20 Common Types of Malware: What They Do and How to Avoid Them

Table of contents
Malware isn’t just a nuisance. It’s a moving target. One day, it’s a fake invoice in your inbox. Next, it’s ransomware that’s locked down your entire network. And sometimes there are several different types of malware attacks working together at once.
No two malware attacks look the same. But they all start with familiar building blocks. Let’s explore 20 of the most common types of malware. You’ll learn what they do, how they’re used, and how to avoid them before they get a foothold.
1. Ransomware
Ransomware attacks are malicious software that encrypt data and and withhold the decryption key until a ransom is paid, often with threats to leak stolen files.
- How ransomware works: Cybercriminals usually gain access through phishing emails, exposed RDP ports, or vulnerable internet-facing assets. Once inside, they move laterally, escalate privileges, and identify valuable systems to encrypt.
- How to stop it: CISA’s ransomware guide recommends keeping backups of critical data, implementing a zero-trust model to your computer networks, regularly patching software, limiting remote access, and adding phishing-resistant MFA for all services.
- Ransomware examples: There are many emerging ransomware groups to be aware of, including Lynx, Cl0p, Akira, RansomHub, and LockBit. These offer ransomware-as-a-service (RaaS), allowing anyone to run cyberattacks with their plug-and-play solutions.
2. Spyware
Spyware is a malicious program designed to monitor user activity without consent, capturing sensitive data like keystrokes, passwords, browsing history, and even camera or microphone input.
- How spyware works: It’s often bundled with legitimate-looking apps or delivered via phishing links. Once installed, it silently collects sensitive information. Some variants are used for targeted surveillance, while others steal credentials for resale.
- How to stop it: There are some programs that block spyware. You can also use endpoint detection tools, enforce strong permissions management, and educate your team on suspicious downloads and enforce mobile device security controls.
- Spyware example: The Pegasus Project, led by a consortium of journalists and Amnesty International, revealed that a type of spyware—developed by NSO Group—was used to secretly target journalists, activists, and political figures worldwide.
A video from Amnesty International explaining the Pegasus spyware scandal. Source.
3. Trojans
Like the famous Greek myth of the Trojan horse, computer trojans disguise themselves as legitimate software or files but contain hidden malicious code designed to give attackers access or control.
- How trojans work: They’re often delivered through email attachments, fake software downloads, or poisoned ads. Once executed, they can install backdoors, steal data, or drop additional malware onto the system.
- How to stop them: Use email filtering, apply sandboxing for unknown files, and block unverified software from running. Apply the principle of least privilege to limit what malicious code can access.
- Trojan example: Emotet is a Trojan that downloads or drops other malware onto computer systems after a malicious link is clicked.
4. Worms
Worms are self-replicating malware infection that spread across networks without any user interaction, often causing widespread disruption.
- How worms work: They exploit unpatched vulnerabilities or weak credentials to move laterally through systems. Unlike trojans, they don’t need to trick users. They move on their own, scanning for more targets.
- How to stop them: Prioritize patching, isolate network segments, and monitor unusual internal traffic. You should also use intrusion detection systems to catch unauthorized access and rapid lateral movement.
- Worm example: In 2017, the WannaCry worm used the EternalBlue exploit to spread automatically, infecting over 300,000 machines in just a few days.
5. Rootkits
Rootkits are stealthy tools that hide deep inside a system to give attackers long-term, hidden access, often without triggering alerts.
- How rootkits work: They embed themselves in the operating system or firmware, masking malicious activity like keystroke logging or file tampering. They’re difficult to detect and even harder to remove.
- How to stop them: Monitor for unusual system behavior, and run kernel-level integrity checks. Bear in mind that rebuilding infected computer systems from known-good backups may be the only safe way to clean a rootkit infection.
- Rootkit example: In 2005, Sony BMG included a rootkit in its music CDs to enforce copy protection, but it also exposed users to serious security risks. Attackers quickly exploited it to hide malware on affected systems.
Explainer video documentary on the Sony BMG rootkit scandal. Source.
6. Keyloggers
Keyloggers record every keystroke a user makes, capturing passwords, messages, credit card numbers, and other sensitive data.
- How keyloggers work: They can be installed through phishing emails, malicious downloads, or bundled with trojans. Some run in the background quietly; others use hardware plugged directly into a device.
- How to stop them: Use endpoint protection with behavioral analysis, restrict admin privileges, and enable two-factor authentication to reduce the impact of stolen credentials.
- Keylogger example: Olympic Vision is a low-cost keylogger sold for $25 on the black market and has been used in business email compromise (BEC) attacks in the US, the Middle East, and Asia.
7. Fileless malware
Fileless malware doesn’t rely on traditional files to infect a system. Instead, it runs in memory, making it much harder to detect and remove.
- How fileless malware works: It often abuses legitimate tools to execute malicious commands. Since it leaves little or no footprint on disk, it can bypass many antivirus tools and firewalls.
- How to stop it: Your security team should monitor script usage and memory activity, restrict access to admin tools, and log command-line behavior across endpoints.
- Fileless malware example: The Astaroth malware campaign abused built-in Windows utilities to hide its activity. This helped it avoid detection while stealing credentials and system information.
8. Adware
Adware is a form of malware that floods users with unwanted ads and pop-ups, often redirecting them to malicious sites or tracking their activity without permission.
- How adware works: It’s commonly bundled with free software or browser extensions. Once installed, it can hijack search results, slow down devices, and serve as a gateway for more serious threats.
- How to stop it: Remember to vet all software before installation and restrict browser extension permissions. Regularly scan devices and educate users on the risks of “free” downloads.
- Adware example: Fireball infected over 250 million devices by attaching to legitimate-looking software. It also had the capability to run malicious code, turning it into a potential backdoor.
9. Backdoors
Backdoors are hidden ways into a system that bypass normal authentication, giving attackers ongoing access without being noticed.
- How backdoors work: They’re often installed after an initial compromise or secretly embedded in software during development. Once active, attackers can return at any time to steal data, move laterally, or drop additional malware.
- How to stop them: Monitor outbound traffic for unusual connections and regularly audit code, especially from third-party suppliers. Use threat hunting to spot persistence mechanisms that attackers might leave behind.
- Backdoor example: The SolarWinds supply chain attack inserted a backdoor known as SUNBURST into the Orion software update. This gave cybercriminals access to US government agencies and major companies for months before detection.
10. Botnets
A botnet is a network of infected devices controlled by an attacker, often used to launch large-scale attacks like DDoS, spam campaigns, or credential stuffing.
- How botnets work: Once a device is compromised—often through malware or weak credentials—it quietly connects to a command-and-control server. From there, it follows remote instructions without the user ever knowing.
- How to stop them: Monitor for unusual outbound traffic and block known command-and-control domains. Keep devices patched, and disable unused services to reduce your attack surface.
- Botnet example: The Mirai botnet took control of hundreds of thousands of IoT devices, then used them to launch a massive DDoS attack that knocked major sites like Twitter, Netflix, and Reddit offline in 2016.
11. Logic bombs
Logic bombs are bits of malicious code hidden inside legitimate programs, triggered by specific conditions like a date, action, or system change.
- How logic bombs work: They sit dormant until their trigger is met, then execute—deleting files, corrupting data, or opening a backdoor. Because they’re silent until activated, they’re often planted by insiders or hidden in trusted software.
- How to stop them: Ensure that you review scripts and automation tasks regularly. Use code signing (digital signatures), access controls, and behavior monitoring to catch any tampering early.
- Logic bomb example: In 2002, a disgruntled UBS Systems administrator planted a logic bomb that crashed servers on key trading days, costing the company over $3 million.
12. Polymorphic malware
Polymorphic malware constantly changes its code to avoid detection. This means that each time it infects a new system, it looks slightly different.
- How polymorphic malware works: Polymorphic malware uses encryption and obfuscation to disguise itself from antivirus and signature-based tools. It’s often used in spam campaigns, downloaders, and file-infecting viruses.
- How to stop it: Use behavior-based detection tools that look at what the malware does, not just what it looks like. Make sure you run suspicious files in a sandbox before they reach your endpoints.
- Polymorphic malware example: The Storm Worm spread through fake news headlines and evolved rapidly, making it hard for security tools to keep up, as its code changed every 30 minutes.
13. Ransomworms
Ransomworm malware combines the worst of two threats: ransomware’s encryption with a worm’s ability to spread on its own.
- How ransomworms work: Once inside a network, the ransomworm encrypts files and then scans for other vulnerable systems to infect, no user action needed. The result is fast-moving damage across multiple machines.
- How to stop them: Isolate infected systems quickly to stop the spread. Segment your network and monitor for unusual internal traffic to catch lateral movement early.
- Ransomworm example: NotPetya looked like ransomware but acted more like a wiper, spreading rapidly across corporate networks using stolen credentials and the EternalBlue exploit. Some sources named it the costliest cyber attack in history.
14. Cryptojackers
Cryptojacking malware hijacks your system’s processing power to secretly mine cryptocurrency for attackers.
- How cryptojackers work: It often spreads through malicious websites, browser extensions, or infected software. Once running, it quietly drains CPU and memory, slowing systems down and increasing power usage without alerting the user.
- How to stop them: Monitor for unexpected spikes in resource usage. Use browser security tools and block known cryptomining domains at the network level.
- Cryptojacker example: The Coinhive cryptojacker was embedded into thousands of websites (often without the site owner’s knowledge) and used visitors’ browsers to mine Monero cryptocurrency.
15. Mobile malware
Mobile malware targets smartphones and tablets to steal data, spy on users, or take control of devices.
- How mobile malware works: Mobile malware often hides in fake apps, malicious links, or SMS phishing (smishing). Once installed, it can access contacts, messages, location, and even cameras or microphones.
- How to stop it: Use mobile device management (MDM) tools to enforce app controls. Encourage users to install updates and avoid apps from unofficial stores.
- Mobile malware example: Joker malware snuck into the Google Play Store by hiding in seemingly harmless apps. It was detected in over 1,700 apps before being removed.
16. Malvertising
Malvertising delivers malware through ads—even on trusted websites—without the user ever clicking.
- How malvertising works: Attackers inject harmful code into ad networks, which then serve infected ads to users. Sometimes, just loading the page is enough to trigger an exploit.
- How to stop it: Use reputable ad blockers and filter network traffic at the DNS level. Where possible, block unnecessary scripts and plugins in browsers.
- Malvertising example: The Angler Exploit Kit was delivered through malicious ads on major sites like MSN, silently infecting users with ransomware and banking trojans.
17. RATs (Remote Access Trojans)
RATs give attackers full remote control over an infected device, often without the user knowing. The hacker gets full administrative privilege from anywhere in the world.
- How RATs work: They’re typically spread through social engineering tools, such as phishing attacks, or bundled with other malware. Once active, attackers can browse files, log keystrokes, turn on webcams, and move laterally across a network.
- How to stop them: Watch for unusual outbound connections and restrict admin tool usage. Also, make sure you use EDR to detect signs of remote control and privilege misuse.
- RAT example: Blackshades was a widely sold RAT that let attackers spy on victims through webcams, steal data, and lock files for ransom. It was sold for as little as $40 and used in attacks across more than 100 countries, infecting half a million computers worldwide.
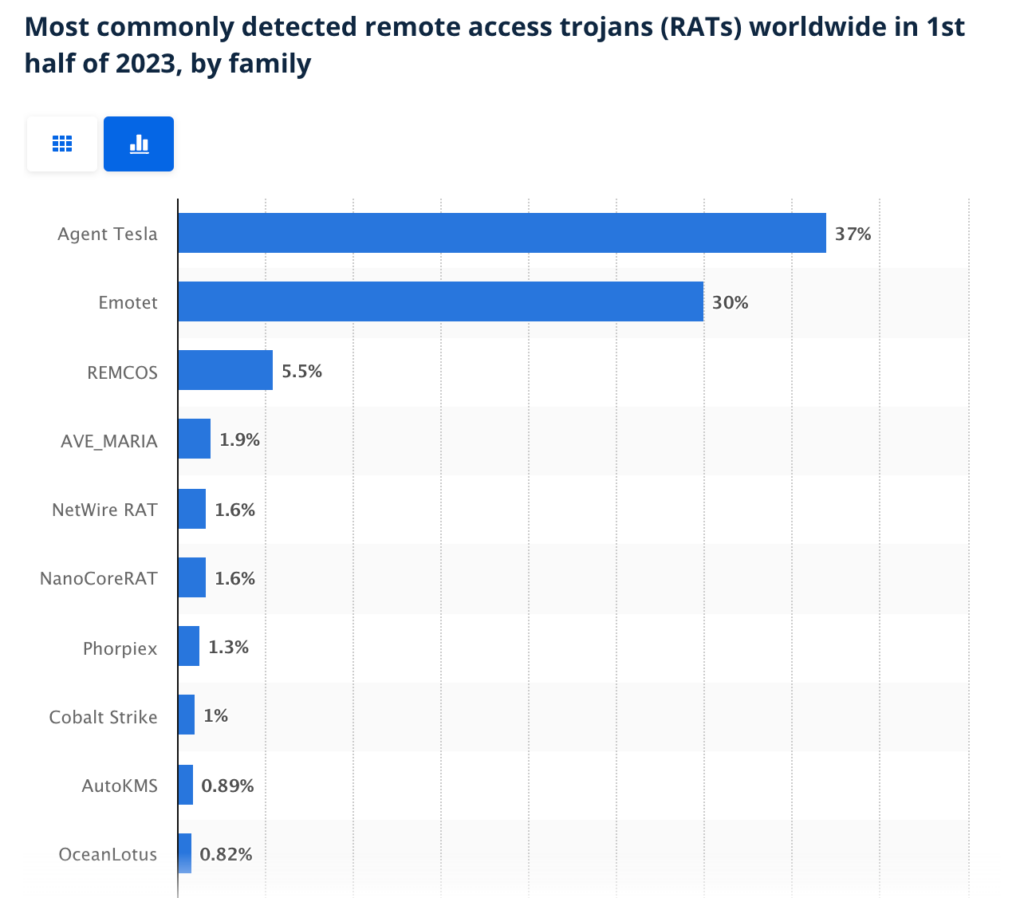
Statista report showing some of the most common RATs. Source.
18. Bootkits
Bootkits are a type of rootkit that infect the system at the bootloader level, before the operating system even loads. This makes them extremely difficult to detect or remove.
- How bootkits work: Bootkits modify the boot process to hide malware and maintain persistence. Some even disable security tools before the OS starts up.
- How to stop them: Enable UEFI Secure Boot to prevent unauthorized changes during startup. Also, ensure you regularly scan firmware and use hardware-level security features where supported.
- Bootkit example: TDL4 (or Alureon) was one of the most advanced bootkits discovered, capable of infecting Windows systems and controlling the boot process. It has been used to infect millions of computers.
19. Macro viruses
Macro viruses hide inside Microsoft Office documents and run malicious code when a user enables macros (one-click commands to run automations). They often spread via email attachments that appear safe at first glance.
- How macro viruses work: Macro viruses are written in the same macro language as software like Excel or Word, and they execute commands automatically when the application is opened. These computer viruses rely heavily on social engineering tactics.
- How to stop them: Disable macros by default and only allow signed macros to run. Train users to be cautious with unexpected attachments, even if they look familiar.
- Macro virus example: The Melissa virus in 1999 spread through Word documents and emailed itself to the top 50 contacts in the victim’s Outlook address book. It caused major disruption to corporate email systems and led to millions in damages.
20. Rogue security software
Rogue security software pretends to be antivirus or cleanup tools but actually installs malware or scams users into paying for fake fixes. It plays on fear, popping up fake warnings to convince users their system is infected.
- How rogue security software works: Once installed, it floods the screen with alerts and urges users to buy the “full version” to remove nonexistent threats. In some cases, it also steals data or disables real security tools.
- How to stop it: Only allow software from trusted sources and use application allowlisting. Teach users to spot fake alerts and report anything suspicious immediately.
- Rogue security software example: SpySheriff (or BraveSentry 2.0) misleads people with fake security alerts, prompting them to buy the program. It’s difficult to remove, and can cause the user’s computer to restart unexpectedly. It can also disable other antivirus software.
Anti-malware cybersecurity best practices
Stopping malware isn’t just about one tool. It’s about putting good habits and strong defences in place across your environment.
Start with the basics. Use strong passwords for all accounts and enforce multi-factor authentication (MFA) wherever possible. This makes it much harder for attackers to log in, even if they manage to steal your credentials.
Keep software and operating systems updated. Many attacks rely on old, unpatched software vulnerabilities. Limit admin privileges so malware can’t spread freely, and back up important data regularly—ideally offline or in immutable storage.
Finally, train your team. Most attacks start with someone clicking the wrong thing. Your best defense is ensuring your employees can recognize cyber threats before they happen.
Final thoughts
Understanding different malware threats isn’t just trivia. It helps you know what to look for and how to respond when something goes wrong.
The next step? Make sure you’ve got visibility.
Most types of malware attacks don’t happen via the front door. They break in through forgotten assets, misconfigured services, and outdated apps you didn’t even know were online.
CybelAngel helps organizations track, prioritize, and secure what’s visible on the outside, and the threat actors who want to target them.
Book a demo to find out about how external threat intelligence could help protect your organization from cybercrime.

