CVE-2023-34362 Explained: Inside the Zero-Day that Fueled Global Data Theft

Table of contents
In May 2023, a zero-day exploit in Progress Software’s MOVEit Transfer exploded into one of the largest supply chain breaches on record. CISA later estimated that more than 3000 US organizations and 8000 worldwide were affected, from banks and insurers to airlines and federal agencies. But for many, the first sign of trouble was seeing their data listed on Cl0p’s leak site.
This wasn’t a random compromise. The Cl0p ransomware gang used a precise attack chain, including a SQL injection vulnerability, a custom web shell called LEMURLOOT, and rapid data exfiltration. Let’s step back through that chain to understand how it happened… and how defenders can spot the signs before it happens again.
Background: Why MOVEit matters
Managed file transfer (MFT) platforms sit at the heart of supply chains. They’re used for many different purposes, such as to:
- Move payroll data between HR providers and banks
- Transmit patient records across healthcare partners
- Handle sensitive files for government contracts
In many organizations, these MFT tools replace email or file transfer protocol (FTP) as the trusted channel for high-volume, regulated transfers.
And it these managed file transfer vulnerabilities make them highly appealing to attackers.
1. What is MOVEit Transfer?
MOVEit Transfer is one of the most widely deployed MFT solutions. It supports Microsoft SQL Server and Azure SQL databases, can integrate with business automation workflows, and underpins critical data flows for enterprises and public institutions.
Exploiting a MOVEit vulnerability gave the Cl0p ransomware group direct access not only to a single company’s files, but in many cases to downstream partners as well.
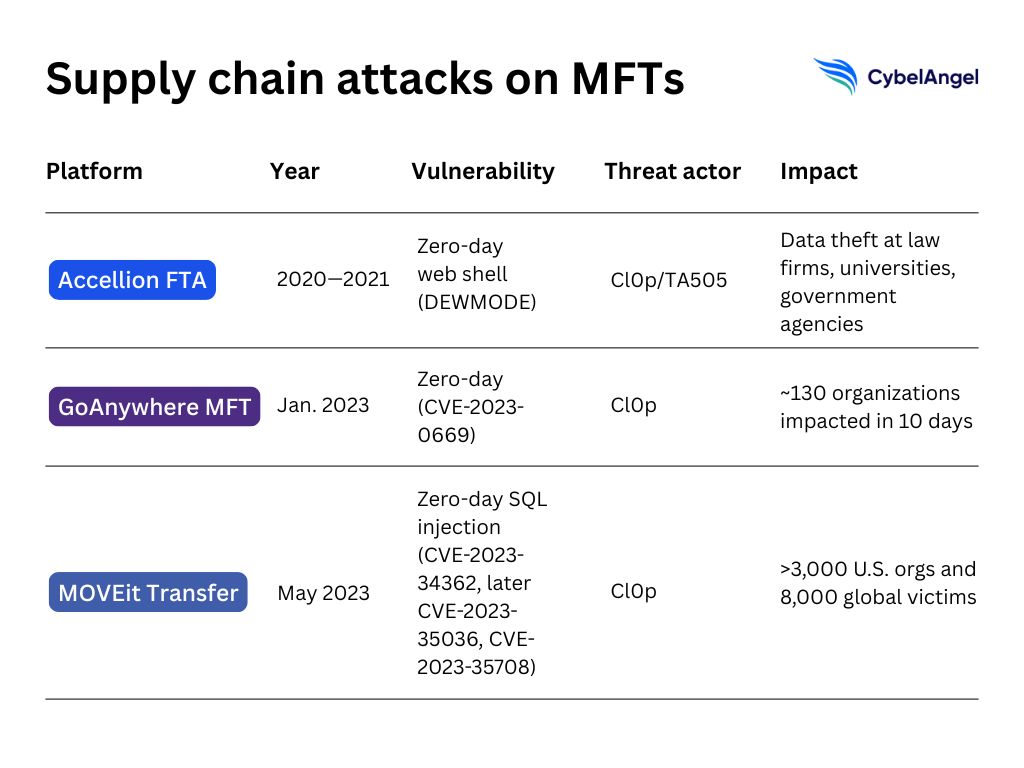
2. Are other MFTs under fire?
This wasn’t the first time threat actors exploited MFT software.
- In 2020, Accellion’s File Transfer Appliance was compromised through a zero-day web shell dubbed DEWMODE, leading to data theft across law firms, universities, and government agencies.
- In early 2023, Fortra’s GoAnywhere MFT was hit by another zero-day, CVE-2023-0669, with Cl0p claiming data exfiltration from more than 130 organizations in just ten days.
MOVEit followed the same pattern, with a critical vulnerability being exploited before patches were available, with data exfiltration as the endgame.
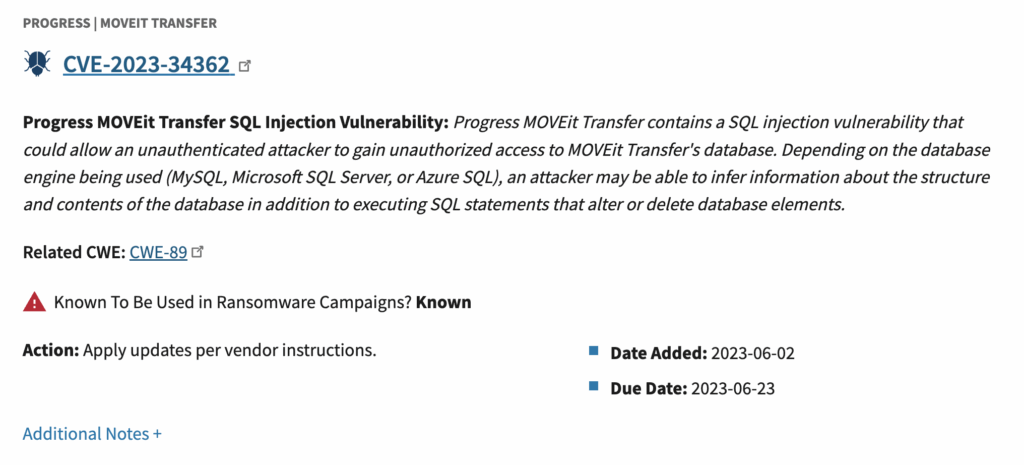
The zero-day vulnerability (CVE-2023-34362)
So, how did the MOVEit hack happen? At the center of the MOVEit breach was a SQL injection zero-day in Progress MOVEit Transfer, tracked as CVE-2023-34362.
SQL injection is a technique where attackers manipulate database queries by inserting malicious input into a web application field. In this case, it allowed unauthenticated attackers to interact directly with MOVEit Transfer’s database and execute commands beyond the software’s intended functionality.
The vulnerability was first exploited in the wild on May 27, 2023, before Progress Software had any public knowledge of it. Patches were released on May 31, 2023, but by then, active exploitation had already begun. The flaw affected multiple MOVEit Transfer versions, including 2020.0.x through 2023.0.0.
In June 2023, CISA added CVE-2023-34362 to its Known Exploited Vulnerabilities (KEV) Catalog, marking it as a critical vulnerability with ongoing exploitation.
But unfortunately, CVE-2023-34362 was only the first in a series of critical flaws:
- In June 2023, Progress disclosed CVE-2023-35036, another SQL injection vulnerability in MOVEit Transfer
- CVE-2023-35708 was another SQL injection flaw in MOVEit Transfer that allowed unauthenticated attackers to craft payloads granting unauthorized access
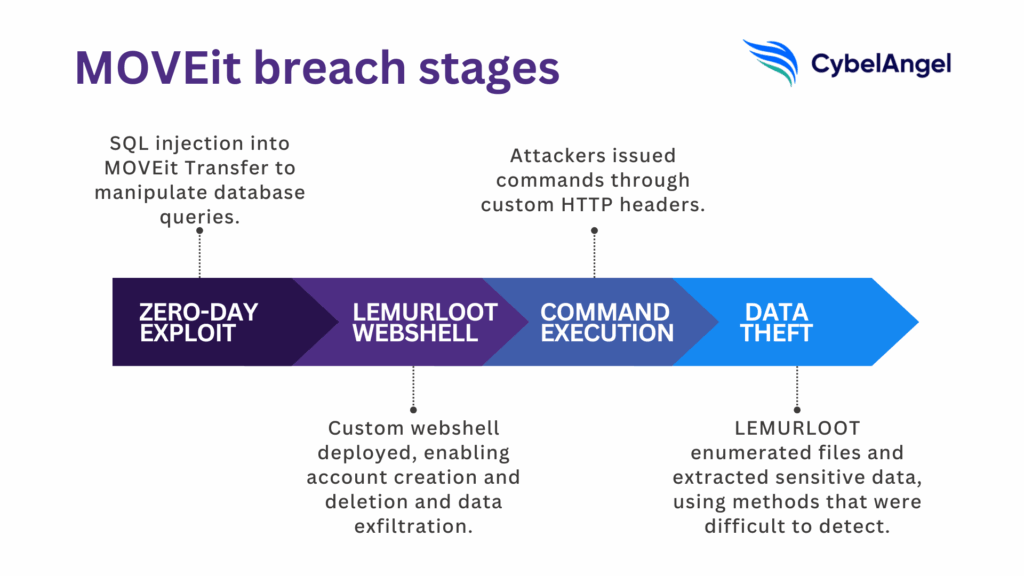
From exploit to webshell: LEMURLOOT analysis
Once the SQL injection vulnerability was exploited, the Cl0p ransomware gang used it to deploy a custom web shell known as LEMURLOOT.
Written in ASP.NET (as an .aspx file), LEMURLOOT was typically installed under the name human2.aspx to blend in with MOVEit Transfer’s legitimate human.aspx component.
This gave the attackers a backdoor directly into the MOVEit Transfer web application.
LEMURLOOT’s functionality went well beyond a simple command shell. It could:
- Create or delete user accounts, often with administrator privileges, disguised as “Health Check Service”
- Exfiltrate data from MOVEit Transfer’s SQL database and from Microsoft Azure configurations
- Masquerade as a legitimate file, compressing its responses in gzip to reduce detection
Access to the web shell required a valid HTTP request with a custom header, X-siLock-Comment, set to a randomly generated password established when the shell was first installed.
Once authenticated, attackers could chain commands using additional headers such as X-siLock-Step1, X-siLock-Step2, and X-siLock-Step3.
This allowed persistence even if parts of the server were rebuilt, as long as the MOVEit database wasn’t fully cleaned, malicious accounts remained active.
Command execution and persistence
Once authenticated to the LEMURLOOT web shell, attackers could issue commands through custom HTTP headers.
The most common were X-siLock-Step1, X-siLock-Step2, and X-siLock-Step3, which acted as stages in executing payloads and managing responses. These headers allowed Cl0p operators to chain commands and automate data exfiltration.
One of the most damaging features was the ability to create privileged accounts in the MOVEit Transfer database. These accounts used randomly generated usernames but appeared in the system under the innocuous label “Health Check Service.”
Attackers could later delete or recreate these entries at will, ensuring repeat access even if the shell itself was discovered and removed.
This persistence extended further.
If an organization rebuilt its MOVEit Transfer web server but left the SQL database untouched, the malicious accounts remained active. That meant Cl0p could log back in long after the initial compromise, bypassing remediation steps and prolonging exposure.
The data theft stage
With the web shell in place, Cl0p moved quickly to turn access into stolen data.
LEMURLOOT was used to enumerate MOVEit Transfer’s SQL databases, extract Microsoft Azure system settings, and pull sensitive files directly from the managed file transfer environment. Responses were compressed in gzip and sent back through HTTP requests, making the activity harder to detect.
Within just a few days of the first exploitation on May 27, 2023, thousands of organizations were compromised worldwide. CISA estimated that more than 3000 US entities and 8000 globally were affected.
Victims included financial institutions, airlines, universities, and government agencies, showing how a single zero-day vulnerability in a widely deployed file transfer system could cascade across entire supply chains.
This stage marked a shift in ransomware operations. Because instead of encrypting systems, Cl0p focused purely on data exfiltration, knowing that exposure on leak sites could be just as damaging as downtime… and often harder to recover from.
Attribution: The Cl0p ransomware group
The MOVEit exploitation was carried out by the Cl0p ransomware gang, also known as TA505.
Active since at least 2019, TA505 has a long track record of large-scale phishing, financial fraud, and ransomware operations. What makes them distinct is their repeated use of zero-day vulnerabilities in managed file transfer (MFT) platforms.
Prior to MOVEit, they exploited Accellion’s File Transfer Appliance (2020–2021) and Fortra’s GoAnywhere MFT (2023), both supply chain attacks that enabled data theft across dozens of industries.
Cl0p’s tactics have also evolved. Early campaigns followed the typical encrypt-and-extort model, combining ransomware deployment with threats to leak stolen data.
By 2021, the group increasingly relied on data theft alone, skipping encryption altogether. The MOVEit campaign showed this shift in full. Compromised organizations were contacted directly with ransom notes, and if they refused, stolen files were listed on the group’s leak site.
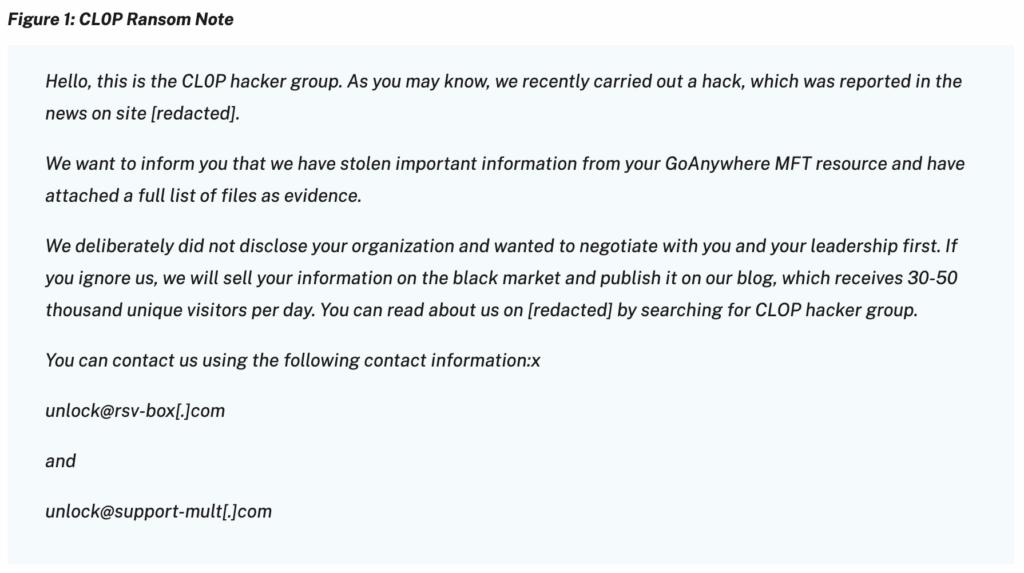
Indicators and detections
The MOVEit campaign left behind a clear set of indicators of compromise (IOCs).
CISA and the FBI released technical details in their June 2023 advisory, including file hashes, IP addresses, and detection signatures that cybersecurity defenders can use to hunt for evidence of intrusion.
Some of the most relevant IOCs included:
- LEMURLOOT web shell files (often named
human2.aspx) - SHA256 file hashes linked to malicious ASPX and DLL payloads
- IP addresses associated with command-and-control servers used in late May and June 2023
Example (excerpt from CISA’s IOC list):
File hash (SHA256): 0b3220b11698b1436d1d866ac07cc90018e59884e91a8cb71ef8924309f1e0e9
File name: human2.aspx
To aid detection, researchers also published YARA rules specifically designed to spot LEMURLOOT.
These rules look for characteristic strings, such as the X-siLock-Comment HTTP header, the “Health Check Service” account creation, and ASP.NET references embedded in the malicious payloads.
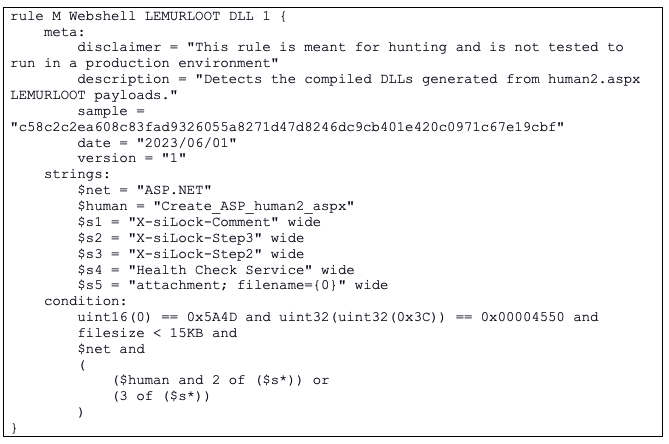
Some of the MITRE ATT&CK techniques observed in this campaign include:
- Initial Access – Exploit Public-Facing Application (T1190): SQL injection against MOVEit Transfer web application.
- Persistence – Server Software Component: Web Shell (T1505.003): Installation of LEMURLOOT for ongoing access.
- Exfiltration – Exfiltration Over C2 Channel (T1041): Compressed data exfiltrated via HTTP requests to attacker infrastructure.
Mapping these behaviors to ATT&CK helps defenders not just detect MOVEit-specific activity, but also recognize similar exploitation chains in other MFT or supply chain platforms.
Mitigation steps
The clop ransomware MOVEit incident showed how quickly a zero-day vulnerability can be turned into a mass exploitation campaign.
Key defensive steps include:
- Patch and scan continuously: Apply vendor updates as soon as they’re released and run automated vulnerability scans against internet-facing systems.
- Audit accounts: Check MOVEit Transfer’s database for unusual administrator accounts, such as those labeled “Health Check Service,” which Cl0p used for persistence.
- Segment and monitor networks: Use firewalls and network segmentation to limit lateral movement. Monitor logs for abnormal authentication attempts, and use EDR solutions to spot suspicious processes.
- Improve visibility: Track IOCs such as malicious ASPX files, DLL payloads, and suspicious IP addresses published by CISA and other security advisories.
Defenders need to catch exposures before attackers weaponize them.
CybelAngel helps organizations do just that.
It can detect internet-facing vulnerabilities, unauthorized data exposures, and exploited assets early. This means that SOC teams can remediate before the situation escalates.
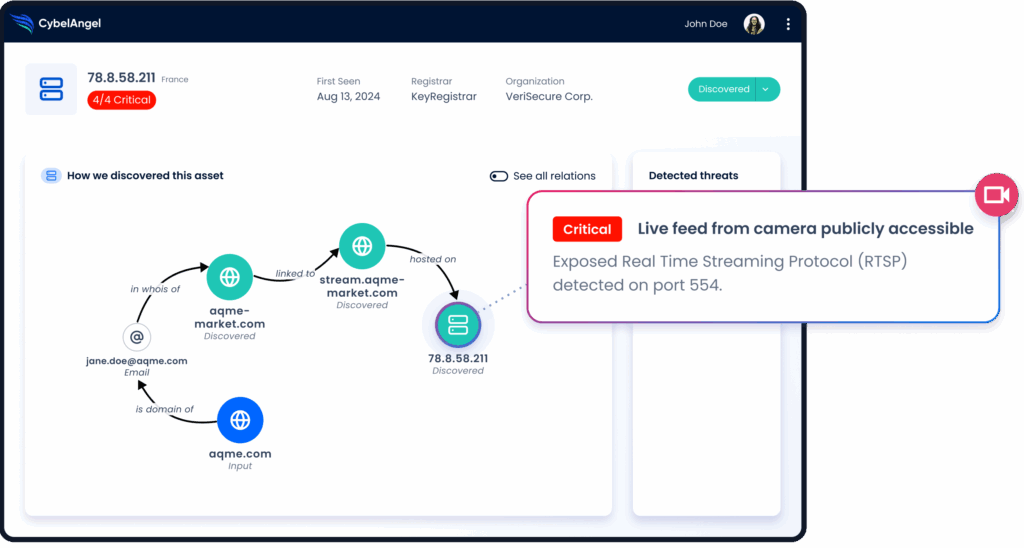
Figure 8: External threat intelligence in action. (Source: CybelAngel)
FAQs
What is the MOVEit Transfer vulnerability (CVE-2023-34362)?
It was a critical SQL injection flaw in Progress MOVEit Transfer that allowed attackers to access and modify the platform’s database without authentication {CISA, 2023}.
How did the Cl0p ransomware group exploit MOVEit?
They used the SQL injection to install a malicious ASPX web shell (LEMURLOOT), create hidden admin accounts, and exfiltrate data at scale.
What is a zero-day SQL injection attack?
A zero-day means the flaw was unknown to the vendor when exploited; SQL injection lets attackers manipulate database queries by inserting malicious code into inputs.
What is the LEMURLOOT web shell?
A custom backdoor disguised as a MOVEit file (human2.aspx) that let attackers run commands, steal Azure configs, and pull sensitive files.
What were the stages of the MOVEit attack?
Here are the main stages:
- Initial SQL injection exploit
- Web shell installation
- Creation of privileged accounts
- Database and file enumeration
- Large-scale data exfiltration techniques
How can businesses protect themselves?
Apply vendor patches quickly, monitor for unusual accounts or ASPX files, and use tools that detect exposures and IOCs before attackers move to exfiltration. Also, read CISA advisories for additional information.
Conclusion
This breach showed how one flaw in the MOVEit transfer environment cascaded through entire supply chains. But tools like CybelAngel can break the cycle. Defenders need visibility, and CybelAngel offers it, by detecting and remediating exposures before they become breaches. Book a demo to learn more.

