Reviewing the Docusign API Trust Exploit [Plus 5 Security Takeaways]

Table of contents
This blog written by CybelAngel’s analyst Tania Abou Ltaif is an analysis of the exploitation of eSignature platform, Docusign’s API, to distribute fraudulent invoices. Interested in reading more of our investigative content? You can find investigative threat note blogs here.
Why are trusted platforms like Docusign being used by cybercriminals?
Docusign is an award-winning leader in the eSignature and intelligent digital management space, headquartered in Silicon Valley, San Francisco.
The company, founded over two decades ago, focuses on streamlining contract management with its Intelligent Agreement Management platform. Users from real estate, finance, and government sectors can sign documents electronically through a quickstart process: upload, place fields, and send. Docusign also integrates with a well rounded tech-stack, including, Microsoft and Salesforce- making it a popular choice for millions of clients.
The premise of the tool is that its secure cloud storage ensures customer documentation is secure and easily accessible, and that includes a thorough security policy. It encompasses, for example, permissions for the end user like MFA authentication, digital checksums to validate document integrity, application-level encryption using AES 256-bit technology. Additionally, the platform offers signer authentication options and notifications for document status updates for extra peace of mind.
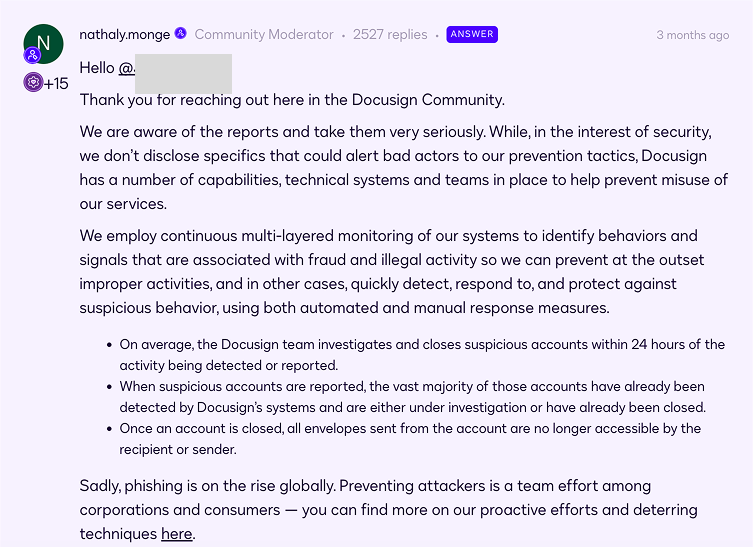
Despite a clearcut security first mindset built into the functionality of the Docusign platform, was still targeted by malicious actors.
Four months after this elevated phishing attack, let’s explore why and how this happened, and what your team can takeaway
An outline of the API trust exploit campaign at Docusign
Incident context
On November 5th, 2024, a cyber attack targeting Docusign’s API was uncovered by Wallarm Security, revealing a sophisticated method used by cybercriminals to exploit the platform for fraudulent purposes.
These attackers leveraged Docusign’s trusted system to send fake invoices that appeared legitimate, posing a significant threat to organizations relying on the platform for secure document management and electronic signatures.
Attackers used paid Docusign accounts to access the API, allowing them to automate and send fake invoices that appeared legitimate. This type of API misuse highlights an exploitation of application trust and not specific to only exploiting system vulnerabilities.

Cybercriminals leveraged legitimate Docusign accounts to distribute fraudulent invoices, bypassing traditional spam and phishing defenses.
Here is a quick rundown of how they carried out this attack:
- Exploitation of Docusign’s API for malicious purposes
- Use of legitimate, paid Docusign accounts by attackers
- Creation of fraudulent invoices that mimicked trusted sources
- Inclusion of realistic product pricing and fabricated charges
- Automation of the attack process through API integration
- Difficulty for recipients to distinguish fraudulent requests from genuine ones
- Bypassing of traditional email security filters due to use of legitimate Docusign platform
What were the hallmarks of this elevated phishing campaign?
During this incident, hackers exploited the platform’s “Envelopes: create API” to orchestrate a sophisticated phishing campaign targeting corporate users. What shaped the credibility of this attack was how attackers created legitimate, paid Docusign accounts, allowing them to manipulate templates and directly use the API to send automated emails that appeared authentic and standard.
These fraudulent emails contained fake invoices that mimicked requests from well-known brands, such as Norton Antivirus.
The invoices included accurate product pricing, additional charges like activation fees, and sometimes direct wire instructions. By sending these emails through Docusign’s platform, the attackers bypassed traditional email security measures and spam filters.
The campaign’s goal was to trick users into stamping their esignature onto these documents. These signatures could then be used to request unauthorized payments from organizations or their finance departments. This attack method has been ongoing for several months, with a noticeable increase in user reports over the past five months.
For example, the fraudulent invoices included the following elements:
- Company logos of well-known brands
- Accurate product pricing
- Additional charges (e.g., $50 activation fee)
- Direct wire instructions or purchase orders
- Requests for eSignatures
The attack’s success lies was its singular focus to bypass traditional security measures. Without malicious links or attachments, seen in classic phishing attempts, these fraudulent emails appeared authentic. This use case hammers home the need for vigilance and careful scrutiny- advancing techniques in phishing, SMS phishing, vishing etc. are all case in point for CISOs and SOC teams to prioritise zero-trust workspace wide policies, even amongst trusted tools.
Pointers for developers
Developers can fortify their API security by implementing a multi-layered approach.
Start by employing continuous API discovery to identify and catalog all active interfaces, including shadow APIs. Then invest time and training into reinforcing robust authentication mechanisms like OAuth 2.0 or JWT. You should also implement strict input validation to prevent injection attacks.
Here is a security workflow to keep in mind as you streamline everything from API requests to webhook admin:
- Encrypt all traffic using TLS, especially for REST APIs, to safeguard against man-in-the-middle attacks (including traffic related to web forms, PowerForms, and notarization processes).
- Adhere to the principle of least privilege when designing access controls, and use rate limiting to mitigate DDoS attempts (check out our latest DDoS guide for a refresh). Extend this principle to SDKs and any custom integrations. The CNIL have some great security tips here.
- Implement API gateways to centralize security controls, enabling easier management of policies, encryption, and protection against common vulnerabilities.
- Regularly audit your API endpoints for potential misconfigurations or exposed sensitive data.
- Finally, integrate security checks into your CI/CD pipeline to catch vulnerabilities early in the development process and enforce best practices in your workspaces. If you see anything unusual in the future, you can also report any unusual issues to Docusign developers here.
Wrapping up
API threats are set to grow from 2024 into 2025, driven by expanded usage, emerging vulnerabilities, and increasing automation tools like Bots-as-a-Service used by cybercriminals. These factors will significantly broaden the attack surface and heighten the risk of exploitation.
CybelAngel’s API Threat Detection feature offers comprehensive visibility into an organization’s external API landscape. This solution employs non-invasive scanning techniques powered by machine learning-driven analysis to identify vulnerable and misconfigured APIs. It allows customers to launch on-demand DAST scans on REST and GraphQL APIs to uncover potential threats, making API abuse one less concern for businesses
You can dive into our API Threat Detection handbook for more specific exposure use cases.
Understand API threat trends with CybelAngel
Equip you and your team with evolving threat intelligence to intercept and defend against all sophisticated phishing attempts. Be more equipped to fight API attacks by getting in touch with our team to see how we can help?
If you don’t want to stop reading check out our 2025 External Threat Intelligence report. Our CISO Todd Carroll analyzes the rising tide of AI fueled phishing attacks, and much more.


