IoT Cybersecurity: Connecting the Dots

Table of contents
There’s a whole hidden ecosystem of devices out there. Smart thermostats, security cameras, and even fish tank monitors are all part of the Internet of Things (IoT).
Unfortunately, many IoT devices have minimal security. They come with weak passwords, lack regular updates, and are easy targets for hackers. Once compromised, they can be used for data breaches, surveillance, or large-scale cyberattacks.
Let’s explore the biggest IoT cybersecurity risks, the most famous incidents, and the steps you can take to secure your connected devices.
What is IoT cybersecurity?
IoT cybersecurity is the practice of protecting internet-connected devices from cyber threats.
IoT technology—ranging from smart home gadgets to industrial sensors—collects and transmits data, making it a potential entry point for hackers. And with 40 billion connected devices incoming by 2030, finding IoT security solutions is more vital than ever.
Without proper security, attackers can exploit weak passwords, outdated software, or unencrypted connections to gain access, steal information, or even take control of the devices.
This video from NIST introduces what the Internet of Things is, and how to secure it.
What are the biggest IoT security risks?
IoT security isn’t just about preventing data breaches. A hacked IoT device can disrupt critical infrastructure, leak sensitive information, or be used as a tool in a larger cyberattack. Here are some of the biggest security risks.
- Weak authentication and default credentials: Many IoT devices ship with preset usernames and default passwords. If these aren’t changed, hackers can find them easily—sometimes with a simple Google search. Attackers scan for devices with default credentials, log in, and take control.
- Lack of encryption: Encryption protects data from being intercepted. But many IoT devices transmit information in plain text, making it easy for hackers to steal data or inject malicious commands.
- Insecure APIs: Application programming interfaces (APIs) allow IoT devices to communicate with apps and cloud platforms. If they aren’t properly secured, attackers can exploit them to gain access to sensitive systems.
- Outdated firmware and patch management issues: Unlike computers and smartphones, IoT devices don’t always receive regular security updates. Many don’t have an easy way to update at all. This means vulnerabilities stay exposed long after they’re discovered.
- Botnet attacks: Once hacked, IoT devices can be recruited into a botnet—a network of infected devices controlled by attackers. These botnets are often used for large-scale cyberattacks, like distributed denial-of-service (DDoS) attacks that overload websites or networks.
- Physical security weaknesses: IoT devices are often small, portable, and placed in public areas. If attackers gain physical access, they can tamper with the hardware, extract credentials, or install malicious firmware.
This CISA infographic shows an example of an IoT ecosystem, and the many security vulnerabilities it can introduce.
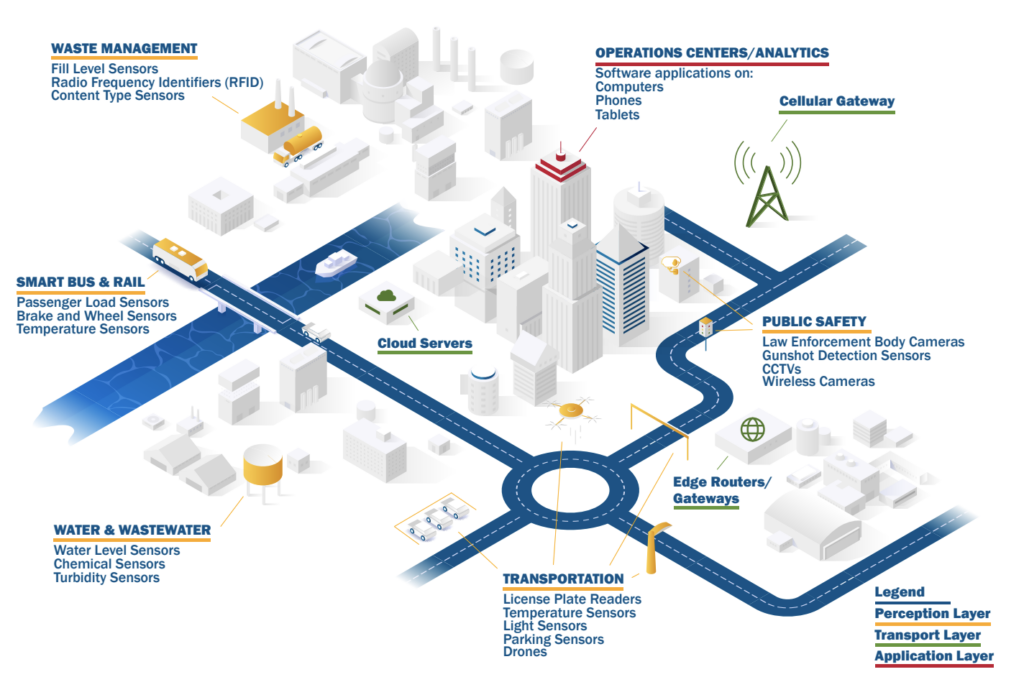
Why is IoT device security so challenging?
Securing IoT devices is harder than securing traditional computers or servers. And the issue is only growing, with CybelAngel identifying a 68% increase in vulnerable assets last year.
Let’s explain the challenges of securing IoT devices.
Firstly, IoT devices are everywhere. A single company might use thousands of them, each with different manufacturers, software versions, and security levels. Keeping track of them all is a challenge.
Also, each device often has limited computing power. Many IoT devices are built to be cheap and efficient. They don’t have the processing power for advanced security features like real-time threat detection, encryption, or antivirus software.
Smart devices are often dependent on third-party components, too. These supply chain vulnerabilities can introduce security flaws before the device even reaches the user.
Plus, with no universal security standard for IoT solutions, some device manufacturers follow best practices, while others do not. It’s inconsistent, and it’s unreliable. This makes it almost impossible to enforce cybersecurity for IoT devices across the board.
Deployments are often remote and unmanaged, as well. Many IoT devices operate in remote locations or outside traditional IT security controls. Industrial sensors, smart meters, and surveillance cameras may be deployed far from human oversight, making them harder to monitor and update safely.
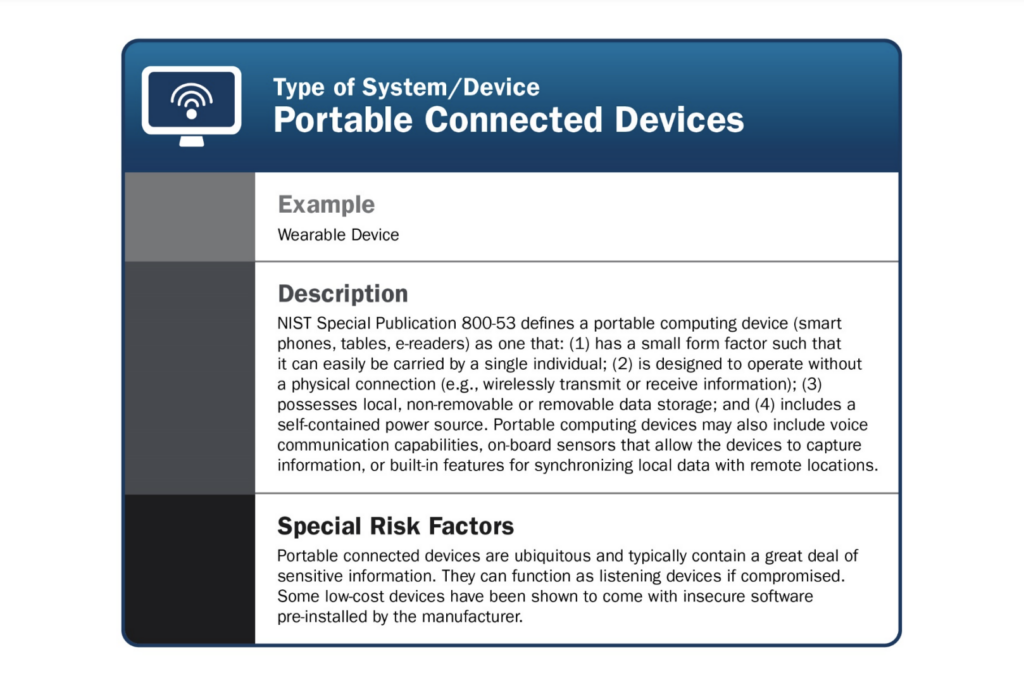
What are the most famous IoT attacks?
Some of the biggest cyberattacks in history have been linked to IoT vulnerabilities. Here are a few examples.
1. Mirai botnet (2016—present)
The Mirai malware scanned the internet for IoT devices with default credentials, took control of them, and turned them into a massive botnet. This botnet launched some of the largest DDoS attacks ever recorded, knocking major websites offline, including Twitter, Netflix, and Reddit.
A more recent variant has posed new security challenges to the IoT network, targeting AVTECH cameras and Huawei routers.

2. BrickerBot (2017)
Unlike traditional malware, BrickerBot didn’t just infect IoT devices. It destroyed them. The malware exploited weak security settings to corrupt device firmware, effectively “bricking” them and rendering them useless.

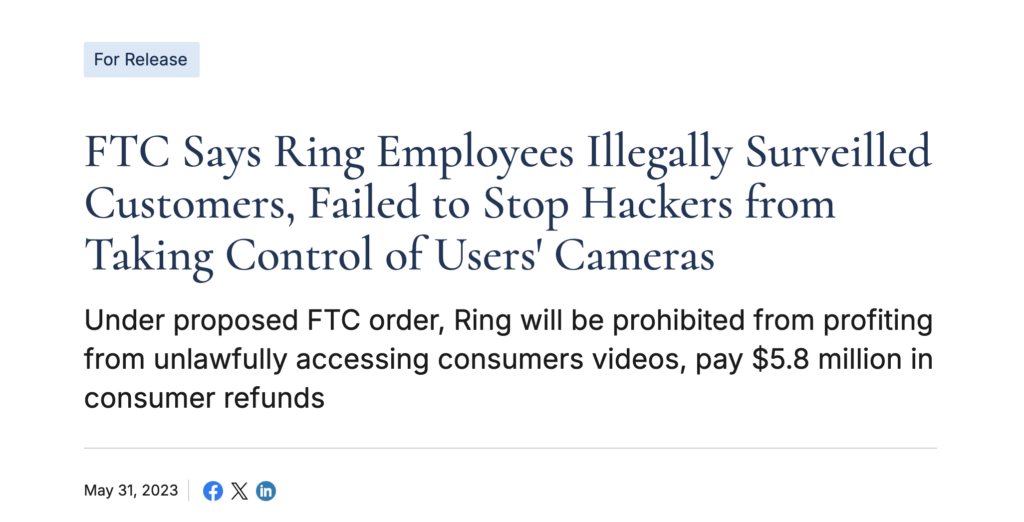
3. Ring camera hacks (2019)
Hackers gained access to home security cameras by exploiting weak passwords. In some cases, they used the cameras’ speakers to harass homeowners, and even an 8-year-old girl, demonstrating the dangers of poor IoT security in personal devices.
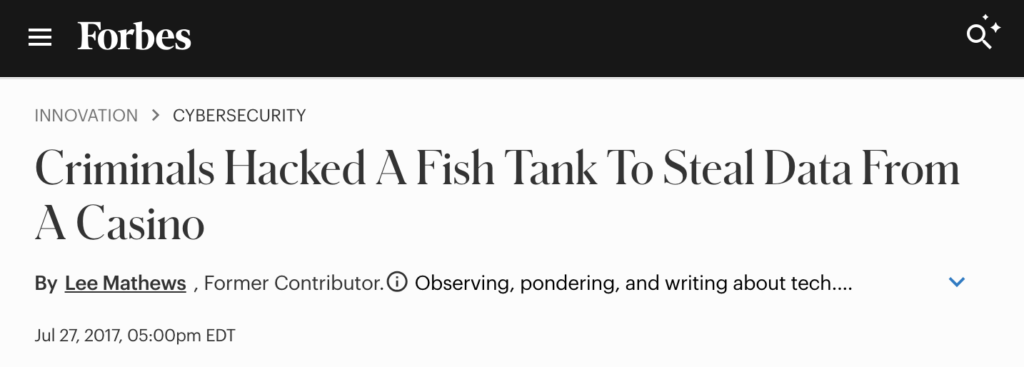
4. Casino thermostat breach (2017)
In a high-profile North American casino breach, cybercriminals infiltrated a smart thermostat used in a fish tank. This thermostat was connected to the casino’s internal network, allowing attackers to steal 10GB of sensitive data.
Securing the IoT: Insights for every level
CybelAngel’s 2025 annual report found that IoT device attacks will continue to rise this year.
IoT security isn’t just a concern for large enterprises. It affects individuals, businesses, and even entire industries.
Here’s how to strengthen IoT security, from established frameworks to practical steps for individuals and businesses.
1. Frameworks: The foundation of IoT security
A structured approach to IoT security helps organizations and governments set clear standards.
Several frameworks provide guidance on securing IoT devices:
- NIST IoT Security Framework: The National Institute of Standards and Technology (NIST) provides a widely used set of guidelines, covering everything from access control to data protection.
- IoT Cybersecurity Improvement Act (US): This legislation mandates security requirements for IoT devices used by government agencies, influencing best practices for the private sector.
- ENISA IoT Security Guidelines (EU): The European Union Agency for Cybersecurity (ENISA) outlines recommendations for securing IoT devices in consumer and industrial environments.
- The IoT Security Foundation: An organization with a goal of securing the IoT and providing frameworks and best practices.
2. Personal security steps everyone can take
Even a single insecure IoT device can be an entry point for attackers. These steps help individuals protect their connected devices:
- Change default passwords immediately: Factory-set passwords are easy to find online. Replace them with strong, unique credentials for each device to prevent account takeovers.
- Enable two-factor authentication (2FA): If your device or associated account supports 2FA, turn it on for an added layer of security.
- Keep firmware updated: Many IoT devices receive security patches. Enable automatic updates or check for firmware updates regularly.
- Disable unnecessary features: Features like remote access, voice control, or Bluetooth may introduce security risks. If you don’t need them, turn them off.
- Use a separate network connection for IoT devices: Keeping IoT devices on a separate Wi-Fi network from your main devices (like laptops and phones) reduces the risk of a network security breach.
3. IoT risk management for businesses
For businesses, IoT security challenges are even more complex. Companies often deploy hundreds or thousands of devices, each with its own potential vulnerabilities.
A strategic approach is necessary to improve the security of IoT devices.
- Implement network segmentation: Separating IoT devices from core business systems prevents an attacker from moving laterally across networks.
- Monitor and log IoT activity: Continuous monitoring can detect suspicious behavior before it turns into a security incident.
- Use secure APIs: Many IoT systems rely on APIs to communicate with apps and cloud platforms. Ensuring these APIs are properly authenticated and encrypted prevents unauthorized access.
- Enforce strong access controls: Not every employee, stakeholder, or system needs access to IoT devices. Limit permissions to only those who require them.
- Conduct regular security audits: IoT environments evolve quickly. Regular vulnerability assessments help identify and fix security gaps before they’re exploited.
- Demand secure devices from vendors: Businesses should prioritize IoT vendors that follow security best practices, such as providing regular firmware updates and using encrypted communication protocols.
- Invest in IoT cybersecurity services: CTI tools like CybelAngel can help you to track and contain all your public-facing assets, reducing your cybersecurity IoT risks.
FAQs: IoT and cybersecurity
What does IoT stand for?
IoT stands for Internet of Things, referring to physical devices connected to the internet, such as smart home gadgets, industrial sensors, and wearable technology.
What does IoT stand for in the context of cybersecurity?
IoT stands for the Internet of Things, which is a network of connected devices that can pose security issues when best practices aren’t followed.
What is IoT used for?
IoT is used in smart homes (thermostats, security cameras, voice assistants), healthcare (wearable monitors, smart medical devices), industrial automation (factory sensors, smart grids), and logistics (tracking systems, fleet management).
What is an example of an IoT device?
A smart thermostat (e.g., Nest), a wearable smart watch or fitness tracker (e.g., Fitbit), or a smart security camera (e.g., Ring) are all examples of IoT devices.
What is IoT in cybersecurity?
IoT in cybersecurity refers to the security measures needed to protect internet-connected devices from cyber threats like hacking, data breaches, and malware infections.
What are cyberattacks through IoT?
IoT attacks include DDoS attacks (e.g., Mirai botnet), data breaches (e.g., casino thermostat hack), and device takeovers (e.g., Ring camera hacks).
What is an example of IoT security?
Using strong passwords, regularly updating firmware, encrypting data, and keeping IoT devices on a separate network from critical systems.
Conclusion
IoT devices are everywhere. Many are built for convenience, not protection, making them easy targets for attackers.
Businesses using IoT devices need to take security seriously. The reality is, if an IoT device is connected to the internet, it’s a potential entry point for hackers. Cybersecurity in IoT isn’t just good practice. It’s a necessity.
Book a call with CybelAngel to talk further about securing your external attack surface, and taking back control of your security posture.

