How to Avoid Doxxing as an Executive

Table of contents
Doxxing is when someone’s personal details are shared on purpose—and it can be hugely damaging. It’s often a tool for revenge or cyberbullying, or to destroy an organization’s reputation.
Let’s break down what doxxing is, how it works, and how to protect yourself from it, such as by using brand protection services.
1. What is doxxing and swatting?
What is doxing? And how does it differ from swatting? Here’s a quick rundown of swat vs dox meanings:
- Doxed meaning: Doxxing (short for ‘document tracing’) involves collecting and publishing someone’s private information online without consent, such as their financial information or social security numbers.
- Swatted meaning: Swatting is a form of doxxing where a false report is made to law enforcement, sending a SWAT team to the victim’s home address and creating a potentially life-threatening situation.
Doxxing can be perpetuated by abusers wanting to intimidate their victims, stalkers of famous celebrities, or cybercriminals wanting to damage a company’s reputation, for example.
How does doxxing work?
While it can happen in various ways, doxxing typically involves several steps that perpetrators use to gather, share, and exploit sensitive data.
Step 1: Gathering the information
There are lots of ways that doxers can gather information about their victims, including:
- Social media scraping: Social media platforms like Facebook, Instagram, and LinkedIn often contain a wealth of personally identifiable information (PII), including photos, locations, phone numbers, and details about personal relationships.
- Public records and databases: Information from public databases, such as voter registration, property ownership records, and court documents, can often be accessed online.
- Data breaches: When a company’s database is compromised, personal information such as email addresses, passwords, phone numbers, and even credit card information can be leaked.
- Social engineering: A doxer could use phishing emails or other impersonation tactics to persuade someone to share valuable information about themselves.
- People search engines: Websites like Spokeo, Whitepages, and Pipl collect and sell personal data, including addresses, phone numbers, and employment details.
- Reverse lookup services: Doxers can track the owner of a particular image or phone number to gather more information.
Step 2: Posting the information
Once the information is compiled, doxers can share it on open docs, public platforms, or anywhere else they choose, including:
- Social media platforms: Doxxers can publicly share the victim’s personal details on platforms like Twitter, Reddit, or Facebook, and tag the victim’s friends or family members to increase the exposure.
- Doxxing websites: Some websites are specifically designed to host doxxed information, and they often have large followings.
- Forums and online communities: Platforms like 4chan other anonymous forums are known for being hotspots for doxxing activities.
2. Is doxing a crime?
It depends on the jurisdiction, but generally, doxxing can be viewed as a crime. It’s a malicious act that can lead to online harassment, identity theft, ruined reputations, and psychological distress for its victims and their family members.
The consequences of doxing include:
- Harassment and threats: Victims often face relentless online harassment, including abusive messages, spam calls, and threats to their safety.
- Reputation damage: Doxxing can tarnish a person’s personal or professional reputation, especially if false or harmful information is shared.
- Emotional distress: The exposure of private details can lead to anxiety, fear, and emotional trauma, affecting mental health.
- Physical danger: In extreme cases, doxxing can lead to stalking, swatting, or even physical attacks, endangering lives.
- Financial loss: If sensitive information like bank account details or credit card numbers is exposed, victims may suffer identity theft or financial fraud.
- Professional consequences: Public exposure of controversial opinions, past mistakes, or private details can jeopardize careers or business relationships.
What are some doxxing laws?
There are lots of laws across the world that could apply to doxers, including:
The UK’s Malicious Communications Act (1988)
Under this law, sending threatening, offensive, or false messages with the intent to cause distress or anxiety is a criminal offense. Doxxing can fall under this category if someone publishes private details online with malicious intent, resulting in harm or distress to the victim.
Australia’s Cybercrime Act (2001)
Australia’s Cybercrime Act includes provisions related to online harassment and privacy breaches. It criminalizes the use of telecommunications or data networks to intentionally harm others, including posting personal details online without consent.
The EU’s General Data Protection Regulation (2016)
While not specifically a “doxxing law,” the GDPR provides strong protection for personal data. It requires organizations to handle personal data securely and gives individuals the right to request the removal of their data if it is publicly exposed or mishandled. Doxxing could violate GDPR provisions, and those responsible can face heavy fines.
The Interstate Doxxing Prevention Act (2015-16)
American Congress has introduced a law that criminalizes the intentional publication of someone’s personal information online with the intent to harass, intimidate, stalk, or harm them. This law provides penalties for offenders, including possible jail time of up to five years.
3. What are some recent doxxing use cases?
Let’s look at some real-life examples of doxing in action, with devastating (and sometimes tragic) consequences.
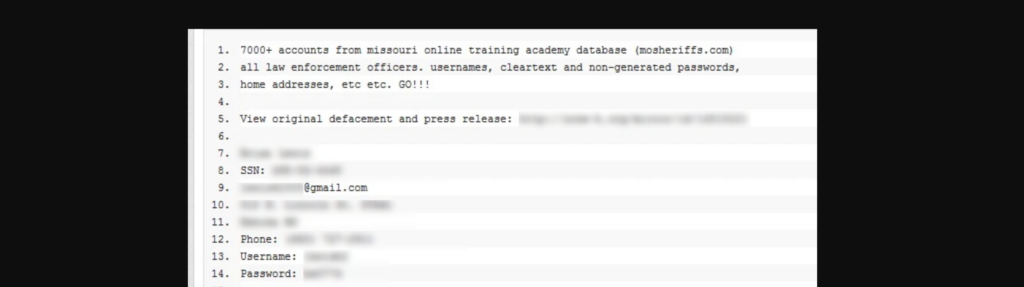
When law enforcement was exposed…
In 2011, the online coalition called Anonymous leaked the data of law enforcement officers from across America, allegedly in retaliation for police violence at a series of recent protests.
When JK Rowling was a target…
In 2021, JK Rowling accused three protesters of sharing a photo of her Edinburgh address on Twitter, by “carefully positioning themselves” to display it. Her mansion is also listed on Wikipedia.
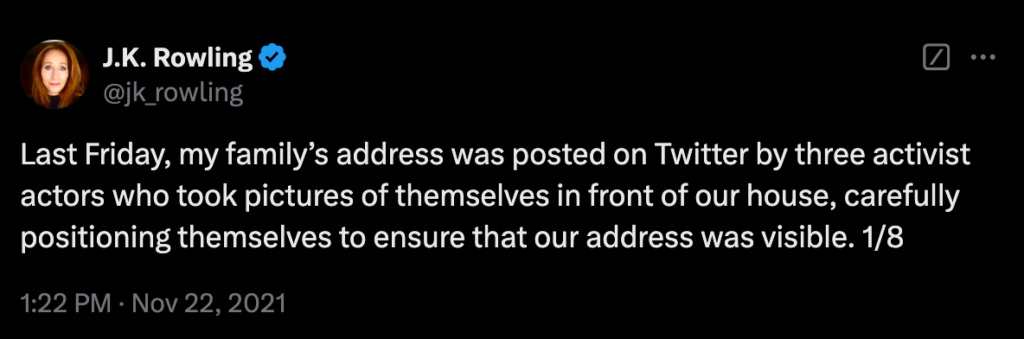
JK Rowling’s tweet in response to the photo outside her home. Source.
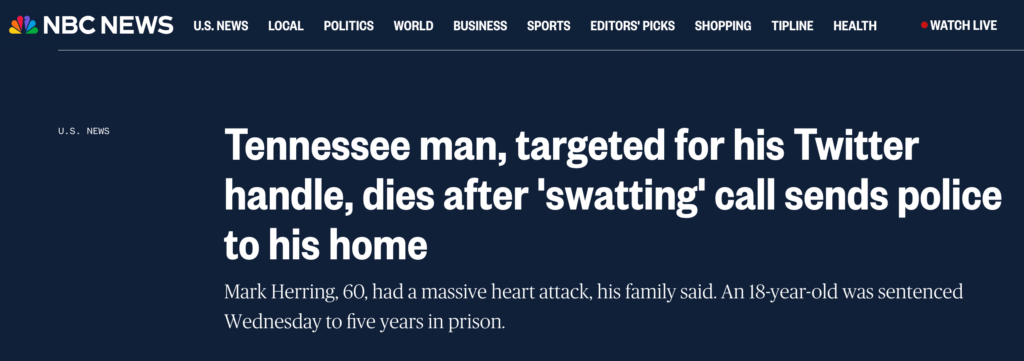
When a swat attack had tragic consequences…
After a dispute over a Twitter handle, a swatter then reported a fake murder at a 60-year-old man’s home. Tragically, the man died of a heart attack when law enforcement surrounded his home with guns drawn.
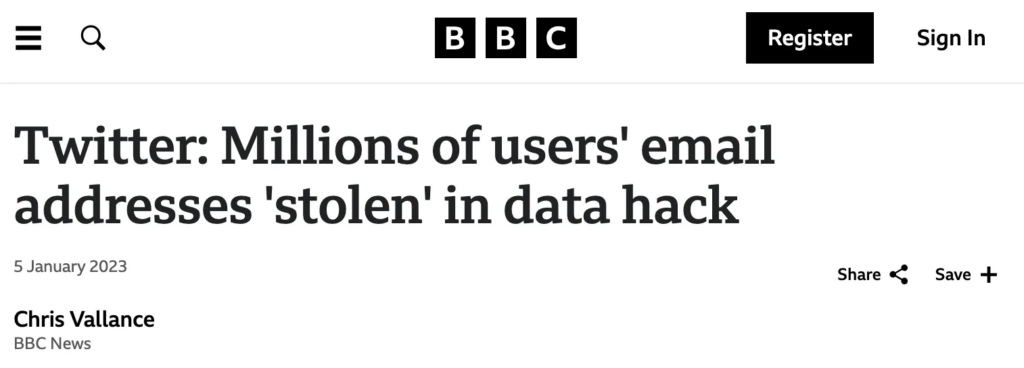
When X/ Twitter lost their users’ data…
In 2023, hackers posted the data of 200 million Twitter users on a forum for free, with experts saying it would, “lead to a lot of accounts getting hacked, targeted with phishing, and doxxed.”
When a doxxing site suffered…
In an ironic twist in 2022, the doxxing website Doxbin[.]com was targeted by a threat actor and suffered a leak of its own. Illicit forums are often subject to infighting and retaliatory actions against each other.
4. How to avoid getting doxxed
Let’s talk about how to not get doxxed in 5 proactive steps.
- Limit information shared online: Review your social media profiles and make sure you’re not sharing unnecessary personal details like your full address, phone number, and travel plans.
- Use pseudonyms: If you don’t need to use your real name in certain online spaces, consider using a pseudonym or an alias. This makes it harder for doxers to track down your personal information.
- Enable privacy settings: Social media platforms like Facebook and Instagram have privacy settings that allow you to control who can see your posts.
- Review your digital footprint: Regularly search for your name online to see what information is available about you. Set up Google Alerts for your name so you’ll be notified if your personal information is being shared publicly.
- Educate employees: For businesses, it’s essential to train employees, especially high-ranking officials, on data protection. Cyber hygiene practices like strong passwords, encryption, and avoiding public Wi-Fi are key to protecting sensitive data.
Bonus: Invest in brand protection
Brand protection services, like those offered by CybelAngel, play a crucial role in safeguarding your personal information and your company’s reputation.
CybelAngel’s comprehensive brand protection solutions include safeguarding against social media and app impersonation, domain protection, and dark web fraud.
Brand protection can fight against:
- The spread of false information
- Reputational damage
- The risk of swatting incidents or harassment
Through continuous monitoring, CybelAngel can detect when your personal or company information is being shared or sold on unauthorized websites, giving you the chance to intervene before the damage escalates.
5. Can you check if you’ve been doxxed on any websites?
Yes—but it can be time-consuming. One of the easiest ways is to search for your name, address, email, and other personal details on popular pages, doxxing websites, and social media platforms.
Some services, like the ones offered by CybelAngel, can automatically monitor the web and alert you if your information appears on any known data leak platforms, dark web pages, or doxxing forums.
6. What to do if you get doxxed
If you do find that you’ve been doxed, it’s important to act quickly. Here are the immediate steps you should take:
- Remove the information: Contact the websites and platforms where your information has been posted. Many websites will allow you to request the removal of personal data. If the platform refuses, take screenshots as proof, escalate the issue, and consider seeking legal assistance.
- Notify authorities: If you feel threatened, or if your information was shared with malicious intent, contact local law enforcement. If the doxxing escalates into threats of violence, whether by emails, phone calls, or otherwise, it’s important to report it immediately.
- Engage cybersecurity experts: If you’re a business or public figure, work with cybersecurity professionals to identify how your information was exposed and mitigate the damage. This can include removing data from data brokers and service providers, securing your social media accounts and network, and implementing brand protection services.
Wrapping up
You never know when someone who dislikes you or your brand might take action.
For businesses, brand protection services are a must. CybelAngel’s suite of cybersecurity tools and monitoring services can help ensure that your sensitive information—and that of your employees—remains secure.
If you want to protect yourself and your organization from the threat of doxxing, consider trying CybelAngel’s Brand Protection service with a demo.


