The Cyber Kill Chain Explainer Guide

Table of contents
In this in-depth guide on the Cyber Kill Chain, we share a basic overview of this model, the 7 phases of APT intrusions, and its framework goals We’ll also share a basic overview of how cybersecurity professionals can better analyze and understand cyber intrusions.
But first, let’s look at some context for the cyber kill chain model.
An overview of the Cyber Kill Chain and its drawbacks
The Cyber Kill Chain was a model developed by researchers at Lockheed Martin, a global security, defense and aerospace contractor. This early model categorized seven stages of targeted cyber attacks and shared recommendations for “Intelligence-Driven Computer Network Defense.”
This defense model is based on the military concept of the “Kill Chain” which uses phase-based models to describe different types of attacks to identify capability gaps and prioritize their fulfillment.
The Cyber Kill Chain addresses Advanced Persistent Threat (APT) intrusions, which are more sophisticated and difficult to prevent than familiar automated viruses.
Organizations protect themselves using automated solutions like antivirus apps and firewalls. However, these solutions are less effective against APT campaigns. APT threats are more stealthy than other cyber attacks such as ransomware campaigns.
What are the main objectives in an APT campaign?
The main objective in an APT campaign is to gain command and control to a targeted network and remain undetected while exfiltrating sensitive data over a long period of time.
Let’s look at a recent example of this in action:
During the period 2023-2024, APT41, a Chinese espionage group conducted prolonged cyber attacks across multiple sectors in countries including Italy, Spain, and the UK, targeting the technology and automotive industries. During the stages of a cyberattack they commonly use tactics like DLL sideloading and deploy advanced malware such as Dustpan and Dusttrap. They maintain access and exfiltrate sensitive data through tools from PineGrove to Microsoft OneDrive.
Their operations, characterized by minimal traces and long-term network persistence, exemplify a sophisticated execution of the cyber kill chain that leads to huge data loss for the intended victims.
Why does this mean for associated security measures?
The good news — there continues to be a decreasing global median for APT dwell time (i.e., the time an APT actor stays on a network). According to the latest Mandiant M-Trends report, the global attacker median dwell time has reached its lowest point in over a decade. In 2023, organizations detected intrusions within a median of 10 days, a significant decrease from 16 days in 2022.
The bad news is that despite a significant decrease in APT dwell time, APT actors often remain undetected for long periods in their target’s network, causing chaos as they access sensitive information. Hackers are constantly evolving their impact during this period of unauthorized access.
Can automated solutions thwart APT?
APT campaigns bypass the most common cyber defense mechanisms implemented by organizations. By mixing “simple” techniques with advanced techniques and tools, APT actors make their campaigns difficult to detect and tackle using only automated solutions. The Cyber Kill Chain provides analysts with a framework that allows them to:
- Retrace the steps of a detected attempted intrusion
- Identify the gaps exploited by attackers
Analysts can then mitigate those gaps to be better prepared to face intrusions using the same techniques.
What are the 7 phases of APT intrusions in the kill chain framework?
There are seven common phases of APT intrusions:
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command & Control
- Action & Objectives.
Let’s examine these in more detail from an information security standpoint.
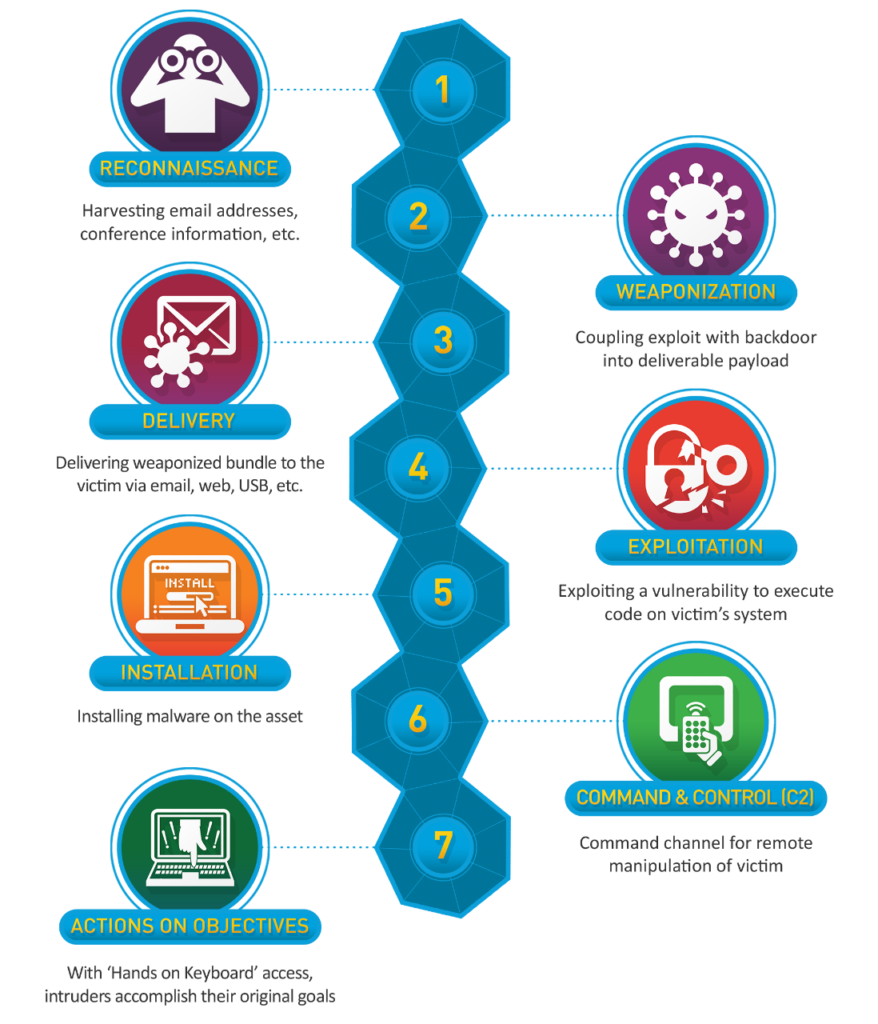
Step 1: Reconnaissance Phase
In this first step, cybercriminals gather as much information as possible on their target, using various tools and methods. Attackers may use active and passive reconnaissance to gather data on the target’s network (e.g.: exposed devices, used OS, versions), plus identify the level of exposure. For instance, are there readily available credentials or information related to employees?
The goal
Attackers aim to select the target’s weakest entry points to enter the target’s system.
Step 2: Weaponization
Attackers craft a specific tool based on the evidence they’ve assembled during the reconnaissance phase and from knowledge of known vulnerabilities.
Attackers often use malware (commonly a Remote Access Trojan, or RAT, with other programs for the exploitation phase) coupled with a deliverable payload, such as an infected document (PDF, PPT or Excel file).
However, depending on the delivery method, weaponization can take many other forms, such as exploit kits. In this case, attackers do not hide malware in a seemingly legitimate file and trick their target into downloading it.
Instead the target is encouraged to visit an infected website, which could result in the “drive-by download” of malware or a vulnerable host targeted directly by attackers. See more on exploit kits here.
The goal
Overall, the weaponization phase is about how the attackers tailor their malware to the target in order to hide malicious content. There can be several “levels” of weaponization and several malicious programs used to reach their intended goal.
Step 3: Delivery
Things get more serious from this point on, as this stage of an attack enters into an “active” phase. This phase refers to the delivery of the tool crafted in the previous phase, which can take many forms.
For instance, if attackers found relevant credentials or unprotected devices on their target’s network, they could remotely access and compromise the devices with their malware. Other delivery methods include compelling an employee to share access credentials and exploiting vulnerabilities to access security controls (Over the past 10 years, the use of stolen credentials has appeared in almost one-third (31%) of all security breaches)
The goal
Hackers aim to send infected files or links, for example, through well-crafted phishing emails that use social engineering techniques, to access your personal data and credentials to do further harm.
Step 4: Exploitation
Once the weapon is delivered to the target, the exploitation phase can begin.
Malware commonly targets vulnerabilities in applications or Operating Systems (OS), whether known (Common Vulnerabilities and Exposures, or CVEs), or unknown zero-day vulnerabilities (those that have not yet been spotted and patched by the provider of the exploited instance).
The goal
The goal is to spread malicious code in the network, privilege escalation, or anything else required by attackers to prepare for complete intrusion in real time.
Step 5: Installation
As mentioned previously, APTs are often about information exfiltration over a long period of time. In the installation phase, the attackers try to “install” themselves on the network and maintain persistence, frequently using RATs and backdoors.
The goal
Cybercriminals aim to deploy multiple tools to provide redundancy, should one of their access points be discovered.
Step 6: Command and Control (C2)
Once the attackers are “installed” in the network, a C2 server is implemented to create a channel between the compromised hosts and the malicious actors. This C2 server can be used by the intruders to directly interact with their target.
The goal
It is quite simple in this step, it is to be exfiltrate sensitive information or inject new malware.
Step 7: Action on Objectives
Once all the previous steps are completed, APTs finally begin to work on their initial objectives.
The phased approach is supported by the hypothesis that if a defender is able to detect and document one of the steps used in an APT attack, a similar intrusion will ultimately fail.
The goal
This may involve data exfiltration, remaining in stealth until a specific time, installing malware intended to disable or destroy systems. It can also mean pivoting toward higher priority targets or systems linked to the system they have compromised.
What is CybelAngel’s part in the Cyber Kill Chain?
It is good to keep in mind that the Cyber Kill Chain is conceptual and only reflects parts of how an intrusion can occur. It is a great tool, if dated tool, to help defenders map certain types of threat environments. But it needs to be adapted to the defender’s available resources for incident response.
In an age of big data, APT actors can easily find information that is not secure. It is necessary to make it increasingly difficult for attackers to target your enterprise.
We help from the Reconnaissance Phase!
CybelAngel protects businesses by reducing the opportunity of attacks at the first step, during the hacker’s Reconnaissance Phase. The more difficult you make reconnaissance of your organization, the less likely you will be hit or even targeted.
By focusing on freely available resources on multiple external attack surfaces across the internet, we reduce the opportunity for security threats to manifest.
Every day, we detect a significant volume of information that could be leveraged by APT actors in an attack.
For example in the following use cases, we can help:
- Third party suppliers who expose detailed confidential documents about your network on a connected storage device without
- Credentials exposed in code repositories
- API Threat Detection
- Stop the purchase of stolen credentials on the dark web
and many more…
CybelAngel detects exposed credentials before malicious threat actors identify and use these. Our threat intelligence helps you to proactively protect your organization, starting with better equipping your security teams with more visibility.
What to do if you’ve been targeted by a hacker?
CybelAngel can help in the investigation of a data breach by making sure that stolen documents are not shared or exposed on the perimeters we scan; we even find unprotected command and control C2 servers.
You can find out more by contacting our REACT team.
