Lessons from the Postman Data Breach: API Security Gaps & Solutions

Table of contents
In December 2024, CloudSEK‘s TRIAD team discovered a critical security issue in the Postman API development and testing platform. Sensitive information, including API keys, access tokens, and refresh tokens, was leaked from 30,000 public workspaces.
The shocking discovery exposed businesses and professionals to significant risk, ruining Postman‘s reputation in the process.
How did this happen? Let‘s take a look at how the Postman data breach affected thousands of businesses worldwide and the impact on the industry at large.
What happened in the Postman data leak?
Postman emerged as a user-friendly tool for API testing and creation, used by 30 million organizations globally. The high use of Postman among developers made the discovery of critical vulnerabilities all the more distressing, increasing the risk of future attacks from threat actors.
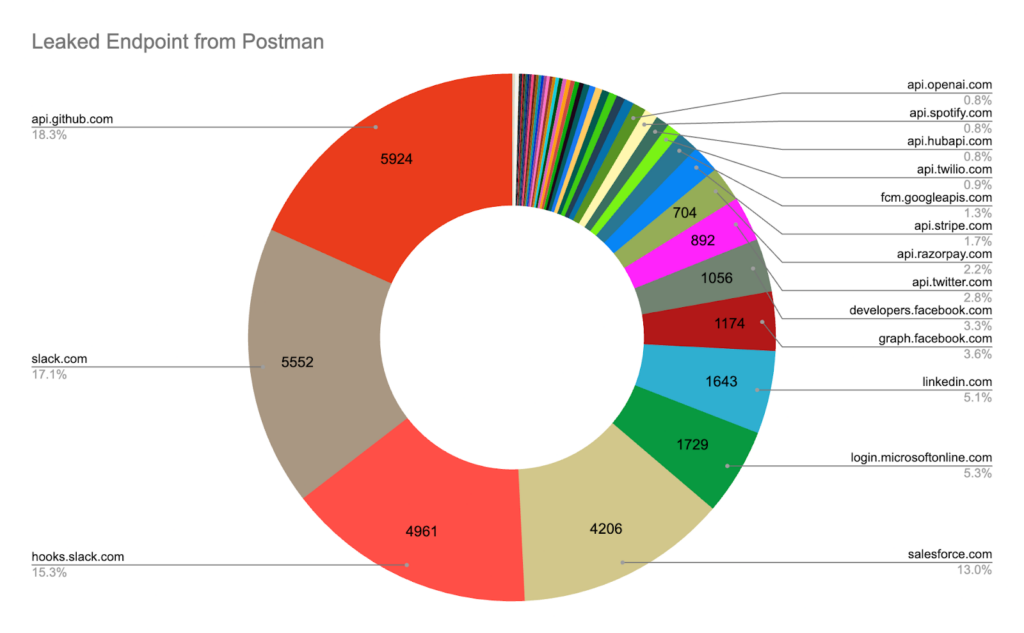
Postman data breach in numbers…
- 18% of leaked API endpoints were connected to GitHub.
- E-commerce and payment systems contributed to 3.9% of all endpoint leaks.
- Dropbox API endpoints made up 7% of the total leaks.
The Postman data breach highlights how sensitive data can be accessed and spread, even on notable, reliable platforms.
What are Postman’s built-in security gaps?
Postman is a platform designed to make collaboration easy and effective. Unfortunately, this also meant that security practices could be lacking. Content on Postman.com can be publicly accessible depending on how users configure visibility settings – and that’s where sensitive data can leak due to developer’s carelessness or lack of knowledge.
Here are the root causes of the Postman data breach, as identified by CloudSEK:
- Accidental sharing of collections and environments: Postman’s focus on collaboration led to sensitive data being shared indiscriminately, increasing unauthorized access risks.
- Misconfigured access controls: Workspaces were often set to “public” instead of “private,” exposing data to search engines and external users.
- Syncing with public repositories: Collections synced with platforms like GitHub without masking or sanitizing threatened to expose sensitive data to anyone with access to the repository.
- Storing sensitive data in plain text: Postman, by default, saved sensitive data in a plain text format without any encryption, allowing anyone with access to the workspace to view potentially sensitive data.
- Minimal secrets management: Many users chose not to utilize Postman’s secret management tools, putting sensitive data at risk.
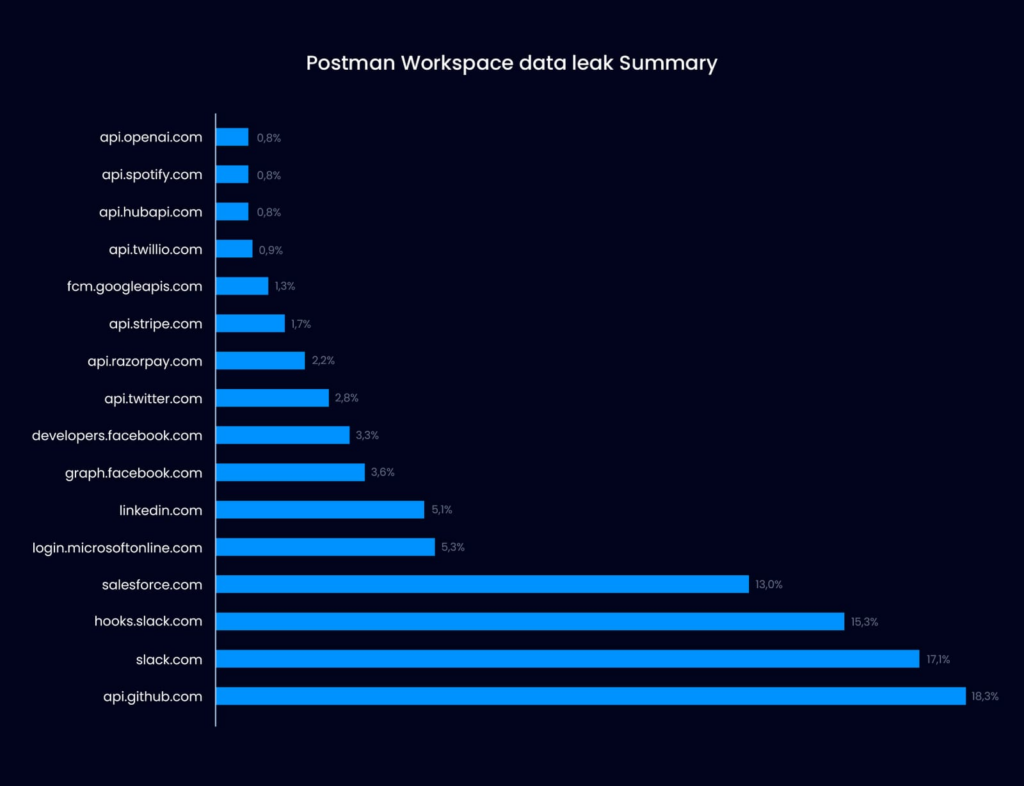
A bar graph showing the public repositories affected most by Postman‘s data leak. Source.
Why are Postman workspaces a growing attack vector?
The insecure practices used by Postman without security guardrails led to sensitive data exposure, giving attackers a window into the compromised organization.
Here‘s how attacks can utilize different vulnerabilities to cause damage:
- Leveraging exposed API keys: Attackers can leverage exposed API keys in Postman to access and exfiltrate sensitive data.
- Taking control of exposed API tokens: Threat actors can gain control of leaked tokens by generating their own API requests to gain access to internal systems and escalate issues quickly.
- Impersonating users with leaked credentials: Attackers can impersonate legitimate users with stolen credentials such as usernames and passwords.
- Stealing confidential business secrets: Cybercriminals can exfiltrate confidential trade secrets and potentially sell this data to competitors.
How did attackers exploit exposed Postman data?
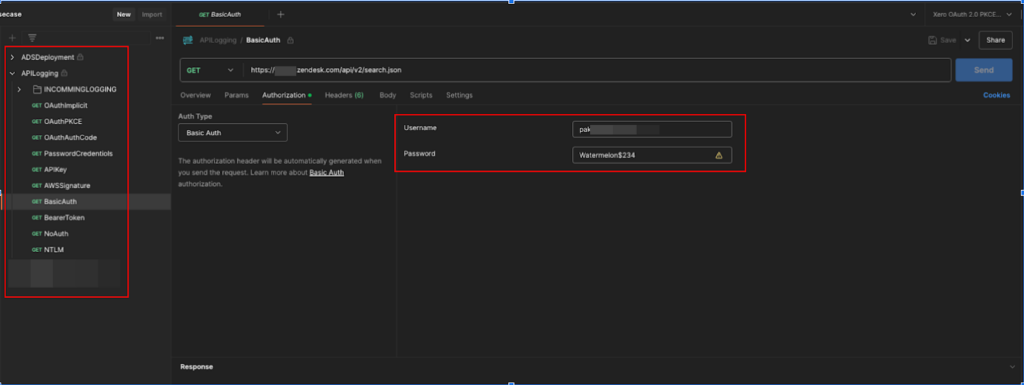
When healthcare customer records were leaked
The Postman data breach exposed sensitive healthcare customer records due to misconfigured workspaces. Active Zendesk admin credentials were leaked, opening the potential for threat actors to cause harm to the healthcare company and the wider public.
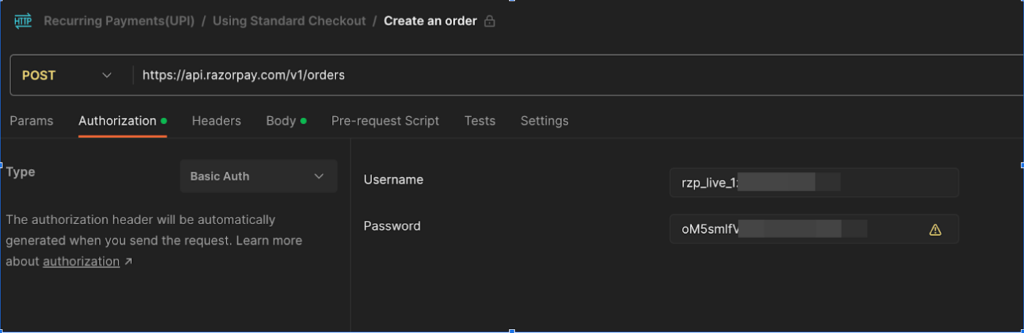
Razorpay API credentials were breached
Razorpay, an online payment platform, had many API keys accidentally leaked from publicaly shared Postman workspaces.
The API keys were designed to securely connect to Razorpay from Postman, but they were left unprotected and vulnerable to threat actors. Data such as Razorpay usernames and passwords were leaked, leaving the door open to financial fraud or misuse of company payment systems.
A major CRM software company had their refresh token exposed
A popular CRM platform had its refresh tokens and session secrets exposed, as well as API endpoints, so threat actors could generate their own access tokens.
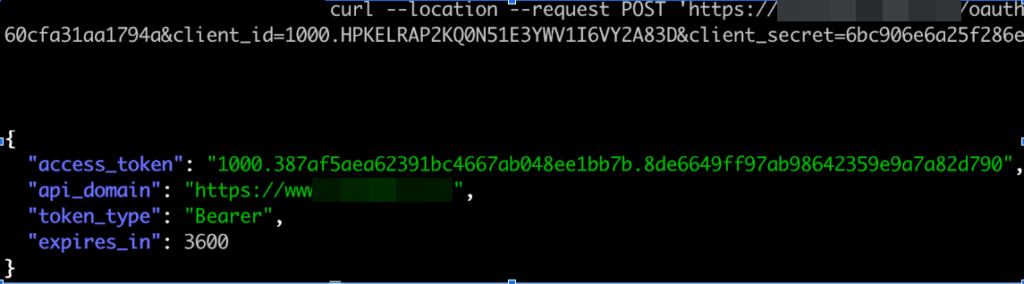
Unauthorized users could now hijack user sessions to directly access systems. From there, attackers can access customer data and other insights to extort funds from organizations.
In one example, researchers found API keys had provided full administrative access to critical cloud resources. Attackers can use this access to deploy malicious code, exfiltrate sensitive data, or disrupt services.
New Relic API credentials were disclosed
New Relic, a real-time analytics platform, was often used by Postman users to monitor and log APIs. During the Postman data leak, API keys to New Relic were also exposed, which could potentially give threat actors access to system and application logs, product usage data, network traffic data, and user credentials.
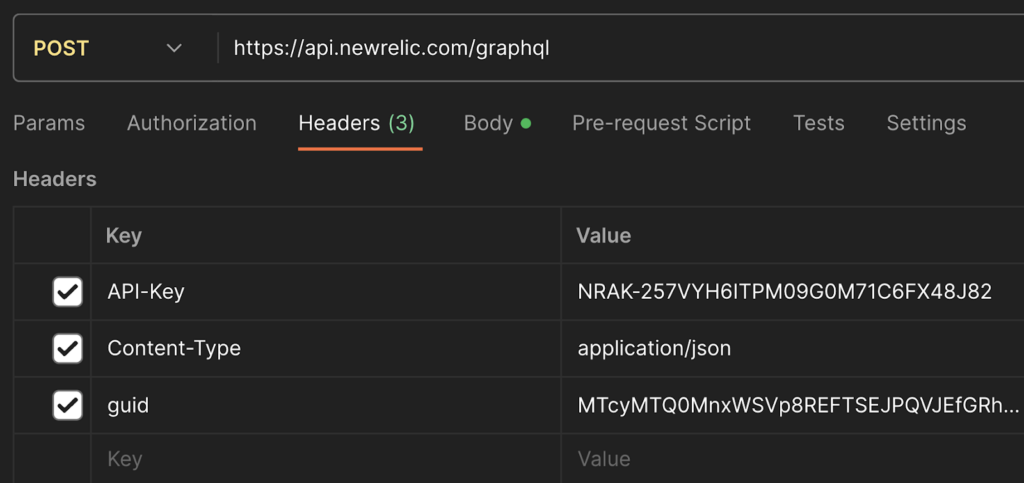
The data can expose internal ICT infrastructure to enable threat actors to gain unauthorized access and perform intricate attacks.
How could a Postman data breach affect your business?
What are the consequences of poor security?
Here are just some of the risks associated with a breach at any scale.
- Hindering business operations: Organizations lose time managing the fallout of the incident, leading to a loss in productivity.
- Reputational damage: Organizations risk losing clients and partners in the event of a data leak.
- Financial losses: Attacks can utilize vulnerabilities to extort funds, deploy ransomware or malware, and damage internal systems, leading to lost revenue.
- Increased phishing and social engineering attacks: Attackers can leverage the legitimate information they have acquired to infiltrate deeper into the organization through phishing and social engineering attacks.
Preventing data breaches in 2025
A security first mindset means focusing on preventative measures, and continuous monitoring.
Here‘s how you can prevent Postman leaks:
- Restrict permissions: Share collections and environments only with those who truly need access. Regularly review permissions and steer clear of organization-wide sharing for sensitive environments.
- Minimize use of long-lived tokens: Opt for short-lived tokens whenever possible and implement automated token rotation, reducing the risk if a token is exposed.
- Review before sharing: Before sharing any collection or environment, carefully check for sensitive information stored in variables or requests.
- Leverage external secrets management: Use dedicated secrets management tools to store and retrieve sensitive information securely to reduce the risk of exposure.
- Audit and monitor access: Utilize Postman’s activity logs to track sharing and access. Regular audits can help identify who has access to sensitive data and detect suspicious activity before it causes damage.
Since the attack, secret scanning for Postman has been implemented to help users better track any exposed data, however, only public workspaces are scanned, leaving private spaces at risk if attackers already have access.
How can CybelAngel’s new feature solve this?
Misconfigured workspaces can have devastating effects on an organization.
Cybel Angel automatically monitors Postman daily, detecting leaks before they become breaches.
Misconfigured workspaces can have devastating effects on an organization—not just because they expose internal projects and data, but also because they often contain sensitive credentials like usernames and passwords, or API keys and tokens, stored in plaintext or shared inadvertently.
In platforms like Postman, such misconfigurations have led to thousands of public workspaces leaking credentials, giving attackers the opportunity to access critical systems, exfiltrate sensitive data, or even perform unauthorized transactions.
CybelAngel’s External Threat Intelligence platform is designed to address Postman-related risks with built-in capabilities to prevent Postman-related threats. Additionally, CERT-ready incident reports provide detailed, actionable intelligence on breaches, allowing you to respond before attackers can cause harm.
Book a demo to learn more.

