Cyber Attack Wipes Out Over 30% of Unsecured Databases
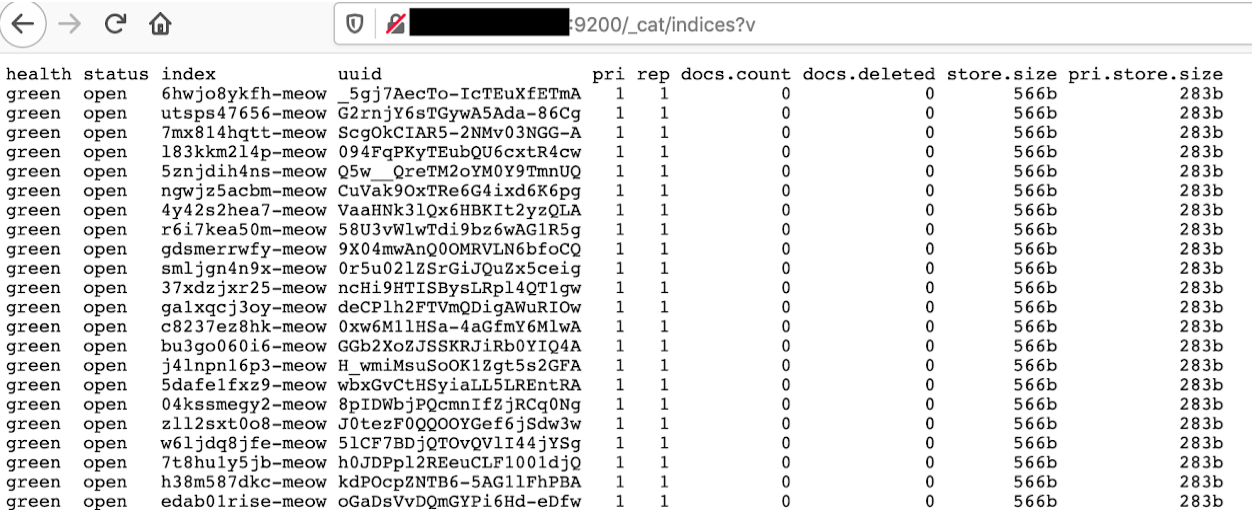
Table of contents
In a cyber threat landscape largely governed by profit incentives, a newcomer known as “Meow” has been targeting unsecured databases, erasing all the data without leaving any kind of ransom note or demand. Since the discovery of this automated attack in mid-July 2020, speculations about the nature of the attacker and its underlying motivations are seemingly legendary. Behind this harmless nickname lies a destructive bot seemingly running automated scripts to attack its preys, databases lacking security access controls, replacing their indexes by new and empty ones renamed with a random string followed by the word “meow.” The first cyber attack, that targeted an unsecured ElasticSearch database containing personal data from users of UFO VPN, was uncovered by cybersecurity researcher Bob Diachenko on July 20, 2020. It did not take long before other victims surfaced, such as Zimbabwe’s leading online payment platform, Paynow, or a medical software company, Adit. In the latter case, 3.1 million patients’ records exposed on an unprotected database were destroyed by the Meow bot. Public actors don’t seem to be spared either: on July 25th, Bob Diachenko revealed that the Argentinian Ministry of Public Health had an ElasticSearch cluster storing personally identifiable information from 115,000 Covid-19 circulation permits applicants infiltrated by the Meow bot, although the data was apparently left intact. 
One example of an ElasticSearch server targeted by Meow: all indexes renamed and emptied from their content
While most specialized cybersecurity information websites stated a figure of approximately 4,000 targeted databases at the end of July 2020, a new search on Shodan suggests this number could now be as high as 20,000. According to CybelAngel data, 22,311 of 57,771 unprotected databases detected appear to have been hit between July 20th and August 18th, with the majority of affected servers located in China (9,672 hits) and the United-States (3,779 hits), unsurprisingly the countries of the leading cloud services providers. 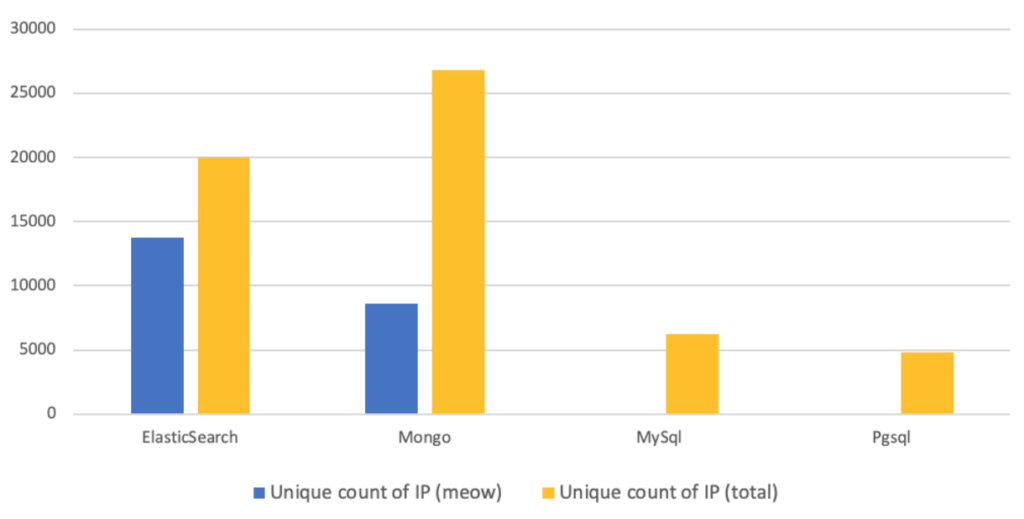
Repartition of Meow attacks by protocol between July 20th and August 18th (proprietary CybelAngel data)
As the chart presented above illustrates, ElasticSearch clusters clearly appear to be the primary target, accounting for a majority of the impacted databases. Together with MongoDB, they accounted for 97% of the servers hit by the Meow bot as of July 25th, according to BleepingComputer. These figures may seem surprising, but they probably reflect the sheer number of vulnerable ElasticSearch servers compared to other types of databases, considering the ease of access to the ones that do not require any authentication. In theory, an individual willing to connect to such a database would only need to know its IP address and use a search engine, without having to possess specific skills. In June 2020, CybelAngel published a white paper revealing that ElasticSearch misconfigurations accounted for 30% of all records exposed, and that the number of breaches caused by Elasticsearch misconfigurations had nearly tripled from 2018 to 2019. It’s not the first time that unprotected ElasticSearch servers are targeted by a large-scale offensive: in early April 2020, ZDNet revealed that a hacker had used an automated script to wipe and deface more than 15,000 servers from the database management system, while trying to divert the blame on a cyber-security firm, Night Lion Security. Interestingly, the modus operandi appeared to follow a similar pattern to Meow attacks. In May 2020, our analyst team was able to identify a single hacker group, dubbed Superflow, who was allegedly deleting records from unsecured ElasticSearch databases and leaving a “readme” index containing a ransom demand. 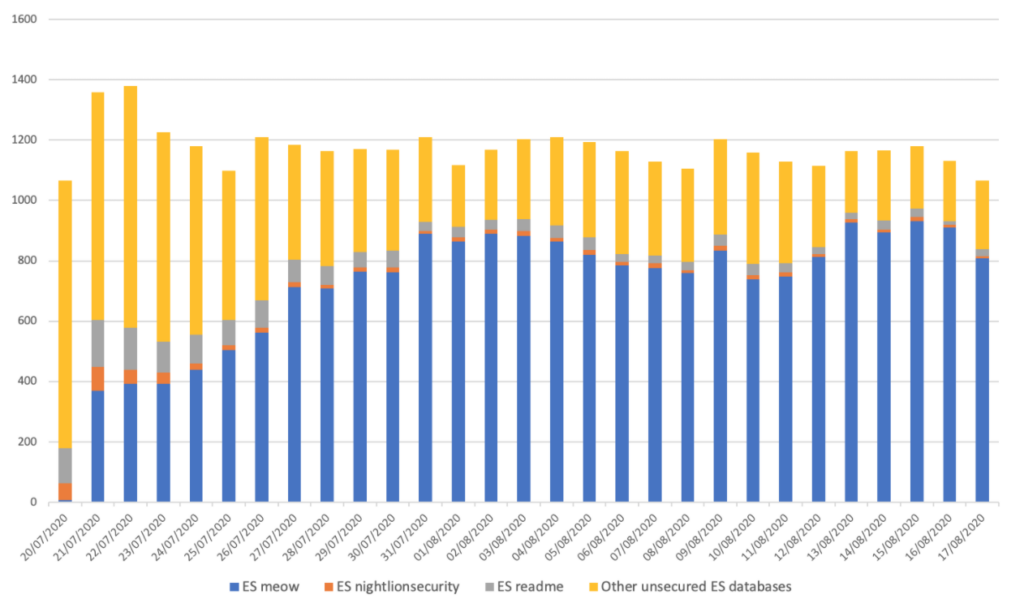
Evolution of ElasticSearch databases targeted by Meow over time compared to other types of attacks (CybelAngel data)
The main interrogation revolves around the motives behind such a cyber attack. There is no evidence that the data is even copied before being removed, which almost certainly excludes the assumption of an extortion attempt. There is little probability that these attacks are orchestrated by a benevolent individual, deleting sensitive data to protect it from being exposed. However, it is much more likely that they are the work of a grey hat hacker trying to raise awareness about the risks of data leaks involving unprotected databases. Meow could also be a way for a new threat actor to gain visibility before moving towards a profit-driven doctrine, but no clues enabling to identify the attacker have been found at this point, which practically excludes this conjecture. Even if its motivations are still unclear, this new threat highlights a critical vulnerability in databases’ security configuration, allowing malicious actors to exploit this breach with ease – especially as regards ElasticSearch servers – and industrialize the process to launch large-scale campaigns of data compromise. In this high-risk and time-critical environment, it is crucial for a business actor to be able to detect unsecured databases exposing confidential information in a prompt and comprehensive way, so that potential vulnerabilities can be addressed, and data leaks avoided. At CybelAngel, we offer our clients extensive coverage on the most commonly used database systems, such as ElasticSearch, MongoDB or MySQL. We consider it a priority to notify impacted clients in a timely fashion; thus, we rely on continually improved scanning tools to detect unsecured databases with very few latency, as well as our cyber analyst team who qualify potential risks of data exposure.