Alert of the Month – GitHub, Credentials, and APTs

Table of contents
The Alert of the Month for May 2022 is a data exposure on GitHub that revealed high-level credentials risking network penetration, ransomware, and data exposure. This alert is emblematic of the continuing issues companies are experiencing with code repositories leaking credentials and other sensitive data. Without an External Risk Protection platform to locate this exposure, the risk to our client’s brand and continued operations would have gone unnoticed until they were exploited.
You can read on to learn more or hear directly from the analysts themself here.
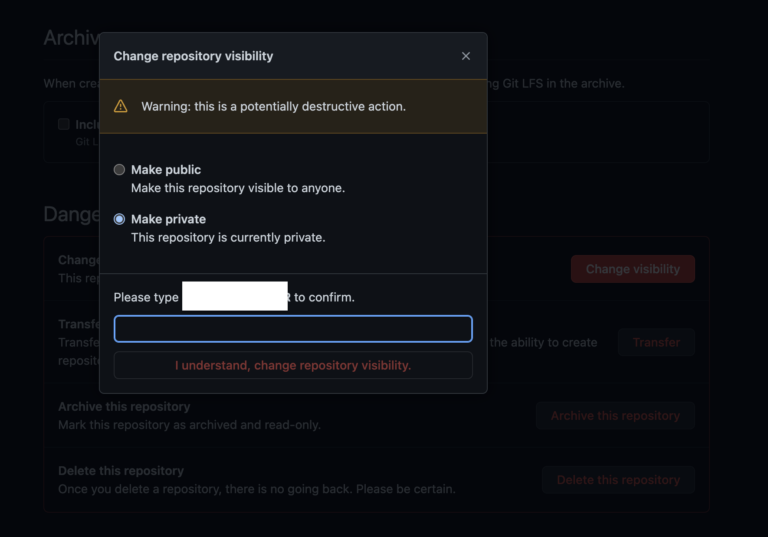
On May 6th, just after midnight, the CybelAngel platform identified a public code repository containing several of our client’s keywords. The Readme file reveals that the repository was created as a “compilation of useful data for an internal project.” Inside a YML was a series of credentials granting access to multiple systems, including production and test environments, Google Cloud Storage, MongoDB, and BigQuery. CybelAngel Cybersecurity Analyst Camille Faidherbe discovered the initial alert and began her investigation. “My first steps are always to confirm the findings; in this case, I was able to identify the identity of the repository owner and confirmed they worked for the client,” Camille explained. “From our analyst’s platform, we have several tools to help pinpoint sensitive information, like credentials. That helped me locate the passwords in the YML file, and once I had an idea of what was exposed, I could write up the incident report and inform the client,” said Camille. “What struck me was that the repository was not always publicly accessible as we would have seen it earlier. That tells me that at some point quite recently, someone who had access and the right permissions made the repository public,” explained Camille. “Changing a repository’s visibility is very risky, so much so that GitHub puts multiple warnings and checks in place to prevent users from making a mistake. It couldn’t be an accident, but that does not rule out someone needing to share this quick and ignoring warning labels,” she said. Having confirmed the platform findings, Camille prepared to inform the client of their risks. 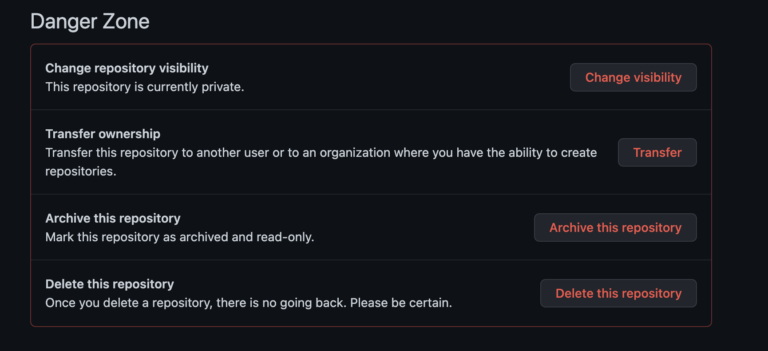
Did you enjoy this month’s alert? You hear from Camille herself on our LinkedIn Live.
