From Reveton to Maze: Tracing the Evolution of Ransomware

Table of contents
Ransomware is experiencing rapid growth as a cyber attack — impacting private individuals to cities, from enterprises to non-profit organizations to government agencies. To appreciate where ransomware is going, it is imperative to understand the ransomware story from Reveton to Maze. This ongoing ransomware trend began in the 2013-2014 timeframe and appears to be escalating — if not in number, then in damage to its victims. Organizations affected by these attacks can lose tens of million dollars in recovering from the attack or choose to pay a few millions in ransom for their data. According to CybelAngel’s investigation, CWT (formerly known as Carlson Wagonlit Travel) paid $4.5 million to recover some 2TB of data stolen by Ragnar Locker. While the cities of Baltimore and Atlanta did not pay the demanded ransom, the cities reported the recovery from their ransomware attacks were $18.2 million and $17 million respectively.
What is ransomware?
Ransomware is malicious computer software that takes data hostage. It encrypts and blocks the files on your computer and asks for ransom in exchange for a key to decrypt them. Very often, ransomware infiltrates in the form of a computer worm, through a file downloaded or received by email and encrypts the victim’s data and files. The aim is to extort a sum of money to be paid generally by virtual currency to avoid any trace. The concept of ransomware has existed since the 1990s. However it wasn’t until 2012 when the first major “public” attack made front-page news using the name Reveton (aka the Police ransomware). Reveton infected computers and locked its data. The ransom demand was disguised as a law enforcement message, demanding a “fine” be paid before the data would be unlocked. By 2014 the first crypto-ransomware arrived under the name Cryptolocker, and there was an explosion of worldwide attacks, including WannaCry and Petya. What we now call “ransomware” is short for crypto-ransomware because ransomware needs a cryptolocker to encrypt data and lock the devices. 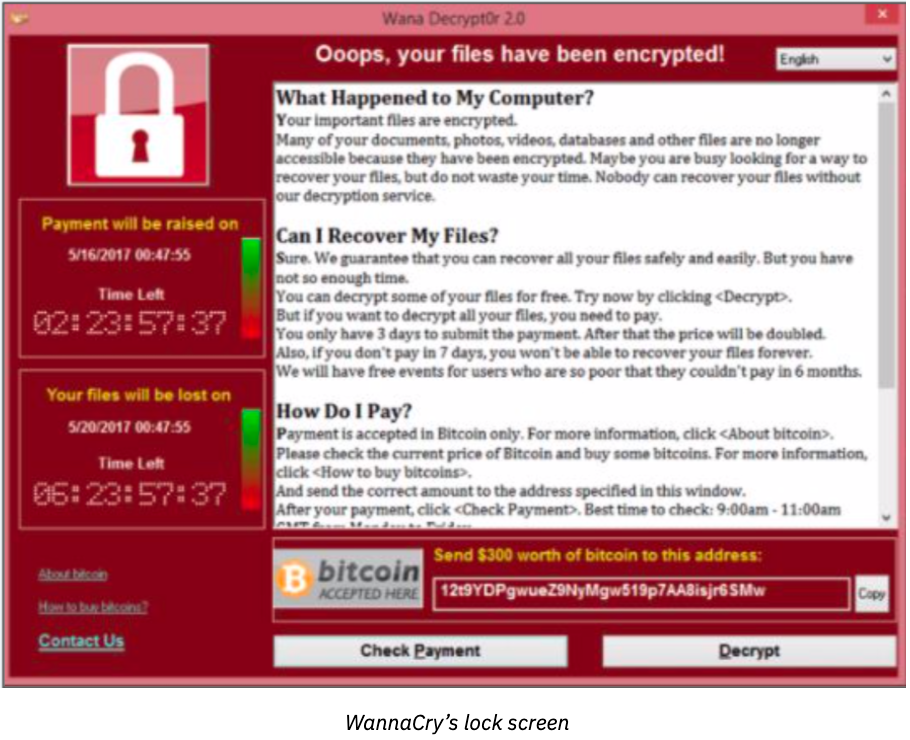
Latest Ransomware trends
Today, advanced piracy collectives are investing in innovation. Ransomware gangs are evolving to more accurately target and extract larger ransoms from their victims. These gangs increase pressure on their targets while increasing the ransom demand by launching websites to shame their victims and threaten to release all or part of the stolen data. In this scenario, companies may suffer from a loss of competitive business intelligence, legal prosecution from third parties, or the ruination of their brand. Some of the most notorious and innovative gangs include: Maze, REvil (Sodinokibi), Netwalkers, Doppelpaymer, among others. 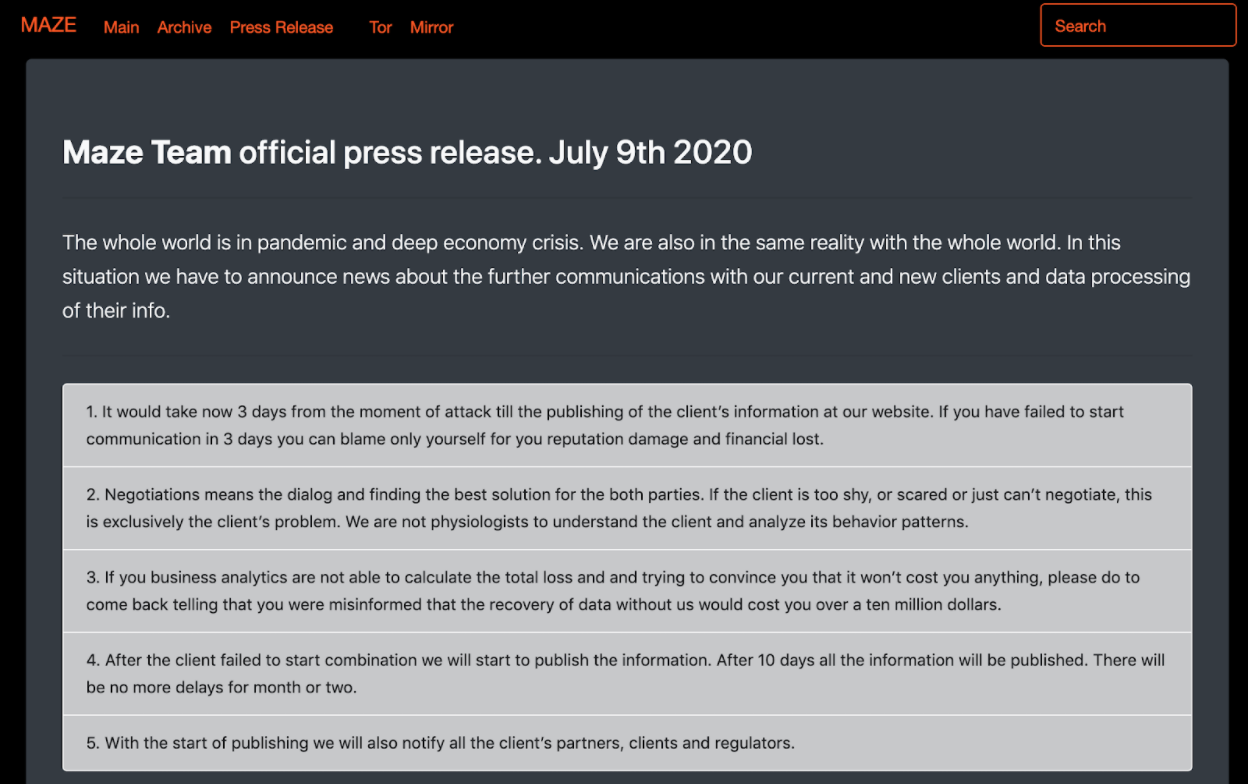 Some examples and gang signatures include:
Some examples and gang signatures include:
- Nefilim uses the live countdown for the release of the documents.
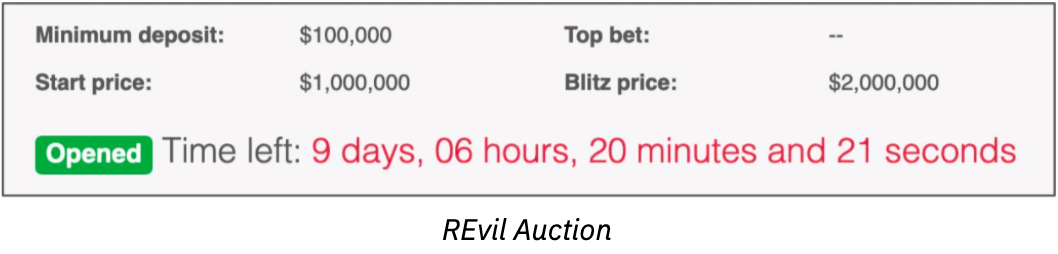
- REvil threatens to auction the data to coerce additional payment from their victims.
- Partnerships between ransomware gangs, such as Ragnar and Lockbit with Maze, have given rise to complex schemes to exploit documents from Victim A to attack Victim B.
 Lastly and perhaps the most worrisome trend is the move to Ransomware-as-a-Service or RaaS. By hosting the ransomware software, cyber criminals have now made ransomware tools available to bad actors who don’t need development skills to ransom people or companies. They simply use the RaaS, and the developer/provider takes a commission on the ransom. From proof of concept to international looting, ransomware gangs are in a cycle of perpetual evolution; therefore we can expect newer methods and improvements along the next few months. And the fact that some of them make millions of dollars within a few months is certainly not going to lower the trend.
Lastly and perhaps the most worrisome trend is the move to Ransomware-as-a-Service or RaaS. By hosting the ransomware software, cyber criminals have now made ransomware tools available to bad actors who don’t need development skills to ransom people or companies. They simply use the RaaS, and the developer/provider takes a commission on the ransom. From proof of concept to international looting, ransomware gangs are in a cycle of perpetual evolution; therefore we can expect newer methods and improvements along the next few months. And the fact that some of them make millions of dollars within a few months is certainly not going to lower the trend.