Inside Ryuk Ransomware Attacks

Table of contents
Known for its precision targeting and devastating impact, Ryuk has earned a reputation as one of the most formidable ransomware families.
Ryuk ransomware was one of the first ransomware variants capable of identifying and encrypting network drives and resources, as well as deleting shadow copies on victim endpoints, making data recovery nearly impossible without external backups.
Let‘s explore how Ryuk ransomware started its campaigns and how to defend against attacks.
What is Ryuk ransomware?
First appearing in 2018, Ryuk ransomware quickly made headlines for targeting large, enterprise Microsoft OS. Ryuk‘s uniqueness is down to its ability to identify and encrypt network drives and resources, while deleting shadow copies on the victim endpoint.
Ryuk is a variant of the Hermes 2.1 ransomware, first sold on the dark web in 2017 by the cryptocriminal gang CryptoTech. In 2021, it was discovered that the new Ryuk variant had self-spreading, worm-like capabilities to cause damage without human intervention.
How does Ryuk compare to other ransomware?
Here‘s an overview of the differences and similarities between the ransomware families:
| Ransomware group | Year of emergence | Primary targets | Attack methods | Ransom amount extorted (average) |
|---|---|---|---|---|
| Ryuk | 2018 | Large organizations e.g. businesses, hospitals, government institutions, and city services | Phishing, deleting shadow copies, encryption of networks. | $150 million |
| Cl0p | 2019 | Large organizations e.g. financial services, healthcare, manufacturing, and media | Quadruple extortion, DDoS attacks, supply-chain attacks. | $500 million |
| LockBit | 2019 | Financial services, healthcare, manufacturing, education, energy, government, and transportation | Double extortion, phishing, Remote Desktop Protocol (RDP), lateral movement. | $1 billion |
| Akira | 2023 | Businesses and critical infrastructure entities | Lateral movement, exploit remote access vulnerabilities, data encryption. | $42 million |
| Lynx | 2024 | Healthcare, finance, education, real estate, manufacturing, and logistics | Double extortion, phishing, encryption, deleting shadow copies. | over $1 million |
Ryuk vs. LockBit comparison
Although Ryuk and LockBit are both forms of ransomware, their methods of operation differ significantly.
Ryuk usually targets larger organizations, such as medical and government institutions, to extract higher payloads. Ryuk‘s encryption methods are slower than encryption from LockBit, however, the attacks can be more devastating as the malware focuses on erasing backups and spreading within networks to maximize damage.
In contrast, LockBit functions as a Ransomware-as-a-Service (RaaS) solution, readily available for cybercriminals to exploit in extorting victims. It is capable of encrypting files in under 4 minutes and employs double extortion strategies to maximize pressure on its targets.
Who is behind Ryuk ransomware?
Initially thought to be linked to North Korean, Ryuk ransomware was discovered to be associated with a Russian cybercriminal organization, Wizard Spider. It later became suspected that Wizard Spider operated Ryuk activities from a smaller cell in the organization named Grim Spider.
The ransomware group’s name is unique—Ryuk originally comes from the name of a character from the popular manga and anime series Death Note. In the story, Ryuk is a death god driven to targeted killings.
Ryuk primarily targets victims in the USA and Canada, with 75% of attacks going towards the American healthcare sector.
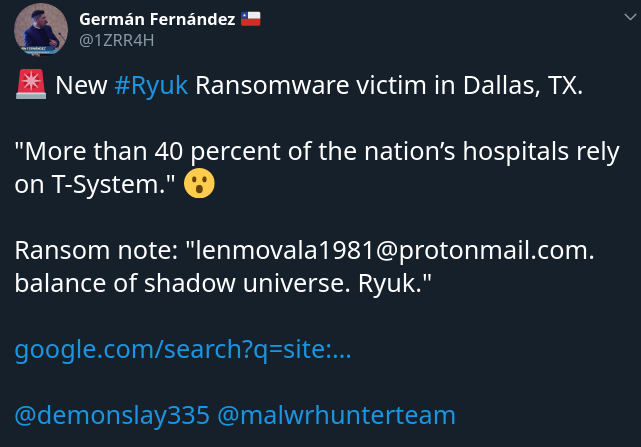
In Texas, security researchers found that platforms managed by T-Systems were down, showing the ransomware infection had spread to public segments such as DMZ, extranet, and helpdesk. The company affected by the attack provides services for more than 1,900 emergency care facilities, with more than 40% of America‘s hospitals relying on T-Systems.
How Ryuk ransomware works
Ryuk ransomware attacks perform their initial compromise through TrickBot, a recognised banking Trojan malware or backdoor vulnerabilities distributed by phishing emails. Microsoft categorizes Ryuk as a human-operated ransomware operation. Threat actors move laterally through systems to perform reconnaissance, steal sensitive information, and exfiltrate data.
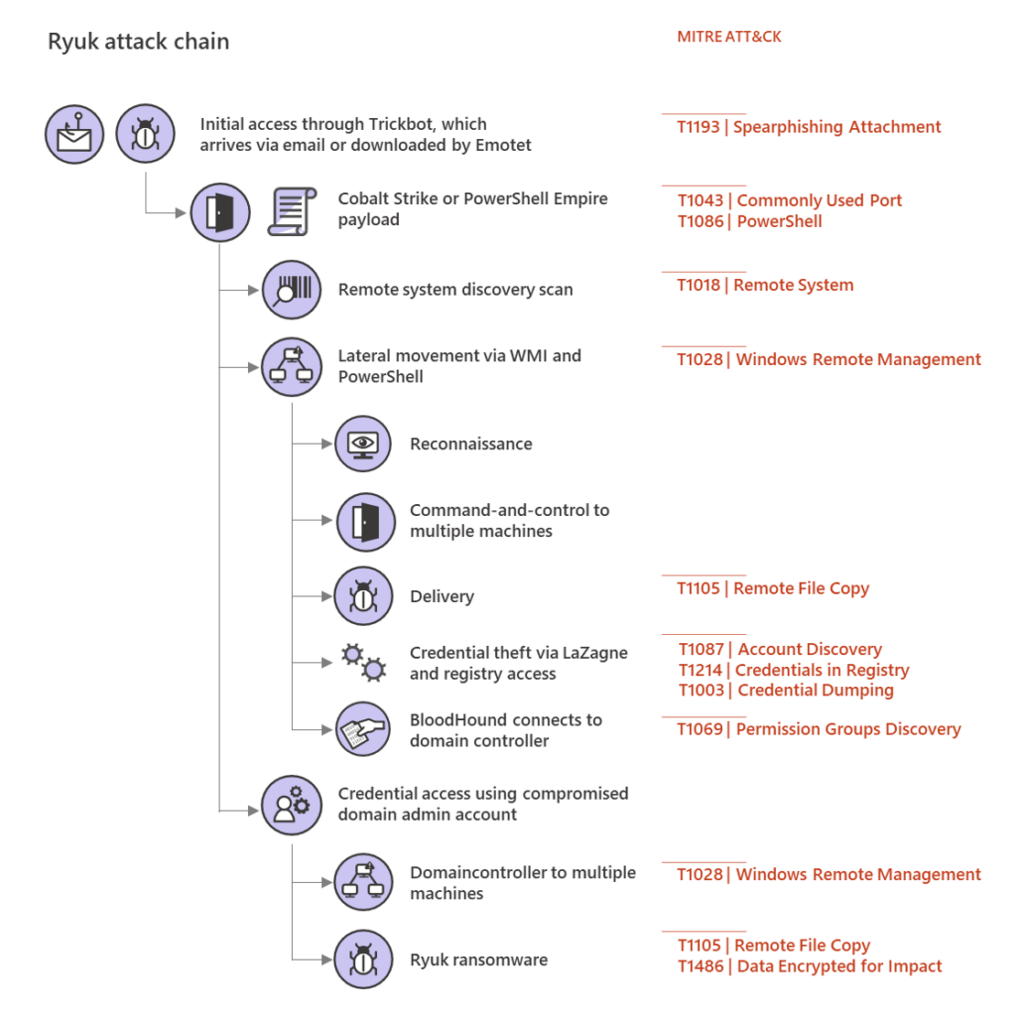
A diagram of the Ryuk attack chain from Microsoft. Source.
When a user clicks on a malicious link or attachment, ransomware is installed onto a victim‘s device. Ryuk‘s ransomware encrypts files on the victim’s device using a strong encryption algorithm—a combination of RSA-2048 and AES-256. Ryuk‘s encryption also avoids any processes or disk locations that may slow down or interfere with the encryption.

From this vulnerability, the ransomware can spread through internal systems and networks. Ryuk functions as a late-stage payload, delivered by widely used frameworks like Cobalt Strike, Emotet, GrimAgent, or TrickBot. The ransomware payload is spread across the target environment to extort maximum funds from the business. Volume Shadow copies (VSS) are also deleted to inhibit full system recovery.
Ryuk launches attack on a Department of Defense contractor…
In January 2020, Ryuk ransomware attacked the systems of a U.S. government contractor, Electronic Warfare Associates (EWA)—a client of the Department of Homeland Security, Department of Defense, and Department of Justice.
The attack was suspected to have originated from a phishing email, and data exfiltration was the goal of the attack.
US police department hit with Ryuk ransomware attack…
In July 2019, the New Bedford Police Department was hit by Ryuk ransomware, infecting a network of 200 systems and over 3,800 laptops. The malware encrypted data stored on servers and 153 workstations and blocked access to the data.
Ryuk threat actors demanded a $5.3 million ransom; however, no ransom was ever exchanged, and the extent of the internal damage is unknown.
How does Ryuk evade detection?
Ryuk’s ability to evade detection can be attributed to a relaxed cybersecurity posture within organizations. Microsoft researchers noted that targets lacked firewall protection, had weak password security, no multifactor authentication (MFA), and non-randomized local admin passwords.
In the affected organizations, there was a prevailing belief that implementing robust security measures would compromise performance and disrupt operational workflows, ultimately leaving them exposed to threats.
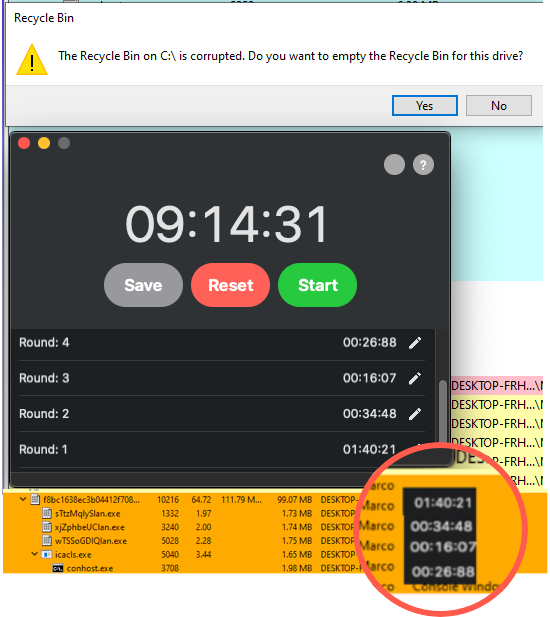
Another factor contributing to Ryuk’s ability to evade detection is its rapid encryption of files and data. Ryuk has been shown in one test to have encrypted 100,000 files, totaling 53GB, in 14 minutes and 30 seconds.
What‘s Ryuk’s ransom model?
Ryuk‘s ransomware model evolved from scattered wire fraud to targeting larger companies and institutions. Threat actors go after organizations with critical assets that are more likely to pay, also called “Big Game Hunting”.
Ryuk operates by collecting enough leverage on their victims before asking for demands. Once the threat actors have the data needed, a ransom note is deployed.
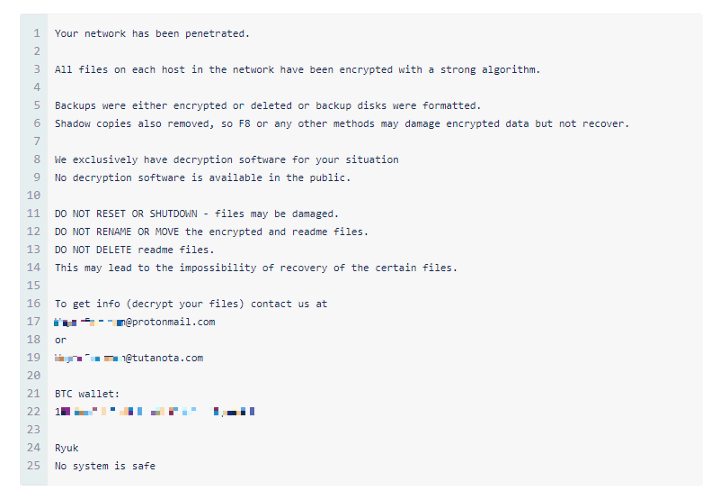
Ryuk ransomware has demanded ransoms ranging from $100,000 to $500,000, typically paid in Bitcoin to conceal the transaction. In one case, the FBI reported that a Ryuk ransom payment amounted to $5 million worth of Bitcoin.
Why is Ryuk still a top threat in 2025?
The looming threat of malware such as Ryuk and other ransomware families continues to be persistent in 2025.
The World Economic Forum found in 2024 that 49% of public-sector organizations lack the necessary talent to meet their cybersecurity goals. Globally, organizations of all sizes are struggling to keep up with the innovative tactics of threat actors.

Microsoft‘s findings show that organizations can implement strategies to stop fast-spreading malware like Ryuk. By removing or hindering the ability of threat actors to move laterally, the network is more resilient against all kinds of cyberattacks.
How can organizations mitigate Ryuk attacks?
Given the resilience of the new Ryuk variant, proactive prevention is more effective than mitigation after an attack.
According to the CISA, here‘s what you can do to begin protecting your organization:
- Update systems regularly: Patch operating systems, software, and firmware as soon as manufacturers release updates. Threat actors often exploit known vulnerabilities from previous versions, leaving you exposed to an attack.
- Regularly change passwords: Stay secure across network systems and accounts by updating and periodically changing passwords to prevent unauthorized access.
- Check configurations on all OS: Check the configurations for every operating system version to prevent local administration accounts from being disabled during an attack.
- Enable MFA: Implementing multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of verification, significantly reducing the risk of unauthorized access to systems and sensitive data.
- Restrict access: Disable unused remote access credentials, unused Remote Desktop Protocol (RDP) ports, and monitor remote access and RDP logs for suspicious activity. Catching suspicious entries early is key to preventing malware from spreading.
- Zero-trust architecture: Audit user accounts with administrative privileges and configure access controls with least privilege in mind.
- Implement network segmentation: Segmenting networks helps keep sensitive data safe if a system is infiltrated. For example, place sensitive data on a different server than the email environment in case of a phishing attack.
- Train users to put safety first: Most ransomware attackers gain a foothold through social engineering. Ensure that employees know how to identify suspicious emails and attachments, how to report suspicious activity, and how to respond in case of a cyberattack.
Detect Ryuk ransomware early with CybelAngel
CybelAngel is an all-in-one tool that can help you stay ahead of ransomware attacks with innovative solutions:
- Data breach prevention: Prevent unauthorized access and limit lateral movement to stop Ryuk ransomware attacks in their tracks.
- Account takeover prevention: Stop your company credentials from being distributed on the dark web, preventing future attacks.
- Remediation services: Reduce downtime by up to 85% to get daily business running again after a Ryuk attack.
Ready to get started?
