How to Mitigate the Risk From Phishing Attacks

Table of contents
Data breaches often start with phishing attacks
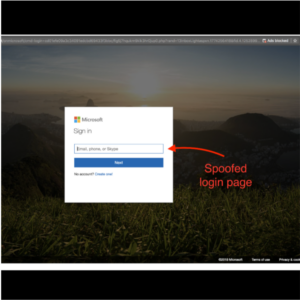 CEOs and decision makers are a popular target for phishing attacks. When executives are faced with spoofed screens like the Microsoft 365 log-in screen, IT administrators have their hands full trying to stop the damage before it’s too late. The truth is, phishing attacks can dramatically increase workloads for IT administrators. While your IT team is busy fending off phishing attacks, cybercriminals are busy stealing sensitive data. In 2020, 45% of all phishing emails sent were Microsoft-themed. When cybercriminals gain access to an organization via Office 365 credentials, they appear to be legitimate users and go undetected. Data breaches often start with phishing attacks. CEOs and decision makers are popular targets for phishing attacks. These attacks can be some of the worst for overworked IT teams to face. According to the latest Verizon Data Breach Investigations Report, stolen credentials are the top hacking tactic for the fourth consecutive year. If this isn’t enough to get the attention of cybersecurity professionals, the report further states that 37% of all data breaches are the result of used or stolen credentials.
CEOs and decision makers are a popular target for phishing attacks. When executives are faced with spoofed screens like the Microsoft 365 log-in screen, IT administrators have their hands full trying to stop the damage before it’s too late. The truth is, phishing attacks can dramatically increase workloads for IT administrators. While your IT team is busy fending off phishing attacks, cybercriminals are busy stealing sensitive data. In 2020, 45% of all phishing emails sent were Microsoft-themed. When cybercriminals gain access to an organization via Office 365 credentials, they appear to be legitimate users and go undetected. Data breaches often start with phishing attacks. CEOs and decision makers are popular targets for phishing attacks. These attacks can be some of the worst for overworked IT teams to face. According to the latest Verizon Data Breach Investigations Report, stolen credentials are the top hacking tactic for the fourth consecutive year. If this isn’t enough to get the attention of cybersecurity professionals, the report further states that 37% of all data breaches are the result of used or stolen credentials.
Security leaders lack faith in cyber preparedness
Nearly 80% of senior IT and IT security leaders believe that their organization lacks sufficient protection against cyberattacks, according to a new survey from IDG Research Services. There is a lack of cybersecurity confidence this year despite increased investment last year made by many organizations to improve IT security to deal with distributed IT and employees working remotely. The lack of confidence in cybersecurity posture, prompted 91% of respondents to increase their cybersecurity budgets for 2021. From this same IDG Research survey, only 57% of respondents conducted a risk assessment for data security in 2020. If you are in the same position as the majority of respondents who need a risk assessment for data security and lack faith in their cyber preparedness, see the below steps to take to mitigate the risk of phishing attack.
Steps to mitigate the risk of phishing attack
 Where does your organization stand against phishing attempts? As cybercriminals increase their sophistication in attacks, organizations can take the following steps to mitigate the risk of phishing attacks. User education and training. Even executives get fooled by fake Microsoft login screens. Ongoing employee education with the latest phishing examples can help your workforce recognize and avoid current threats. Password reset policies. Automated password reset reminders should be in place. Password policy should reject previously used passwords, which is a popular method used by cyber attackers. A survey by Google identified that 65 percent of people use the same password for multiple or all accounts. These statistics validate the magnitude of the problem and the need for organizations to take action to prevent credential-stuffing attacks from succeeding. Login verification via multi-factor authentication (MFA). Cybersecurity pros know that MFA is a security enhancement that allows a user to present two pieces of evidence in order to log into an account. If your organization is not using MFA, now is the time to get with it. Effective monitoring of devices and networks. Migration to cloud and remote access to data means that all devices and network access need to be continuously monitored for leaking of sensitive data. When even senior executives can be fooled by phishing attacks, organizations turn to CybelAngel to defend against phishing attacks and prevent account takeovers. If your IT administrators are spending too much time defending against phishing attacks, there is a better way. Enterprises around the world rely on CybelAngel to detect stolen credentials from phishing and other attacks, and so can you.
Where does your organization stand against phishing attempts? As cybercriminals increase their sophistication in attacks, organizations can take the following steps to mitigate the risk of phishing attacks. User education and training. Even executives get fooled by fake Microsoft login screens. Ongoing employee education with the latest phishing examples can help your workforce recognize and avoid current threats. Password reset policies. Automated password reset reminders should be in place. Password policy should reject previously used passwords, which is a popular method used by cyber attackers. A survey by Google identified that 65 percent of people use the same password for multiple or all accounts. These statistics validate the magnitude of the problem and the need for organizations to take action to prevent credential-stuffing attacks from succeeding. Login verification via multi-factor authentication (MFA). Cybersecurity pros know that MFA is a security enhancement that allows a user to present two pieces of evidence in order to log into an account. If your organization is not using MFA, now is the time to get with it. Effective monitoring of devices and networks. Migration to cloud and remote access to data means that all devices and network access need to be continuously monitored for leaking of sensitive data. When even senior executives can be fooled by phishing attacks, organizations turn to CybelAngel to defend against phishing attacks and prevent account takeovers. If your IT administrators are spending too much time defending against phishing attacks, there is a better way. Enterprises around the world rely on CybelAngel to detect stolen credentials from phishing and other attacks, and so can you.
Get your complimentary risk assessment of your data that may already be found in the wild. CybelAngel secures your digital world.

