, anyone can reduce their cyber risk. By staying ahead of the trends, proactively implementing strong cybersecurity measures, and keeping employees informed and vigilant, we can reduce the chances of infostealers gaining the upper hand.
And of course, with a little help from cybersecurity tools like CybelAngel, you can monitor your external attack surface on autopilot and enjoy peace of mind.