Zero Trust Architecture [An Analysis]

Table of contents
This analysis is written by CybelAngel’s analysts, Alizé Marchand and Damya Kecili.
The proliferation of cloud services, remote work, and IoT devices has introduced new vulnerabilities, and these have rendered the traditional perimeter-based security approaches less effective.
In a nutshell, this is why Zero Trust Architecture (ZTA) has emerged in recent years as a leading framework. It offers a robust solution to today’s complex cybersecurity challenges.
Let’s explore why.
Limitations and weaknesses of traditional authentication methods
Traditional cybersecurity models are rooted in the belief that there is a defined boundary between an external network that cannot be trusted and a protected internal network. This access implies safety from any kind of threat.
The traditional perimeter security model, often referred to as the castle and moat approach, centers on establishing a robust security perimeter. This is primarily done through firewalls and intrusion detection systems, to safeguard a network. The fundamental objective is to prevent malicious entities from accessing the network by creating a substantial barrier. Security infrastructures based on this concept assume that individuals within the castle’s walls could be trusted and that therefore substantial risks were kept at bay.
But how does it work in practice?
In traditional security architecture, the network is protected by perimeter firewalls, isolating trusted internal systems from the untrusted internet. Public-facing services (like web and email servers) are placed in a DMZ, a semi-trusted zone between the internet and the internal network. An internal firewall further separates sensitive resources (such as databases, application servers, and user devices) from semi trusted zones. Security tools like intrusion prevention systems (IPSs), web application firewalls (WAFs), and antivirus operate in the security operations center to monitor and respond to threats, relying on a hardened perimeter to keep attackers out.
However, traditional user authentication methods are inadequate against numerous vulnerabilities. The rise of remote work and hybrid cloud as the dominant enterprise infrastructure has placed previously trusted employees and infrastructure outside traditional security perimeters. A perimeter-based security model does not, in fact, allow an organization to protect its assets managed by a third-party cloud service provider. Some argue that the very concept of a defined security perimeter is now outdated. The growing number of cybersecurity attacks targeting remote employees truly highlights the limitations of these traditional methods.
It is also important to remember that trust in itself is a human concept that we taught computers to adapt to, and that it is unreliable on several levels. It is indeed impossible to ascertain that every single employee within the perimeter, as well as contractors and approved parties, are trustworthy.
Let’s take a look at this use case example
In 2022, a former employee of the digital wallet Cash App, who was apparently holding grudges against the company, was able to download the personal data of users, including their full names, brokerage portfolio values, brokerage portfolio holdings, and stock trading activity. This data breach ended up affecting around 8.2 million customers. The company faced a class action lawsuit after a four-month delay in notifying those impacted following the discovery of the incident. This data leak was made possible by the fact that, even though the contract of the aforementioned employee was terminated, their user access permissions had not been revoked, making it possible to download internal data from outside the company.
Considering these cases, it is clear that modern network complexity and increasing threats require a revised approach to security. The concept of Zero Trust emerged from this evolving need.
II. How does ZTA overcome current challenges
Zero Trust Architecture represents a fundamental shift in the cybersecurity framework. It provides a range of strategic and operational benefits, allowing organizations to build more resilient and secure digital environments.
What is ZTA?
Theorised in 2011, by John Kindervag, a former Forrester Research analyst, Zero-Trust Architecture (ZTA) has emerged as a leading cybersecurity paradigm. Unlike conventional approaches that assume implicit trust within an organization’s network. Zero Trust operates on the principle of “never trust, always verify.” This model treats all users, devices, and systems, both inside and outside the corporate network, as potential threats. It requires continuous authentication, strict access controls, and real-time monitoring.
The NIST Special Publication 800-207 identified seven principles associated with a Zero-Trust Architecture:
- Explicit trust: Always authenticate and authorise. You should never trust implicitly.
- Least privilege access: Minimise access rights and grant only the minimum necessary permissions to perform tasks.
- Assume breach: Assume that a breach has either already occurred or will occur. Organisations must always be prepared to detect, respond to, and contain threats.
- Micro-Segmentation: Reduce the chances of lateral movement by segmenting the network into isolated segments.
- Continuous monitoring and validation: Constant monitoring of user behavior, devices, applications and network traffic, required to detect and respond to any suspicious activity.
- Centralised policy enforcement: Unifying the system to manage authentication, authorisation and access control.
- Automated response and adaptive security: Security systems should automatically respond to threats and adapt based on the continuously gathered data.
With technological advancements and escalating cybersecurity threats, a Zero Trust Architecture is emerging as a key solution for organizations. Recognizing the increasing prevalence of internet-based threats, major technology companies like Microsoft, Google, and Amazon have adopted the ZTA model.
Catch up on more NIST framework compliance via our blog:
The benefits of ZTA
The Zero Trust Architecture differs from traditional on-premises models by prioritizing adaptable and strong security across both internal and external organizational boundaries. Many cybersecurity professionals view ZTA as a potential answer to the increasing complexities of modern cyber threats.
Strengthens your security framework
Rather than relying on a one-off verification, Zero Trust continuously checks the security status of users and devices. Access is constantly reassessed, ensuring only the most up-to-date and trusted entities are granted access, which helps mitigate threats in real time. By restricting entry points to only those users and devices with a legitimate need, organizations dramatically reduce the surface area for potential attacks.
Faster and more effective incident management
Zero Trust empowers organizations with continuous network monitoring and sophisticated analytics to detect threats as soon as they emerge. Lateral movement is prevented through the isolation of compromised systems and the implementation of strict access controls.
Smoother adaptation to evolving threats
Security measures are adaptable and evolve alongside new technologies.
Organizations implementing the ZTA model can safely adopt cloud computing or remote work. Today’s widespread remote and hybrid work models introduce new cybersecurity challenges. The traditional security approach relied on VPNs, whereas Zero Trust Architecture (ZTA) offers a comprehensive authentication framework, encompassing policies and technology, to ensure security regardless of location.
III. Implementing ZTA across industries
While still largely a theoretical framework, ZTA demonstrates significant adaptability across various sectors, such as healthcare, financial services, manufacturing, and satellite operations. Let’s take a closer look at use case examples.
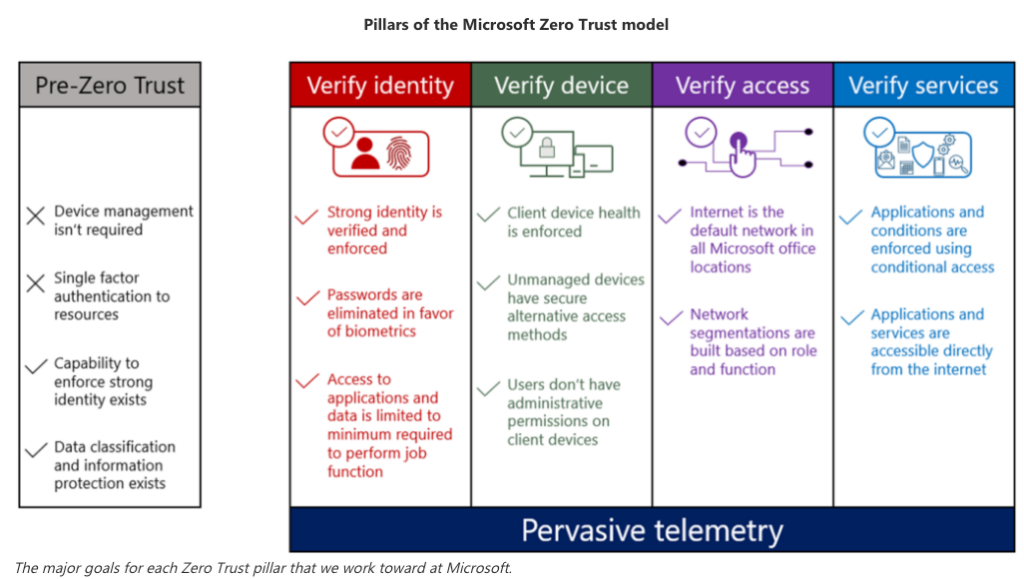
ZTA at Microsoft
Initiating a shift to a Zero Trust Architecture over seven years ago, Microsoft can be seen as a precursor in this field. Carmichael Patton, principal architect at Microsoft, has shared more about how the company as a whole has been making a constant effort to implement the principles of ZTA.
Here are some measures that have been implemented to ensure stronger security:
- The identity of devices is systematically validated and the health of those same devices is continuously monitored.
- Pervasive telemetry is implemented. To put it simply, telemetry is the automatic collection and transmission of data from remote or distributed systems so that it can be monitored and analyzed. Pervasive telemetry means doing this everywhere and all the time: across all parts of a system, network, or application.
- Least privilege access is enforced. This means that employees are only granted access to parts of the infrastructure that are needed for them to work. Segmentation, meaning dividing a network, into smaller segments to control traffic and improve security. It is also put into place at the company level.
Microsoft also developed internal features to further protect its data. These include:
- Microsoft Information Protection
- The sensitivity button available on Microsoft 365 applications
- Azure Information Protection
- Cloud App Security which can monitor the connections where documents are being transmitted.

ZTA at Cairn Oil & Gas Vedanta
In March this year, Cairn Oil & Gas Vedanta, a prominent and innovative Indian oil and gas corporation, won the ETCIO Awards in 2025. This recognized their strategic adoption and meticulous deployment of a comprehensive zero-trust architecture. This advanced security framework has been instrumental in bolstering their digital infrastructure. It also directly contributed to their business success and industry recognition.
The company based their ZTA model on three emerging digital technologies: Cloud, AI/ML, and Data Analytics.
- Cloud-based SaaS solutions offered scalability and agility throughout the organization. This enabled the company to securely manage its growth in both personnel and cloud infrastructure while effectively addressing emerging security threats.
- Leveraging advanced AI and Machine Learning algorithms, sophisticated solutions are deployed to meticulously analyze and track user behavior patterns across digital platforms. This proactive approach allows for the identification of anomalies and suspicious activities in real-time, facilitating rapid detection of potential security threats.
- Data analysis platform to monitor user and application traffic in real time, detecting anomalies and threats. This visibility allows proactive threat identification, reducing data breach risk. This approach enables quick security action to protect sensitive information and maintain trust.
The adoption of a Zero Trust Architecture (ZTA) led to significant improvements in both security and user experience for Cairn Oil & Gas Vedanta.
This strategic move allowed the organization to successfully achieve three key objectives: the establishment of a secure and trusted IT architecture, the consolidation of proxy and VPN services, and an overall enhancement of user experience.
IV. What does the future hold for ZTA?
Even though the need for rapid and solid adaptation of cybersecurity infrastructures to be protected against new rising threats is undeniable, it is necessary to keep in mind that ZTA is not a magic solution that can be implemented within a day — something that has been confirmed by John Kindervag himself. ZTA is not a simple, unique product that can be purchased and used. Zero trust adoption is not a one-time event but rather an ongoing process. This progression involves the continuous implementation and improvement of security tools. The design of automated processes, comprehensive employee training, and the establishment of clear policies.
The journey to a full ZTA implementation is long and can be costly. To overcome these obstacles, companies need to establish a relevant, comprehensive strategy. It should encompass a proper schedule for a phased and smooth implementation of ZTA-related measures, a good budgeting analysis, as well as a good communication and training plan to ensure all employees are on board and don’t feel left out.
As the attack surface continues to expand, the implementation of zero trust policies becomes increasingly crucial. However, many companies are not adapting at the same pace. To enhance security measures, subscribe to an External Threat Intelligence tool. It ensures that your company remains fully aware of any vulnerabilities it might face.
CybelAngel complements a Zero Trust Architecture by providing critical attack surface management and threat intelligence that enhances the security posture beyond the internal network focus of Zero Trust.

