The Cybersecurity Trends Shaping 2025 (So Far)

Table of contents
The first half of 2025 has been anything but quiet. We’ve seen a wave of targeted campaigns from state-backed actors, the rise of leaner ransomware groups, and social engineering tactics that feel more like espionage than cybercrime.
This article distills the most critical trends and threat developments from the past six months. From AI-enhanced malware to PDF-laced phishing campaigns, here’s what’s happening, who’s behind it—and what you should be watching next.
Why cybersecurity trends matter
Trends are signals. They show us how threat actors are evolving, where vulnerabilities are being exploited, and what techniques are gaining traction.
For CISOs, understanding these trends isn’t about chasing hype. It’s about anticipating where risk will come from next. You can also focus your resources where they matter the most.
And ultimately, recognizing patterns early can make the difference between a quick containment and a full-blown data breach.
With that in mind, let’s break down the top 7 trends shaping the first half of 2025.
1. Nation-state activity: More sophisticated, and harder to spot
Advanced Persistent Threats (APTs) are cyberattacks designed to gain unauthorized access to systems and remain undetected for extended periods, with goals including cyberespionage and data theft. Many nation states sponsor APT groups to further their own geopolitical aims.
And their methods are diverse, and difficult to spot:
- Velvet Chollima, a North Korean APT group, launched a long-game spear-phishing attack using weaponized PDF documents. The group built trust with government officials over weeks (even posing as South Korean government staff) before delivering their payload.
- Russian-linked TAG-110 has gone back to basics with macro-enabled Word files in Central Asia. This is proof that even low-tech cyber threats can do serious damage.
- Luna Moth has been blending social engineering and voice phishing, no malware needed. This lets them bypass traditional security measures.
Takeaway
APT hackers don’t always trip threat detection alarms. Review your threat intelligence feeds to monitor impersonation and long-term social engineering attacks. Plus, make sure your staff can recognize trust-building tactics, rather than just obvious phishing campaigns.
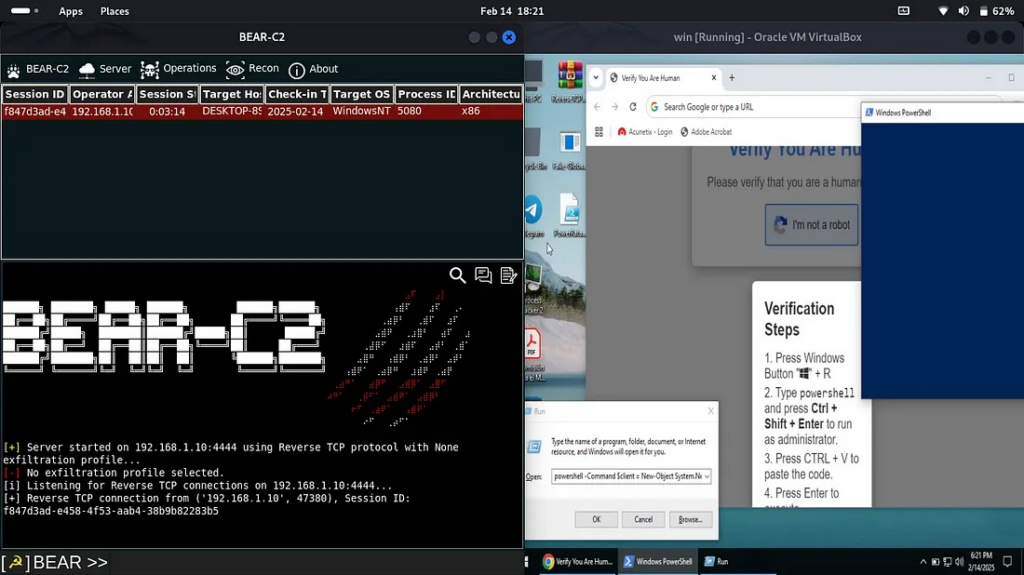
2. Ransomware is blurring into social engineering
While high-profile takedowns like LockBit have disrupted top-tier players, the overall threat has simply shifted shape.
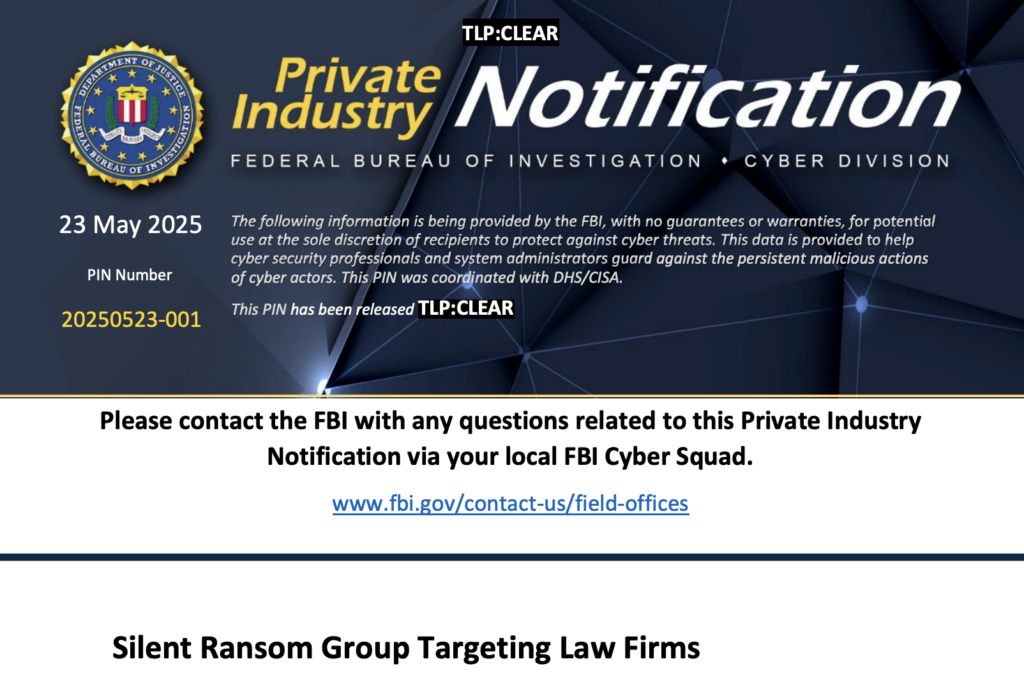
Take Luna Moth, also known as Silent Ransom Group. This actor skips the ransomware payload altogether. Instead, they use callback phishing (also called TOAD, or telephone-oriented attack delivery) to lure victims into calling fake IT support lines.
Once on the phone, attackers convince users to install remote access tools, then exfiltrate sensitive data. The extortion comes later.
The FBI issued a warning this year specifically about Luna Moth’s focus on law firms. But the tactic is spreading. It’s low-tech, low-cost, and surprisingly effective, bypassing many technical controls by leaning on human trust.
Takeaway
Don’t rely on encryption as the signal for ransomware. Monitor for unusual outbound data flows, and prepare your team for voice-based phishing and extortion initiatives like TOAD. If it sounds like your IT team but feels off, it probably is.
3. AI-driven phishing is the next big thing
Phishing has always relied on believability. And in 2025, AI phishing is raising the bar.
Scammers are now using large language models (LLMs), machine learning, and generative AI tools to craft and optimize phishing emails, clone voices, and spin up fake websites, all tailored to their targets.
This year, attackers have used AI tools like DeepSeek and ChatGPT to generate spear-phishing emails that mimic internal communications with uncanny accuracy.
In one case, employees at a multinational firm joined what they thought was a legitimate video call with their CFO. It wasn’t. The entire call was a deepfake, orchestrated to authorize a fraudulent $25 million wire transfer.
Takeaway
Train employees to verify identity across multiple channels, especially for high-value requests. Assume voice, email, and even video can be faked. If your process relies on trust alone, it’s already vulnerable.
4. AI-powered malware isn’t that smart (yet)
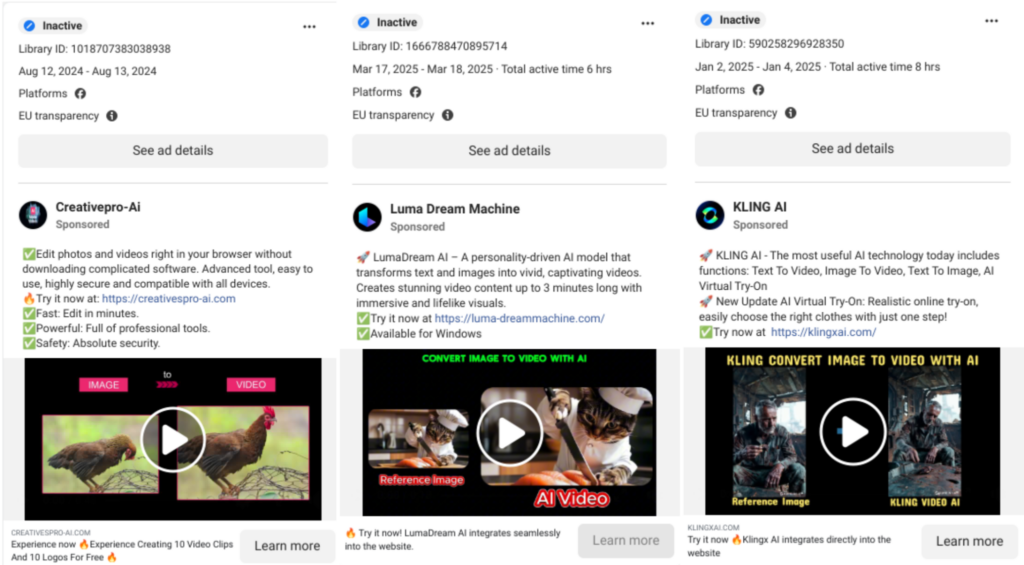
Since late 2024, Mandiant has tracked a campaign by UNC6032, a threat actor using fake artificial intelligence tool websites to lure victims. These sites, impersonating platforms like Luma AI and Canva Dream Lab, promise to generate videos from text prompts. In reality, they deliver Python-based info-stealers and remote backdoors.
The hook is simple. Advertise a trendy GenAI tool on social media, point users to a fake site, and let curiosity do the rest. Thousands of malicious ads have reached millions across LinkedIn and Facebook.
But so far, AI algorithms haven’t produced an actual malware that rivals human-authored code. Experts agree that current models lack the complexity and control to generate reliable, evasive payloads on their own.
But that’s not the point. AI makes it easier for less-skilled actors to launch viable attacks. And it’s only getting better. Once AI automation becomes deeply embedded in legitimate software pipelines, we should expect the same for malware.
Takeaway
AI-generated malware isn’t highly advanced yet. But it’s coming. Start monitoring AI is working in the threat landscape now, so you’re not playing catch-up later. Then your cybersecurity strategy will be ready to face it head-on.
5. Supply chains are the weakest link
Modern supply chains are hyper-connected, and increasingly exposed. Every vendor, tool, and integration is a potential attack path. Threat actors know this. Instead of battering down the front door of a well-defended enterprise, they slip in through smaller, less-secure suppliers.
A 2024 study found that 91% of organizations suffered a software supply chain attack in the last year, with the global cost expected to hit $60 billion in 2025.
These attacks often target:
- Third-party code repositories
- Open-source components
- Cloud infrastructure misconfigurations
- Poorly secured APIs
- Remote work setups
Compromising a single provider can ripple across thousands of customers, partners, and end users, as seen in the SolarWinds breach, where malicious code updates were silently pushed to over 18,000 customers, including government agencies.
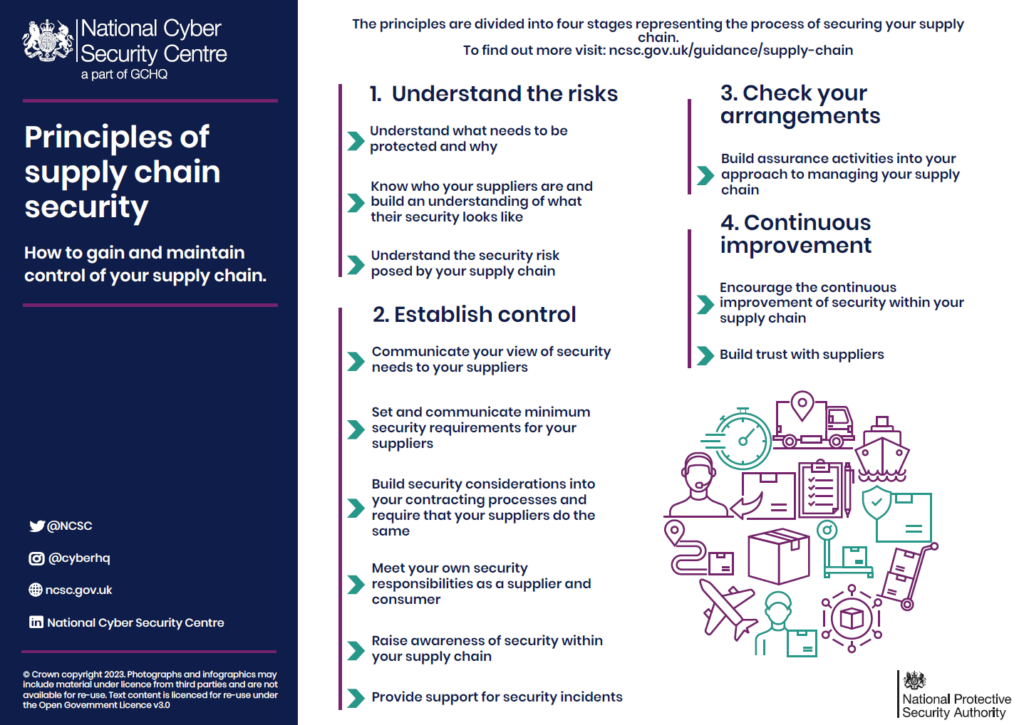
Takeaway
Map your critical suppliers and rank them by risk, not just spend. Start asking harder questions about security posture and incident response. If a breach at one vendor could take you offline, it’s time to rethink the partnership (or the controls around it).
6. Tax season is a cybercriminal’s playground
Tax season isn’t just busy for accountants. It’s peak hunting season for cybercriminals. Between January and April 2025, the US financial sector saw a sharp rise in phishing attacks, leaked credentials, and malware-laced emails.
A lot of these cybersecurity threats were tax-themed, with fake IRS messages, scam CPAs, and fraudulent “tax correction” alerts. For example, in Q1 2025, a cybercriminal group called Storm-0249 sent thousands of emails with fraudulent Docusign pages to launch a malware installation.
Attackers also leveraged vishing and smishing tactics to bypass multi-factor authentication (MFA )and reach employees directly. In some cyber incidents, they impersonated IRS officers using AI-generated deepfakes (voice and video) to trick victims into handing over sensitive information.
Social media played a role too. Fraudsters posed as “tax refund influencers” or fake CPAs offering free services. Once trust was gained, victims handed over personal data, unknowingly giving scammers everything needed to file fake returns and drain accounts in real time.
Takeaway
Run targeted phishing simulations during tax season, especially in finance, HR, and executive teams. Train staff to verify any tax-related communication. If it mentions a refund, audit, or urgent filing correction, it’s a red flag until proven otherwise.
Run targeted phishing simulations during tax season, especially in finance, HR, and executive teams. Train staff to verify any tax-related communication. If it mentions a refund, audit, or urgent filing correction, it’s a red flag until proven otherwise.
7. Turf wars, takedowns, and new faces
Cybercrime isn’t static, and neither are the players behind it. Ransomware groups, infostealer crews, and politically motivated hackers are all caught in an ongoing tug of war for dominance, visibility, and resources.
In early 2025, one of the biggest stories wasn’t just an attack. It was a power grab. The group DragonForce rebranded as a cybercrime “cartel” in March and promptly went after its rivals. Within weeks, RansomHub’s infrastructure was knocked offline, contributing to a noticeable drop in ransomware attacks in April.
Elsewhere, takedowns made serious dents. Black Basta, once a major ransomware-as-a-service operation, slowed dramatically following a law enforcement clampdown, the Qakbot botnet takedown (Operation Duck Hunt), and the leak of its internal chat logs.
Meanwhile, Lumma Stealer, one of the most prolific info-stealer threats in circulation, was disrupted by a joint Microsoft–Europol operation in May. Over 1,300 malicious domains were seized, with infrastructure rerouted to sinkholes.
But while some names fall, others return. The Russian group Killnet resurfaced after months of silence, claiming to have hacked Ukraine’s drone-tracking systems. The timing was no accident, as the announcement aligned with Russia’s Victory Day celebrations. While the tactical impact is unclear, the symbolic move suggests Killnet may be rebranding itself.
Figure 7: Tweet from Europol announcing the Lumma Stealer takedown. (Source: Europol)
Takeaway
Threat intelligence should track actor behavior, not just malware signatures. When groups fragment or rebrand, their tactics often shift too. Security teams should maintain dynamic threat profiles, and don’t underestimate the impact of disruption, even when it comes from within the ecosystem.
Threat intelligence should track actor behavior, not just malware signatures. When groups fragment or rebrand, their tactics often shift too. Security teams should maintain dynamic threat profiles, and don’t underestimate the impact of disruption, even when it comes from within the ecosystem.
How CISOs should respond
The first half of 2025 has made one thing clear: the cybersecurity landscape is more adaptive, more personal, and more interconnected than ever. Defending against evolving threats means thinking beyond firewalls.
Focus your efforts on three key areas:
- Continuous attack surface discovery: You can’t protect what you don’t know.
- Threat actor profiling: Know who’s targeting you, and how they operate.
- Vendor risk monitoring: Because your weakest link might be upstream.
Ask yourself:
- “Do we track TTPs by actor category, or just by alert volume?”
- “How quickly would we detect a vendor compromise in progress?”
- “Are we prepared for an AI-enabled phishing or malware campaign?”
- “Do we have adequate identity and access management (IAM) procedures?”
Plus, bear in mind that if you need extra support, CybelAngel’s external threat intelligence platform helps you answer these questions with real-time visibility.
FAQs
Is AI really changing the threat landscape, or is it just hype?
AI isn’t creating next-gen malware (yet) but it’s already changing how phishing, malware delivery, and impersonation work. It’s removing friction for attackers, allowing faster, more convincing scams at scale. That trend is only going in one direction.
How do I know if my supply chain is putting us at risk?
Start by mapping your suppliers, including cloud platforms and third-party integrations. Then, assess their cybersecurity maturity, not just compliance. If you can’t trace how a vendor stores or processes sensitive data, that’s your first red flag.
Are nation-state threats only a concern for governments?
Not anymore. APTs increasingly target critical infrastructure and private sector organizations. And many tactics used by state-backed actors (like social engineering and impersonation) are being adopted by criminal groups.
How can I prepare for social engineering attacks that bypass technical controls?
Use phishing simulations that reflect real-world tactics like voice spoofing and fake DocuSign pages. Make verification across channels a policy, not just a suggestion. And treat trust (especially during high-pressure seasons like tax time) as a vulnerability.
Conclusion
The first half of 2025 has shown just how quickly the threat landscape can shift. From AI-powered advancements to infighting among ransomware groups, attackers are adapting faster—and getting smarter about how they operate.
For cybersecurity professionals, staying ahead means tracking not just the threats, but the people behind them. And if you’re curious about what your external threat surface really looks like, you can book a demo with CybelAngel to find out.
