Our Investigation into Quishing Attacks [Threat Note]

Table of contents
This blog is a summary of our latest threat note, “When QR Codes Become Weapons” which is available for all our clients to read in the CybelAngel portal. Interested in reading this report as a non client? Get in touch with us to access this content.
What are ‘quishing’ attacks?
QR code phishing, more commonly known as “quishing, drives QR code users into visiting malicious websites or downloading harmful software. It is a stealthy way for scammers to strike without the intended user realizing it. Just as legitimate QR codes are becoming a fast favourite (QR code scans reached 26.95 million last year,a 433% increase on 2021), cybercriminals have found their endless possibilities rather tempting. Now, they represent an easy path to create and distribute malicious content.
Our new threat note looks at how unsuspecting victims are lured and targeted via these more subtle phishing campaigns. Hackers have developed subtle means to distribute this threat source. Telegram groups are now disseminating phishing kits hosted on platforms like GitHub and share QR code phishing tactics to help criminals better deceive and scam victims, making these tools and techniques widely accessible. Similarly phishing kits are also available for free via the dark web. We take a look at how-skilled attackers are able to leverage fake QR codes to devastating consequences.
An outline of how hackers are weaponizing QR codes
QR codes have come a long way since their creation in Japanese auto factories in 1994. Originally they were designed to store more data than the barcodes used. Today they are a go-to bridge between our physical and digital worlds. During the recent COVID-19 pandemic, QR codes were adopted en masse as a quick response to sharing information safely.
Now scammers have graduated to utilizing “Phishing as a Service” (PaaS) platforms. These platforms provide ready-made phishing kits and resources.
Here are some examples of these phishing kits:
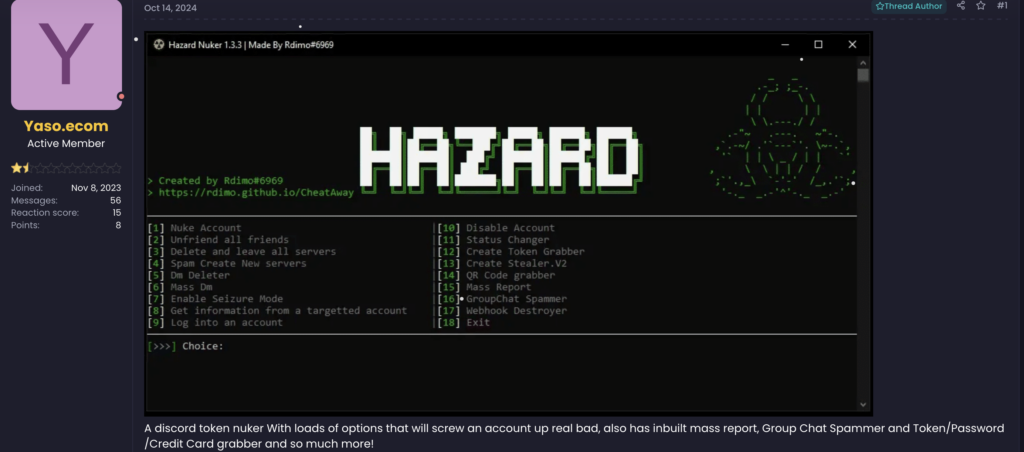
RipperSec, a notorious player in cybercrime circles, has been spreading phishing techniques through encrypted channels like Telegram. They recently touted a clever scam involving water bottles with QR codes supposedly worth RM200. Unsuspecting victims who scan these codes end up on a fake site that steals their personal data. In a similar vein, Silent Cyber Force, another Telegram-based group, has been sharing an array of phishing tools on Github, including QR code jacking methods. These tools are part of advanced campaigns aimed at outsmarting current security protocols.
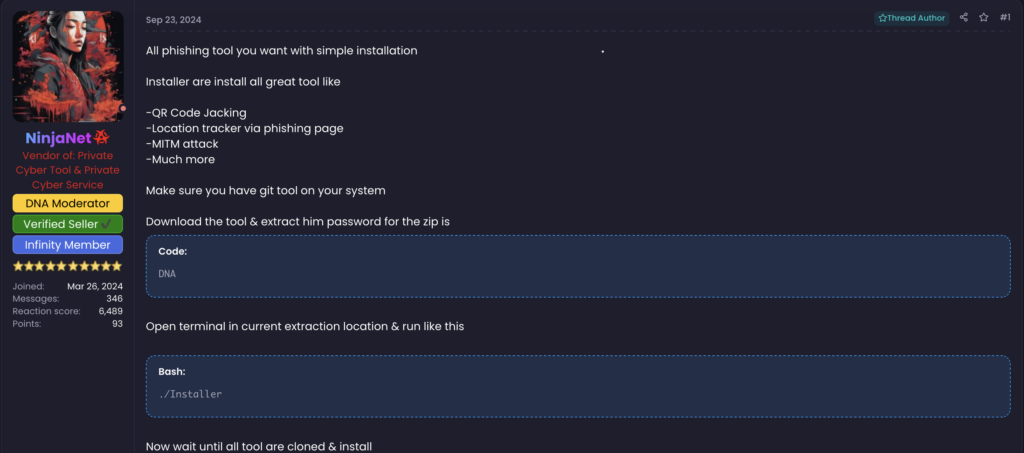
We detail more of these strategies is, only in our threat note
How does QR code phishing evade security solutions?
When deploying these scams, cybercriminals are also increasingly using ASCII-based designs to make detection by cybersecurity tools a challenge. ASCII-based QR codes can evade security tools employing OCR (Optical Character Recognition) because these tools fail to recognize them as images. These codes are treated instead as a plain text, allowing them to pass through security measures without detection. It is important to note that the difference between a standard QR code and a phishing QR code is minimal (Executives are targeted x42 times more than any other employee).
What is more is that cybercriminals frequently impersonate well regarded brands, like Microsoft, to increase the likelihood of success. For example Black Basta a high-profile ransomware group uses this tactic by deploying Microsoft Teams chat messages as a means of gaining initial access to login credentials. They exploit paths like email security-related updates to bypass user skepticism and create a sense of urgency to gain access to sensitive information, like contact information and financial information.
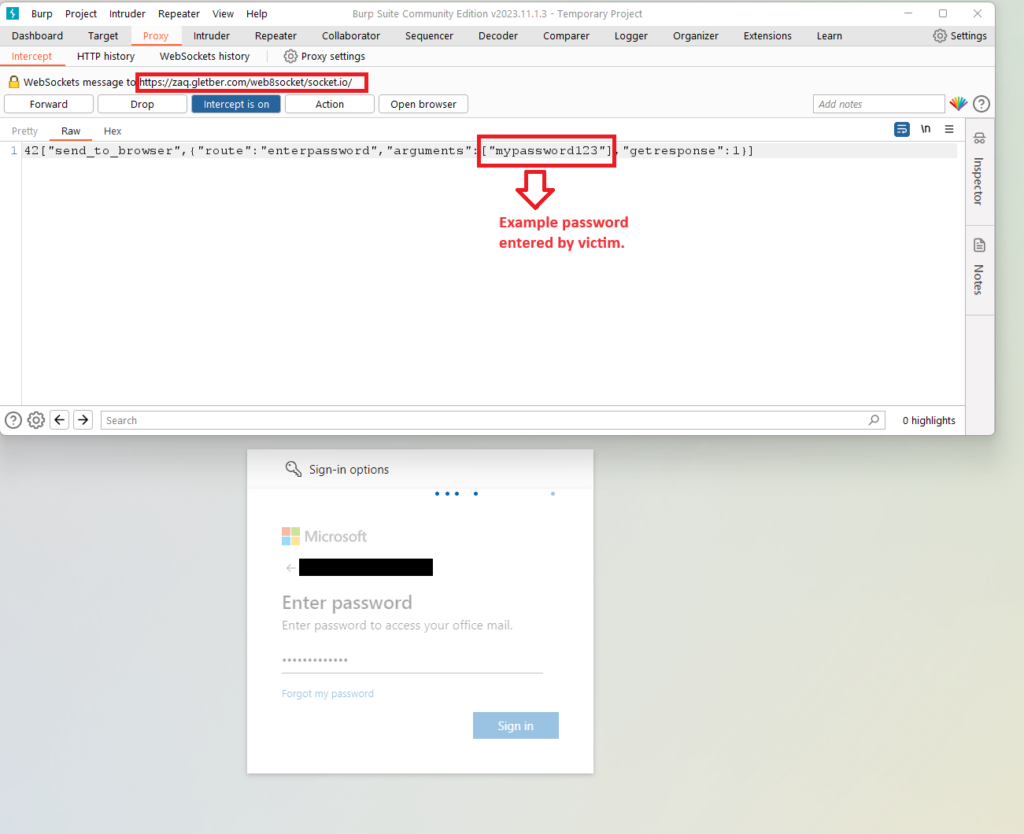
Within this threat note, our analysts review more use cases to share practical social engineering examples used by threat actors to boost your security awareness and protect your sensitive data from scammers.
What can be done to combat quishing?
Is there a recommended way to sidestep these threats? Are any notable patterns detectable even if QR codes present as normal? What security measures are advised for businesses?
Our analysts have created proactive recommendations within this note so that you can avoid deadly QR code scams moving forward.
The full list of topics covered
Within this threat note there are four main areas of focus. You’ll find analysis and comments from our CyberOps Analytical Team. As always, the report contains recommendations to stay clear of QR related phishing attacks.
The main focus areas of this report:
I. Understanding QR code phishing
II. QR Code exploitation techniques
|III. A review of the impacts of sustained quishing attacks
IV: A rundown of new trends and mitigation strategies to avoid cyberattacks
Good to know
In this threat note, our analysts also explore why cybercriminals on the dark web are offering phishing kits for free. CybelAngel monitors various platforms for potential threats, including Telegram. Within our Dark Web Monitoring service, we scan TOR, I2P, Discord, Telegram and IRC among other platforms.
Understand the full dangers of malicious QR codes, only in our latest threat note
Who are the key targets of these deadly malicious links? What is driving a surge in these malware scams? What are the recommendations to enforce from today? Find the answers to these questions, and more, only within our threat note blog.
Not a CybelAngel client? Dive into the full report by getting in touch with us.
If you don’t want to stop reading check out our latest analysis on RansomHub, “RansomHub: A Rising Danger in the RaaS Market.”

