Phishing & Spear Phishing Attacks on the Rise
Table of contents
It has happened to all of us. You receive an email from your bank asking you to click on a link to “update your account.” The displayed page informs you that due to unusual activity on your account, the bank is taking the following security measures — because IT security is their top priority. The bank has locked your access to the bank’s website; however, regaining access will be a quick process and is designed to protect you and your account(s). Sure, why not?
Step One: Validate your personal information by confirming your personal data by completing the following form including: name, address, social security, phone number, etc.
Step Two: Provide your credit card number, expiration date, and CVV.
Step Three: Now, you can now access the legitimate website of your favorite bank. “Click here.”
The Phishing Trap
Given this is a blog, you likely saw this as a phishing trap, but unfortunately it is quite successful with victims less aware of cybercrime. This attack is one designed to provide the attacker with your personal data and access to your financial accounts. Before thinking it will never happen to you, 61% of American could not identify a fraudulent website. This is particularly concerning given “Phishing attacks increased 35o% amid COVID-19 Quarantine.” Let’s talk about phishing attacks, and why it is so hard to prevent. As the previous scenario demonstrates the aspects of a phishing attack are fairly straightforward.
- It exploits a user’s trust in an institution, brand, or individual. The example delivers a fake warning from a trusted bank.
- It also engenders trust with language about protecting the user and their accounts. What better way to ensure the victim will follow the instructions?
- It targets as many users as possible. By increasing the breadth of the phish, the criminal increases the number of victims and their revenue opportunities.
- Most importantly, it aims to acquire confidential information from the victim: traditionally a password or the code of your credit card. It could be anything you are supposed to keep secret… and that a bank would never ask.
 A phishing attack gambles on the law of large numbers. The more emails sent, the more targets, and the higher probability someone will provide their sensitive information. Such low-tech attacks often prove to be enough to deceive an unsuspecting user, but not a well-informed individual. These individuals are not likely to trust the phishing story, unless the scheme is thoroughly researched and well-presented — a spear phish. (Note: When referring to a high-level target, such as a CXO, the official spear phishing term is “whaling” — because it’s a big fish. Got it ? But seriously, who really uses this term?) As a general rule of thumb, the level of attack preparation is inversely proportional to the number of targets.
A phishing attack gambles on the law of large numbers. The more emails sent, the more targets, and the higher probability someone will provide their sensitive information. Such low-tech attacks often prove to be enough to deceive an unsuspecting user, but not a well-informed individual. These individuals are not likely to trust the phishing story, unless the scheme is thoroughly researched and well-presented — a spear phish. (Note: When referring to a high-level target, such as a CXO, the official spear phishing term is “whaling” — because it’s a big fish. Got it ? But seriously, who really uses this term?) As a general rule of thumb, the level of attack preparation is inversely proportional to the number of targets. 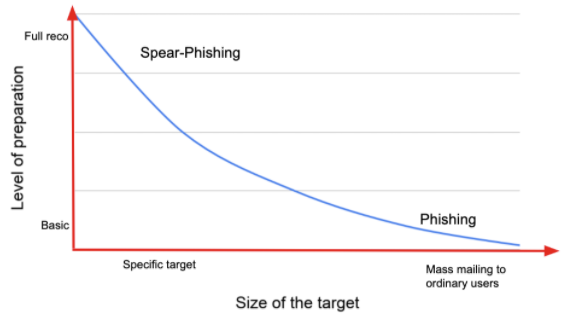 The goal of spear phishing is first to gain the trust of the victim and then to steal the victim’s sensitive data. The cyber pirate needs to know everything he/she can about his target: profession, title, habits, acquaintances, current company, and so on. A common scenario might include a phone call from a new employee, who is filling in for a colleague who is on holiday. The new employee introduces themselves and tells you the name of the employee they are backfilling. (Note: Information about time away from the office can be easily obtained on social media channels or even an “Out of Office” message.) The new employee says they need access to a specific customer or financial file to complete a task for their temporary boss. The new employee seems overwhelmed, and you want to help. The guy knows so many details, the request must be legitimate. You are willing to help newcomers, because you are a good guy, aren’t you? Every detail is useful in creating a credible story that will convince the target to share confidential information. It often requires social engineering techniques, ultimately leading to the malware delivery. It almost always takes time, but the bad guys are patient. And the rewards match the effort. Recently the Lazarus Group (aka Hidden Cobra) used a spear-phishing attack on an employee of a cryptocurrency exchange with a fake job offer in order to plant malware and steal a “substantial” amount of cryptocurrency from the targeted exchange, according to security firm F-Secure. This is not a new technique for the Lazarus Group, as they have been involved in several other thefts from banks and exchanges, including the theft of $81 million from Bangladesh Bank in 2016. Yet another group of cyber criminals, China-based APT have been sending organizations spear phishing emails that distribute intelligence-collecting malware named Sepulcher. According to ThreatPost, these attacks were first seen earlier this year targeting European legislative bodies and more recently Tibetan dissidents. As visualized in the previous graph, spear phishing campaigns are most often highly targeted against a specific agenda. Sometimes the threat actors will even impersonate a “whale.” In this infamous CEO impersonation fraud example, the CFO emails a junior-level member of the team instructing him to wire transfer a credit to a key client (the attacker got the name of the client from your website). She would do it herself, but she is out-of-the-office and headed into a meeting. The CFO writes that it is imperative the transfer is made immediately to retain this customer. Furthermore, she states to email her with proof of the wire transfer as soon as it is made. Our junior accountant doesn’t want to be the reason the company loses a marquis account and embarrass his CFO. So, he makes the transfer and emails the proof to the ‘fake’ CFO. Spear phishing scams like the one described are on the rise with the workforce shifting to home offices. The APWG report states that in the second quarter of 2020 the average amount siphoned from enterprises through wire transfers resulting from a BEC (Business Email Compromise) incident rose to $80,183, up from $54,000 in the first quarter of 2019.
The goal of spear phishing is first to gain the trust of the victim and then to steal the victim’s sensitive data. The cyber pirate needs to know everything he/she can about his target: profession, title, habits, acquaintances, current company, and so on. A common scenario might include a phone call from a new employee, who is filling in for a colleague who is on holiday. The new employee introduces themselves and tells you the name of the employee they are backfilling. (Note: Information about time away from the office can be easily obtained on social media channels or even an “Out of Office” message.) The new employee says they need access to a specific customer or financial file to complete a task for their temporary boss. The new employee seems overwhelmed, and you want to help. The guy knows so many details, the request must be legitimate. You are willing to help newcomers, because you are a good guy, aren’t you? Every detail is useful in creating a credible story that will convince the target to share confidential information. It often requires social engineering techniques, ultimately leading to the malware delivery. It almost always takes time, but the bad guys are patient. And the rewards match the effort. Recently the Lazarus Group (aka Hidden Cobra) used a spear-phishing attack on an employee of a cryptocurrency exchange with a fake job offer in order to plant malware and steal a “substantial” amount of cryptocurrency from the targeted exchange, according to security firm F-Secure. This is not a new technique for the Lazarus Group, as they have been involved in several other thefts from banks and exchanges, including the theft of $81 million from Bangladesh Bank in 2016. Yet another group of cyber criminals, China-based APT have been sending organizations spear phishing emails that distribute intelligence-collecting malware named Sepulcher. According to ThreatPost, these attacks were first seen earlier this year targeting European legislative bodies and more recently Tibetan dissidents. As visualized in the previous graph, spear phishing campaigns are most often highly targeted against a specific agenda. Sometimes the threat actors will even impersonate a “whale.” In this infamous CEO impersonation fraud example, the CFO emails a junior-level member of the team instructing him to wire transfer a credit to a key client (the attacker got the name of the client from your website). She would do it herself, but she is out-of-the-office and headed into a meeting. The CFO writes that it is imperative the transfer is made immediately to retain this customer. Furthermore, she states to email her with proof of the wire transfer as soon as it is made. Our junior accountant doesn’t want to be the reason the company loses a marquis account and embarrass his CFO. So, he makes the transfer and emails the proof to the ‘fake’ CFO. Spear phishing scams like the one described are on the rise with the workforce shifting to home offices. The APWG report states that in the second quarter of 2020 the average amount siphoned from enterprises through wire transfers resulting from a BEC (Business Email Compromise) incident rose to $80,183, up from $54,000 in the first quarter of 2019.
How can we prevent phishing and spear phishing losses?
Unfortunately, there is no comprehensive fix when it comes to phishing attacks. From a technology perspective, you can set rules to deny traffic from malicious websites to protect your colleagues. However, it will not prevent attacks targeting people outside your own network, like your customers, vendors, or suppliers, who may have access to sensitive data beyond the protection of your network. You can also contact your company’s security or fraud team about a suspicious site. They may, in turn, contact the appropriate registrar to contest the malicious website and request it be taken down. These actions will have varying levels of success, as malicious intent is not always easy to prove before a phishing email is sent, and take down regulations vary from country to country. The most successful option to fight phishing remains to train the users:
- Never click on a link sent by an unknown person.
- Always check the URL before clicking.
- Never give your password to anyone, whatever the reason, and especially not on the phone. (Note: Phone attacks like this are called “vishing.” This attack method is on the rise.)
- Remind your customers and your employees what are and what are not legitimate email requests.
- Use multi-factor authentication to mitigate the risk even if your credentials are compromised.
- Routinely quiz employees to keep them sharp in spotting potential phishing or spear phishing scams. One such quiz can be found HERE.
Apart from these good practices, seeing the threat coming can be even more effective than some of the previously discussed actions. CybelAngel provides its customers with cutting-edge technology that matches your assets against thousands of domains and subdomains to detect potentially malicious new domains. Our capability goes way beyond this simple detection. By scanning servers, databases and cloud-based content left open by negligence, CybelAngel protects companies from sensitive information leaks that can prove to be gold mines for attackers in the reconnaissance phase of a spear-phishing attack. If you want to learn more about how CybelAngel can protect you and your company, CLICK HERE.

